Welcome back, my novice hackers!
Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.
For the sake of making things interesting, let's assume we have a suspected terrorist that we need to keep eyes on because there is reason to believe that he is planning a terrorist attack (right out of last night's news!). Our employer (presumably a law enforcement, military, or espionage agency) has asked us to spy on his Internet traffic to see whether our suspicions are true. How can we do this?
Fire Up Kali & Access His Network
Our first step, of course, is to fire up Kali, our tried and trusted hacking toolkit. In it, there are numerous hacking tools. Before we can spy on our suspect we will need to place ourselves on the same network. This can be done numerous ways.
First, if he is using a wireless network, this might be the easiest. We can either crack his WPA2 password or crack his WPS PIN. In either case, after we crack the access code, we can then log into his AP to get on the same network.
Second, we could physically place ourselves by the same network at his place of employment, school, institution, etc. We could pose as a new employee, new student, repair person, etc. and gain access to the network in that way.
Third, we could hack and own his computer or any other computer on the same network. This might be the most time consuming and difficult. In any case, I am assuming you have access to the same network as the suspect, so let's continue with this tutorial.
Conduct a MitM Attack
Although there are numerous ways to conduct a MitM (man-in-the-middle) attack, the simplest is probably using Ettercap, which is built into Kali and has both a command line and graphical user interface. To keep things simple, let's use the GUI. We can activate the Ettercap GUI by typing:
kali > ettercap -G
When we do so, it opens a GUI like that below.
Place Ourselves in the Middle
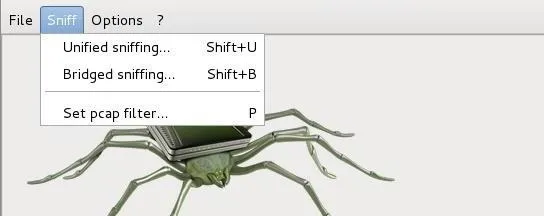
In the next step, we need to place ourselves in the middle between the suspect and his router. The first step to doing this is to get Ettercap to sniff on the network. Go to the "Sniff" menu and select "Unified sniffing."
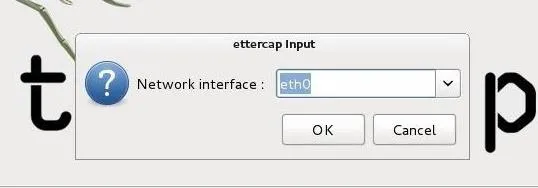
Select the interface you want to sniff on. If you are on a wired network, it will usually be eth0. On a wireless network, it will usually be wlan0.
Scan for Hosts
The next step is to scan for hosts. This means that Ettercap will scan the network and find the IP address and MAC address of all the systems on the network. From the "Hosts" menu, select "Scan for hosts."
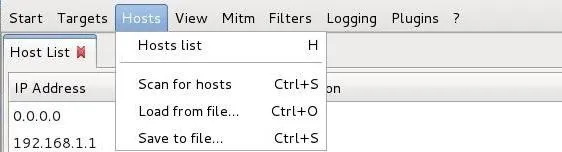
When Ettercap is done scanning the network, we need to select the "Hosts" menu again and select "Hosts list." Ettercap will now show you all the hosts on the network with IP addresses and MAC addresses.
Start the MitM Attack
Select the "Mitm" menu at the top of the screen. It will pull down several options. Select "Arp poisoning."
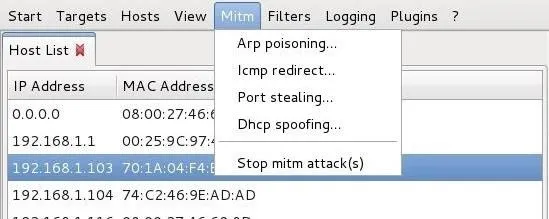
Next, select your targets from the list of hosts. From the "Host List" tab, select the suspect as Target 1 and the router as Target 2.
