Welcome back, my tenderfoot hackers!
Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.
Vulnerability scanners are notorious for throwing false positives. These are found vulnerabilities by the scanner that are not really there. If vulnerability scanners could accurately detect vulnerabilities, then who would need pentesters?
Among the most widely used vulnerability scanners on the market is Nessus. It has become a kind of standard for vulnerability scanners. Originally begun as an open-source project, it was purchased by Tenable and is now a commercial product. Despite this, Nessus still has a "home" vulnerability scanner that they give away for free, and you can use it for up to 16 IP addresses. That's what we will be using here.

As a hacker, if you can do a vulnerability scan on an internal network, you will have a database of all the potential vulnerabilities on the network. Then, you simply need to find the proper exploit to take advantage of it. Unfortunately, vulnerability scanners are very "noisy" and a vigilant security/network admin will detect it. Fortunately, not all organizations have a vigilant security/network admin.
Although Nessus has been around for quite awhile, the U.S. government has only recently switched over to Nessus for all their vulnerability scanning. Nearly every federal office and U.S. military base around the world now uses Nessus to scan for vulnerabilities. This could be useful information.
Vulnerability scanners are not perfect. They cannot detect zero-days, and like AV software, their database needs to be updated daily to be accurate. Probably the greatest limiting factor in using vulnerability scanners are the false positives. These scans may produce hundreds of potential vulnerabilities and usually less than 10% are actual vulnerabilities. That's why companies and institutions still need white hat hackers—to separate out the false positives from the true positives. When they no longer produce false positives, penetration testers will be unemployed, but I don't expect to see that in my lifetime.
As a white hat hacker/pentester, you need to be familiar with vulnerability scanners. Since Nessus is the most widely used one, let's try it out. For those of you who might want a vulnerability scanner that integrates into Metasploit, consider Rapid7's Nexpose (and see my tutorial on using it).
Step 1: Installing Nessus
To begin, we need to download Nessus from the Tenable website. Tenable does not make it easy to find their free, home version, but you can find it right here.
Tenable requires that you register to get their free application, so you will need to give them an email address to receive an activation code.
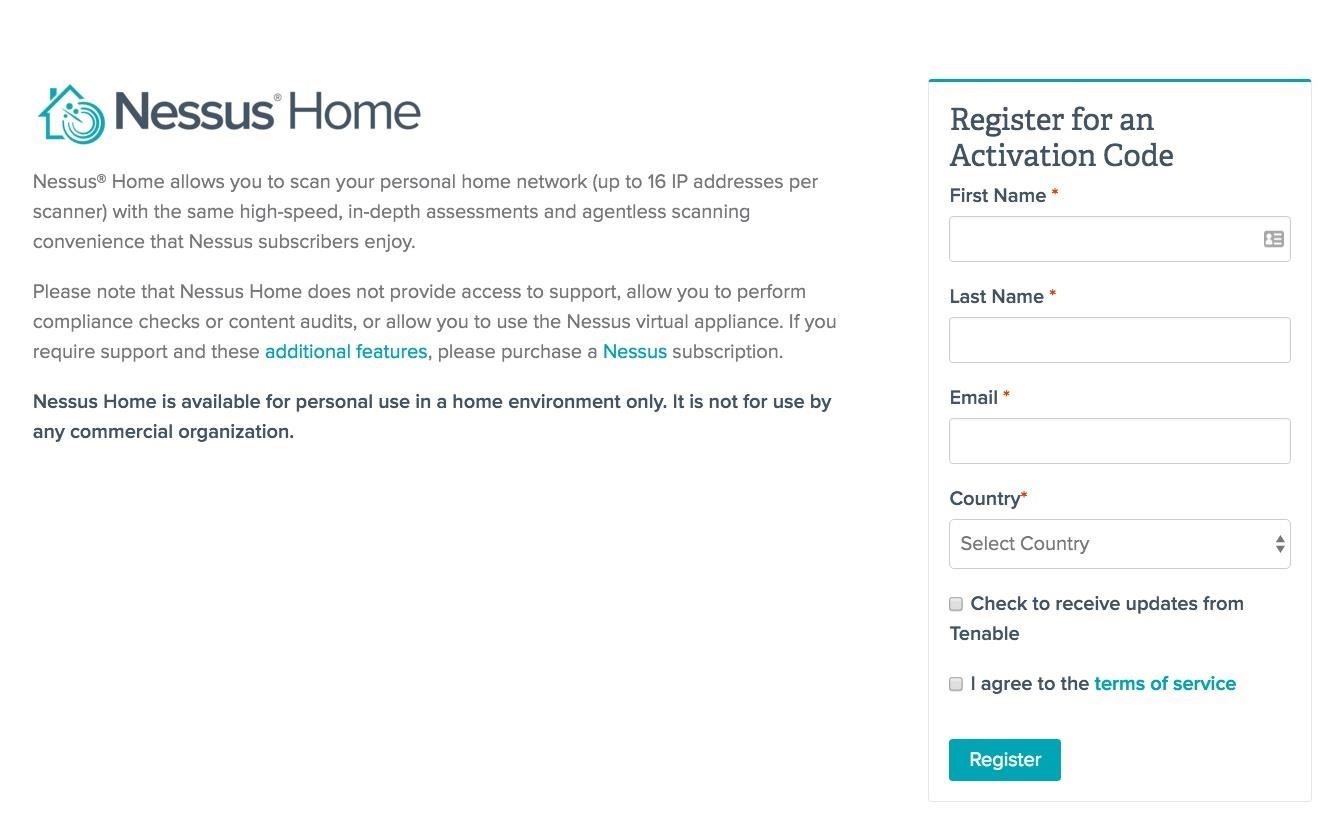
When you click on "Register," select the "Download" button to visit the downloads page, where it asks what operating system you are using. In my case, I downloaded the 64-bit Windows 7 version. Of course, download the version appropriate to your operating system and architecture.
