If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?
This is where password management services like LastPass come into play. You simply remember one secure password and the service remembers the rest. Enter the one true password when prompted, then the service will auto-populate the password for the site you're visiting. Sounds safe, right?
On the surface, sure. LastPass has solid security measures that prevent someone from being able to brute-force attack your account and unlock your master password. But now, thanks to some clever new phishing sites, you might unwittingly hand the password over yourself—meaning every login credential for every service stored on LastPass could be stolen.
LostPass: The LastPass Phishing Clone That Could Fool Anybody
Developer Sean Cassidy has created a phishing tool that perfectly clones the LastPass expired login prompt, and he named the tool LostPass. It detects when the user has LastPass installed, then displays a "session expired" message on the phishing site that prompts you to log back into LastPass.
This is where LostPass gets really nasty. When you enter your user name and password on the following screen, LostPass immediately hijacks your account. The user name (email address) and master password are sent upstream to the attacker's server, so the bulk of the damage is already done.
At this point, if you have two-factor authentication enabled on your LastPass account, you'll be prompted to enter your verification code. As with the "session expired" message and the login prompt, this interface is virtually identical to the official LastPass prompt.

Now LostPass has everything it needs to take total control over your account. It uses the login info and two-factor authentication token it just stole to create a backdoor into your account by way of the LastPass "Emergency contact" feature, then sets the attacker's server as a trusted device to prevent any email notifications. To put it simply, all of your passwords are now compromised, and you probably have no idea that this just happened.
Note: As Sean stated on his blog, "LastPass now requires email confirmation for all logins from new IPs. This substantially mitigates LostPass, but does not eliminate it." So, it's a small chance that you might get hacked, but it's still a chance if there's a clever, persistent hacker behind the wheel.
How to Make Sure You Don't Get Tricked
LostPass works because it's almost a perfect replica of the official LastPass interface—but there are some subtle distinguishing elements. Depending on if you're using Chrome or Firefox as your browser, there are two different ways to spot this phishing attack, and I'll outline both below.
Spotting LostPass on Chrome
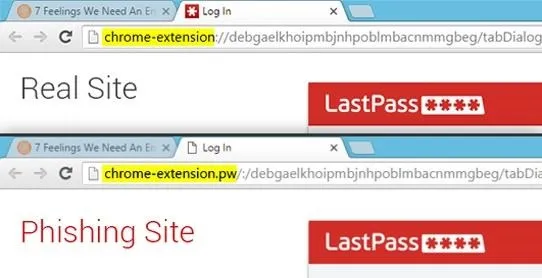
If you're using Chrome as your browser, spotting a LostPass phishing site takes a keen eye. The only real difference is in the URL bar—the address for the LastPass login prompt will start with chrome-extension if it's legit, but it will start with chrome-extension.pw, or something similar, if it's a LostPass phishing attempt.
Spotting LostPass on Firefox
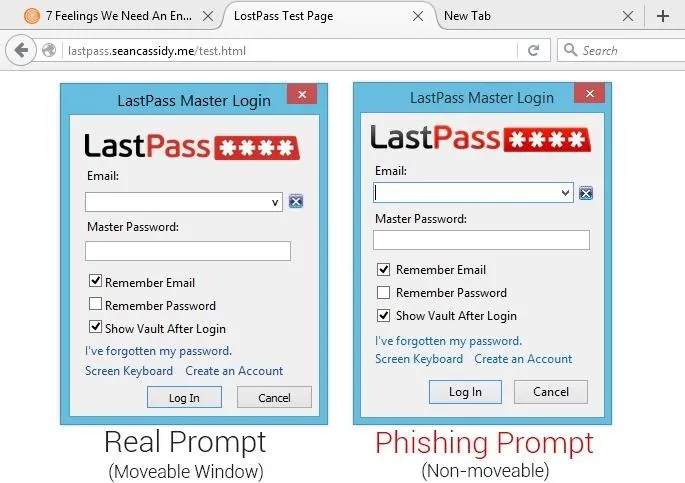
A phishing attempt would be a bit easier to spot on Firefox, since the official LastPass login prompt is a floating window, whereas the LostPass phishing prompt is embedded into the webpage. The interface will look virtually identical, but if you can't freely move the pop-up window, you're dealing with a phishing attempt.

























Comments
Be the first, drop a comment!