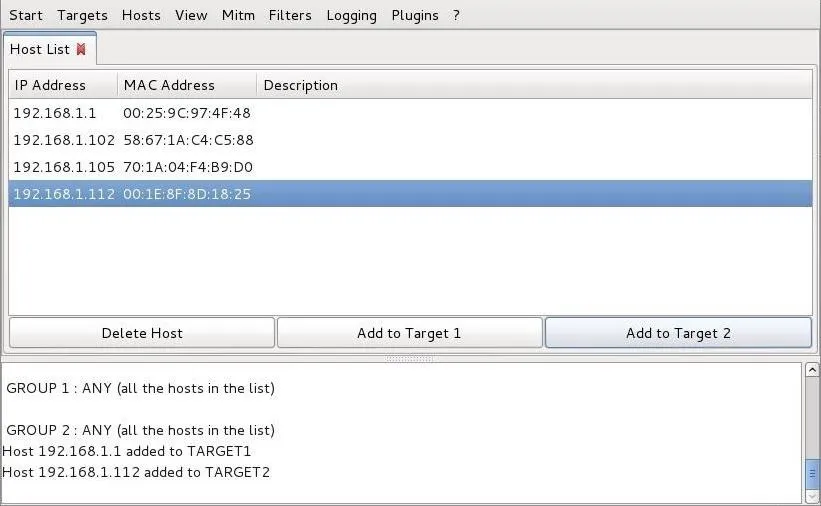
Now, we have successfully placed ourselves between the suspect and his router and all of his Internet traffic is traveling through our system!
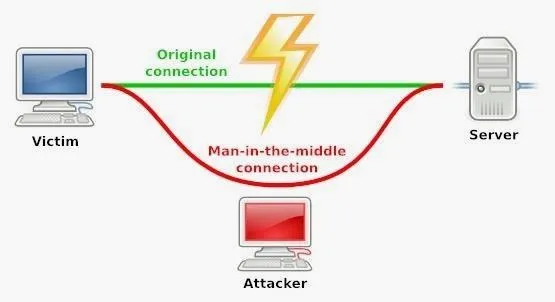
Use Snort as a Spy Tool
Now that have established ourselves between the suspect and his router, all of his traffic must go through our computer. This means that we can "see" all of his traffic. We could simply sniff his traffic with sniffers such as Wireshark, but that would mean tediously filtering, scanning, and saving all of his traffic to look for suspicious activity. Our task would be much simpler if we could automate this process.
Snort was originally developed as an IDS to sniff Internet traffic and search for malicious activity. It picks up every packet and inspects it, using its rule base to look for traffic that might be malicious. It does this automatically and transparently with little human intervention.
Here, we will alter Snort a bit. Instead of looking for malicious traffic coming into our network, we want to look for suspicious keywords coming from or going to the suspect's machine from the Internet. If any of these words appear in his traffic, it will send us an alert.
The first step is to download Snort, if you don't already have it. It can be found in the Kali repository, so you need only type the following. (If you have a recent version of Kali, it is already on your system, and you don't need to do this.)
kali > apt-get install snort
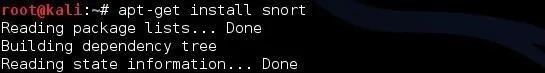
This should successfully install Snort on your system.
Set Up Snort Rules
Snort uses a rule set to look for malicious traffic. In addition, Snort allows us to add our own rules. What we will be doing here is disabling all the rules that look for malicious traffic and instead creating rules that will look for suspicious keywords that might indicate the intentions of the suspect.
We need to open snort.conf in any text editor. Here I will be using Leafpad.
kali > leafpad /etc/snort/snort.conf
We now need to navigate to the bottom of this file and comment out all the "includes" that pertain to the rule files. In my snort.conf, the "includes" begin at Line 570 with the local rules (yours may differ slightly). This will disable all the Snort rules that come with the IDS.