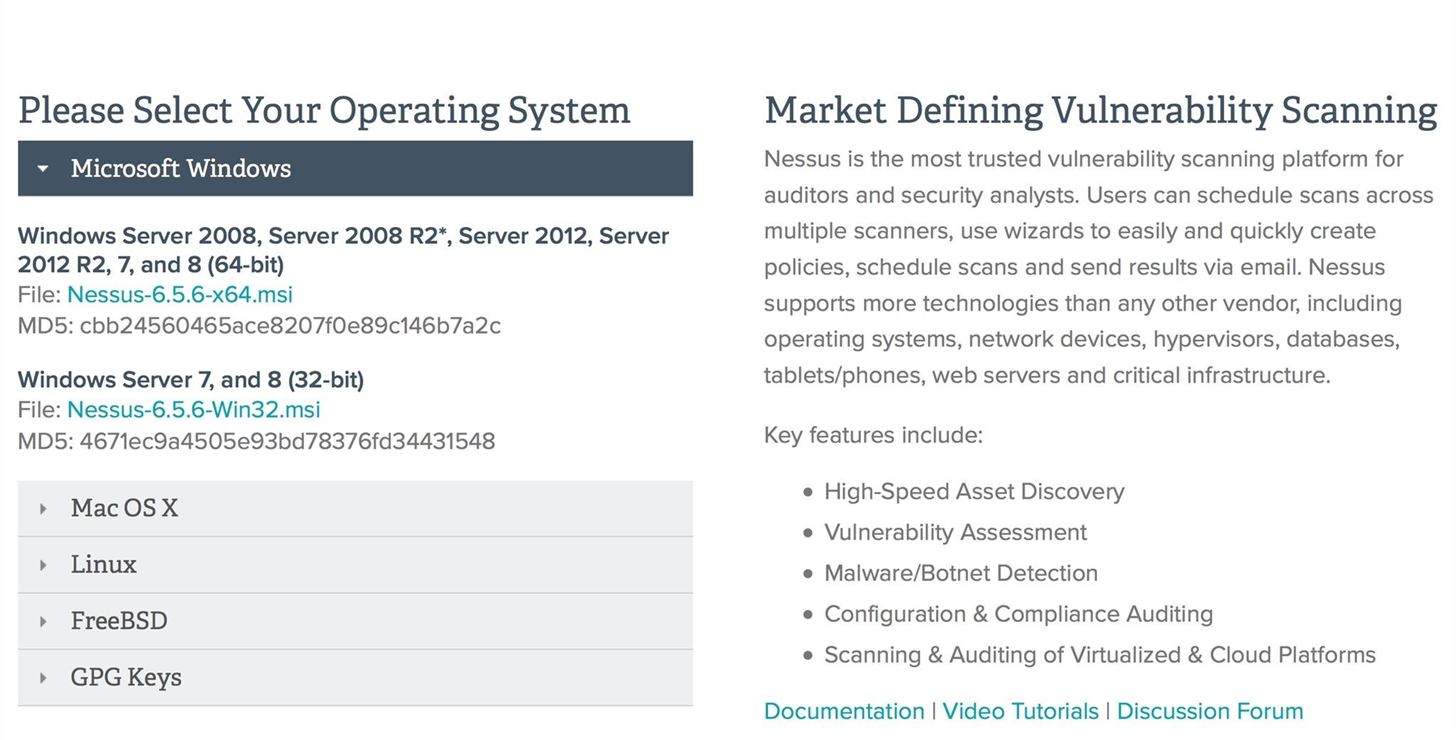
After choosing the right file, Nessus will download an installer package to your computer. Double-click on it, and it should be fairly intuitive from there to complete the installation process.
