Hello friends. This is actually my first how to.
In this tutorial I'll be teaching how to simply copy someone's WhatsApp pictures gallery into your computer, in an automated way. It is just an example of how easy is to steal data from someone's smartphone. I am covering WhatsApp because almost every smartphone has it installed, and it can contain valuable and sensitive information about a target, like screenshots of important conversations. However, the script can easily be modified to fit your needs. I must consider saying that I do not take any responsibility from the misuse of this tutorial. Try it at your own risk.
For this tutorial we'll need:
- An Android Phone (Target's).
- An USB cable.
- A BASH script that runs in background.
For learning and testing you should use your own Android device, I'll be using mine also.
Step 1: Building the script.
This tutorial doesn't require much understanding of BASH scripting, although I recommend you to read these great series, Mr_Nakup3nda's and OTW's, about BASH programming. Let's begin.
We need to create a directory to save our acquired data, so we use the mkdir command. I choose to save at Dropbox slash dot happy face. Beginning with a dot it becomes a hidden directory, so a normal user won't notice if him browses at my Dropbox folder. But you can choose your own destiny folder. Additionally, I'm redirecting the standard error output (2>) to /dev/null, so if we get an error, like the directory already exists, it will be suppressed.
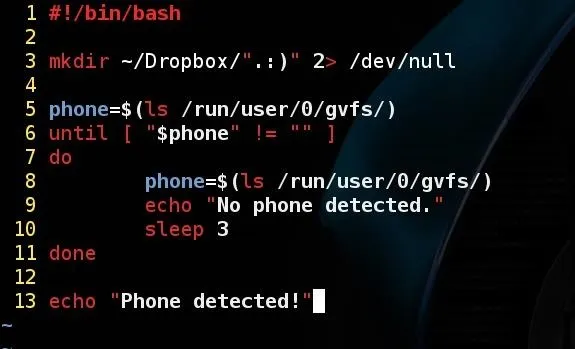
On line 5 we create a variable called phone and assign it to the output of the command ls /run/user/0/gvfs/. This is the directory where my Android phone appears when I plug it in my computer through USB cable. In other words, is the directory where the Android is mounted on my computer. I'm using Kali Linux 2.0, It may vary depending on your operating system. To check which directory it is mounted on your computer, do the following: plug your phone in your computer with USB, enter in it's directory, then right-click anywhere and finally, choose "open in terminal". Some Linux distributions doesn't have this option, but you still can enter in it through command line. Try it out.
If you had no trouble finding this directory, we can move on. Still on the screen shot above, we create an until loop. It's similar to the while loop, that keeps repeating until it fits my condition, in this case, until the phone variable is no longer an empty string. I've said previously that our variable phone has the output of the ls command. If there is no phone connected on the computer, the variable value will be an empty string. Then we say to print a message while it is in the loop, and another message when it exits. Since it will be executing 'forever' I told it to wait 3 seconds before loop again with the sleep command, but you can change it's value.
Now, following our logic, the script must exits the loop after we plug in a phone. Let's test it out! Remember to give it execution permission with chmod +x. I am with zero creativity at this moment so I've named the script got_you.sh.
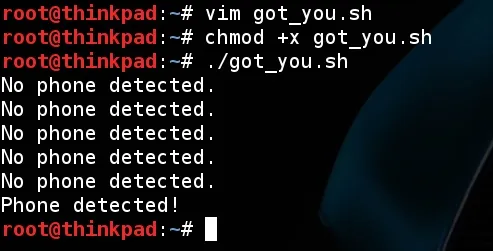
After I executed it, I waited a few seconds then plugged in my phone and it printed out what I was expecting! Our script work! But... The Android system only allow you to make file manipulations if the phone screen it's unlocked. So, we won't get anything from Android while we are facing something like this:
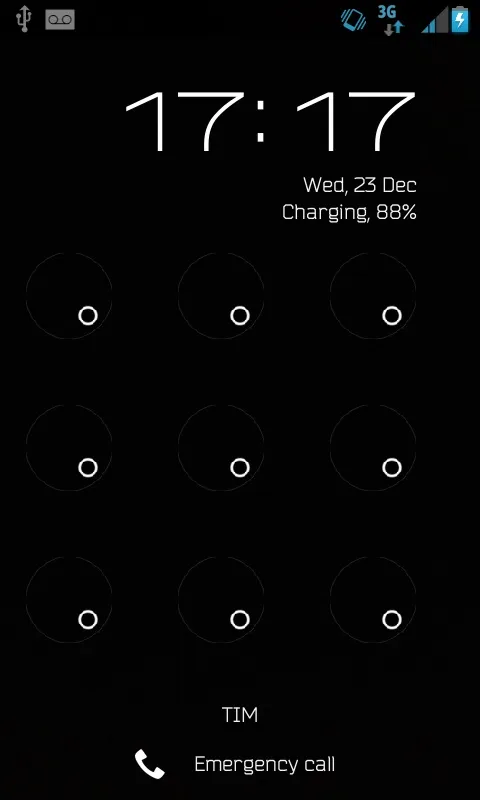
This is where the social engineering will be entering. But let's get back to our script. We could tell it to copy the desired folders, but this would be useless if the phone is locked. So we must assure that it is unlocked first.
