Welcome back, my nascent Hackers!
In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.
In this tutorial, we'll look at active reconnaissance of a target with one of the best network scanning tools, nmap.

The risk with active scanning is that you will be detected and the security hardware or security admin will block any further attempts by you to pwn the site, or worse—report you to law enforcement. Nmap has multiple modes of scanning a potential target and many ways of evading detection.
Step 1: Open Nmap
Let's go to our hacking platform, BackTrack, and open up nmap. To find it, go the BackTrack button at the bottom left of the screen to open up the initial menu options. Then, select BackTrack -> Information Gathering -> Network Analysis -> Network Scanners, and click on nmap.
Step 2: Using Nmap
When you select nmap, you'll open a screen that looks like the screenshot below.
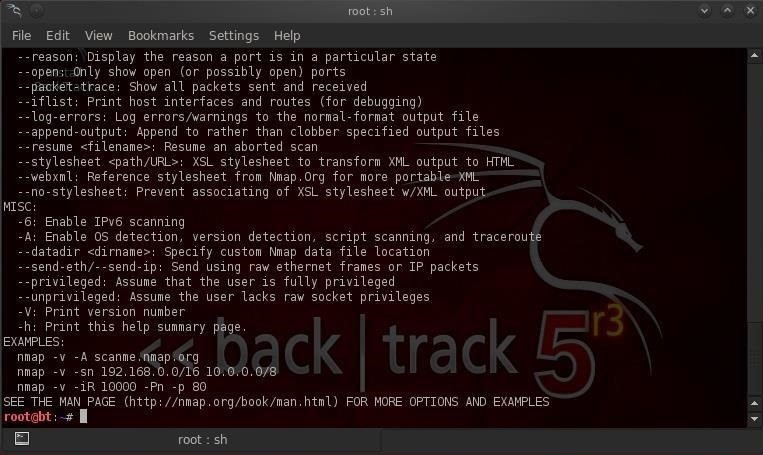
Note that it opens a Linux terminal with the help screen for nmap. Whenever you want to see the help screen, you can simply type at the command prompt:
- bt > nmap -h
You can also get the manual for nmap by typing:
- bt > man nmap
Nmap is a delightful tool for gathering information on a network or site. For instance, if we want to gather information on ESPN.com, we can type:
- bt > nmap -sT espn.com
We can see some of the output below.
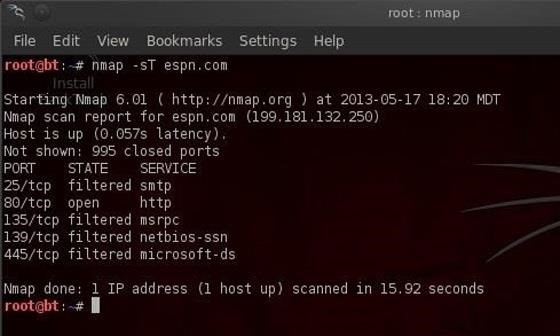
This command tells nmap to scan (-s) using TCP (T) the domain espn.com. Note that the output shows us the ports that this web server has open. With this information, we can then reasonably conclude that the default services for these ports are running on this system. In this case, this server has port 25 open (SMTP), port 80 open (HTTP), port 135 open (msrpc), port 139 open (net-bios), and port 445 (msds).
This is important information to have when selecting a hack/exploit as each hack is specific to technologies/services.
