Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.
Shodan has changed the way hackers build tools, as it allows for a large part of the target discovery phase to be automated. Rather than needing to scan the entire internet, hackers can enter the right search terms to get a massive list of potential targets. Shodan's Python library allows hackers to quickly write Python scripts that fill in potential targets according to which vulnerable devices connect at any given moment.
You can imagine hunting for vulnerable devices as similar to trying to find all the pages on the internet about a specific topic. Rather than searching every page available on the web yourself, you can enter a particular term into a search engine to get the most up-to-date, relevant results. The same is true for discovering connected devices, and what you can find online may surprise you!
Step 1: Log in to Shodan
First, whether using the website or the command line, you need to log in to shodanhq.com in a web browser. Although you can use Shodan without logging in, Shodan restricts some of its capabilities to only logged-in users. For instance, you can only view one page of search results without logging in. And you can only see two pages of search results when logged in to a free account. As for the command line, you will need your API Key to perform some requests.
Step 2: Set Up Shodan via Command Line (Optional)
A particularly useful feature of Shodan is that you don't need to open a web browser to use it if you know your API Key. To install Shodan, you'll need to have a working Python installation. Then, you can type the following in a terminal window to install the Shodan library.
~$ pip install shodan
Collecting shodan
Downloading https://files.pythonhosted.org/packages/22/93/22500512fd9d1799361505a1537a659dbcdd5002192980ad492dc5262717/shodan-1.14.0.tar.gz (46kB)
100% |████████████████████████████████| 51kB 987kB/s
Requirement already satisfied: XlsxWriter in /usr/lib/python2.7/dist-packages (from shodan) (1.1.2)
Requirement already satisfied: click in /usr/lib/python2.7/dist-packages (from shodan) (7.0)
Collecting click-plugins (from shodan)
Downloading https://files.pythonhosted.org/packages/e9/da/824b92d9942f4e472702488857914bdd50f73021efea15b4cad9aca8ecef/click_plugins-1.1.1-py2.py3-none-any.whl
Requirement already satisfied: colorama in /usr/lib/python2.7/dist-packages (from shodan) (0.3.7)
Requirement already satisfied: requests>=2.2.1 in /usr/lib/python2.7/dist-packages (from shodan) (2.21.0)
Building wheels for collected packages: shodan
Running setup.py bdist_wheel for shodan ... done
Stored in directory: /root/.cache/pip/wheels/fb/99/c7/f763e695efe05966126e1a114ef7241dc636dca3662ee29883
Successfully built shodan
Installing collected packages: click-plugins, shodan
Successfully installed click-plugins-1.1.1 shodan-1.14.0Then, you can see all the available options -h to bring up the help menu.
~$ shodan -h
Usage: shodan [OPTIONS] COMMAND [ARGS]...
Options:
-h, --help Show this message and exit.
Commands:
alert Manage the network alerts for your account
convert Convert the given input data file into a different format.
count Returns the number of results for a search
data Bulk data access to Shodan
domain View all available information for a domain
download Download search results and save them in a compressed JSON...
honeyscore Check whether the IP is a honeypot or not.
host View all available information for an IP address
info Shows general information about your account
init Initialize the Shodan command-line
myip Print your external IP address
org Manage your organization's access to Shodan
parse Extract information out of compressed JSON files.
radar Real-Time Map of some results as Shodan finds them.
scan Scan an IP/ netblock using Shodan.
search Search the Shodan database
stats Provide summary information about a search query
stream Stream data in real-time.
version Print version of this tool.These controls are pretty straightforward, but not all of them work without connecting it to your Shodan API Key. In a web browser, log in to your Shodan account, then go to "My Account" where you'll see your unique API Key. Copy it, then use the init command to connect the key.
- Don't Miss How to Use the Shodan API with Python to Automate Scans for Vulnerable Devices (Like Mr. Robot)
~$ shodan init XXXXxxxxXXXXxxXxXXXxXxxXxxxXXXxX
Successfully initializedStep 3: Search for Accessible Webcams
There are many ways to find webcams on Shodan. Usually, using the name of the webcam's manufacturer or webcam server is a good start. Shodan indexes the information in the banner, not the content, which means that if the manufacturer puts its name in the banner, you can search by it. If it doesn't, then the search will be fruitless.