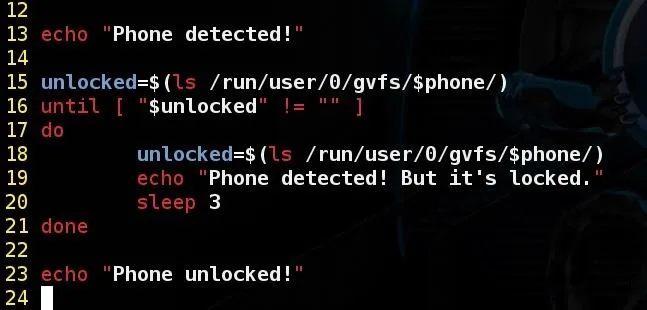
Continuing, this block of code do the same thing we've done before, but now we are assigning the variable unlocked to what we've found after the /run/user/0/gvfs/$phone/ directory (Or the one that appears on your Linux). To illustrate, if the phone is locked it would be appearing like this:
If it is unlocked it will show up like this:
Now it should exit the loop and print the expected message when someone unlock the phone. Lets test it again and see what happens!
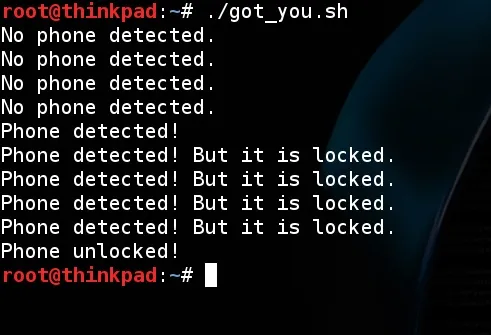
It worked as expected! Printed that was unlocked when I unlocked it. Now we can tell it to copy anything from the phone, including WhatsApp encrypted backups. I'll be covering just the images folder on this tutorial, but feel free to modify it. Moving on.
"GVfs (abbreviation for GNOME Virtual file system) is GNOME's userspace virtual filesystem designed to work with the I/O abstraction. ... GVfs comes with a set of back-ends, including trash support, SFTP, FTP, WebDAV, SMB, and local data via Udev integration, OBEX, MTP and others. ... There is a set of command line programs starting with "gvfs-" that lets you run commands (like cat, ls, stat, etc) on files in the GVfs mounts."
Now that you know a little about gvfs, you should now that your phone (or the target's) will be running at one. Therefore, we won't be using the cp command but gvfs-copy.

It works almost identically to cp, including the same syntax: gvfs-copy <source> <destination>. One difference I've found is that it can't copy directories recursively, so we must call it twice, for 'Images' and 'Sent' directories. Note that in my path to WhatsApp folder there is '/Phone/WhatsApp/...', the 'Phone' word is not the same as the phone variable. It is whats your phone labels it, and it may vary depending on the phone vendor and the language settings. For example, it could be 'Internal Storage', so adapt your script to the scenario you are in.
After adding those lines, test it out!
Step 2: Running in background.
If you tested the script at this point, you've seen that it worked like magic! We've successfully copied the images from 'images' and 'sent' folders (If it did not worked for you, tell me on the comments so we can find a solution together). But it kept printing messages that we don't wan't our target to see, so you can remove the lines with the echo command. I let just one on the bottom of the script, so I can know when it has finished
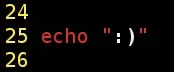
To leave it working, you should run it passing the character & at the end of command for making it run in background, this way:
I recommend you to run the clear command after, and then keep using your computer normally. Or just minimize the terminal. Or even don't use your computer at all, to not raise any suspects.
Step 3: The social engineering.
I must say that I'm awful in social engineering, so this part is up to you. We've built the script and it is running in background, the only missing thing is to actually connect someone's phone on your computer and make them unlock the screen. You can offer the target to charge his phone and hope he unlocks it after a while. I've warned you I was horrible.
Conclusion.
Firstly, thank you for reading. We've seen how easy is to acquire some data from an smartphone with a little of social engineering. I repeat that you should use this tutorial at your own responsibility. Taking someone's data from their device without their consent is considered ilegal in my country, I bet it is in your's too. Stay out of trouble.
Merry Christmas, and see you later!
As a side note: If a site admin is reading this I would like to ask for sending me an email verification link, because I haven't received and now I can't answer PMs. Grateful in advance.

























Comments
Be the first, drop a comment!