Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.
Networks scanners are recon tools for finding vulnerabilities and are often seen as the first stage in an attack. While primarily an information gathering tool, the Fing network scanner actually allows us to connect directly to a wide range of devices by guessing the password. In an advanced attack, Fing can be used to rapidly obtain targeting information to guide powerful, Hydra passwordcracking attempts.
Scanning a network with Fing can lead to many exciting discoveries because often the people who set up the network do so in ways that don't make any sense. In some setups, the "Guest" Wi-Fi network can even show you a page with the password to the second "Secure" Wi-Fi network in plain text, just by navigating to the router's IP address.
Sure, there are many fancier setups for exploiting access, but when physical access is limited, flexibly using your existing tools can be a lifesaver.
The essential things that Fing accomplishes are:
- Mapping a network by discovering all devices connected to it.
- Scanning discovered devices for OS information and open ports.
- Connecting directly to devices on the network with open ports by guessing or cracking the default password.
The first two bullets above provide the information to support an educated attempt to own devices on a network, or for targeting the router with a more advanced attack against the device, such as Routersploit. If you're interested in stumbling into security cameras, printer servers, wireless routers, and other random devices you'll find on networks, read on to learn what you need.
System Compatibility & Requirements
In this use-case, we will use the disclosure of a Wi-Fi password to quickly scan and fingerprint the network, identify and fingerprint a machine with an open HTTP port, and guess the model-specific default username and password to log in to the device. To do this, you will need any current iPhone or Android device.
While you can access any device with HTTP ports like 80 or 8080 open on your phone's browser, you will need an app to open SSH, FTP, and Telnet connections. Today, we will talk about HTTP, but I recommend Juice SSH, for connecting to other ports on Android, or Shelly, for use on the iPhone.

