Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.
The PowerShell payload generated by Unicorn works as expected when used against the target Windows 10 machine. It creates a reverse HTTPS connection back to the attacker's Kali setup while actively evading Windows Defender and Avast antivirus detections. This is all great, but the real challenge is tricking the target Windows user into executing the code on their computer.
To accomplish this, a few things can be done to the PowerShell payload before sending it to the victim. The payload needs to be converted into a Windows executable (EXE). The icon (ICO file) will need to be changed as well to look like an ordinary text file. The biggest red flag that the fake text file is actually an executable is the file extension. Some Windows users disable the "Hide extensions for known file types" option to protect against file extension spoofing attacks. In this article, I'll show how to spoof the file extensions — even with file extensions unhidden.
For readers who might've skipped the first part of this article, here's the GIF again showing the real and fake text files side by side:
The file on the left is a real text file. The file on the right is the PowerShell payload, designed to first open Notepad before executing the PowerShell payload.
Save the PowerShell Payload
The following steps require a Windows operating system. I recommend using a Windows 10 virtual machine (VM) in VirtualBox.
Before going further, the previously created PowerShell payload should be moved to the Windows system and saved as payload.bat using Notepad or a preferred text editor. The payload.bat will be manipulated to appear as a normal text file in proceeding steps.
Download the Windows 10 Icons
Windows 10 icons will need to be downloaded to begin transforming the payload.bat into a fake text file. These icons will be used to spoof the file icon. You can download the Windows 10 icons using git clone 'https://github.com/B00merang-Project/Windows-10-Icons'.
~$ git clone 'https://github.com/B00merang-Project/Windows-10-Icons'
Cloning into 'Windows-10-Icons'...
remote: Counting objects: 3495, done.
remote: Total 3495 (delta 0), reused 0 (delta 0), pack-reused 3495
Receiving objects: 100% (3495/3495), 14.69 MiB | 294.00 KiB/s, done.
Resolving deltas: 100% (393/393), done.
Checking connectivity... done.This repository may not contain exact replicas of the built-in Windows 10 icons but appear close enough and will serve nicely for the purposes of this article. If readers are capable of designing icons or locating better icons online, I encourage the usage of those.
I'm using text-x-generic.png located in the Windows-10-Icons/256x256/mimetypes/ directory, but any PNG will work to continue following along.
Convert the PNG to ICO Format
The PNG will need to be converted into the Windows ICO icon format. This can be done using online tools such as ConvertICO. Simply upload the desired PNG to the website and it will reproduce it in ICO format. Save the new ICO with the file name fakeTextFile.ico.
Install BAT2EXE
I've featured BAT2EXE (B2E) in an article before. This is a great tool for converting BAT files to Windows executables.
To download B2E, the website requires users mine cryptocurrency for several minutes in exchange for downloading their free software. If readers wish to support the B2E developer's, proceed to the download page and grab the latest B2E software. Otherwise, readers can use my mirror of a slightly older version of B2E.
Using my GitHub mirror, in Windows, visit the below URL to download B2E.
https://github.com/tokyoneon/B2E/raw/master/Bat_To_Exe_Converter.zipUnzip the download and run the "Bat_To_Exe_Converter_(Installer).exe" file to install it.
Import the Payload BAT
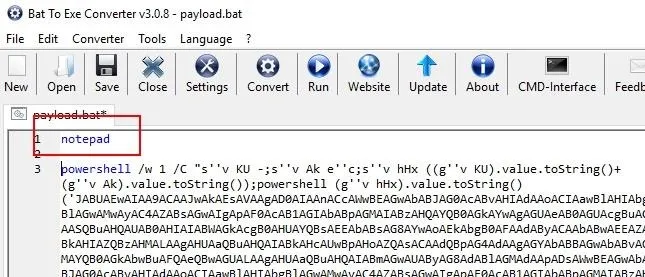
When that's done, start B2E and click the "Open" button to import the payload.bat created earlier.
Trojanize the Payload
Then, add the word "notepad" to the top of the payload.bat, and click "Save." This will make the executable open Notepad on the Windows machine before executing the PowerShell payload. Doing this will make the target user believe the file they just clicked on is indeed a legitimate text file.
Now, there's a lot that can be done to further convince someone the file is legit. For example, if Notepad isn't their default text editor, it might seem suspicious that this one file opens Notepad when other text files open Notepad++, a popular third-party text editor. So improving the BAT to open a default program, instead of Notepad, might be desirable. Also, opening a blank Notepad when the file is reported as being 12 KB in size might also be suspicious, so finding a way to produce text or Trojanize the EXE to first download an actual text file might help improve the effectiveness of such attacks.