Step 3: Operating System Detection
Nmap is also capable of detecting and making a guess as to what the operating system is. Type:
- bt > nmap -O espn.com
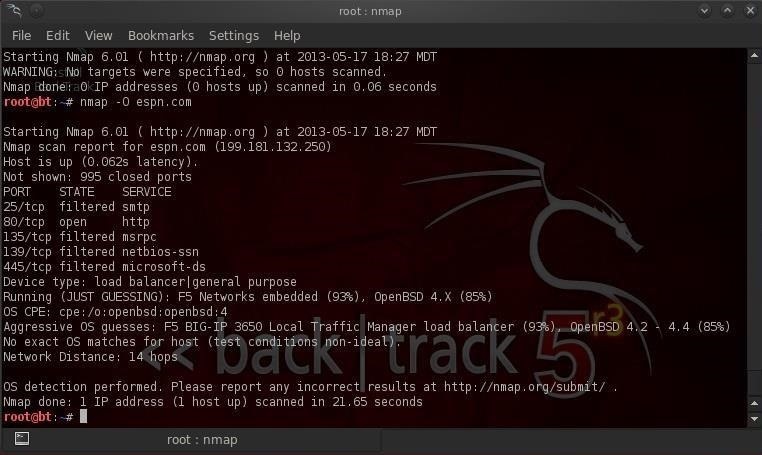
We can see from the screenshot above that nmap guessed that this site is running F5 Networks with a 93% probability and OpenBSD with a lower 85% probability.
Step 4: Stealth Scan
The above scan by nmap is highly reliable, but its drawback is that it's also easily detectable. Nearly every system admin will know that you're scanning their network as it creates a full TCP connection, and this is logged with your IP address in the log files.
A more stealthy scan can be conducted using the -sS switch in nmap. This scan uses SYN flagged packets that do NOT create a connection on the target machine and therefore are not logged. This type of scan is slightly less reliable, but is much more stealthy. Type:
- bt > nmap -sS espn.com
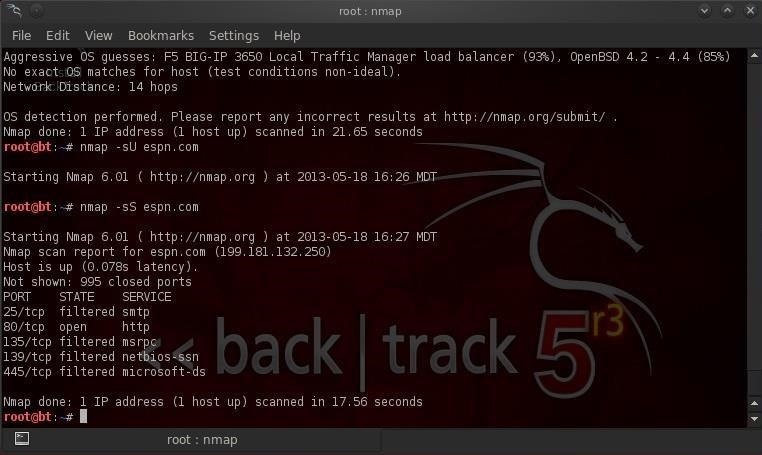
As we can see in the screenshot above, it gave us the same results without our activity being logged by the target system.
Step 5: Evading Intrusion Detection Systems
Most commercial servers and websites have intrusion detection systems (IDS) protecting them. These systems look for telltale signs of malicious activity, then alert the security administrator. Scans such as ours are easily detected by these systems and can set off an alert.
However, there are numerous ways to evade these IDSs, and we'll look at one here.
IDSs usually have a threshold setting. This means that if it sees numerous packets that appear to be scans, then it will alert the admin. To avoid detection, we can simply slow down our scan below this threshold. Nmap has numerous speed settings. Here we'll use the "sneaky" speed setting. Let's type:
- bt > nmap -sS -T2 espn.com
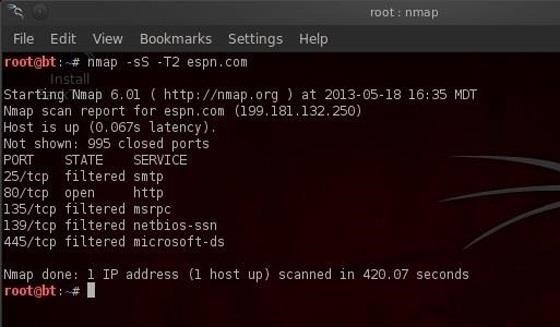
The -T2 setting tells nmap to use the sneaky speed. This scan will likely take longer, but it is much more likely to go undetected by the IDS.