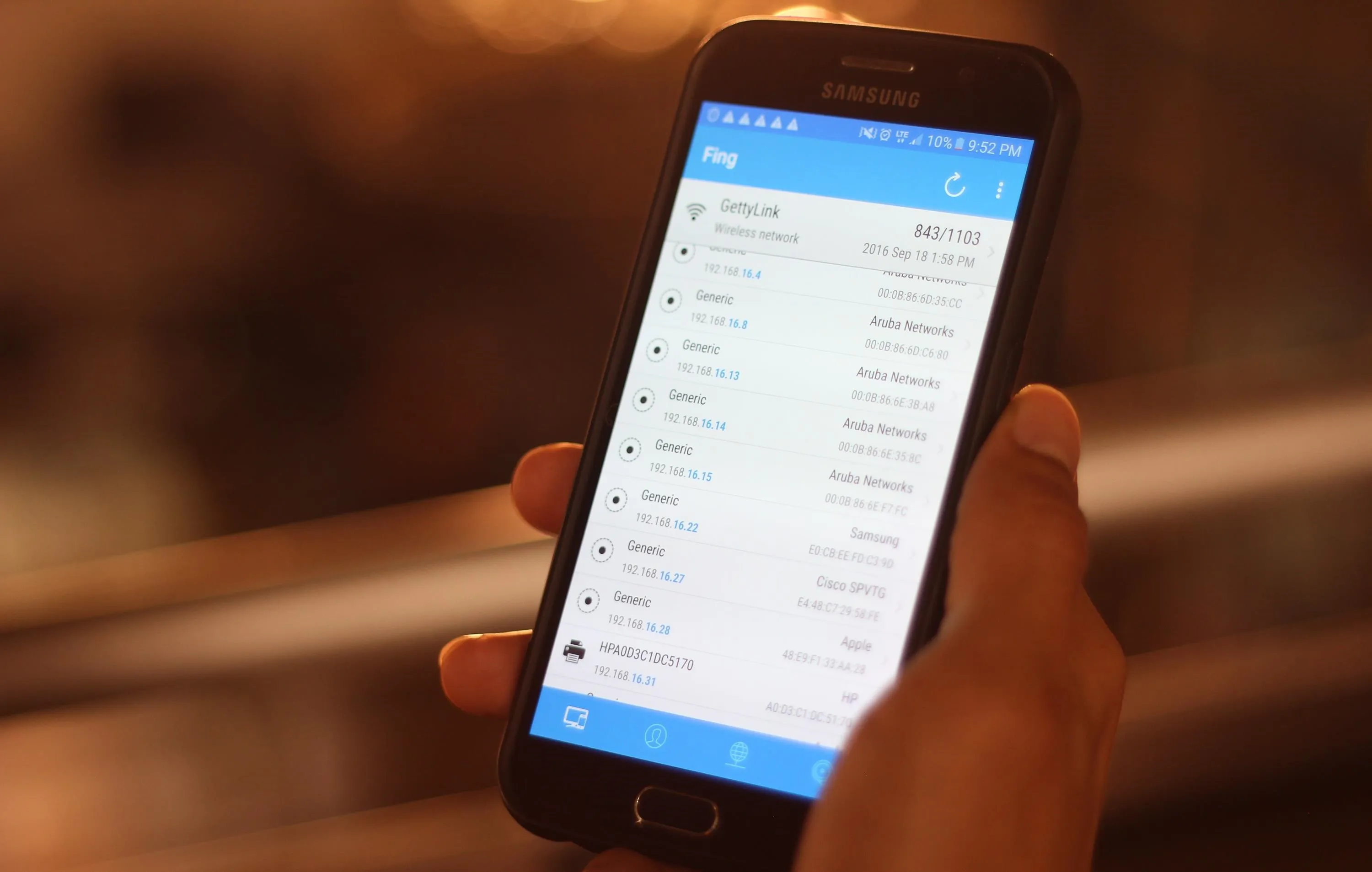
Using the Fing mobile app to explore new networks (1), to create list of devices to probe (2), and to scan an individual device (3).
SADMIN/Null Byte

SADMIN/Null Byte

Using the Fing mobile app to explore new networks (1), to create list of devices to probe (2), and to scan an individual device (3).

SADMIN/Null Byte

SADMIN/Null Byte
Install Fing on iOS or Android Phone
There are many network scanners for Windows, macOS, and Linux, but the best tool to use is often the one you know you'll have with you. Anything too big, specialized, or expensive you'll probably have left at home when you really need it.
That's why we're using the Fing mobile app here. When you have a moment of access to a target, or when you're given a Wi-Fi password unexpectedly, it can be trivial to gain access to many devices on a network with only a smartphone.
Fing works on both Android and iPhone and allows anyone to get started with mapping a network and connecting to devices on it. So use those links to install it on your device, and once you've connected to a Wi-Fi network, Fing will scan the entire network and give a detailed breakdown of each device connected to it.
- Play Store Link: Fing - Network Tools (free)
- App Store Link: Fing - Network Scanner (free)
Join the Wi-Fi Network on Your Phone
Politely ask for the Wi-Fi password of the network you want to scan. It's rare nowadays for someone not to give you this information. Once you have it, connect to the network on your smartphone, then launch the Fing app you just installed.
Fing can't scan a network it hasn't joined. For recon on networks you don't have the password to, check out our article on Wardriving.
Scan the Entire Wi-Fi Network
In the Fing app, start a new network scan by tapping the round arrow icon in the top right to identify all devices on the current network.
Fing performs a scan against a range of all potential IP addresses based on the IP of the network you are connected to. While doing so, it compares the information found against device fingerprints and displays the result in an easy to understand graphical display of all attached devices.
Look for important devices like routers, servers, and desktop computers.
