If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.
Spooky Action at a Distance
If you need to prove you've got remote access to a computer but don't want to risk a demonstration that could put data at risk, SSH can be a lot of fun for a very small amount of work. There are plenty of ways to either cause a big distraction or to confirm you have access to a target device over SSH, and most of them are also pretty dramatic when done correctly.
While the signs of someone messing with your computer remotely may be obvious to some, the average person is not looking for clues that suggest they are under attack and will tend to attribute strange behavior from their computer to bugs, glitches, or other reasons beyond their control. With SSH access, a hacker can easily create fake alerts or cause behaviors to trick others into doing something the hacker wants them to do.
Rather than being subtle, we're going to look at things we can do over SSH to cause the maximum effect to freak out a user on the other end.
Alarming Things You Can Do Over SSH
We have a lot of tools at our disposal when creating an alarming SSH experience. To start, we can launch applications like Firefox to navigate to any webpage we want, launching either fullscreen webpages or multiple smaller browser windows. Most people associate webpages launching with a virus or adware, especially if most of the websites are about Viagra.
Next, we can start making some noise. The speakers attached to a computer represent a lot of fun we can have, and this can take the form of alarming beeping or speech seemingly from nowhere. If someone thinks they are alone in their home, a computer shouting at them from nowhere is a very unwelcome surprise. The same is true of your computer beginning to beep furiously as though it were about to explode.
If we want to be more direct, we can frightening error messages that take up the entire screen and suggest dangerous things are happening on the computer. By combining beeping and error messages, we can create fake problems which look very serious and disruptive.
What You'll Need
To follow along, you'll need a computer that you have SSH access to. This guide is based on an Ubuntu computer, but you can control most Linux computers including MacOS using the same commands.
You'll also need to be on the same network as the computer you want to control. Once you're logged in to the target computer via SSH, you can start launching apps and taking other actions remotely.
Establishing Access & Basic App Launching
To start, we have to specify that we want everything we do to appear on the remote computer we are logged into via SSH, not the local computer we are logged in using. To do that, we'll first set our display path with the following command.
export DISPLAY=:0.0Now, running a simple command like firefox via SSH will open a Firefox window on the remote computer.
That's not very scary, though. For our first example, let's open a scary looking xterm window that will display network data that looks quite alarming to a beginner. To make this even worse, we'll do it 10 times, so when they click out of it, a new one instantly spawns 10 times in a row.
For this to happen, we'll first use the command for i in {1..10}; followed by the code we want to execute, and then done at the end.
for i in {1..10}; do sudo xterm -maximize -e sudo tcpdump; doneIn this case, we're opening a maximum sized terminal window, and the -e command means we are executing sudo tcpdump in the xterm window we launch.
To the average user, their computer has now started spawning hacker shells that can't be closed.
Bells, Whistles, & Speech
Before we can make any noise at all, we'll need to run the following command to let us control the speaker remotely.
sudo modprobe pcspkrAfter this is done, we have a lot of options! First, we can say any phrase through the computer with the say command. We can also use the espeak command to do the same thing.
say "I am a canadian randomware, I have not encrypted any files but would appreciate some change"
espeak "please give me quarters sorry to bother you"We can schedule these to go off periodically in a chrontab later, or just do them live.
If we want to be more subtle, we can use beep to drive a user crazy. To use this, make sure you have it with apt install beep.
Once you have it installed, check out what you can do with it using man beep, a great command.
BEEP(1) General Commands Manual BEEP(1)
NAME
beep - beep the pc speaker any number of ways
SYNOPSIS
beep [--verbose | --debug] [-e device | --device device] [-f
N] [-l N] [-r N] [-d N] [-D N] [-s] [-c]
beep [ OPTIONS ] [-n] [--new] [ OPTIONS ]
beep [-h] [--help]
beep [-v] [-V] [--version]
DESCRIPTION
beep allows the user to control the pc-speaker with preci‐
sion, allowing different sounds to indicate different
events. While it can be run quite happily on the command
line, it's intended place of residence is within shell/perl
scripts, notifying the user when something interesting
occurs. Of course, it has no notion of what's interesting,
but it's real good at that notifying part.
All options have default values, meaning that just typing
'beep' will work. If an option is specified more than once
on the command line, subsequent options override their pre‐
decessors. So 'beep -f 200 -f 300' will beep at 300Hz.
OPTIONS
--verbose, --debug
enable debug output. This option prints a line like
the following before each beep:
[DEBUG] 5 times 200 ms beeps (100 delay between, 0
delay after) @ 1000.00 Hz
-e device, --device device
use device as event device. If the switch isn't used,
/dev/tty0 and /dev/vc/0 are tried in turn.
-f N beep at N Hz, where 0 < N < 20000. As a general
ballpark, the regular terminal beep is around 750Hz.
N is not, incidentally, restricted to whole numbers.
-l N beep for N milliseconds.
-r N specify the number of repetitions (defaults to 1).
