Welcome back, my hacker apprentices!
I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.
Get Wireshark
Although there are numerous tools to do network analysis and investigations, the most widely used tool, by far, for doing so is Wireshark. It's a free, network analysis tool that's ported for Windows, Unix, OS X and Linux, and you can get it from here. Even better, it's built into our BackTrack, so no need to download anything, if you are using BackTrack.
You can start Wireshark from the BackTrack menu by going to BackTrack -> Information Gathering -> Network Analysis -> Network Traffic Analysis and click on Wireshark.
Grab a Live Capture
Next, we need to start Wireshark, which is capable of doing analysis on pcap and other capture files, as well as a live capture. Let's do a live capture. Click on Capture on the Menu across the top and it will open a window like that below.
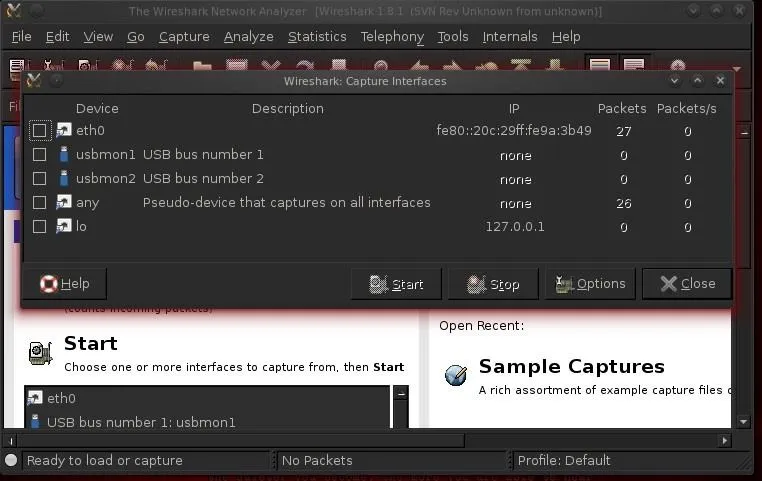
Select the active interface, which in this case is eth0, as I'm running it on a wired connection.
Our Problem
Here's the problem we're faced with.
Our client has been complaining that strange things are happening on his computer. His browser keeps changing his home page to a page that keeps telling him that his computer is infected with a virus, while also telling him that he needs to buy an antivirus program. We've all seen this at one time or another.
In addition, his computer is running slowly and various ads keep coming up. Something has infected this system. Let's see what we can decipher about this situation.
Live Capture
We start by sniffing the traffic on the network and we can see the live packets go by like that below.
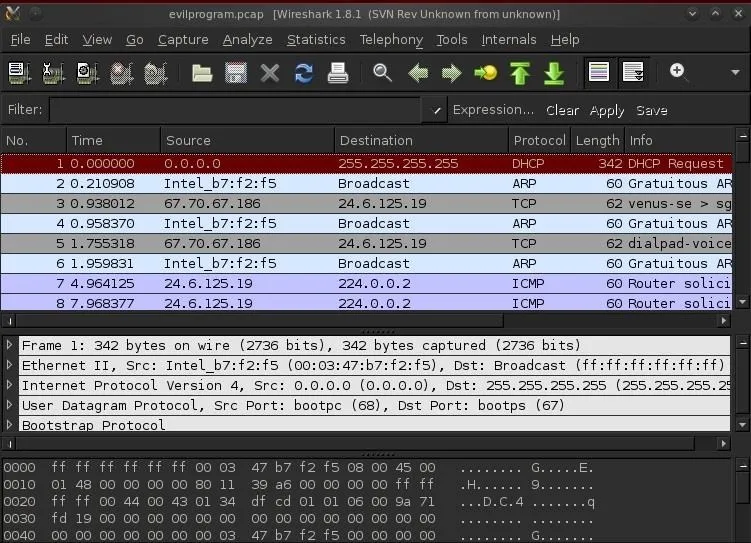
Note that Wireshark has three windows. The upper windows shows us each packet and some basic information about it. The middle window enables us to see each and every bit and byte of the packet headers. The bottom window shows us the packet contents in hexadecimal and ASCII.