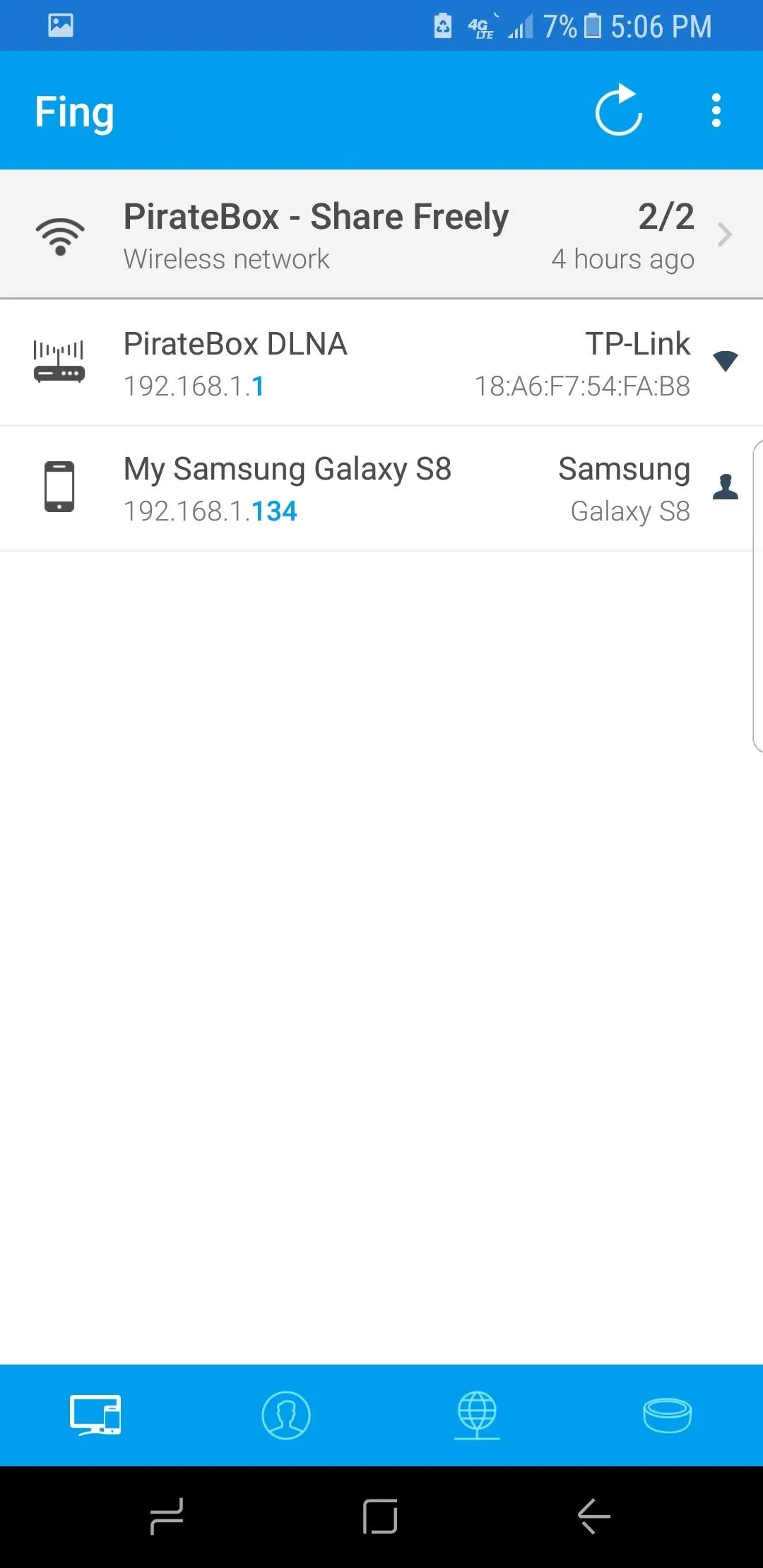
Most public wireless networks will not assign you to an isolated subnet, allowing you to interact with sometimes hundred of devices.

Most public wireless networks will not assign you to an isolated subnet, allowing you to interact with sometimes hundred of devices.