-d N, -D N
specify a delay of N milliseconds between repeti‐
tions. Use of -d specifies that this delay should
only occur between beeps, that is, it should not
occur after the last repetition. -D indicates that
the delay should occur after every repetition,
including the last. Normally, -d is what you want,
but if, for example, you are stringing several beep
commands together to play the star wars anthem, you
may want control over every delay.
-n, --new
this option allows you to break the command line up
into specifying multiple beeps. Each time this
option is used, beep starts treating all further
arguments as though they were for a new beep. So for
example:
beep -f 1000 -n -f 2000 -n -f 1500
would produce a sequence of three beeps, the first
with a frequency of 1000Hz (and otherwise default
values), then a second beep with a frequency of
2000Hz (again, with things like delay and reps being
set to their defaults), then a third beep, at 1500Hz.
This is different from specifying a -r value, since
-r repeats the same beep multiple times, whereas -n
allows you to specify different beeps. After a -n,
the new beep is created with all the default values,
and any of these can be specified without altering
values for preceding (or later) beeps. See the EXAM‐
PLES section if this managed to confuse you.
-s, -c these options put beep into input-processing mode.
-s tells beep to read from stdin, and beep after each
newline, and -c tells it to do so after every charac‐
ter. In both cases, the program will also echo the
input back out to stdout, which makes it easy to slip
beep into a text-processing pipeline, see the EXAM‐
PLES section.
-h, --help
display usage info and exit
-v, -V, --version
display version information and exitWe can make pretty much any noise with Beep. It even comes with a handy reference table for composing notes.
Note Frequency
C 261.6
C# 277.2
D 293.7
D# 311.1
E 329.6
F 349.2
F# 370.0
G 392.0
G# 415.3
A 440.0
A# 466.2
B 493.9
C 523.2In our case, we're going to do something horrible. Here, the -f flag sets the frequency to a ear-piercing 4000 kHz, the -d flag sets the duration of the delay between beeps to 500 ms, and the -l flag sets the length of the beep to a second. Finally, the -r flag repeats this awful noise 10 times.
beep -f 4000 -D 500 -l 1000 -r 10You can use this to alarm anyone into thinking their computer objects strongly to something they just did.
Frightening Error Messages
Confusing or alarming error messages can be a lot of fun to send, as users will generally believe them until they become too absurd. There are a couple of different types we can send, some of which are lame.
We can pop up subtle little messages by using the notify-send command, with the title first and the message body second.
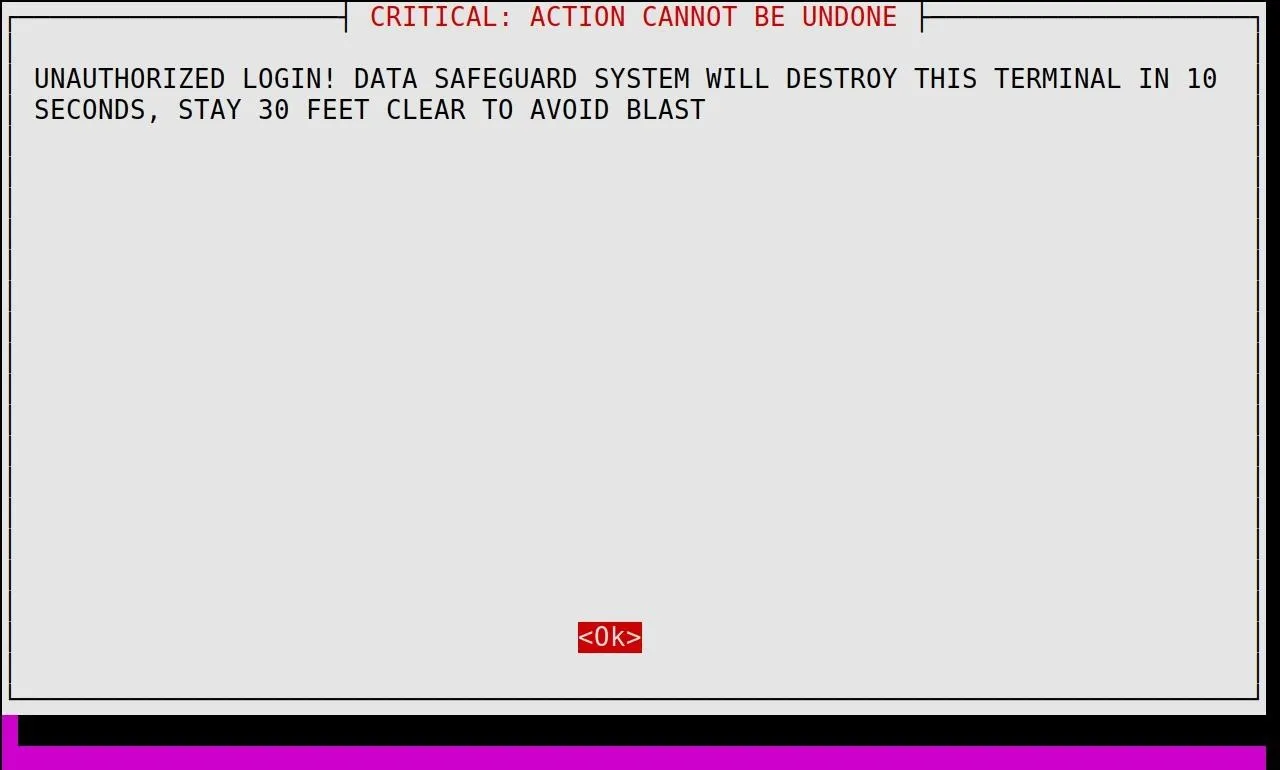
notify-send 'WARNING' 'I AM CALLING THE INTERNET POLICE'This pops up a little alert in the corner. Kinda boring. Instead, we can display this big fat alarming message using whiptail and launching it in a full screen window.