One of my favorites is webcamxp, a webcam and network camera software designed for older Windows systems. After typing this into the Shodan search engine online, it pulls up links to hundreds, if not thousands, of web-enabled security cameras around the world.
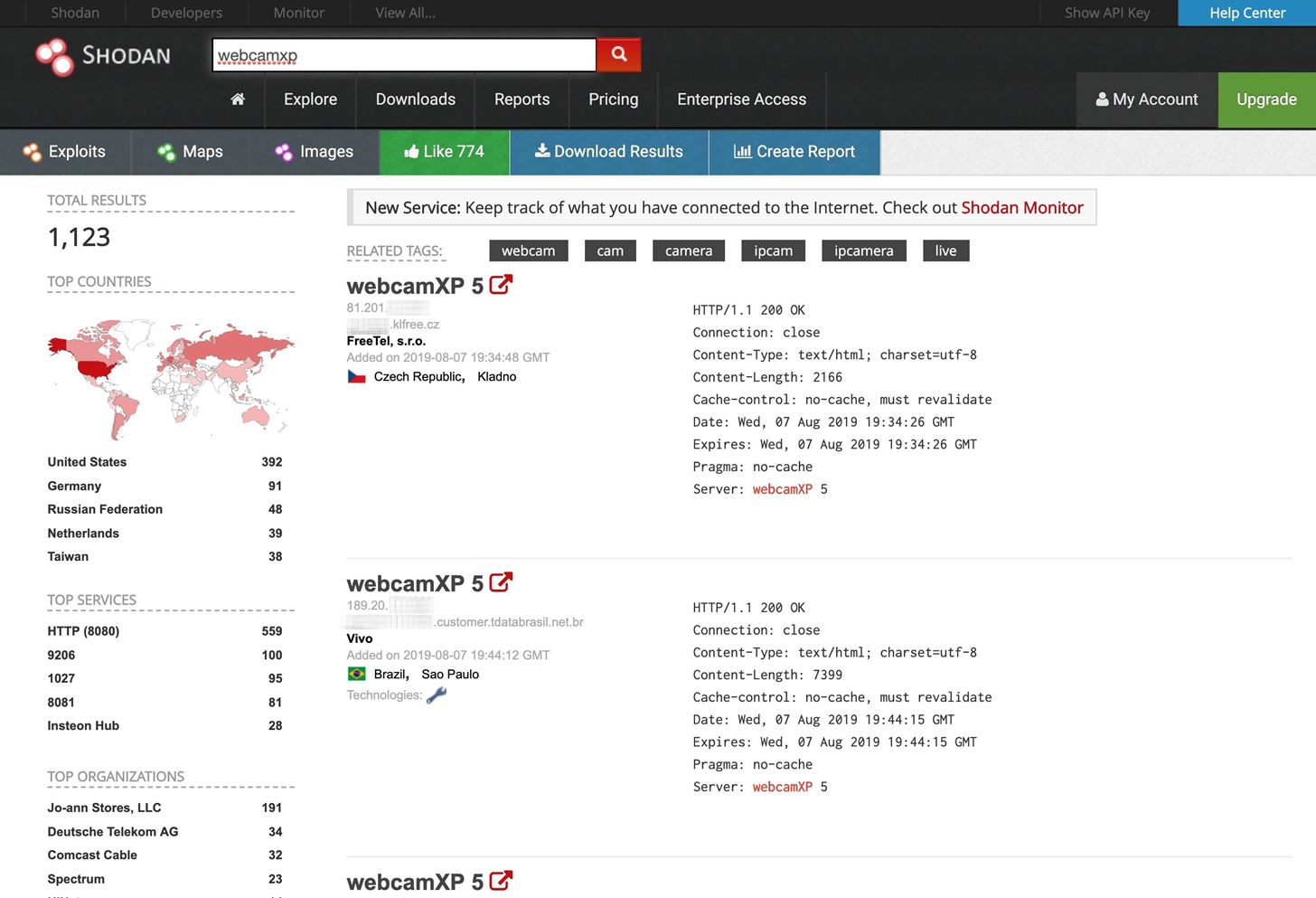
To do this from the command line, use the search option. (Results below truncated.)
