Welcome back, my greenhorn hackers!
Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.
The banner is simply the application advertising what it is. Webserver administrators who are vigilant and savvy about security will often suppress or masquerade their banners.
In other words, to throw off hackers, they might replace the banner of, say, Microsoft's IIS 6.0 with a banner saying it is Apache 2.4.0. In that way, hackers will spend their time and effort trying to hack a relatively vulnerable IIS 6.0, get frustrated when it doesn't work, and eventually go away.
Remember, exploits/hacks are specific to the application and operating system among many factors. That's why fingerprinting is SO important. A hack that works on IIS 6.0 will NOT likely work on Apache.
In addition, some web administrators will put various load balancing and other devices designed to obscure the identity of the web server (Computer Associates advertises one their products with the tagline, "You can't hack what you can't see").
Fortunately, there are more sophisticated ways of determining what web server is running a website. httpprint is just such a tool, which uses heuristics (an educated guess based upon incomplete, but probably sufficient data) to identify the web server as well as web enabled devices such as printers, routers, switches, etc.
Step 1: Open Httprint
Let's start by opening httprint. Unfortunately, the GUI in BackTrack points to the wrong directory, so we need to open a terminal and type:
- bt > cd /pentest/enumeration/web/httprint/linux
Once we are in the correct directory, let's open the help screen in httprint.
- ./httprint -h
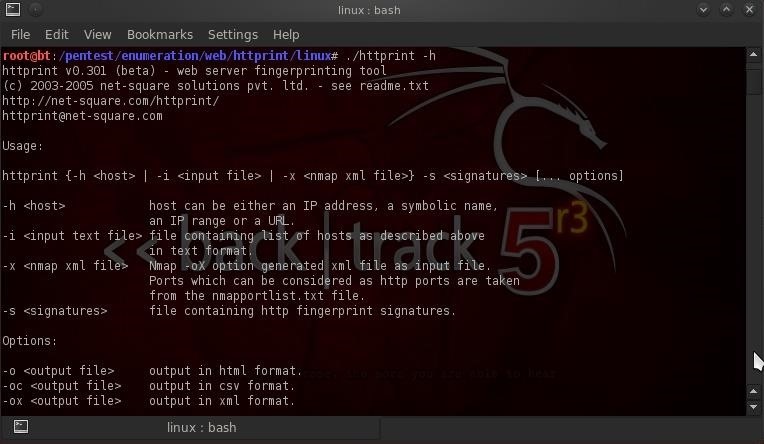
About a third of the way down this help screen, you can see the basic syntax for httprint, which is:
- httprint -h <host> -s signatures.txt
Where signatures.txt is text file in this directory that contains the signatures of the many types of web servers that httprint uses to determine the identity of the target.
Step 2: Test It in CNN.Com
Let's test it on cnn.com's website.
- bt > ./httprint -h 157.166.226.25 -P0 -s signatures.txt
I have added the P0 to suppress the ping (like when using nmap) that often is blocked by network devices and will prohibit us from accessing the web server.
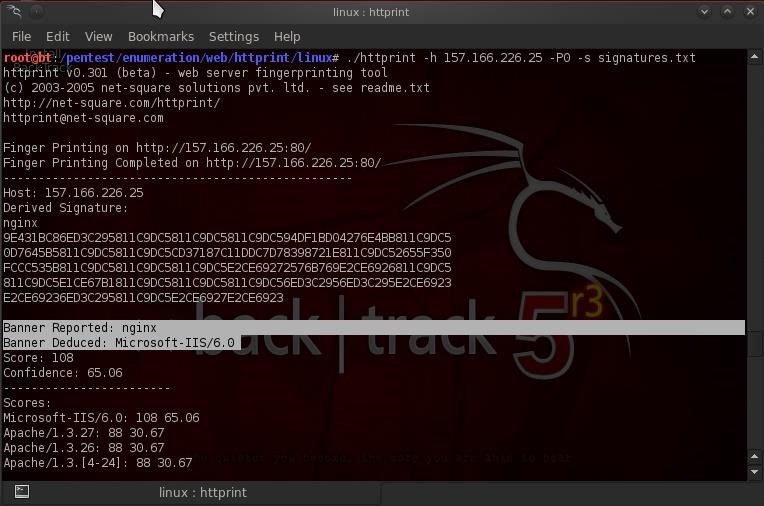
As you can see above, httprint has fingerprinted the site and tells us that cnn.com reports that it is using the nginx webserver, but in reality, is running Microsoft IIS 6.0! Hmm...that is VERY INTERESTING!
Reporting that you are running nginx is a good security strategy for cnn.com as there far fewer known vulnerabilities for nginx than IIS 6.0 This will help to divert most attackers, but not us!
Step 3: Let's Try Craigslist.org
Let's try the same on craigslist.org.
