Welcome back, my aspiring hackers!
In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.
In earlier posts in this series, we examined registry files and what they can tell us about what the user was doing when their computer was seized. Windows has another type of file system that can also reveal a treasure trove of information about the user before the machine was seized for examination—the prefetch files.
Prefetch System
Obviously, Microsoft did not implement the prefetch system for forensic analysis, but rather to improve the performance of Windows. The prefetch system does what its name implies—it prefetches files that the system anticipates the user will need and loads them into memory making the "fetch" of the files faster and more efficient. It's a type of artificial intelligence that attempts to anticipate what you will need next and gets it ready for you.
The beauty of the prefetch system in Windows is that it can reveal much information about what the user was doing even if they are smart enough to try to cover their tracks. Prefetch has been part of the Windows operating system since Windows XP and 2003 (those are the same build), and it is enabled by default through Windows 10. On the server side, Windows Server 2003, 2008, and 2012, application prefetch much be enabled in the registry.
These prefetch files contain metadata about the files used. This metadata includes information such as the last date the application was used, where the application files were stored, how many times the application was used, and several other pieces of useful information to the forensic investigator. This can be critical information in trying to prove that a suspect actually used an application that was involved in the crime, such as the browser or document creation software such as Word, even if it has been removed from the system.
Location of PreFetch Files
You can find the prefetch files under C:\ windows\prefetch. Here is an example of the prefetch files from a Windows 7 system (still the most widely used OS in the world).
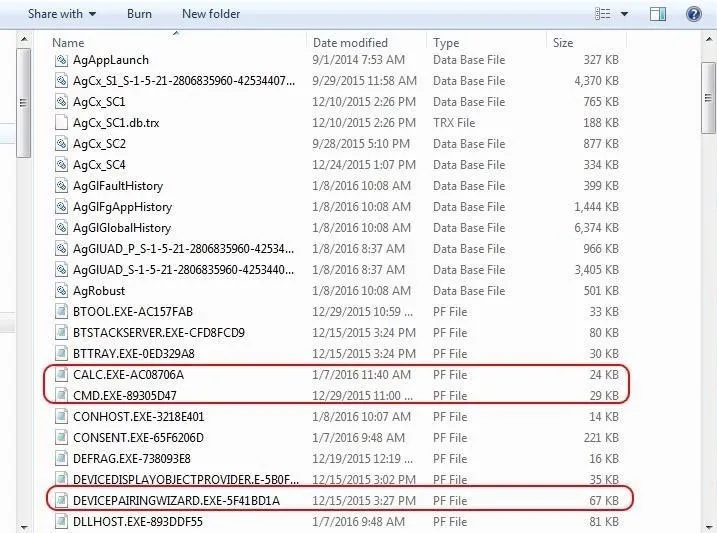
As you can see, in this \windows\prefetch directory, we can see all of the prefetch files. These are the files ending in .pf, but we can also see database files (.DB) as well. For now, let's focus on the .pf files.
In the first group of circled files seen above, you can see the prefetch files for both calc.exe and cmd.exe. In the next column, we can see the last date they were modified, which usually means the data those applications were last used.
In the second highlighted area, we can see the prefetch file for the "DEVICEPAIRINGWIZARD" executable. Note that it was last used on 12/15/2015. This is the Wizard used for Bluetooth pairing. You might imagine a scenario where a suspect might have claimed that they had never used, nor knew how to use, Bluetooth paring that was used in the crime. This file would clearly argue against such a claim in court.
Analyzing Prefetch
Although we can get some basic information by simply viewing the prefetch files, we need to parse the file to get all the information it contains. There are numerous programs capable of parsing these files and all of them work pretty well, but Nirsoft's free WinPrefetchView is about the easiest to use with a nice, intuitive GUI (most of the forensic suites such as EnCase, FTK, and Oxygen are also capable of prefetch parsing). You can download it in either 32-bit or 64-bit.
Simply download and install it, then run it. It will grab all the prefetch files and parse them like below.
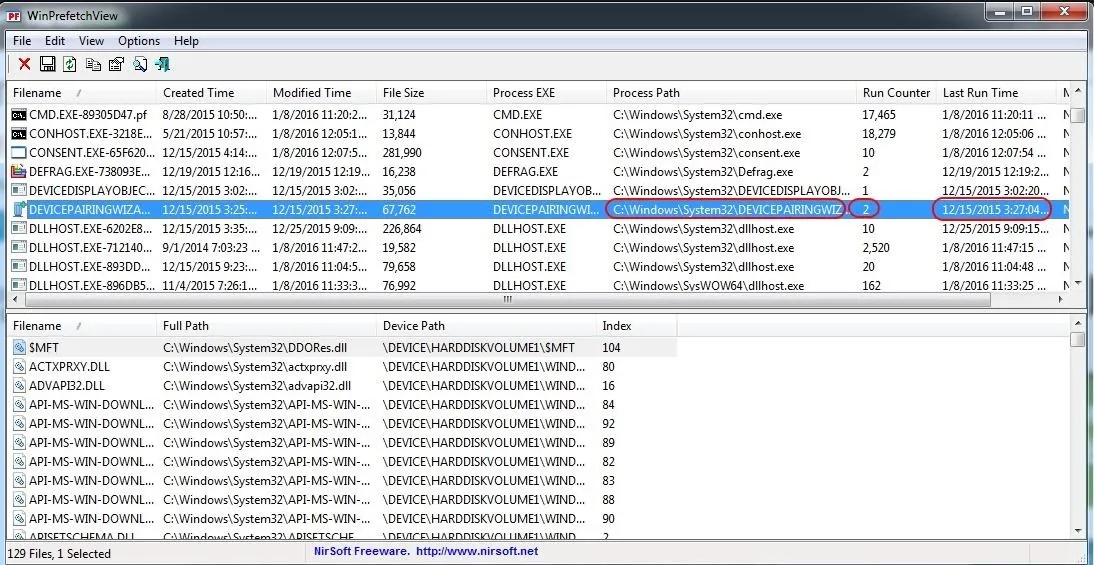
Let's take a look at that Bluetooth Device Pairing Wizard. I have circled it in the screenshot above. We can see where the path to the .exe is, the number of times it has been run, and the last time it was run. This could all be critical information in a forensic investigation. Also note in the lower pane that it lists every file used by the program with a path to the files.