Step 2: Getting Nessus Working
After the installation is complete, Nessus will open your default browser with the message like that below. Nessus is built with a client/server architecture. You have installed your server on localhost and the browser represents the client. In reality, you can access the Nessus server from any system via a web browser.
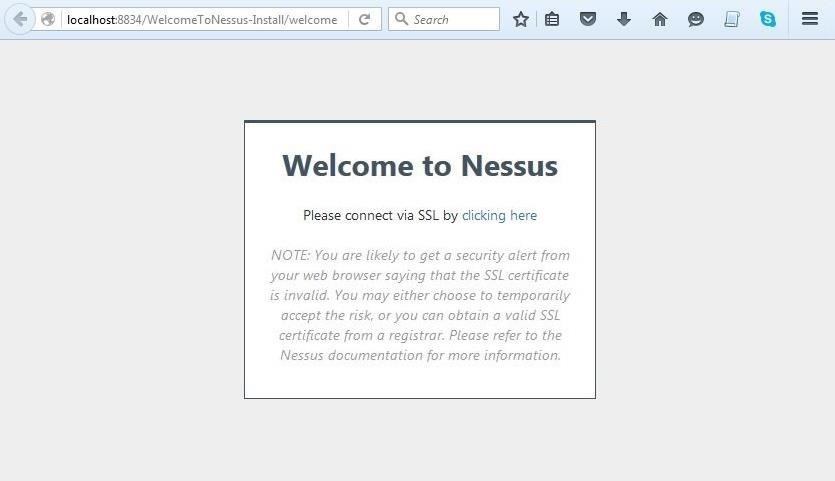
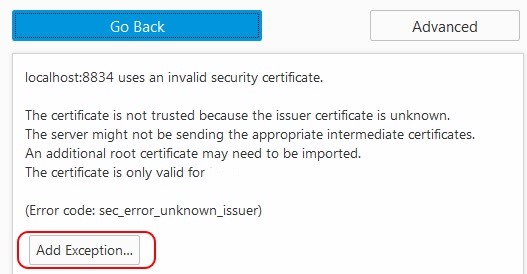
You are likely to get a message that says "Your connection is not secure." Click on "Advanced."
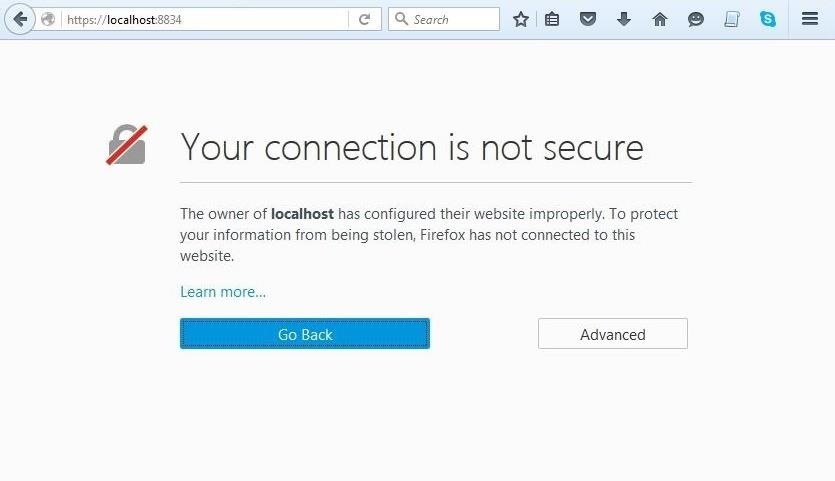
Then, enter an exception for the Nessus connection on port 8834.
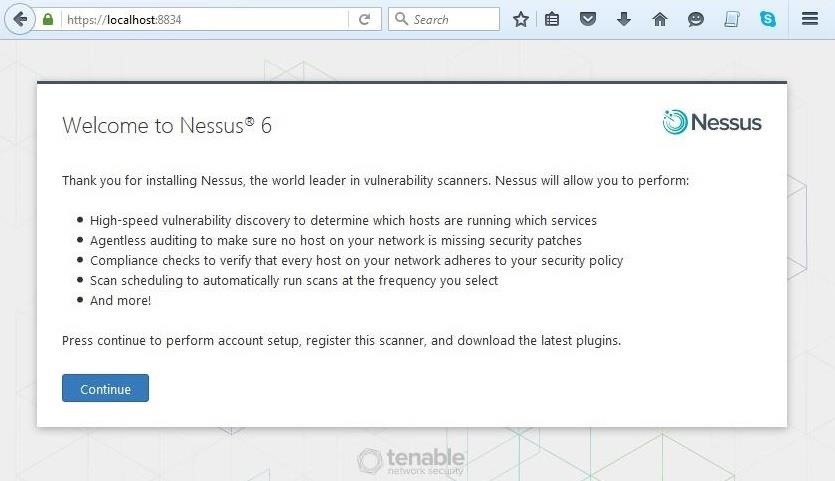
Step 3: Setting Up Nessus
Now we are ready to start using Nessus to find vulnerabilities.