~$ shodan search webcamxp
81.133.███.███ 8080 ████81-133-███-███.in-addr.btopenworld.com
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nConten t-Length: 7313\r\nCache-control: no-cache, must revalidate\r\nDate: Tue, 06 Aug 2019 21:39:29 GMT\r\nExpires: Tue, 06 Aug 2019 21:39:29 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
74.218.███.██ 8080 ████-74-218-███-██.se.biz.rr.com
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 7413\r\nCache-control: no-cache, must revalidate\r\nDate: Wed, 07 Aug 2019 14:22:02 GMT\r\nExpires: Wed, 07 Aug 2019 14:22:02 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
208.83.██.205 9206 ████████████.joann.com HTTP/1.1 704 t\r\nServer: webcam
XP\r\n\r\n
115.135.██.185 8086
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 2192\r\nCache-control: no-cache, must revalidate\r\nDate: Wed, 07 Aug 2019 06:49:20 GMT\r\nExpires: Wed, 07 Aug 2019 06:49:20 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
137.118.███.107 8080 137-118-███-███.wilkes.net
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 2073\r\nCache-control: no-cache, must revalidate\r\nDate: Wed, 07 Aug 2019 12:37:54 GMT\r\nExpires: Wed, 07 Aug 2019 12:37:54 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
218.161.██.██ 8080 218-161-██-██.HINET-IP.hinet.net
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 7431\r\nCache-control: no-cache, must revalidate\r\nDate: Mon, 05 Aug 2019 18:39:52 GMT\r\nExpires: Mon, 05 Aug 2019 18:39:52 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
...
92.78.██.███ 37215 ███-092-078-███-███.███.███.pools.vodafone-ip.de
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 8163\r\nCache-control: no-cache, must revalidate\r\nDate: Wed, 07 Aug 2019 05:17:22 GMT\r\nExpires: Wed, 07 Aug 2019 05:17:22 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
85.157.██.███ 8080 ████████.netikka.fi
HTTP/1.1 200 OK\r\nConnection: close\r\nContent-Type: text/html; charset=utf-8\r\nContent-Length: 7947\r\nCache-control: no-cache, must revalidate\r\nDate: Wed, 07 Aug 2019 00:25:41 GMT\r\nExpires: Wed, 07 Aug 2019 00:25:41 GMT\r\nPragma: no-cache\r\nServer: webcamXP 5\r\n\r\n
108.48.███.███ 8080 ████-108-48-███-███.washdc.fios.verizon.net
HTTP/1.1 401 Unauthorized\r\nConnection: close\r\nContent-Length: 339\r\nCache-control: no-cache, must revalidate\r\nDate: Tue, 06 Aug 2019 22:40:21 GMT\r\nExpires: Tue, 06 Aug 2019 22:17:21 GMT\r\nPragma: no-cache\r\nServer: webcamXP\r\nWWW-Authenticate: Basic realm="webcamXP"\r\nContent-Type: text/html\r\n\r\n
(END)To exit results, hit Q on your keyboard. If you only want to see certain fields instead of everything, there are ways to omit some information. First, let's see how the syntax works by viewing the help page for search.
~$ shodan search -h
Usage: shodan search [OPTIONS] <search query>
Search the Shodan database
Options:
--color / --no-color
--fields TEXT List of properties to show in the search results.
--limit INTEGER The number of search results that should be returned.
Maximum: 1000
--separator TEXT The separator between the properties of the search
results.
-h, --help Show this message and exit.Unfortunately, the help page does not list all of the available fields you can search, but Shodan's website has a handy list, seen below.
Properties:
asn [String] The autonomous system number (ex. "AS4837").
data [String] Contains the banner information for the service.
ip [Integer] The IP address of the host as an integer.
ip_str [String] The IP address of the host as a string.
ipv6 [String] The IPv6 address of the host as a string. If this is present then the "ip" and "ip_str" fields wont be.
port [Integer] The port number that the service is operating on.
timestamp [String] The timestamp for when the banner was fetched from the device in the UTC timezone. Example: "2014-01-15T05:49:56.283713"
hostnames [String[]] An array of strings containing all of the hostnames that have been assigned to the IP address for this device.
domains [String[]] An array of strings containing the top-level domains for the hostnames of the device. This is a utility property in case you want to filter by TLD instead of subdomain. It is smart enough to handle global TLDs with several dots in the domain (ex. "co.uk")
location [Object] An object containing all of the location information for the device.
location.area_code [Integer]The area code for the device's location. Only available for the US.