One Final Note
Nmap can also be an excellent denial of service (DOS) tool. If several individuals all send packets from nmap at a target simultaneously at high speed (nmap "insane" speed or -T5), they're likely to overwhelm the target and it will be unable to process new website requests effectively, rendering it useless.
We'll continue with more reconnaissance techniques in future tutorials, so keep coming back! Until then, feel free to ask questions on this topic below, or head the Null Byte forum for any questions off topic.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















41 Comments
I can't update Metasploit Framework in Backtract 5R3. I'm running it with Virtualbox, and when I type "msfupdate" in the msfconsole, it says "Authentication realm: <https://www.metasploit.com:443> = MSF must be updated via GitHub or a more recent msfupdate. See [http://r-7.co/MSF-SVN for more = . How do I go about fixing this? Is it because Tortoise SVN is installed on my computer?
Thanks in advance.
Dylan:
You must logged in as root to update Metasploit. Try again as root.
OTW
How do I log in as root? It says "Password for root:" and then it gives me the same error. It then asks for username. Not entirely sure where to go about acquiring that. Sorry for the noob questions. On a different note, is there any chance you'll be giving us tutorials on how to use Kali or BTR3 to get into more modern systems like Windows 7? (To install meterpreter.) I've been having trouble getting it on a computer, because I have no physical access to the machine I want to get into, and the methods you outlined in your previous tutorials use old methods (MW2010, IE8, Adobe Reader 9).
Thanks in advance.
Dylan:
The password for root in BackTrack is toor.
I will be offering some tutorials in the near future on exploiting Win 7, so stay tuned. By the way, Microsoft Windows 2010 is still very current and about half of all computers still have Adobe Reader 9 or older, so those techniques will work on most computers.
OTW
It takes about three to four tries, but after I do password - toor and username : root, it gives me this :
svn : E170001 Unable to connect to a repository at URL http://www.metasploit.com/svn/framework3/trunk
svn : E170001 OPTIONS of (^ that url) : authorization failed: could not authenticate to server: rejected basic challenge (https://metasploit.com)
Not sure if that's on my end, or what. If it at all matters, I'm using the GNOME BT5R3 .iso.
I don't know how is it in BTR but in Kali if you didn't use the network mirror in the installer, you can't download things from the repositories. Go to /etc/sources.list and put in the Backtrack repositories.
Dylan:
When log in to BackTrack when it first boots up, do you log in as "root"? I'm not sure where you are logging in at.
OTW
I'll list step by step what I do.
1) Run Virtualbox
2) Run BT5R3 (Ubuntu 64 bit with the x64 KDE ISO)
3) It boots up, and asks me how I want to startup (I always choose the first one, default boot text mode.)
4) It opens the terminal / console / whatever with the root@bt:~# prompt. I type "startx" to get it to startup.
5) The default desktop of BT5R3.
Am I doing something incorrectly?
Dylan:
It sounds like you haven't installed BT5r3 but are running the live CD in Virtual Box. You should install BackTrack in Virtual Box or am I misunderstanding you?
OTW
That might've been my problem this entire time. I'll see what happens after I install. Thanks! (For dealing with my utter noobishness, that is. c:)
Edit - So I've finished installing, and it asked me to restart or continue. I hit continue, as I'm not sure if my progress will save or not on Virtualbox. What do? (If it makes any difference, I never burned a BackTrack5R3 CD. I simply downloaded the ISO and run it with Virtualbox.)
Hey I think it's kind of late to reply but any way you can download the latest Metasploit Framework from the official metasploit website and then just install it on your BT
I read somewhere that you're able to spoof your IP and Mac addy into something else, and in addition, if one were behind a proxy, too along with the spoofing, would he then be safe from detection?