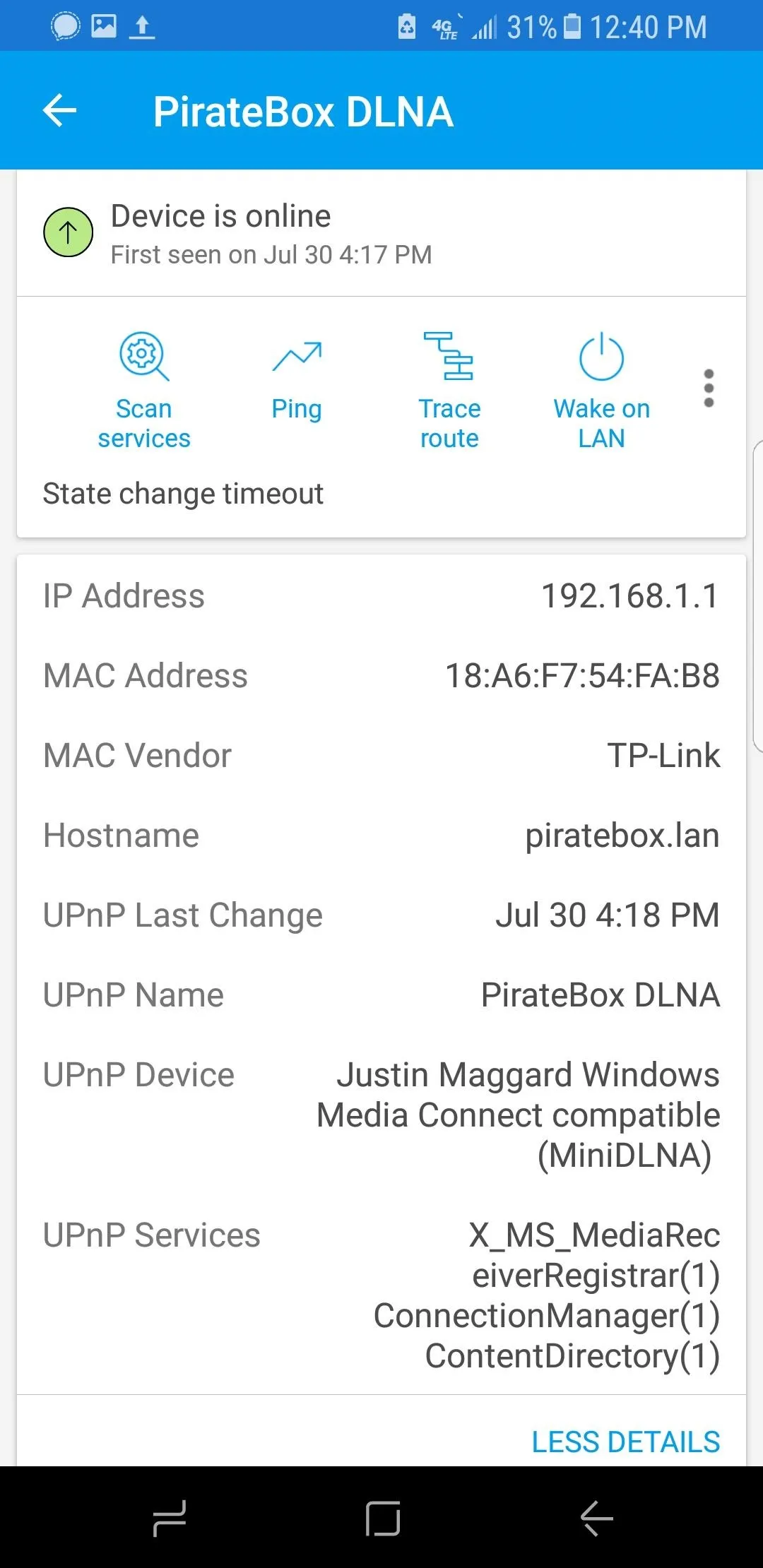
Port Scan a Targeted Device
Selecting a specific device allows you to scan it and find open ports. Just tap on the "Scan Services" option to start the scan. It will probably take longer than the main network scan performed in the previous step.