location.city [String] The name of the city where the device is located.
location.country_code [String] The 2-letter country code for the device location.
location.country_code3 [String] The 3-letter country code for the device location.
location.country_name [String] The name of the country where the device is located.
location.dma_code [Integer] The designated market area code for the area where the device is located. Only available for the US.
location.latitude [Double] The latitude for the geolocation of the device.
location.longitude [Double] The longitude for the geolocation of the device.
location.postal_code [String] The postal code for the device's location.
location.region_code [String] The name of the region where the device is located.
opts [Object] Contains experimental and supplemental data for the service. This can include the SSL certificate, robots.txt and other raw information that hasn't yet been formalized into the Banner Specification.
org [String] The name of the organization that is assigned the IP space for this device.
isp [String] The ISP that is providing the organization with the IP space for this device. Consider this the "parent" of the organization in terms of IP ownership.
os [String] The operating system that powers the device.
transport [String] Either "udp" or "tcp" to indicate which IP transport protocol was used to fetch the information
Optional Properties:
uptime [Integer] The number of minutes that the device has been online.
link [String] The network link type. Possible values are: "Ethernet or modem", "generic tunnel or VPN", "DSL", "IPIP or SIT", "SLIP", "IPSec or GRE", "VLAN", "jumbo Ethernet", "Google", "GIF", "PPTP", "loopback", "AX.25 radio modem".
title [String] The title of the website as extracted from the HTML source.
html [String] The raw HTML source for the website.
product [String] The name of the product that generated the banner.
version [String] The version of the product that generated the banner.
devicetype [String] The type of device (webcam, router, etc.).
info [String] Miscellaneous information that was extracted about the product.
cpe [String] The relevant Common Platform Enumeration for the product or known vulnerabilities if available. For more information on CPE and the official dictionary of values visit the CPE Dictionary.
SSL Properties:
If the service uses SSL, such as HTTPS, then the banner will also contain a property called "ssl":
ssl.cert [Object] The parsed certificate properties that includes information such as when it was issued, the SSL extensions, the issuer, subject etc.
ssl.cipher [Object] Preferred cipher for the SSL connection
ssl.chain [Array] An array of certificates, where each string is a PEM-encoded SSL certificate. This includes the user SSL certificate up to its root certificate.
ssl.dhparams [Object] The Diffie-Hellman parameters if available: "prime", "public_key", "bits", "generator" and an optional "fingerprint" if we know which program generated these parameters.
ssl.versions [Array] A list of SSL versions that are supported by the server. If a version isnt supported the value is prefixed with a "-". Example: ["TLSv1", "-SSLv2"] means that the server supports TLSv1 but doesnt support SSLv2.So, if we wanted to only view the IP address, port number, organization name, and hostnames for the IP address, we could use --fields as such:
~$ shodan search --fields ip_str,port,org,hostnames webcamxp
81.133.███.███ 8080 BT ████81-133-███-███.in-addr.btopenworld.com
74.218.███.██ 8080 Spectrum Business ████-74-218-███-██.se.biz.rr.com
208.83.██.███ 9206 Jo-ann Stores, LLC ████████████.joann.com
115.135.██.███ 8086 TM Net
137.118.███.███ 8080 Wilkes Communications 137-118-███-███.wilkes.net
218.161.██.██ 8080 HiNet 218-161-██-██.HINET-IP.hinet.net
...
92.78.██.███ 37215 Vodafone DSL ███-092-078-███-███.███.███.pools.vodafone-ip.de
85.157.██.███ 8080 Elisa Oyj ████████.netikka.fi
108.48.███.███ 8080 Verizon Fios ████-108-48-███-███.washdc.fios.verizon.net
(END)Look through the results and find webcams you want to try out. Input their domain name into a browser and see if you get instant access. Here is an array of open webcams from various hotels in Palafrugell, Spain, that I was able to access without any login credentials:
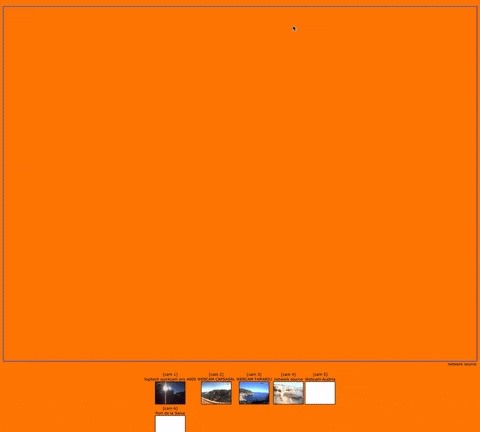
Although it can be fun and exciting to voyeuristically watch what's going on in front of these unprotected security cameras, unbeknownst to people around the world, you probably want to be more specific in your search for webcams.
