Welcome back, my tenderfoot hackers!
One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.
In addition, when we re-encode a module to obscure its malicious nature with msfvenom or Veil-Evasion, we will often need to re-insert them into Metasploit for use by the framework.
In this tutorial, we will look at how to insert a module into Metasploit. In this case, we will be inserting an exploit module that has never been included in the Metasploit Framework, but is available from multiple sources.
Step 1: Fire Up Kali & Open Msfconsole
Let's begin, as usual, by firing up Kali, opening a terminal, and starting the Metasploit console by typing:
kali > msfconsole
Step 2: Search Joomla on Exploit-DB
Let's go to one of my favorite places to find new exploits, Exploit Database (exploit-db.com).
Click on the "Search" button in the upper right of the screen, then on "Advanced search." This will open a search window similar to the one shown below. There, type in "joomla" in the "Free Text Window" and "metasploit" in the "Author" window. (All exploits developed for Metasploit are categorized with metasploit as the author, no matter who wrote them.) This should pull up all Joomla exploits developed for use in the Metasploit Framework. Joomla is the popular, open-source web application CMS.
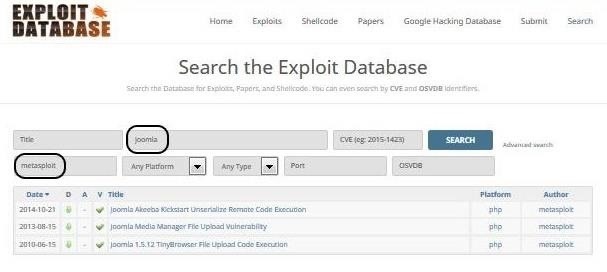
As we can see, there are three. The first one, "Joomla Akeeba Kickstart," is the newest and may not be included yet in the Metasploit Framework.
Step 3: Search Joomla in Msfconsole
Let's go back to our msfconsole and search to see whether that new Joomla exploit has been included. Type:
msf > search type:exploit joomla
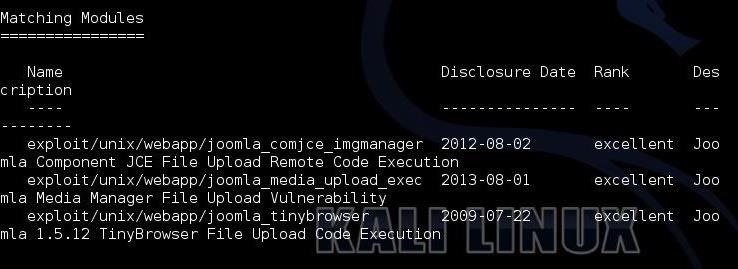
As you can see, there are three exploits in Metasploit as well, but not the "Joomla Akeeba Kickstart" exploit we found in Exploit-DB.
Step 4: Insert the New Exploit in Metasploit
Now that we have established that this new Metasploit exploit is not in the updated Metasploit, the question becomes, how do we insert it into Metasploit so that we can use it?
The first step is to make a copy of the exploit. In this case, I will simply make a copy and paste operation to save it to a text file on the Desktop of Kali.
Go back to Exploit-DB and click on the "Joomla Akeeba Kickstart Unserialize Remote Code Execution" exploit. When you do so, it will open a screen like below that displays the entire exploit.
Let's copy it and put it into a text editor such as Leafpad and save it to our Desktop. In my case, I used "joomla_kicktstart.rb" as the file name. What you name the exploit is not really important, but where you place it is.
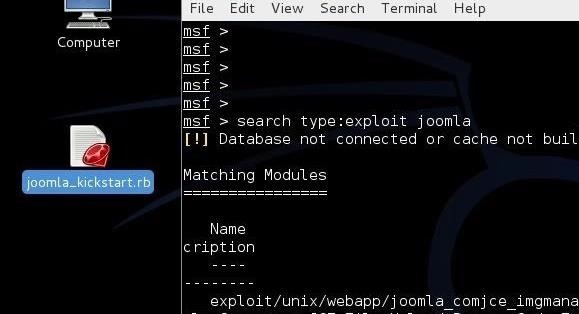
Step 5: Insert It into the Metasploit Modules
First, we need to open another terminal. To load this new module, we will need to create a directory in a format that Metasploit will understand and can read. We can use the mkdir command with the -p switch (create subdirectories as well).
kali >mkdir -p /root/.msf4/modules/exploits/unix/joomla
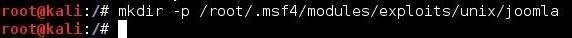
Note that the .msf4 is a hidden directory and will not appear when doing a directory listing unless you use the -a switch, such as ls -al.