You will need to first set up an account. This is the account that you will use to log into the Nessus server.
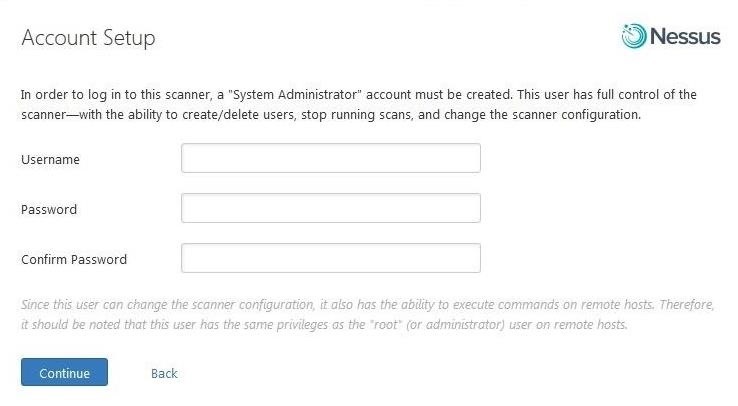
After entering your username and your password (this username and password is only for Nessus), you are ready to activate Nessus. Go back to your email and retrieve the activation code that Nessus sent you and enter it when prompted.
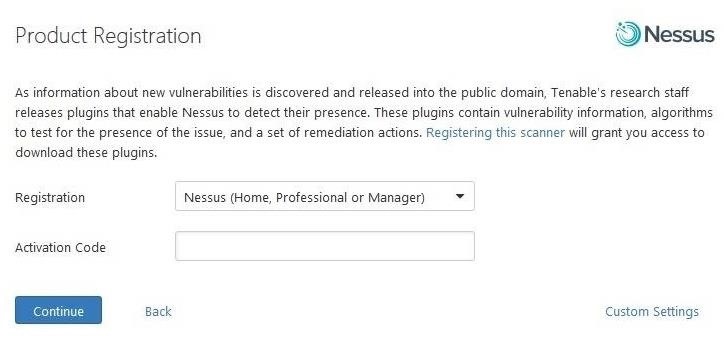
When done, Nessus will begin to download all the updates and plugins necessary to find vulnerabilities on your network. Be patient, as this can take awhile.

Step 4: Starting Your Vulnerability Scan
When Nessus has completed its update, you will be greeted with a screen like that below. Click on "New Scan."
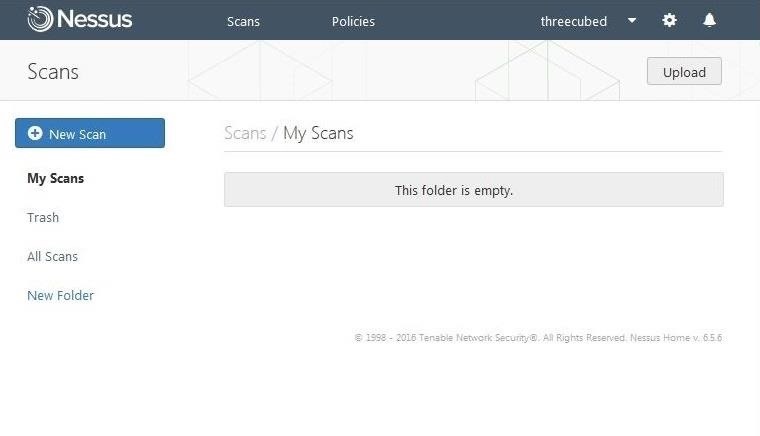
This opens a new screen giving you choices as to the type of scan you want to execute. Note that some of the scans can only be done with an upgrade. Let's click on "Basic Network Scan."