Try Default Username & Passwords
Although some of the webcams Shodan shows you are unprotected, many of them will require authentication. To attempt to gain access without too much effort, try the default username and password for the security camera hardware or software. I have compiled a short list of the default username and passwords of some of the most widely used webcams below.
- ACTi: admin/123456 or Admin/123456
- Axis (traditional): root/pass,
- Axis (new): requires password creation during first login
- Cisco: No default password, requires creation during first login
- Grandstream: admin/admin
- IQinVision: root/system
- Mobotix: admin/meinsm
- Panasonic: admin/12345
- Samsung Electronics: root/root or admin/4321
- Samsung Techwin (old): admin/1111111
- Samsung Techwin (new): admin/4321
- Sony: admin/admin
- TRENDnet: admin/admin
- Toshiba: root/ikwd
- Vivotek: root/<blank>
- WebcamXP: admin/ <blank>
There is no guarantee that any of those will work, but many inattentive and lazy administrators simply leave the default settings in place. In those cases, the default usernames and passwords for the hardware or software will give you access to confidential and private webcams around the world.
Step 4: Search for Webcams by Geography
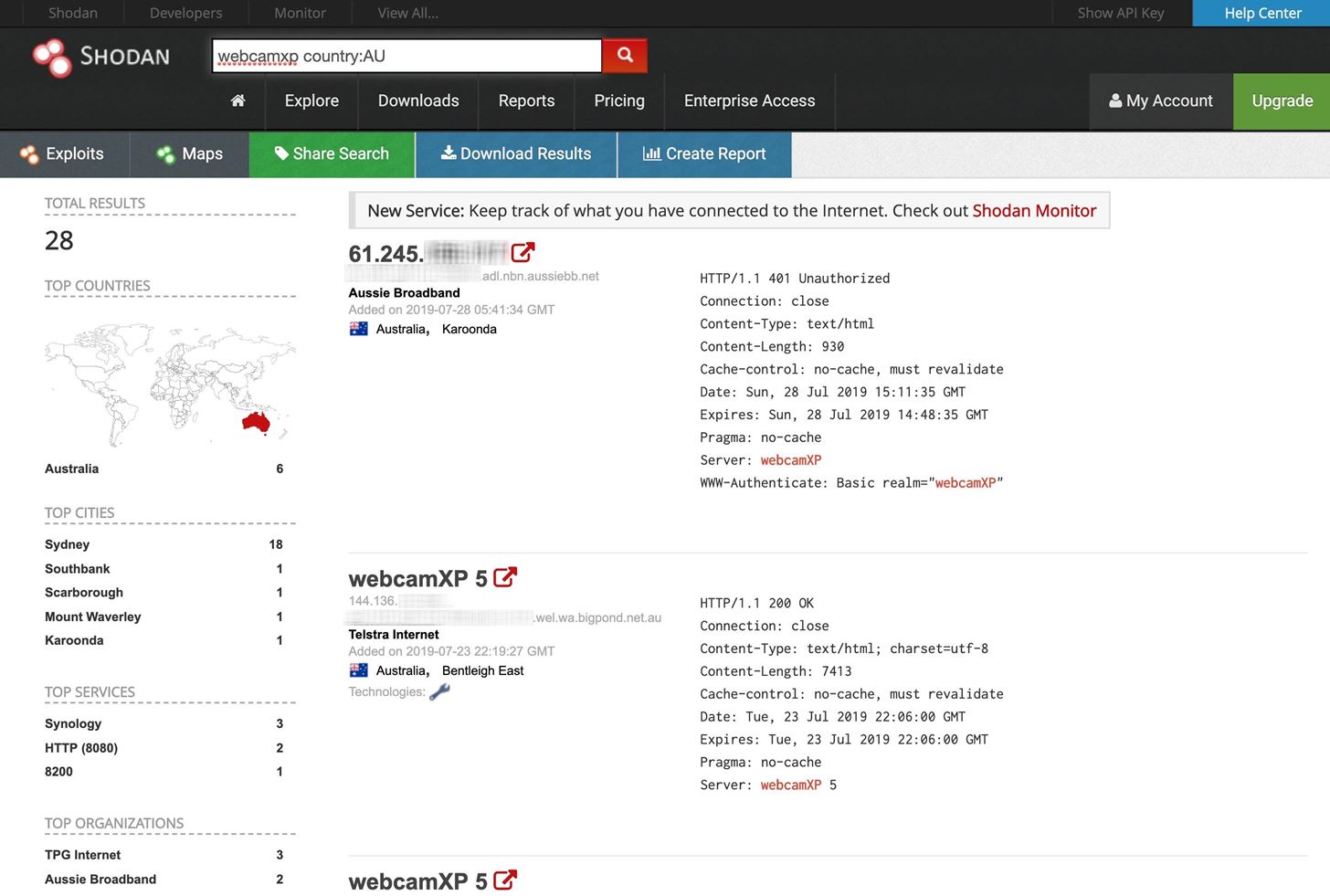
Now that we know how to find webcams and potentially log in to them using default usernames and passwords, let's get more specific and try to find webcams in a specific geographical location. For example, if we were interested in webcams by the manufacturer WebcamXP in Australia, we could find them by typing webcamxp country:AU into the search box on Shodan's website.
So how would we do an advanced search in the command line? Here's a quick list of some of the things you can search for in Shodan via the command line:
after: Search by a timeframe delimiter for things after a certain date.
asn: Search by the autonomous system number.
before: Search by a timeframe delimiter for things before a certain date.
city: Search by the city where the device is located.
country: Search by the country where the device is located (two-letter code).
device: Search by the device or network's name.
devicetype: Search by the type of device (webcam, router, etc.).
domain: Search an array of strings containing the top-level domains for the hostnames of the device.