Scanning a device can tell you a lot about the services it offers. Below, we see a scan of a Raspberry Pi with SSH and a web server with port 80 enabled. Ports 22, 80, and 443 are open.
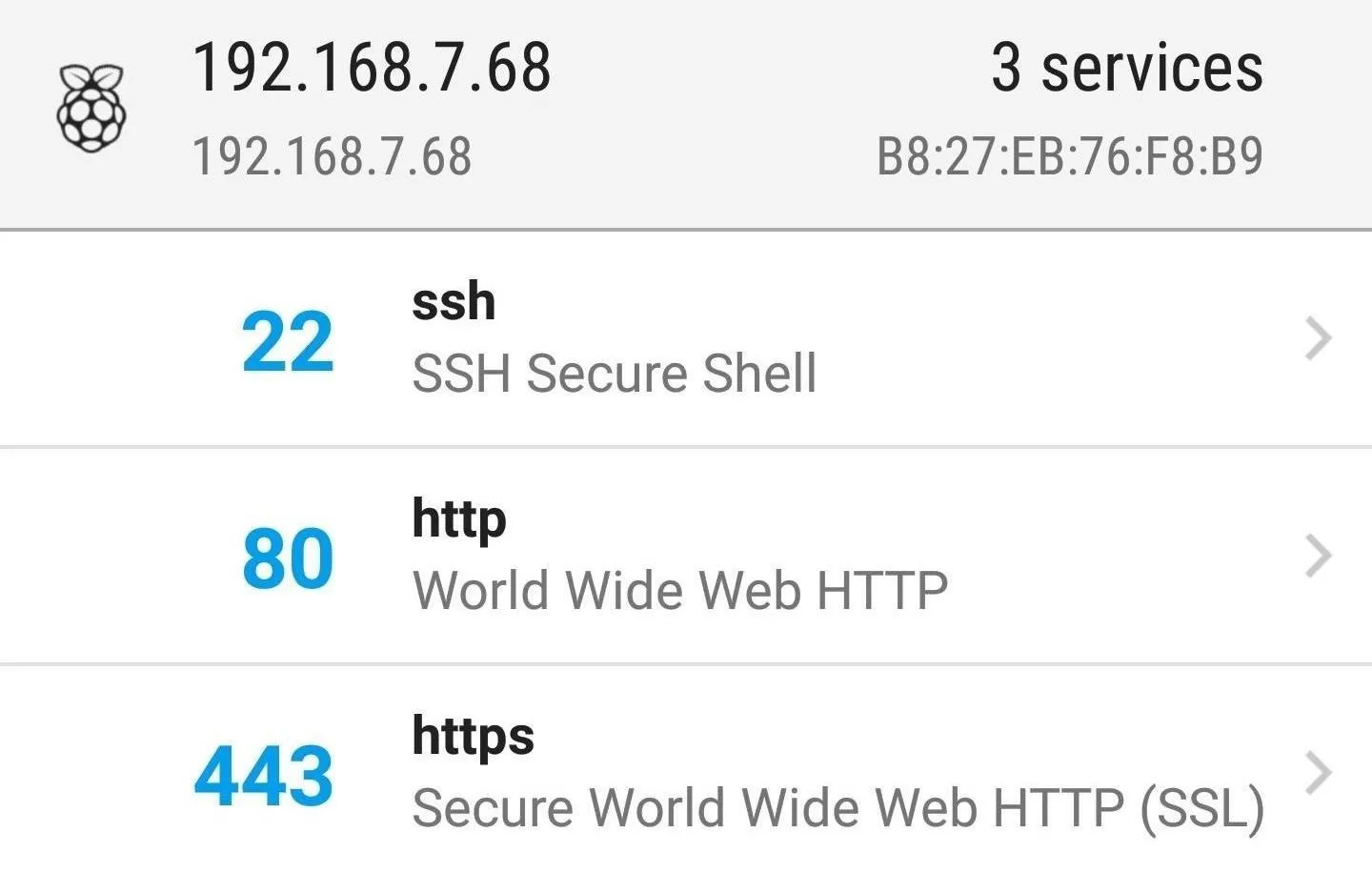
Scan of a Raspberry Pi computer. Of course, using default passwords.
