Welcome back, my fledgling hackers!
A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.
p0f relies upon the different ways that each OS implements the TCP/IP stack, and these different implementations leave their unique fingerprints on the TCP/IP packets. These differences are found in four key fields of the TCP/IP packet—the DF, TTL, Window, and TOS.
In our previous p0f tutorial, we had tested p0f against older operating systems and it did its fingerprinting superbly! When we tried it against Windows 7 and other more current systems, we found that the signatures had not been updated since 2006.
We could have collected the signatures of different systems and added them to the /etc/p0f/p0f.fp file to bring the signatures database current, but I mentioned at the time that the developers of p0f had finally updated it and released version 3.0 after lying dormant for over 6 years.
In the new version, they have not only updated the signatures, but also added new capability to p0f. The new version has been included in the latest release of Kali (1.0.6), so let's take a look at it here. For those using BackTrack or early versions of Kali, you can download the new p0f here.
Fire Up Kali & Open p0f
Let's start by firing up Kali and opening p0f 3.0 up. Interestingly, Kali has placed p0f under Forensic tools, so to open it, we need to go to Kali Linux -> Forensics -> Network Forensics -> p0f.
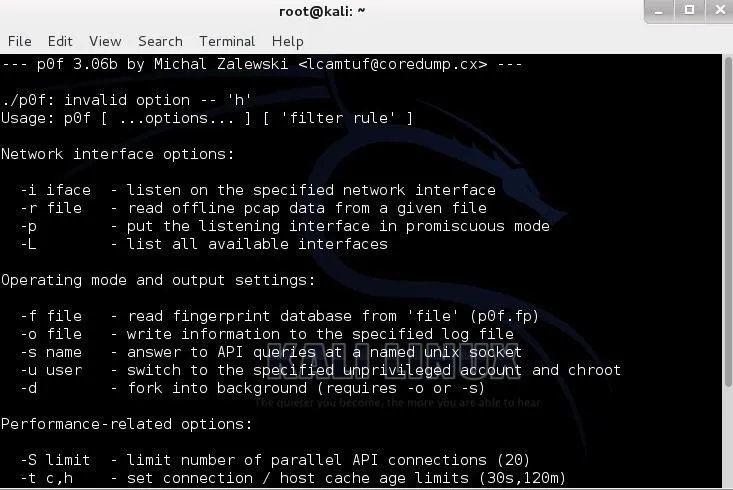
When we open it, we are greeted with a help screen like that below. The syntax is pretty much the same as the earlier versions; it's simply the command and the interface.
- kali>p0f -i eth0
Send Packets from Windows Server 2003
Now, like we did with the older p0f 1.6, let's send packets from a Windows Server 2003 system. We can do that in a number of ways—ftp, telnet, netcat, or simply by opening a browser directed to the IP address of our Kali system.
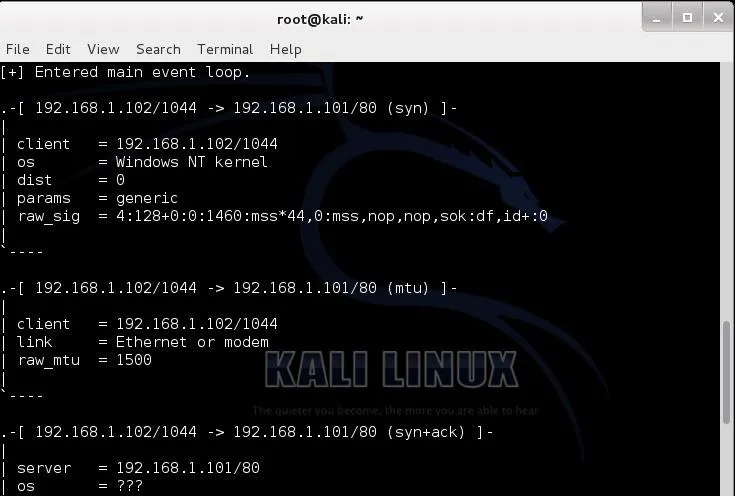
When we do so, we get the results below. p0f identifies the IP address and the link and then identifies the OS as a "Windows NT kernel". Not real specific, but accurate.
Send Packets from Windows XP
Let's now try the same with Windows XP and see what p0f can decipher for us. In this case, I'll try connecting to an ftp server on Kali.
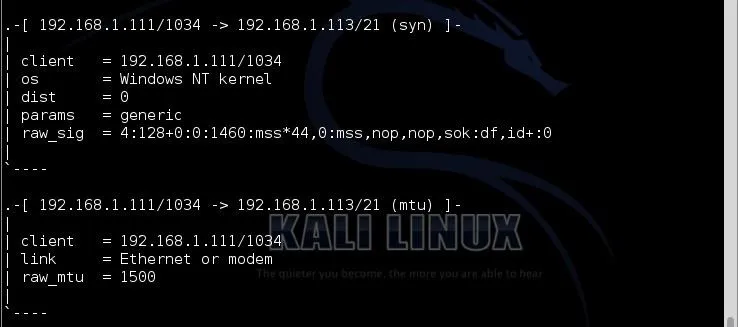
Once again, p0f is accurate, but not very specific. It identifies the OS as Windows NT kernel. Remember that p0f is using the differences in the TCP/IP stack implementation as the way of identifying the OS and if a range of operating systems are using the same TCP/IP stack, it cannot differentiate between them.
Send Packets from Windows 7
One of the issues we found with the older p0f is that the signatures were old (no updates after 2006) and it did not have signatures for Windows 7, 8, Server 2008, and Server 2012. Let's test p0f on one of the modern systems, such as Windows 7.