geo: Search by the coordinates where the device is located.
hash: Search by the banner hash.
has_screenshot:true Search for devices where a screenshot is present.
hostname: Search by the hostname that has been assigned to the IP address for the device.
ip: Search by the IP address of the host as an integer.
ip_str: Search by the IP address of the host as a string.
ipv6: Search by the IPv6 address of the host as a string.
isp: Search by the ISP that is providing the organization with the IP space for the device.
link: Search by the network link type. Possible values are: "Ethernet or modem", "generic tunnel or VPN", "DSL", "IPIP or SIT", "SLIP", "IPSec or GRE", "VLAN", "jumbo Ethernet", "Google", "GIF", "PPTP", "loopback", "AX.25 radio modem".
net: Filter by network range or IP in CIDR notation.
port: Find devices based on the open ports/ software.
org: Search for devices that are on a specific organization’s network.
os: Search by the operating system that powers the device.
state: Search by the state where the device is located (two-letter code).
title: Search by text within the title of the website as extracted from the HTML source.So if we were to search webcamxp country:AU on the website directly, to do it from the command line, you would format as one of the ways below. However, if you're not on a paid plan, you can't use the Shodan API to perform detailed searches like we are trying to here. But you can still perform an advanced search on Shodan's website, with the regular restrictions for free users.
~$ shodan search webcamxp country:AU
~$ shodan search device:webcamxp country:AUOn the website, searching for webcamxp country:AU will pull up a list of every WebcamXP in Australia that is web-enabled in Shodan's index, as shown below.
Step 5: Narrow Your Search for Webcams to a City
To be even more specific, we can narrow our search down to an individual city. Let's see what we can find in Sydney, Australia, by typing webcamxp city:sydney into the website's search bar. For the command line, it would look like one of the following commands — but it's a paid-only feature with the API.
~$ shodan search webcamxp city:sydney
~$ shodan search device:webcamxp city:sydneyOn the Shodan website, the search yields the results below.