Any port you find open means an opportunity to probe further into the device. Once you see a device with port 80, 8080, or 443 open, you can tap on it to open it in your browser.
Identify the Device
Login pages, combined with the information from our Fing scan, can give detailed information on the device manufacturer and often the model number. If you've ever run an "advanced" Google search, you know this is a bad idea, since you can just look up the default password (which we'll talk about in the next step).
In one of my scans, I found an Arris router. On its login page, the default username is quickly shown (as "admin"). Plus, the "HSD" tab shows us the model number and even serial number.
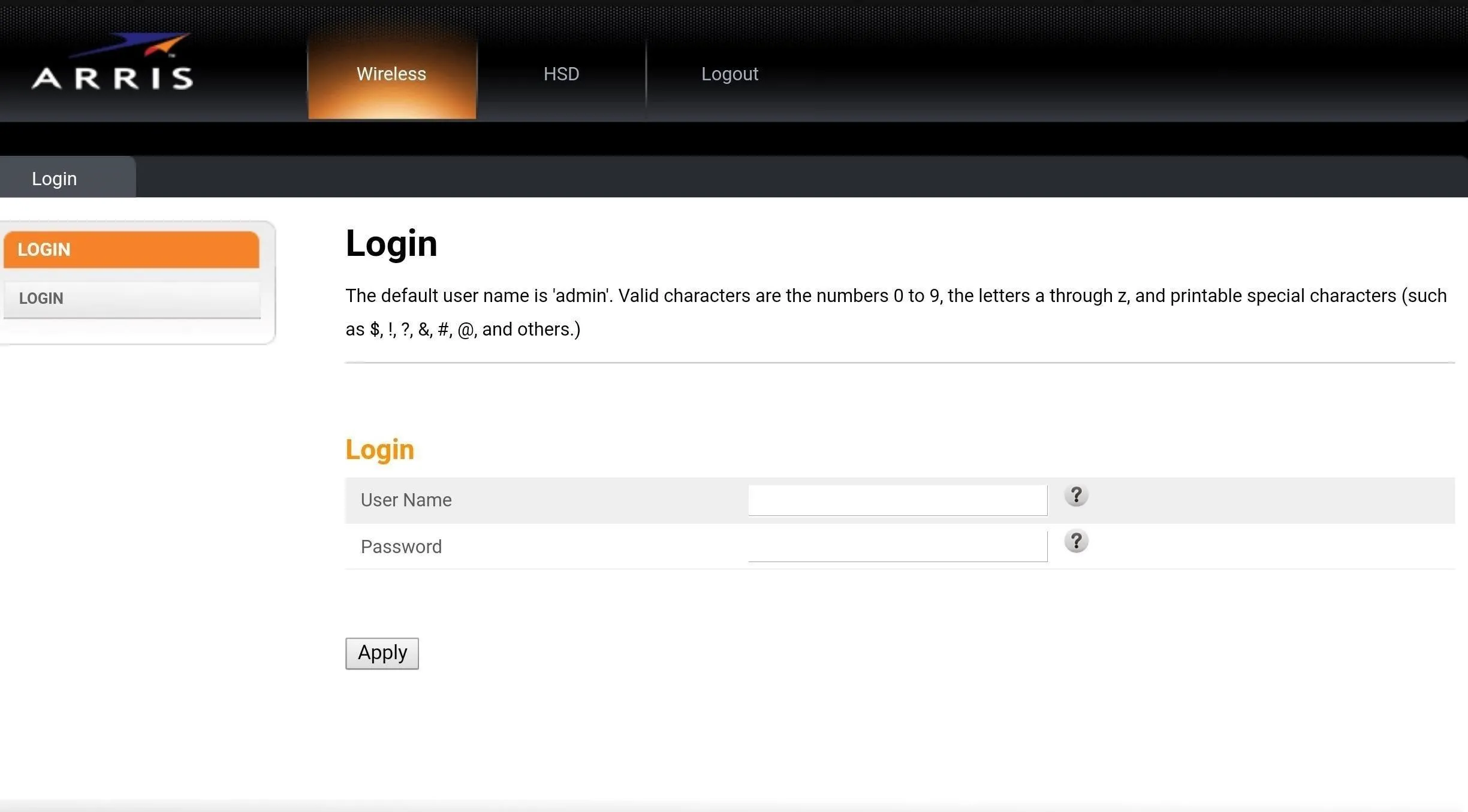
Device configuration pages often give away way too much information, as this Arris router helpfully provides us the default username.
