Greetings fellow students!
I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"
This book will teach you different kinds of Python programs for hacking, forensics or penetration purposes ! ( Good or evil, just what you make of it ;) )
Now i feel obligated to post some of the scripts that haven't been posted on this website yet, so you guys might learn more about making your own scripts! So without further ado, lets begin!
As you guys know the basic unix passwords are stored in the /etc/shadow file, which is only readable by the root user. Now you might be thinking "what if i just download the file and read it" ? Wouldn't that just give me the credentials i need to explore the victim's machine? Well... No. The thing is: it's encrypted so that people couldn't just open the file and read your password! "phew" ...So is that it? Is there no way to get the password now? Well actually, you can accomplish your mission in a lot of ways!
The password is encrypted with a salt and the hash. Now you might be wondering if i ment the salt in the kitchen, No i dont hehe.. A salt is basically a 2-character string which will be used to select one of the 4096 variations of DES ( Data Encryption Standard), an outdated encryption way. Let me give you an example of how this work! Open your IDLE, Gedit or whatever kind of writing program you use!
Import crypt
crypt.crypt("turtle","HX")
"HX.t7090XWhTI" # As you can see the HX is the salt, and the rest is the hashed password! See how this work's now? If you use a dictonairy attack to make each word in the dictonairy a hashed password it will compare the hash of the password in the /etc/shadow and compare it to the hash in the dictonairy. Lets begin writing!
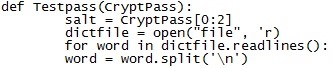
# We started by defining a function called testpass that take's one argument / variable called (CryptPass)
After that we just wanted to make sure that the salt is the first two of the cryptPass: salt = Cryptpass0:2
# Next we open the dictionary file we will use open("fileName", 'r) # The R stands for read only .
# For each word in in the dictionary we want to know it's a new line. So it wont encrypt all the words in one,we do that by using ('\n')
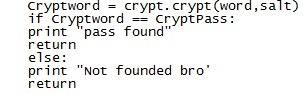
# Next we define a new variable called Cryptword and give it the data : crypt.crypt(word,salt) This is encrypting the words in the dict.
# Now if the CryptWord is equal ('==') to the CryptPass. That means that if the hashed word and the salt is the same as the passwd in the passfile. Then it means that the password has been foundd !" wohoo!"
# Return so it doesn't continue going true the dict file. because you already founded the pass!
# otherwise it continues true the list and if the pass aint found it prints "That the password hasnt been founded".
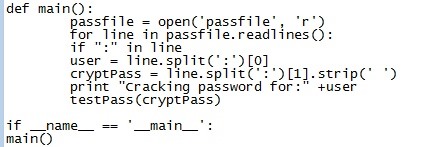
Here we have defined a second function called Main():
# the first line opens the Passfile in read only mode.
# Now it is going to read each line in the passfile.
# Whenever there is an colon ": " in the line.
# You want to save the first word before the colon in the variable "user".
# user = name.split(":")0 means that its splitting the username and the password. which is split by the colon!
If you havent checked your /etc/shadow file ever. This is how it basically looks like:
Root:HX59284UR
Username:HZ48252UR
# The user is always before the colon, and the hashed pass always after the colon.
# That should clear up the user = line.split(":")0 alot better !
# After that it does the same as the user variable. But instead of grabbing the 0 first word in the passfile name, this time it is going to grab the second one 1 .
#Remember, in the computer word it always starts with a zero.
the .split(' ') is just to make sure that there aren't any spaces between them.
# And as you can see. You print " Cracking pasword for: "+user
And that is how you make your own UNIX DES password cracker!
This is the first 'How to' I've made. so be gentle :D , if there is anything I didnt explain right or downright made some errors, please let me know! I'm just a student myself, not a master :)
Now ofcourse this DES is outdated and if I'm correct they use SHA-512 now. I will be doing another tutorial on how to make the script for the SHA-512 encryption :)
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















5 Comments
Very nice guide!
Thank you :)
Great tutorial!
I gotta say I love that book, Violent Python.
It's great for hacking on the fly.
can you post on how to execute this python script using some crypt hashes.
i cant seem to get mine working. Giving me errors on line 5
Share Your Thoughts