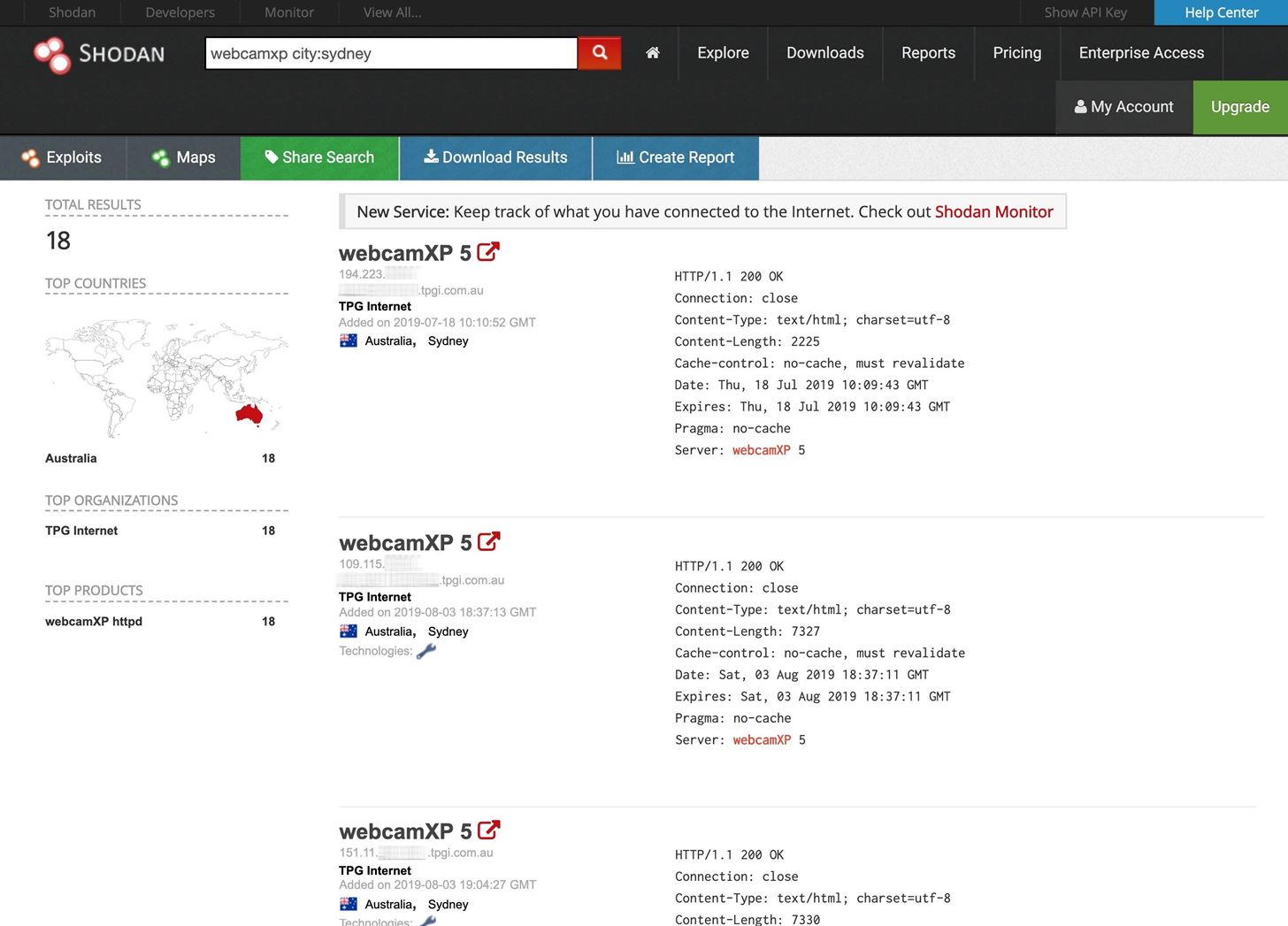
When we click on one of these links, we find ourselves in someone's backyard in Sydney, Australia!

Step 6: Find Webcams by Longitude & Latitude
Shodan even enables us to be very specific in searching for web-enabled devices. In some cases, we can specify the longitude and latitude of the devices we want to find.
In this case, we will be looking for WebcamXP cameras at the longitude and latitude (-37.81, 144.96) of the city of Melbourne, Australia. When we search, we get a list of every WebcamXP at those coordinates on the globe. We must use the keyword geo followed by the longitude and latitude. So in the search bar, use webcamxp geo: -37.81,144.96. On the command line interface, again, which is a paid feature, it'd look like one of these:
~$ shodan search webcamxp geo:-37.81,144.96
~$ shodan search device:webcamxp geo:-37.81,144.96When we get that specific, on Shodan's website, it only finds four WebcamXP cameras. Click on one, and we can find that once again, we have a private webcam view of someone's camera in their backyard in Melbourne, Australia.