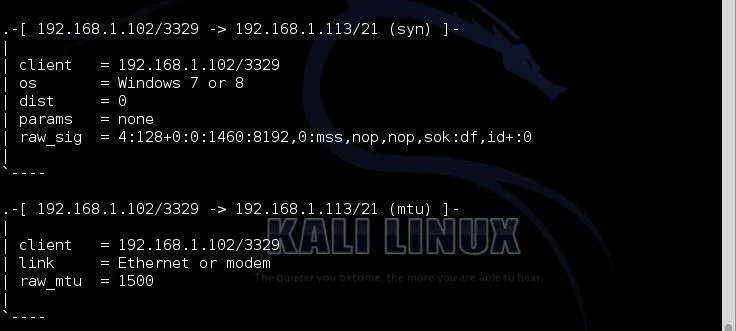
As you can see, it accurately identified it as "Windows 7 or 8". As these two systems are from the same build, it can't distinguish the difference between them. As a hacker, in most cases, the differences are unimportant.
Send Packets from Ubuntu
Now let's try sending some packets from a Ubuntu machine.
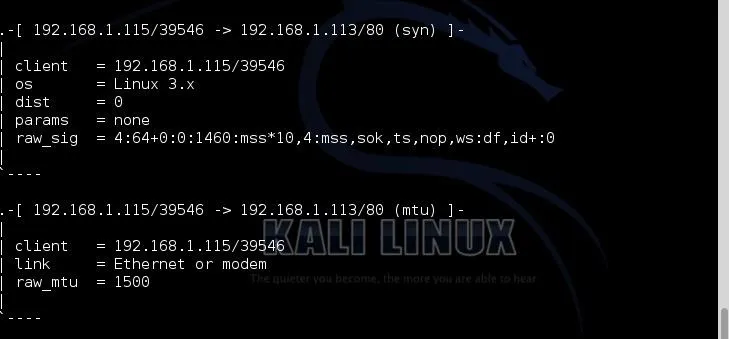
As you can see, p0f accurately deciphered that the system sending the packets was a Linux system with 3.x kernel.
Run p0f for Forensics
In our final test of the effectiveness of the new p0f, let's just let p0f run on our interface and see what it picks up. This can be useful for doing forensics on a compromised system or a system under attack.
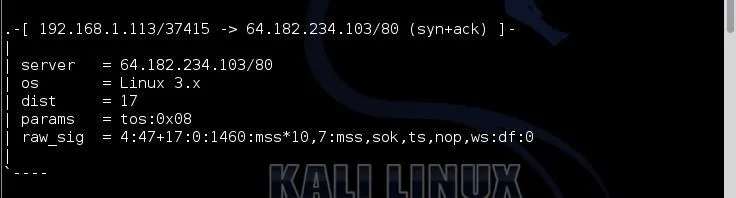
When I let p0f run for a short while on my eth0 interface, I soon started to get entries like those above. I found this puzzling. My Kali system was connecting to an unknown IP address at 64.182.234.103.
In the screenshot above, it identifies it as a Linux server and 17 hops away. This seems odd for several reasons. First, I have not been connecting to any website or server at that address. In fact, my system has been completely idle. Second, 17 hops is long—way long. Generally, you can connect to nearly any server on the planet within 15 hops. This is something I should investigate!
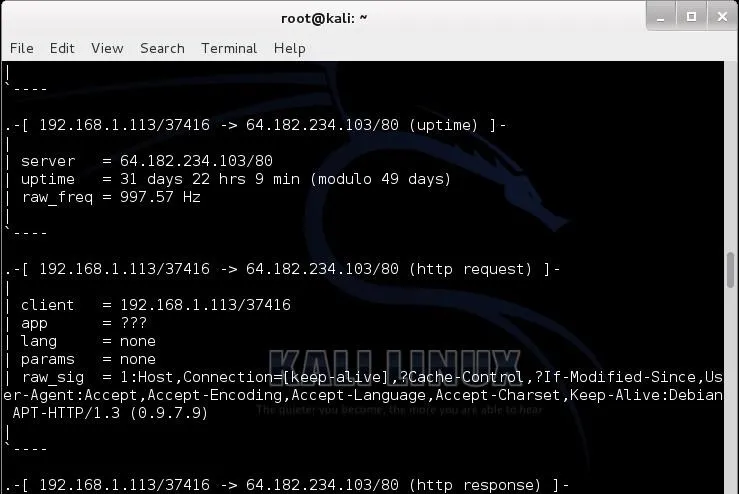
As I scroll down the p0f entries, I can get more information on this server that my Kali system connected to. I can see that my system connected from my port 37416 to its port 80 and that this server has been up over 31 straight days.
Further investigation reveals that this IP address belongs to owncloud.org. I never went to this address, but apparently the folks at Offensive Security have put a client in Kali that is connecting to this site automatically. From the documentation on the website, I was able to decipher that it's apparently a free cloud service similar to Google Apps.
I'm not happy about this! There is nothing that I can find in the Kali documentation regarding this. I'm not saying that this is anything malicious, but I think the folks at Offensive Security should have told us explicitly that they have included a client that automatically connects to this cloud service.
The new p0f is an improvement over the older version, but still is not perfect. Passive reconnaissance has the advantage of being undetectable, but the disadvantage of lower reliability of results. A tool like p0f, though, can be invaluable in identifying the operating systems of the clients that are accessing your website or the systems passing your wire while sniffing traffic.
Original coded fingerprint image via Shutterstock, remixed by Justin Meyers/WonderHowTo

























Comments
Be the first, drop a comment!