In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!
With this article, I am going answer those questions and better explain the pros and cons of each, breaking down the networks, pitfalls, and things you should know to be safe. But first, let's take a brief jump back into the Deep Web to better explain these tools in order to give you the knowledge to make more informed choices.
Back to Onions
Tor and I2P are both anonymizing networks, allowing people to tunnel out of their open and non-secure environments. However, they achieve this in slightly different ways.
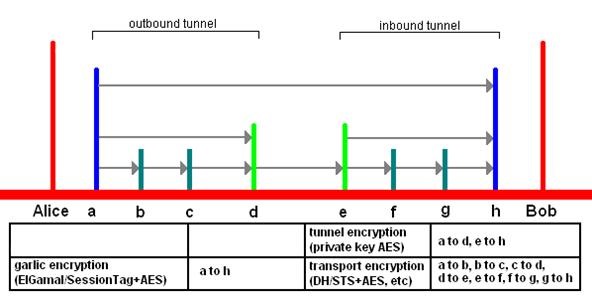
As a quick recap, onion routing involves wrapping your packets in multiple layers of encryption, in a system where each router that passes it along only has the key to decrypt its layer and none of the others. This way, each router can only see the router that sent it the packets and the router it in turn must send the packets to. It's how this is performed that draws its contrasts. Let's take a look at each in more detail.
Tor
Tor has been around quite a while longer then I2P. As a result, it has been studied much more in depth by both the white hat and black hat communities. In my Tor article, I mentioned it was better designed as an out-proxy than I2P is. This is because there are many more exit nodes on the Tor network then on I2P, and with the ability to use TLS and bridges, Tor also performs better at evading state-level firewalls (think China and Iran).
The only reason anyone would be changing the I2P config would be to set up port forwarding, and that's a bit out of this article's scope (though a great idea for a future one). Tor is a simple SOCKS proxy, so your only choice is to be a relay, exit node, or client node. Tor also has advantages in that it holds a large number of talented developers, some of them are even funded. In fact, Tor receives a good amount of money for its maintenance and development, and this shows in the form of its excellent documentation and white papers.

On that note, Tor is written in C, as opposed to I2P's Java. This means that the Tor client typically runs faster and with a smaller memory footprint.
Tor takes the directory-based approach, providing a centralized point to manage the overall 'view' of the network, as well as gather and report statistics, as opposed to I2P's distributed network model. This centralization reduces complexity at each node and can efficiently address Sybil attacks.
I2P
I2P was designed with the internal network in mind. Steps have been taken to provide a better environment for hosting services rather then providing out-proxies. This is the fundamental difference between I2P and the Tor network. I2P was designed and optimized for hidden services, which are much faster than in Tor, as the network is fully distributed and self-organizing. Helping this is the fact that peers are selected by continuously profiling and ranking performance, rather than trusting claimed capacity.
I2P is packet switched, instead of circuit switched, like the Tor network. This means transparent load balancing of messages across multiple peers, rather than a single path. Essentially, all peers participate in routing for others. Also along these lines, I2P's API was created for anonymity, unlike SOCKS, which is designed for functionality. As Tor uses SOCKS, I2P tends to fare better for security than Tor, but keep in mind most people will not have a threat model where this would be of concern, as attacks tend to be highly complex.
Lastly, tunnels in I2P are short lived, decreasing the number of samples that an attacker can use to mount an active attack with, unlike circuits in Tor, which are typically long lived.
What Is Best for Me?
That's a very open ended question. At times, it falls to a technical choice, an example being P2P file sharing over I2P, where as Tor does not support (nor encourage) it. Other times it depends on your personal choices. You will find the content on the Tor and I2P networks to vary. It is not to say you should not host services on Tor, or should not out-proxy with I2P, but the networks are designed with different strengths in mind.
Perhaps the answer to the question is what I do. I use both.
Generally, if you are looking for a robust SOCKS out-proxy, Tor is a great choice. Granted a number of exit nodes have been blacklisted to prevent abuse, the network still has plenty more.
If you want to host hidden services, then I2P would be your better choice, as you are afforded the added protection of decentralization and higher speeds to go along with it.