Now that we have created the directory, let's navigate to that directory with the cd command.
kali > cd /root/.msf4/modules/exploits/unix/joomla
Lastly, we need to move our new exploit to this directory. We can do that with the mv command. Since our exploit is on our Desktop, we need to move it from there to our new directory where Metasploit can use it. We can move it by typing:
kali > mv /root/Desktop/joomla_kickstart.rb /root/.msf4/modules/exploits/unix/joomla
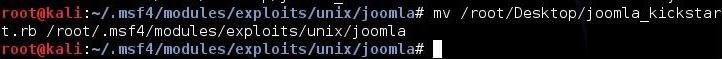
Step 6: Test Whether You Can Use It
Now that we have moved our new exploit to Metasploit, let's test whether we can use it. We will need to restart Metasploit in order for it to load new exploit. When we have a new msf prompt, let's search for our new module by typing:
msf > search type:exploit joomla_kickstart
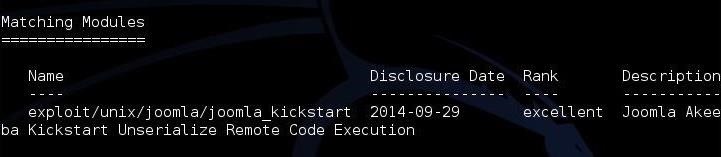
As you can see, Metasploit found our new exploit and it is ready to use! Now, let's load it for use with the use command. Type;
msf > use exploit/unix/joomla/joomla_kickstart
Our new exploit loaded successfully and is ready to start using. Finally, let's stake a look to see whether the options fields loaded successfully by typing:
msf > show options
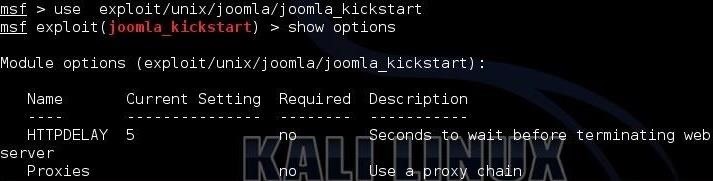
As you can see in the screenshot above, Metasploit responded with the options we need to set to use this new module. We are ready to begin exploiting Joomla with our new module!
We can use this same method to load a new payload, post exploitation, or auxiliary module (with the minor difference that the subdirectory would not be exploits, but rather payloads, etc.).
Keep coming back, my tenderfoot hackers, as we continue expand our knowledge and capability of the world's most popular exploitation framework.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























13 Comments
Lol, I was just thinking about how you hadn't posted in a while just before you posted this.
You mentioned this in the beginning but I would like to reiterate it before people try copying and pasting random exploits and it doesn't work. They have to be built for metasploit. Even if they are written in Ruby they still have to be built for metasploit.
How can you build them if the copy and past does not work bro. I am listening and i am really ready to learn
How would Veil work into this? Can you use payloads in the same fashion?
Winter, read the second to last paragraph.
Hey OTW,
I'd be very grateful if you could give me some suggestions on some decent books on hacking, more importantly the information gathering and reconnaissance part of the whole thing.
Thanks in advance and keep up the good work.
WGDVBS
VBS:
Thanks. Have you read all my reconnaissance and information gathering tutorials on Null Byte?
OTW,
I just remembered about those and now i've ended up with 20 or so open tabs ready to be read :D Anyway, I've always wanted some info source that has everything there is to a topic (in this case reconnaissance) in one place, so that's why I was asking for a book. I'll read all of the tutorials here and I might ask some more questions if I have any, so stay tuned and thanks a lot (also if you think there is in fact a book that might present some more information of great use on this topic, it'd be greatly appreciated :D)
WGDVBS
I don't know of any book that just addresses reconnaissance, but there are a large number of books on hacking on Amazon. Consider "Hacking:The Art of Exploitation". Its a classic.
Thanks again for your attention, I'll definetly get that book.
Live long and prosper.
Hello Im a Big Fan of your tutorials and i learnt a lot from then . I a newbie and have followed your guide since beginning. Now i have stuck in installing an exploit from exploit db site. I was good . the exloit was shown when searched but the problem is when i try the use command to use exploit , it shows me the error -failed to load module. I doont have ruby installed which i have benn suspecting as a problem, but can u tell me the real problem? And i run all of it on elementary os ( a version of ubuntu,pretty awesome and supports all tools from kali linux)
What about .py files? I saw a number of files in exploit-db written in python. Can we use those the same way you have shown for .rb?
Sir
I have been following your highly esteemed tutorials for my self pace CEH and i am doing so well so far and i like your tutorials.But i have one more huddle here.Any time i try to add new modules in msf it does not work.I have tried all from adding to the already existing modules in the metasploit-frame,but didn't work.I have also tried to add from ~/.msf5 folders that didn't work again.Any advice or is there something i am doing wrong....? I wanted to add new modules because the pre-configured ones are all and i need new ones for current systems like win7,8,10 server 2008,12,16 and all current OS and systems
Share Your Thoughts