For sake of simplicity, I'll continue as is, with the BAT opening a blank Notepad. This will hopefully demonstrate how easy it is to create trojans and get readers on the right track to developing this attack to meet their individual needs.
Convert & Export the Payload
With that done, check the "Icon" option to enable it, and import the fakeTextFile.ico icon created in the previous step using the "..." button. Then, change the Exe-Format to "64-bit Windows | (Invisible)" to prevent any terminals from popping up when the target user opens the file.
Click the "Convert" button to create the EXE, and save the filename as fake.exe.
After saving the fake.exe to the desktop and placing it beside a real text file, readers may notice a thin red line in the fake icon that doesn't exist in the real text file icon. This can be easily fixed by using a better Windows 10 icon set or by using a different type of file to spoof.
Spoof the File Extension with Unicode
The bigger issue is the file extension. Thanks to the "Hide extensions for known file types" option in the File Explorer Options, file extensions are not being hidden by the Windows operating system. To get around this, use a Unicode character called "Right-to-Left Override" (RLO) to reverse the order of which the characters are displayed in the filename. That's important to understand since the characters aren't actually being reversed, how Windows displays the characters is being reversed. Windows will still recognize the file extension as EXE.
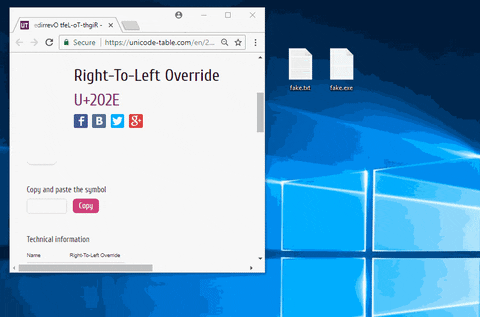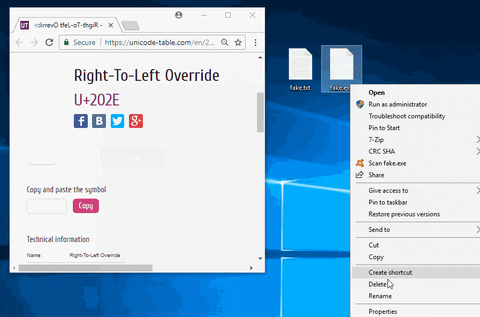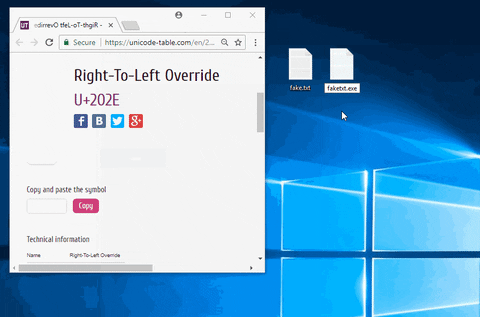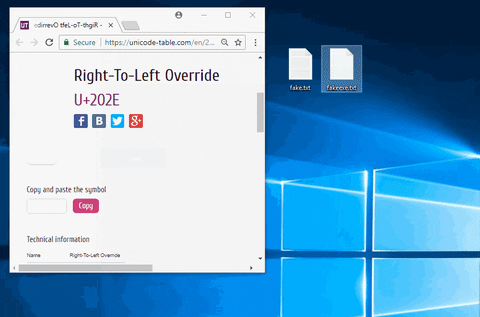
As seen in the above GIF, the invisible RLO character is being injected between the file name ("fake") and the fake file extension ("txt"). All the RLO character is doing here is flipping the order the characters in the file name are displayed. Unfortunately, the "exe" must remain in the spoofed filename.
How to Protect Against File Extension Spoofing Attacks
Since our whole objective here was to create an undetectable payload, antivirus software is not really a good option for protecting against these types of file extension spoofing attacks.
One thing you can do is just put on your magnifying glass when looking at files you download off the internet. In our case above, you won't be able to tell at first glance that the icon is not the same as other text files, but at closer examination, you'll see that something is fishy.
If you're suspicious of a file or its source, try renaming it. Be careful not to double-click on it. Instead, right-click the file and choose the "Rename" option from the context menu. If Unicode is being used, renaming the file using characters found on standard keyboards will remove the Unicode, revealing its true extension.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image by Justin Meyers/Null Byte; Screenshots by tokyoneon/Null Byte

























Comments
Be the first, drop a comment!