Shortfalls
Using these tools, you are only as anonymous as you allow yourself to be. Doing things like logging into your personal Facebook account or checking your personal email while using these networks will remove a good chuck of what is protecting you and keeping you safe. It's wise to keep a few guidelines in mind:
- Think of your 'clear' net identity and your darknet identity as two separate things. Do not mix the two.
- Avoid using any personal information or distinguishing remarks on the network—remember to be someone else. Don't leave clues as to who you really are.
- You should never use your normal browser to view resources through the networks, only use the bundled browsers, or manually turn off those services. Flash and Java are especially good at betraying your location and IP address to servers. Turn them both off.
Tor Exit Nodes
A brief word about exit nodes.
An exit node is a machine that sits on the edge of the darknet. It acts as an intermediary between yourself and the outside Internet. As such, the exit nodes are routing all sorts of unsavory traffic, pretty much all the bad things you might expect to find hidden on a darknet. While Tor does give you the option to function as an exit node, unless you wish to have a talk with the police, leave it alone.
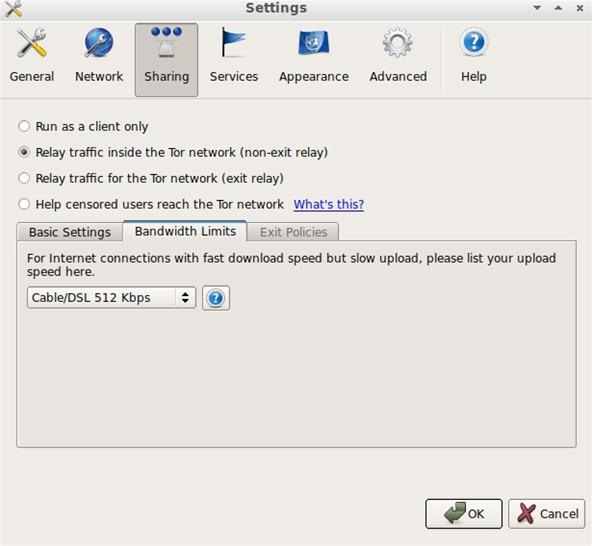
In this case, what you can choose is a non-exit relay. This lets you help with forming more random and unique routes on the network. Helping your mates browsing along with you by giving them more security all while speeding up your own traffic. Why you are on this screen, you can change your bandwidth settings to reflect your capabilities as well.
Now, I want to hear from you!
What do you use Tor and I2P for? Do you like one over the other? Why?
As always if you have any comments or questions, please let me know in the comments below, visit our forum, or come say hello in our IRC channel!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























6 Comments
I didn't get what an exit node is. Can someone clarify?
I guess another simple way to look at it would be to picture the exit nodes as internal proxy servers. They handle your traffic when you are trying to view a resource outside of the network, to protect your true identity.
[you]-----[exit node]-----[non darknet resource]
Ah that helps. Thanks!
an exit node is the computer which fulfills the original URL request, which may be of an unsavory or illegal nature. Imagine the network as this.... You are computer A and send out the url request, which is encrypted in layers. Computer B (somewhere else in the world) recieves the request and can see from whence the request came (you) and can see where to send the encrypted packet of data (Computer C), but it CANNOT see the data itself or the nature of the request. Computer C (somewhere else in the world as well) can view the the fact that it came from computer B, but cannot see computer A (which is you, who originally sent the request). Computer C can see to send it to Computer D. Computer D knows that the request came from C, but has absolutely no idea the I.P addresses of B or A (i apologize for being redundant but it is the manner in which this technology works- B, C, and D are known as "relays") Computer D would then send the information to E, which is the exit node, or the computer that decryptes the request and finds the server with the information of which you seek. This is why it is called the onion router- because an onion has layers (remeber that it- theoretically, is only the exit node which is able to decrypt your request!). It's a technology originaly created by the United States Navy. I hope this helps you out!
Hello Allen, a rookie here i already have tor and i use it to access sites like kat.ph and thepiratebay.org that has been blocked in my country...p2p sharing has been blocked on my university network..and thats where i pass the whole day...is there are a way i can use this I2P to to make my uni network not block my utorrent from having the net? bear with me..am a complete noob...but eager to learn
am tired of paying for vpn :P
Share Your Thoughts