Remote Attempts
The far left column enumerates the packets in the order that they arrive. Let's look at packet 147 below. We can see a messenger packet from a device somewhere on the Internet. Let's take a closer look at this packet by clicking on it. When we do, it's details appear in the middle window in white.
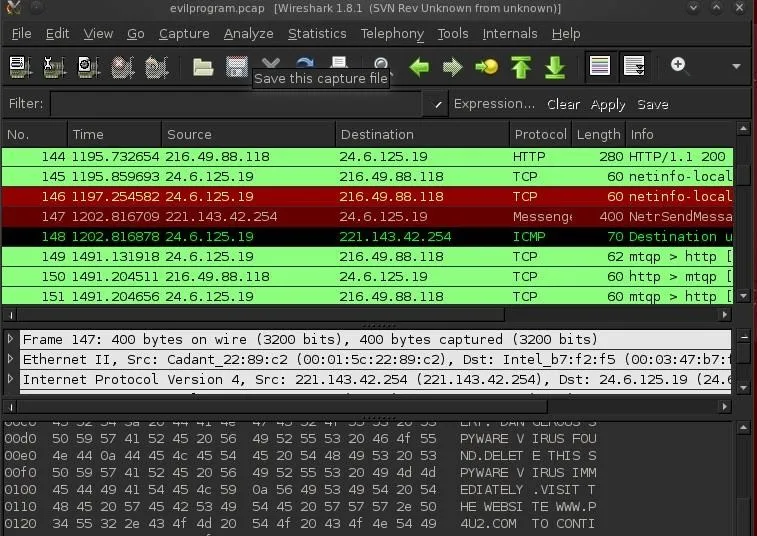
Since the messenger service is disabled on this network, nothing happens. We can verify that by looking at the next packet, which is an ICMP "Destination Unreachable" packet sent back to the IP requesting a messenger connection. This is suspicious activity.
Filter the Traffic
With so much traffic going by, we need to filter the traffic so we only see the traffic we are interested in. If we click on traffic between 216.49.88.118, we can see that this address is antivirus update from McAfee (note in the bottom window in the ASCII section a reference to mcafee.com).
Since this traffic is not dangerous, we can remove it from our viewing by filtering it out. In this case, we want to see everything that is not coming from IP address 216.49.88.118. We can put the following filter into the filter window. When the syntax is correct it, the window background will turn green. The proper syntax to exclude an IP address is:
- !ip.addr == 216.49.88.118
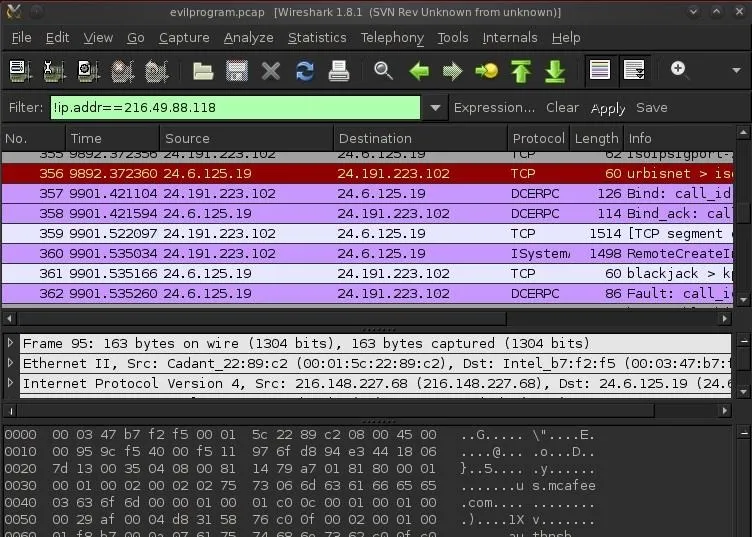
Now we have removed any traffic from our view coming from an innocuous address. This helps us focus our attention on the other, potentially malicious traffic.
In the screenshot below, we have successfully filtered out the traffic to and from McAfee.