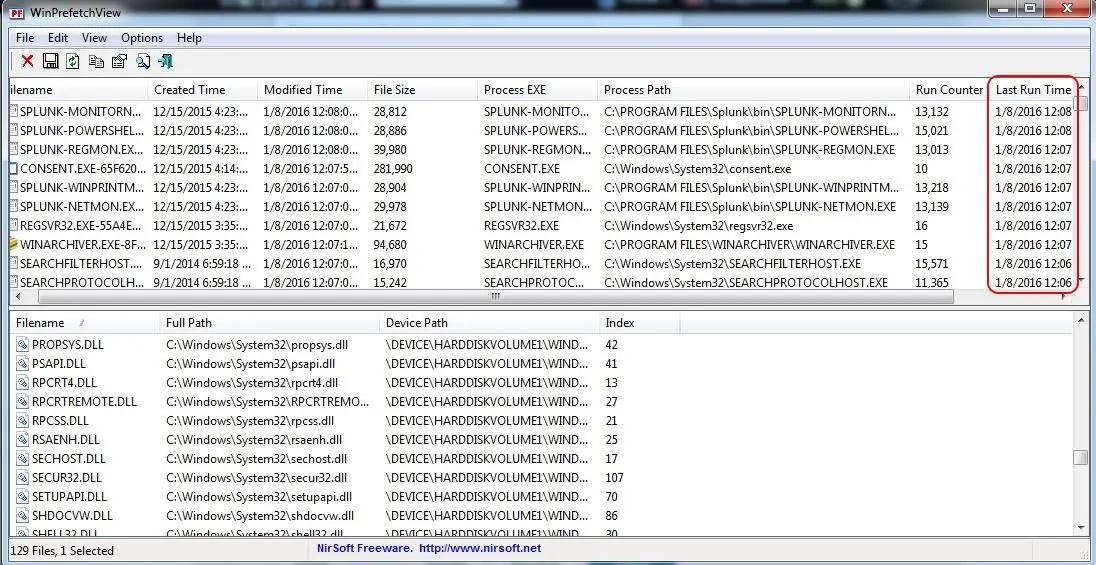
If we click on the "Last Run Time" tab to sort by time, we can recreate a timeline of events that took place on that system.
Disabling Prefetch & Superfetch
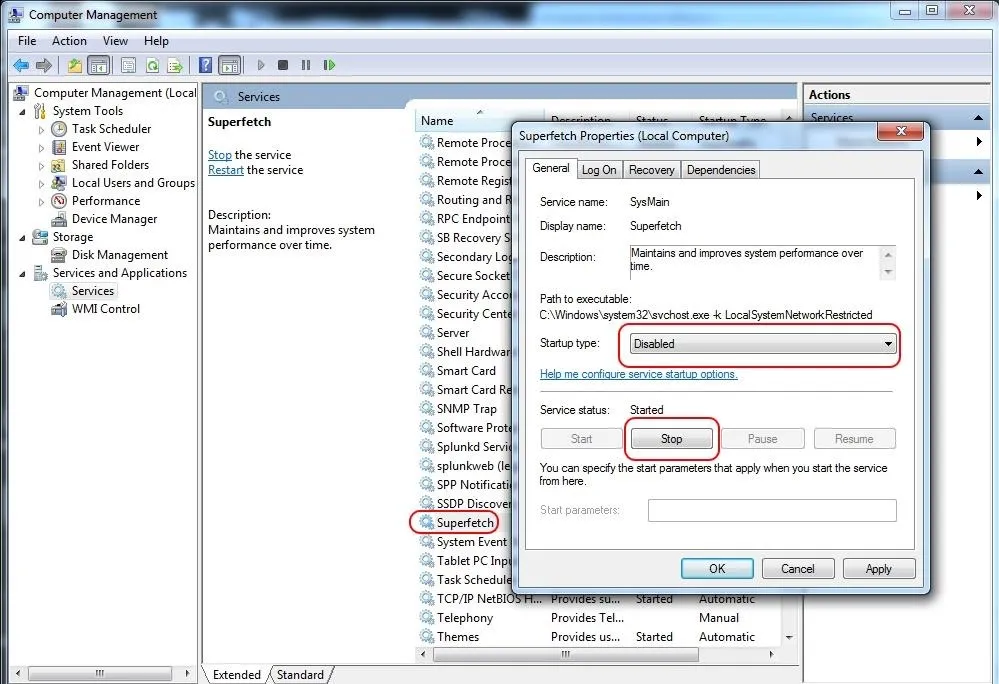
If the suspect were really digitally savvy, they could disable prefetch. They could also disable, or stop, superfetch, which was introduced with Windows Vista and works similarly to prefetch except that it preloads applications based upon your usage patterns. To disable or stop it, go to Computer Management, select Services on the left, then double-click on Superfetch and choose the wanted option.
Keep coming back, my aspiring hackers, as we continue to explore digital forensics to enlighten you into the inner workings of our operating systems and keep you safe!

























Comments
Be the first, drop a comment!