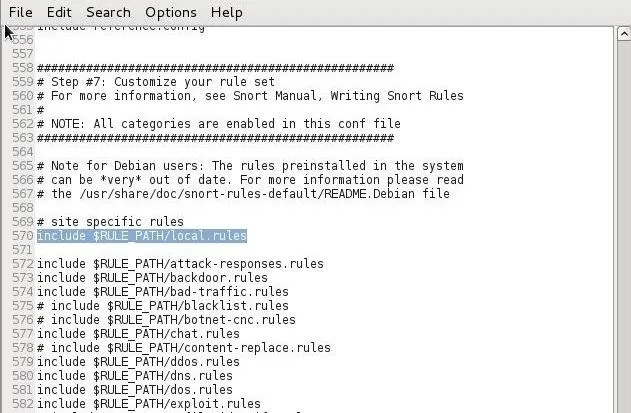
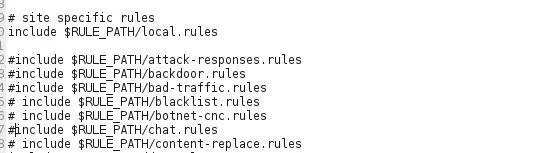
Go through each line except the "include local.rules" one and place a # before each include. This will make certain that only our local rules are activated and used by Snort.
Write Rules to Look for Suspicious Traffic
In our last step, we need to create Snort rules that will search the suspect's Internet traffic for keywords that would indicate his intent of some malicious activity. This may differ based upon the circumstances, but I will set up alerts for whenever the suspect sends or receives traffic that contains the words, "jihad," "ISIS," "suicide," or "bomb." Of course, these keywords can and will differ, and I use these only for demonstration purposes here.
Let's open the local.rules file in Leafpad and write the rules. For information on how to write Snort rules, check out this guide.
kali > leafpad /etc/snort/rules/local.rules
When the file opens, add the file following rules as seen in the screenshot below.
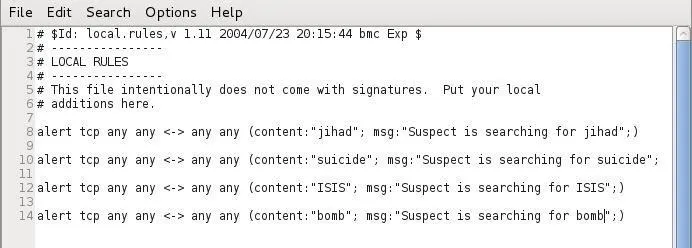
Now, save the local.rules file and start Snort.
kali i > snort -vde -c /etc/snort/snort.conf
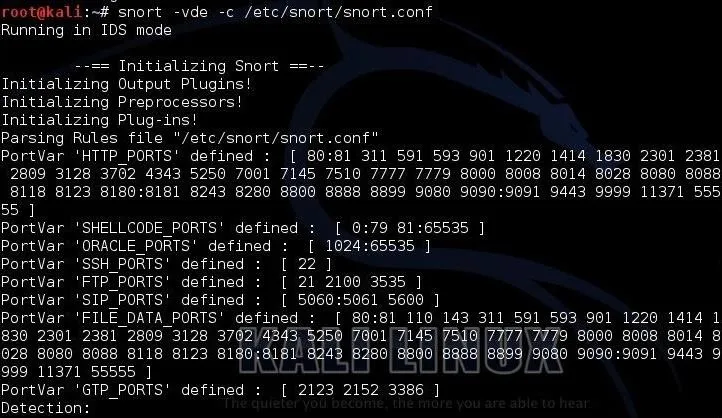
Whenever the suspect has any Internet traffic that contains those keywords, Snort will send you an alert and log the packet so that you can go back later and examine what he was looking at.
We have successfully developed a spying system that will alert us whenever our suspected terrorist sends or receives any network traffic that contains those suspicious keywords. We may have successfully saved many innocent lives, my novice hackers, by simply applying some basic hacking skills!
Cover image via Shutterstock

























Comments
Be the first, drop a comment!