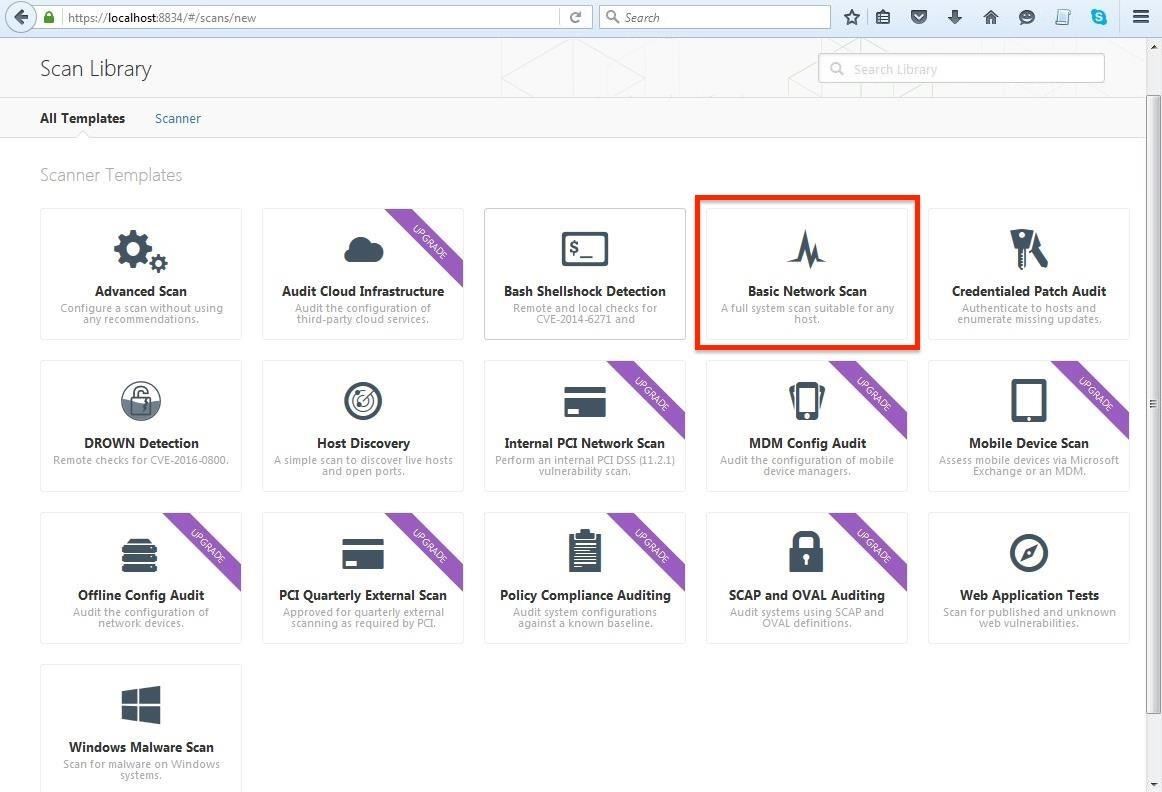
This opens a screen like that below, which asks you to name your scan and enumerate your targets.
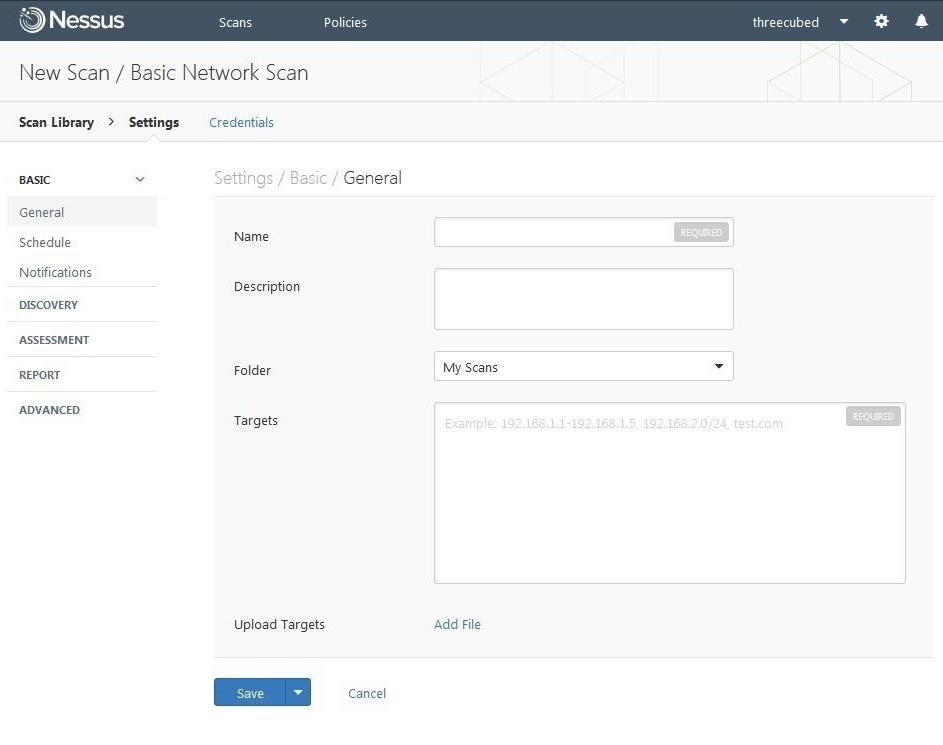
I simply named it "First Scan" and had it scan my local network at 192.168.1.0/24. You can name yours whatever you like, but make certain to use the IPs on your network, then click "Save."