John:
You can spoof both your IP and MAC address. Its a good first step, but doesn't necessarily mean your are safe. When you spoof your IP, you can't get a connection to the target. All replies go to the spoofed IP. Works great for DoS attacks, but little else.
As for using proxies, that's a good idea, but it will still leave behind telltale signs that they were compromised. You will make it harder to track you, but ideally you don't even want them to know you were there.
OTW
are we must use linux to do a DOS attack ?
because iam using windows xp
Rico:
You do not have to use Linux to do a DoS attack. There are many tools in Windows to do a DoS.
OTW
Do SYN and TCP risk detection? Or is one of them undetectable? Also there are FIN and ACK, can they be used instead?
Magnorek:
All of these are detectable, but generally, scans are ignored by most security admins as they are so numerous. A TCP scan, though, will be logged, providing evidence of your IP address when someone detects an intrusion.
FIN and ACK can be used, but generally, do not work on modern Windows systems.
OTW
Please make more recon tutorials, they're awesome.
p.s- on behalf of all null byte readers I'd like to thank you for actually responding to your comments! ( you don't need to respond to this one haha)
-Jojo
Frenzy:
I assume this server is on your network as it has an internal IP address?
OTW
Frenzy:
Ok. Please note that in the tutorial, I wrote;
"If several individuals all send packets from nmap at a target simultaneously at high speed (nmap "insane" speed or -T5), they're likely to overwhelm the target and it will be unable to process new website requests effectively, rendering it useless."
It is unlikely that single individual can DoS a server, but "numerous" individuals running this command likely will, at least for awhile.
OTW
When i DoS a network, i just send a ton of death. requests which doesn't allow anyone to connect.
aireplay-ng -0 (however many u want to send. The more you send the longer their network is unusable.) -a (bssid of the network.) mon0 (or whatever your wireless interface is)
Well, that is the idea of DoS attacks.
OTW :
When I type nmap -sT espn.com it show me this ;
Please any help
Your DNS is not workng.
how can I fix it ? and I have a question so far, all tutorials you made, we need to use a usb wireless adapter for all of them (tutorials) ?
Are you running in a VM? If so, usually you can simply re-boot your system. It could be many things, but check your /etc/resolv.conf. It should have a public IP of the DNS server.
You can use an internal wireless adapter with BackTrack if it is not in a VM. Because most internal wireless adapter don't have the capability to hack, you are best getting a aircrack-ng compatible external wireless adapter.
Thanks for replying
Yes I'm running in a VM but you didn't answer to my question exactly. I will be most clear. My question is, for all tutorials on backtrack (or Kali) we need to use a external wireless adapter ?
Then will then need an external wireless adapter.
thanks for replying
I'm using a netgear WNA3100 and on aircrak-ng website I can see only netgear WNDA3100. There are a problem ? the "D" makes problem ?
If its not on the aircrack-ng list, its not compatible.
How exactly should I interpret this ? The services are not running on its system ? And what more is usefull?
I'm not sure what you are asking me.
I don't exactly know how to go about this information (what to do with it) but I realise it would imply a lot of explanation and I don't want to waste your time. I shall try and find infos by myself. Thank you anyway!
can u do the 'sneaky' setting in conjuction with the tcp connection whilst using an anonymizing network such as I2P?
Yes
I like to be like you
I am new in null-byte and i shocked to see that null-byte is the sea of knowledge for beginners.
Thanks again for this kind job.
Nice!...
I'm confussed... I usually make pentest to my server...
now I'm learning about reconnaissance using nmap, nikto... but I need to know what I do with this dumped information?
Diego Collao
nice tutorial thank you
Is it illegal to scan network with nmap? Without covering ip
You wrote -sS option is stealthy (at least stealthier than -sT option). But I do not see any difference in packet capture in the scanner machine. Would you please explain?
Thanks
Share Your Thoughts