Find the Default Username & Password for the Device
A simple Google search will give you the default credentials for that particular model. Enter the default username and password to test if the device has been properly configured. It probably hasn't.
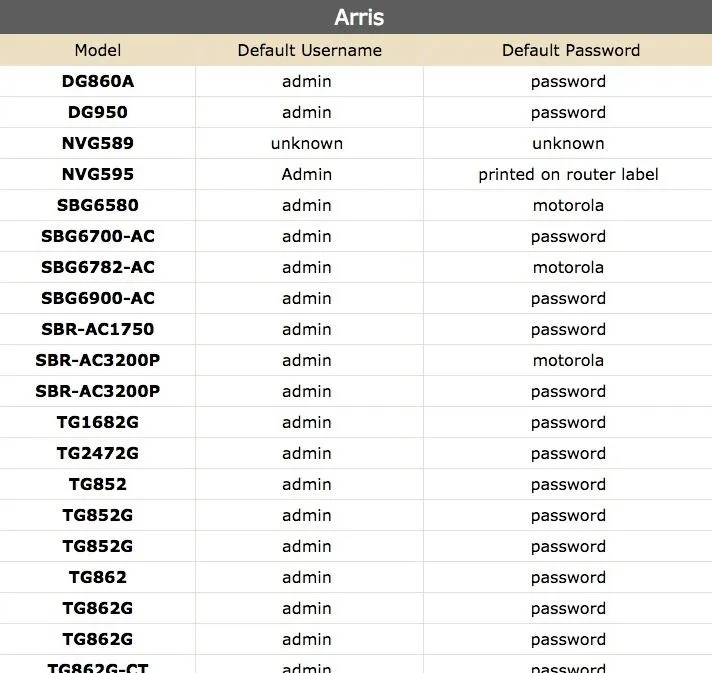
Unless your device is one specific model of router, odds are the password is password. Creative thinking, Arris!
By far the most common logins across all devices are:
- Username: root, admin, user, and super.
- Password: password, (blank), toor, super, admin, user, and root.
Some Warnings on Finging
One thing you'll learn about life is not everyone likes being Finged. Some organizations with IT departments or IDS systems can get quite upset about being Finged by surprise and without permission. As a result, it's wise to not go around Finging every open port if you don't know who might get upset about it, just as in life in general.
In particular, counter-cybercrime training provided to technology companies by the US government targets employees for heightened scrutiny and potential reporting to federal agencies if they become concerned about your behavior on company networks. Port scanning company networks is seen as suspicious and indicative of either espionage or crime. If you work at a company like this, and you're using your phone, keep your Fingers to yourself at work.
Accessing a device without permission is a crime, so while you may have permission to use the internet, "using" typically does not cover logging into the router and changing settings. Like any port scan, Fing will leave traces in the router logs and may trigger a firewall or IDS to block you.
You can ask me questions here or @sadmin2001 on Twitter or Instagram.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by SADMIN/Null Byte

























Comments
Be the first, drop a comment!