Now, click on the "Launch" button to start the vulnerability scan.
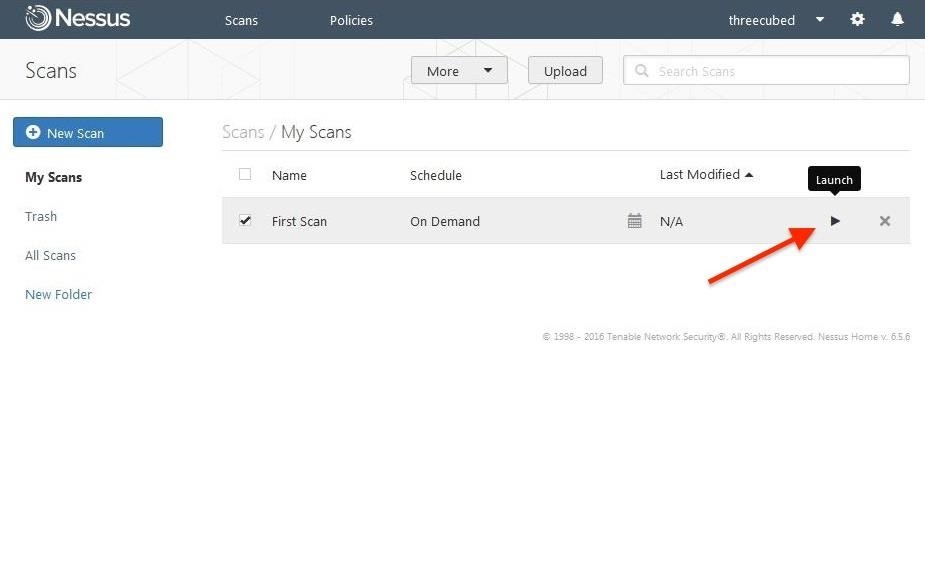
Step 5: Viewing Your Vulnerability Results
When the vulnerability scan is complete, it will list each of the hosts by IPs scanned, and the associated risks to each. The risks are color coded, with the burnt orange being the most critical.
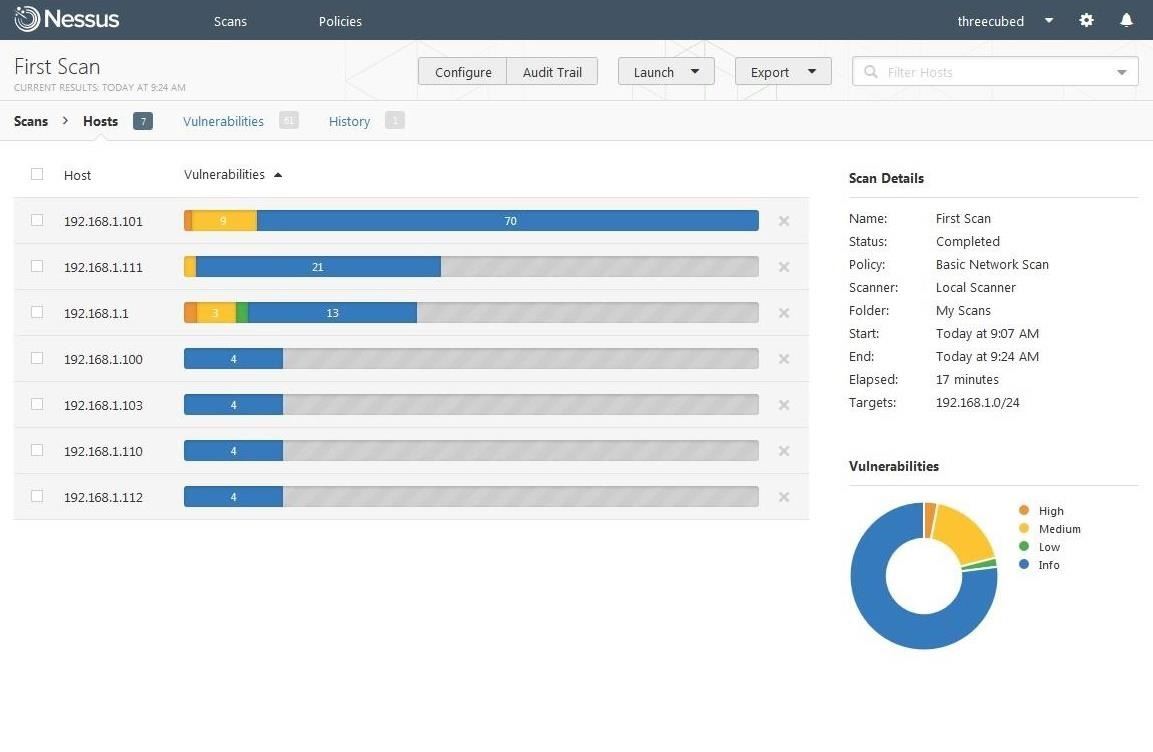
Click on "Vulnerabilities" in the top-line menu to display all the vulnerabilities found on the network.
