Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.
When installed via a drive by download, which occurs when users click on malware-infested URLs in unsuspecting emails, SabPub creates and uses a launcher to keep the malware running. Then, it tries to upload personal data to remote servers.
The name SabPub comes from Backdoor.OSX.SapPub and tries to fool you into thinking it's legit, since there is an actual service called "PubSub" in OS X for syncing RSS feeds among devices (see the picture below). So, if you see something called PubSub or PubSubAgent running in your Activity Monitor, it's cool. If you see PubSab, it's not cool.
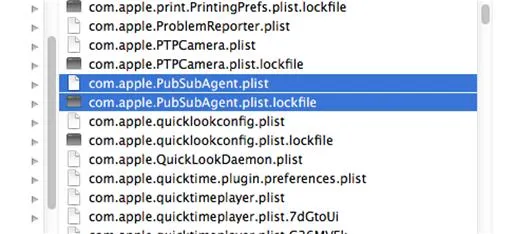
These files are OKAY. They are NOT the malware files!
There is also a "MacKontrol" variant of this malware to look for.
How to Check Your Mac for SabPub Malware
To see if you're infected with SabPub, navigate to the two files below in your Finder by opening up your user Library folder. The first plist one is the malware launcher, while the second pfile one is the process.
- Users/YOURNAME/Library/LaunchAgents/com.apple.PubSabAgent.plist
- Users/YOURNAME/Library/Preferences/com.apple.PubSabAgent.pfile
If they are present, delete them. You can also find and delete them directly from Terminal with these commands:
- rm ~/Library/LaunchAgents/com.apple.PubSabAgent.plist
- rm ~/Library/Preferences/com.apple.PubSabAgent.pfile
How to Check Your Mac for MacKontrol
There's also another malware to look for called MacKontrol, which can be found in the following places. Delete them if there.
- /Library/launched
- Users/YOURNAME/Library/launched
- Users/YOURNAME/Library/LaunchAgents/com.apple.FolderActionsxl.plist
Alternatively, use terminal to delete them directly:
- rm /Library/launched
- rm ~/Library/launched
- rm ~/Library/LaunchAgents/com.apple.FolderActionsxl.plist
Now Update Your Mac
Now, before you stop, make sure to update your Mac with the latest Java security update via Software Update, which will remove the most common variants of the Flashback malware. Also, make sure you're Microsoft Office is updated.
Next, log out of your computer and log back in to wipe the slate clean for your user account.
Tip for Time Machine Users
- If you use Time Machine, make sure to delete all of the questionable files there, too, then perform a fresh backup.
Photo by Travis Isaacs
























Comments
Be the first, drop a comment!