xterm -maximized -fullscreen -fa 'Monospace' -fs 19.31 -e whiptail --title "CRITICAL: ACTION CANNOT BE UNDONE" --msgbox "UNAUTHORIZED LOGIN! DATA SAFEGUARD SYSTEM WILL DESTROY THIS TERMINAL IN 10 SECONDS, STAY 30 FEET CLEAR TO AVOID BLAST" --topleft 23 79You can replace it with your own content, but here's how it looks.
Cron Jobs from Hell
Now, we can start combining these and scheduling them to run automatically. We can check to see if there are any existing jobs in the crontab with the -l flag, and then add a new one with the -e flag.
crontab -l
crontab -eFrom the configuration window that pops up, you can add a job to execute every 60 seconds with the following formula.
* * * * * (your code here)To make the computer beep every 60 seconds, we can add this entry, and then press ctrl x and y to save the file.
* * * * * beep -f 300.7 -r 10 -d 50 -l 400As soon as the file is saved, the computer will beep every 60 seconds.
Killing Tasks
If there is someone on the computer you have backdoor access to, you can deliberately kill the process ID of an application they are using. This causes the application to instantly crash, which can prevent someone from doing anything effective on the computer.
To find the process ID, we can use top or htop to see a list of processes running on the computer. If you don't have htop installed, you can do so with the command below.
apt install htop
top
Tasks: 219 total, 1 running, 178 sleeping, 0 stopped, 0 zombie
%Cpu(s): 3.0 us, 0.4 sy, 0.0 ni, 95.6 id, 0.9 wa, 0.0 hi, 0.0 si, 0.0 st
KiB Mem : 4968836 total, 1431244 free, 1104324 used, 2433268 buff/cache
KiB Swap: 5138428 total, 5138428 free, 0 used. 3367804 avail Mem
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
31906 root 20 0 0 0 0 I 6.2 0.0 0:00.59 kworker/u16:1
32560 toor 20 0 41928 3880 3192 R 6.2 0.1 0:00.02 top
1 root 20 0 160212 9592 6816 S 0.0 0.2 0:02.35 systemd
2 root 20 0 0 0 0 S 0.0 0.0 0:00.01 kthreadd
4 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 kworker/0:0H
6 root 0 -20 0 0 0 I 0.0 0.0 0:00.00 mm_percpu_wq
7 root 20 0 0 0 0 S 0.0 0.0 0:01.33 ksoftirqd/0
8 root 20 0 0 0 0 I 0.0 0.0 0:09.13 rcu_sched
9 root 20 0 0 0 0 I 0.0 0.0 0:00.00 rcu_bh
10 root rt 0 0 0 0 S 0.0 0.0 0:00.00 migration/0
11 root rt 0 0 0 0 S 0.0 0.0 0:00.03 watchdog/0
12 root 20 0 0 0 0 S 0.0 0.0 0:00.00 cpuhp/0
13 root 20 0 0 0 0 S 0.0 0.0 0:00.00 cpuhp/1
14 root rt 0 0 0 0 S 0.0 0.0 0:00.03 watchdog/1If I want to kill the process top, I just grab the PID and run the following command.
kill PID#In the example above, I would run kill 32560 to crash the top process that is running.
Putting It Together: Rickswarm
We'll want to combine everything we've learned to create vivid experiences for whoever happens to be on the computer we have access to. Let's take our alarming random beeping and combine it with some bash commands to make a whole lot of Firefox windows open up every 60 seconds, all navigating to "Never Gonna Give You Up."
for i in {1..10}; do beep -f 4000 -D 500 -l 1000 -r 10 & firefox -new-window "https://www.youtube.com/watch?v=dQw4w9WgXcQ"; doneSSH Access Makes Haunting a Computer Easy
While causing maximum distraction and disruption via SSH is not something that might come up on a daily basis, it's a lot of fun and very useful for social engineering. Obviously, while this is an entertaining prank, it's a very bad idea to do this to someone's computer you don't have permission to, as people who are not tech-savvy will probably think something much worse than a prank is going on and act out of fear. It isn't legal to access a device you don't have permission to, so keep your SSH pranks to pentesting and devices you have permission to access!
I hope you enjoyed this guide to haunting a computer with SSH! If you have any questions about this tutorial on SSH pranks or you have a comment, ask below or feel free to reach me on Twitter @KodyKinzie.
Cover image via 123RF

























Comments
Be the first, drop a comment!