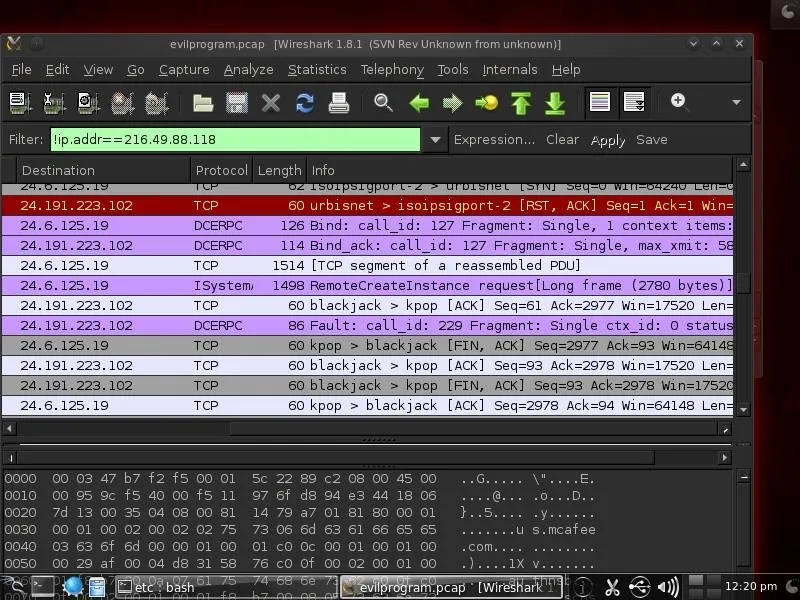
DNS Query
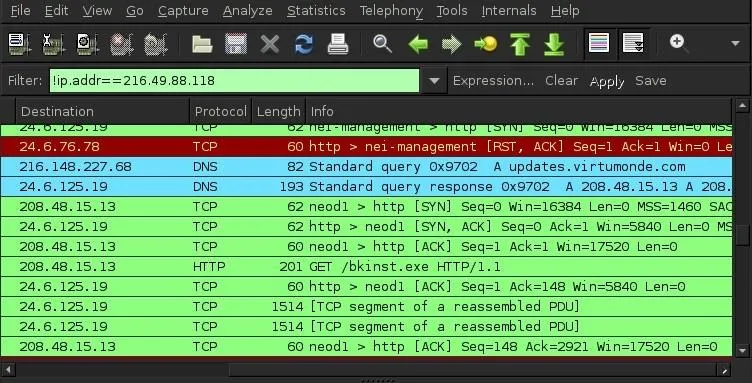
Now let's look down a few packets. In this screenshot, we can see that our client's computer (216.148.227.68) in the second packet shows a "standard query" with the DNS protocol to virtumonde.com. This is suspicious!
If we scroll down to packet 386, we can see our client's host goes out to the virtumonde.com server and requests a download. When we click on this packet and expand its HTTP protocol in the middle window, we can see "updates.virtumonde.com\r\n."
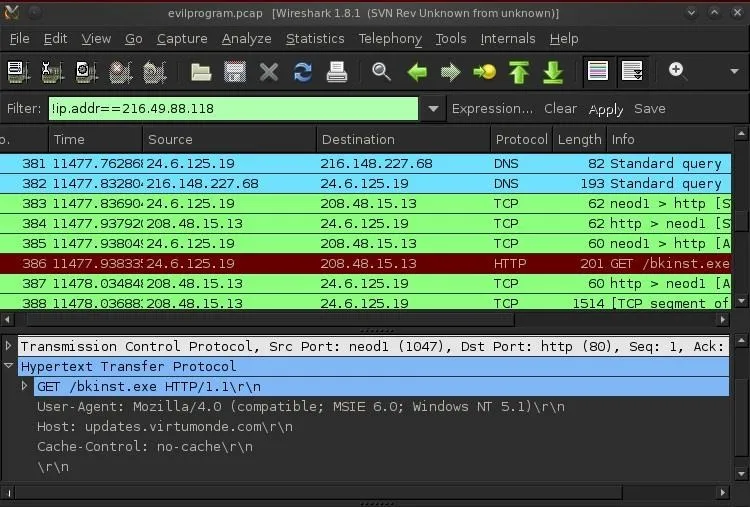
This is VERY suspicious activity and probably indicates that our client's system has been infected with a rootkit or spyware and it's reporting back to its home server.
Keep coming back my aspiring hackers as we keep exploring the finer points of hacking and forensics!

























Comments
Be the first, drop a comment!