- bt > ./httprint -h 208.82.238.129 -P0 -s signtaures.txt
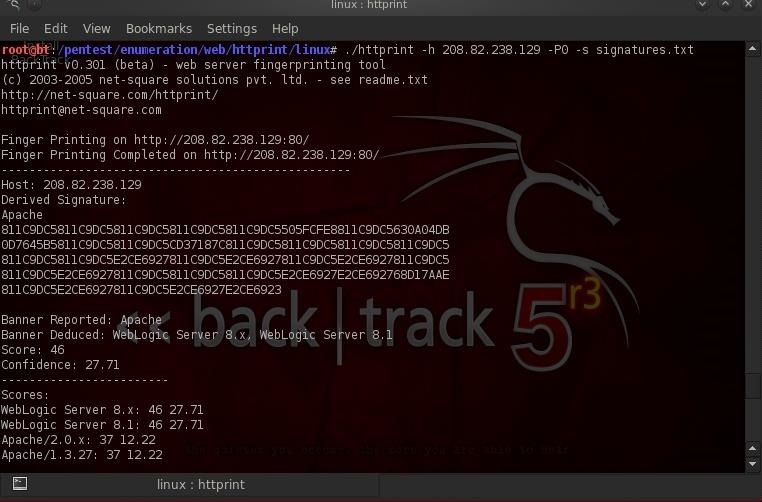
httprint tells us that craigslist.org's website shows a banner saying it is running Apache, but httprint thinks it is Oracle's Web Logic server. One interesting thing about httprint is that it also gives us a confidence level and here it says it is 27.71% confident. Not real high, so we'll take this one with a large grain of salt.
Step 4: Finally, Let's Try Wikipedia.com
Let's try one more site and see what httprint tells us. Let's point it at wikipedia.com.
- bt> ./httprint -h 208.80.154.224 -P0 -s signatures.txt
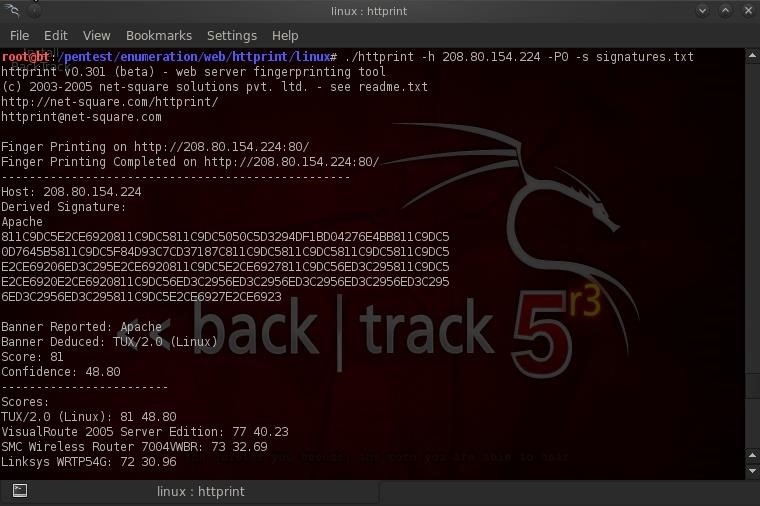
httprint tells us that although Wikipedia says it is running Apache, it deduces with a 48.8% confidence that it is running Red Hat's TUX 2.0.
Httprint is another tool in our arsenal of reconnaissance tools to decipher the nature of the target. These tools are critical as nearly every exploit is specific, so we MUST determine what we are attacking BEFORE we attack.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























8 Comments
One more interesting tutorial. Thanks :)
Hi OTW
Since we upgraded to Kali kindly adice on the path since the pentest/enumeration...is not working.
I understand that most of Kali's software are on the PATH , but whenever I try directly from the terminal it is not working.
Evil Genious
To finish this tutorial in Kali you need to do these:
apt-get install httprint
and
cd /usr/share/httprint
Evil:
One of the drawbacks of using Kali is that developers left off some great tools from BackTrack. You will probably need to download this tool from the repository.
OTW
Hey OTW
Great tutorial! Let's say we run this on a known phishing site and returns with a "signature file does not exist or corrupted signature file" . Is this normal or is there a way to get around this and find the signature file anyway?
Dave:
Welcome to Null Byte!
Any of our fingerprinting tools are only as good as the signatures in their database. If the site is running a server that is not in its database that will be the response. Did you trying running it twice?
OTW
OTW:
Thanks! Yes I ran it a couple times double checking i had the right IP and stuff. It works for other servers just not the phishing one. I was just curious if there was an error on my end. Netcat did pull a banner, but I just couldn't pull the signature.txt file with httprint
where can i download updated signatures.txt file for httprint?
Share Your Thoughts