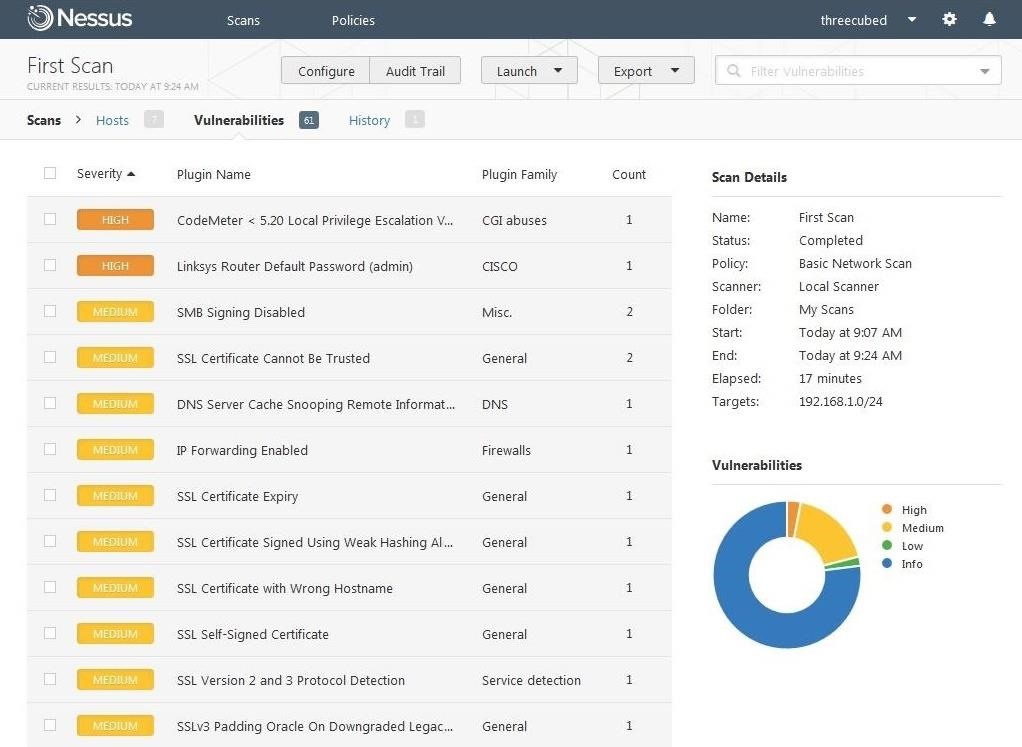
When an individual vulnerability is selected, it displays more detail on that particular vulnerability. My "CodeMeter" vulnerability is shown below.