Step 7: Shodan from the Command Line
Something we can do from the command-line interface that we can't from the website is search for information on a host. For instance, we can run the shodan myip command to print our external IP.
~$ shodan myip
174.███.██.███Once we know it, we can search Shodan for information by running the host command.
~$ shodan host 174.███.██.███
174.███.██.███
Hostnames: cpe-174-███-██-███.socal.res.rr.com
Country: United States
Organization: Spectrum
Updated: 2019-08-02T23:04:59.182949
Number of open ports: 1
Ports:
80/tcpShodan Is a Powerful Way to Discover Devices Across the Net
I hope this short demonstration of the power Shodan gets your imagination stimulated for inventive ways you can find private webcams anywhere on the globe! If you're too impatient to hunt down webcams on Shodan, you can use a website like Insecam to view accessible webcams you can watch right now. For instance, you can view all the WebcamXP cameras that have pictures.
Whether you use Shodan or an easier site such as Insecam to view webcams, don't limit yourself to WebcamXP, but instead try each of the webcam manufacturers at a specific location, and who knows what you will find.
I hope you enjoyed this guide to using Shodan to discover vulnerable devices. If you have any questions about this tutorial on using Shodan or have a comment, ask below or feel free to reach me on Twitter @KodyKinzie.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























23 Comments
Uh, that's my backyard...
Just kidding, awesome post about Shodan. Can't wait to read the next one.
ghost_
Thanks for this great article master.
I was expecting 'How to find vulnerable website to heartbleed' as your next article.
Great post! Thx mate :)
iS shodan safe to use? or i have to use any proxies/vpns to hide myself?
Dragon:
Good question. If you are concerned about being tracked, use Shodan to get an IP and then hack it from behind a proxy/vpn.
OTW
can you make a tutorial about that? i think everyone would be interested in that :)
Dragon:
Did you read my tutorial on proxychains ?
OTW
Great having your lecture skills on this site, great info, but any reason why i seem to always just get a browser hanging when i enter the ip in addy bar??
Attikus:
Sometimes when admins find that people have been accessing or hacking their web cams, they block access with a firewall.
OTW
ahh, ok thank you :) Keep gettin more n more candid w/ your knowledge, ive been following you for a while now love some of the recent stuff
Hi...
sorry for my bad english.. :D
if i want to use for ex nmap and i wuold to use a proxy, i can use the proxychain like in the guide that you have posted in the link in the upper comment..
but if i want to spy a webcam using shodan, i can't use proxychain right?
i have to use for ex tor browser and open shodan in tor browser or there is other way to do this??
thanks..
Yes, you can setup a VPN overall on your system without setting up anything else, OR you could find a good proxy and set your browser proxy settings and you are ready to go.
P.S:Tor is not so recommended anymore because of it's own vulnerabilities.
Ok thanks.. I know tor's problem and i know also that tor now is identified by Lot of security tools.. Can i do the proxychain also whit a good proxy for My browser or if i use a " browser" i can use only one proxy??
Thanks...
I tried this and didn't find any open cams, the search system isnt very good on this site either. Anyone know what Im doing wrong?
Darkfoxx:
No, it's not that the search system isn't very good. It's more that you have to be relatively specific in what you're looking for and follow the keys.
It's a great search engine, just takes a bit of a think to get to know how it works. Reading Occupy the Web's articles about it should clear some things up.
ghost_
Did you read my articles on Shodan and understand that it uses a different indexing system and search terms than Google?
What to do if I see this?
JOP
Does the 'xp' in 'webcamxp' represent Windows XP system? If I want to control a webcam around me,such as my school,is any way to achieve it by shadon? And what kind of info I need to know before doing it?
Charles
if you read the guide and did the exerises you should know the answers by now.
Good luck and dont do something stupid that will fuck up your life :)
Funny, for me the webcamxp command show me around 150 devices in console, but 650 on the shodan website?
thank you so much , so funny :))
You can sadly only do a few searches a day as free user. Maybe 25.
Does this work for devices behind NAT?
Share Your Thoughts