Finally, results can be saved in several different formats for reporting purposes. Click on the "Export" tab to pull down a menu with:
- Nessus
- HTML
- CSV
- Nessus DB
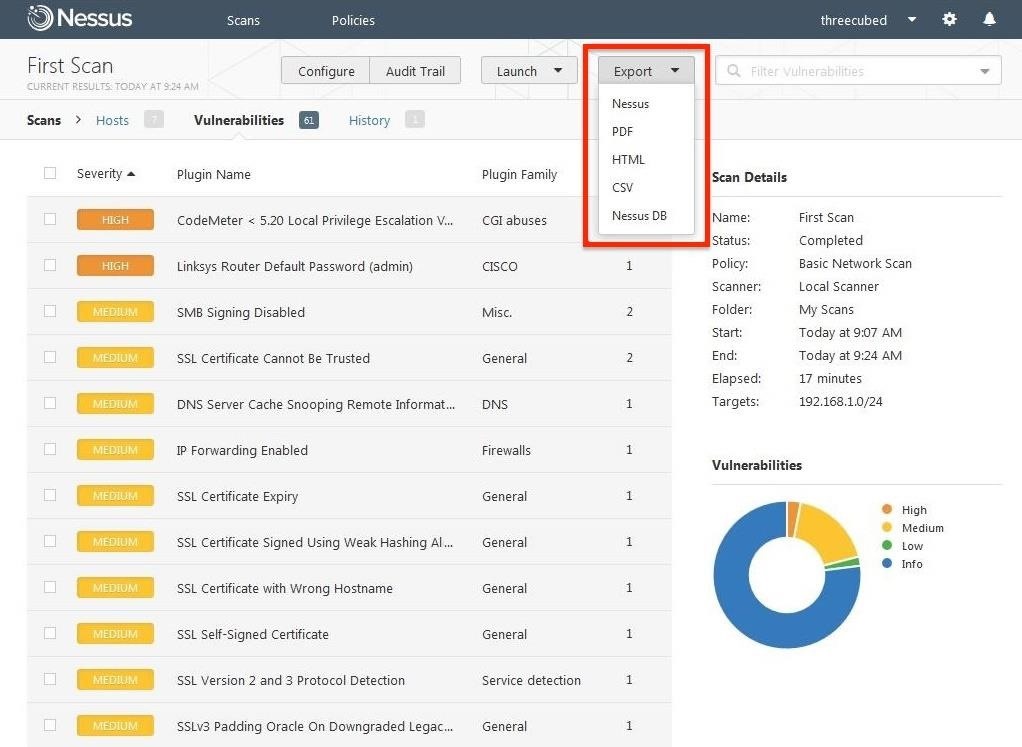
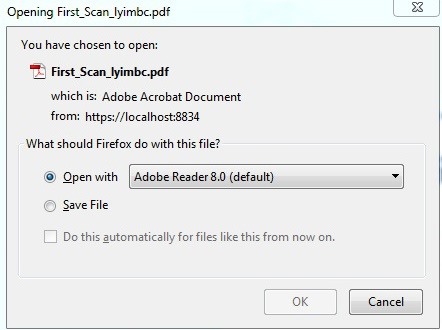
In my case, I chose PDF; a menu pops up with the name of the file, and asks which program to open it up with.
Nessus has become the de facto standard in vulnerability scanners, and every white hat hacker should be familiar with it. It is capable of finding known vulnerabilities, but its limitation, like all vulnerability scanners, are false positives. Once the white hat hacker has this list of vulnerabilities, they need to test each of them to determine if they are actual vulnerabilities or not.
Keep coming back, my tenderfoot hackers, as we learn the technologies and techniques of the most important skill set of the 21st century—hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















9 Comments
Thanks for the tutorial, but why do you say it is reporting false positive sometimes?
Also OTW , i was reading in another post that you said you were going to make a serie about mobile hacking ( i mean hacking with a rooted android phone ).
Are you still going to do it?
Thanks for all your tutorials.
All vulnerability scanners report false positives.
I will be starting a series on hacking mobile devices soon. Hacking with mobile devices is still a ways off in the future.
Thanks i look forward to this serie.
you think its in the future by rooting your mobile devesi makes you an aministrator on any wifi intercepter-ng ,csploit kali NETHUNTERyoull be like the watchdogs
stop thinking thats in the future you dont even know the power of rooting and hacking every device can turn into a hacking device every devise runs the same algorythm there for i can install windows on android device this called programing
i have lots of skills i used linux for a year i know allllllllllllllllllllllllllllot of attacks as you see dont say something you think is true do some research
How long is the basic scan supposed to take?
I started it on a 15-device network and it's running for over 5 hours now.
I have the feeling that that can't be right.
5 hours sounds a bit excessive, but it can take awhile.
quick question for you.
I know the Ip ranges on my network, no problems there. How would I go about scanning another Network, as in how do I get their IP. The reason I ask, is because the capstone project of this term is an end of course project where I will have to employ techniques learned class to take down, or gather as much info as I can on a server our professor has set up. Im working ahead of course, but I would like to get a jump on learning how to scan it for vulnerabilities. I dont know if he will give us the address of that server or if we will have to find it on our own.
Hi i installed nessus on kali although when i try to start it i get Nessus has detected a corrupt database and it says replace the global.db file which i have done although it still does the same, ive tried reinstalling it and still the same anyone know a fix ?
I have complete phpinfo() of a website. Can anyone tell me how can I hack it?
Share Your Thoughts