Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.
For hackers or OSINT researchers gathering digital evidence, photos can be a rich source of data. Besides what's visible in the picture itself, metadata about when and where the photo was taken can also be recoverable. This data can include the device the photo was taken on, the geolocation of the image, and other unique characteristics that can fingerprint an image as haven been taken by the same person or device.
Metadata, or the data that describes files like images or videos, is useful during reconnaissance to investigators because it's often overlooked by otherwise careful targets. If people don't know what kind of data can be retained in a particular file format, they won't know if they're putting themselves at risk by making a specific file public. While many social media platforms have largely eliminated this problem by stripping out metadata from files, there are still many images online with this data left entirely intact.
Exif Data in Images
Exchangeable image file format data, or Exif data, is information that accompanies image files and offers many fields that can be populated or left blank. The information is used by programs to understand better what is contained inside the file to aid in sorting and other functions. Available data fields in Exif are often written to by the device that took the image at the time it was shot but can also be left by processing programs like Photoshop.
Because we can often identify the model of camera used, the settings used, and supplementary information like the owner of the software that made Photoshop changes, it's possible to identify images that came from the same source. The more Exif fields are filled out by the device that shot the image or software that processed it, the easier it is to track other files made by the same process.
The full list of fields that are supported by the Exif standard is quite extensive. Aside from manufacturer-specific information, fields like the owner's name and address can be populated by image processing software without the author knowing each image they produce contains this information.
What You'll Need
While an older Null Byte article on Exif data features a dated Windows-only tool that still works, we'll focus only on a program that's pre-installed on Kali Linux, as well as a few tools that'll work on any system right from a web browser.
Use the Exif Command Line Tool
To start, we'll be using the "exif" tool that comes pre-installed in Kali Linux. This program is the command line front-end to "libexif," and it only works on JPG file types. To see the options available to us, we can run the exif --help command to list the included options.
If you receive an error, or if you're using another OS like Debian or Ubuntu, open a new terminal window and type apt install exif to install the program and any needed dependencies. Similarly, you can install this tool by typing brew install exif on a MacOS device. Then, try exif --help again.
You can use man exif to view even more information about the tool.
~$ exif --help
Usage: exif [OPTION...] file
-v, --version Display software version
-i, --ids Show IDs instead of tag names
-t, --tag=tag Select tag
--ifd=IFD Select IFD
-l, --list-tags List all EXIF tags
-|, --show-mnote Show contents of tag MakerNote
--remove Remove tag or ifd
-s, --show-description Show description of tag
-e, --extract-thumbnail Extract thumbnail
-r, --remove-thumbnail Remove thumbnail
-n, --insert-thumbnail=FILE Insert FILE as thumbnail
--no-fixup Do not fix existing tags in files
-o, --output=FILE Write data to FILE
--set-value=STRING Value of tag
-c, --create-exif Create EXIF data if not existing
-m, --machine-readable Output in a machine-readable (tab delimited) format
-w, --width=WIDTH Width of output
-x, --xml-output Output in a XML format
-d, --debug Show debugging messages
Help options:
-?, --help Show this help message
--usage Display brief usage messageWhile all of the options is a lot to process, the most straightforward application of this tool is to type exif and then the path to the file you want to inspect. Below, a photo that's been processed in Photoshop retains information about the software that modified it, the computer it was modified on, and the camera it was taken on. If you get a "corrupt data" error, there may be no metadata in the file or you're scanning a file that's not a JPG.
-$ exif /Users/skickar/Downloads/Vacaynev-28.jpg
EXIF tags in '/Users/skickar/Downloads/Vacaynev-28.jpg' ('Intel' byte order):
--------------------+----------------------------------------------------------
Tag |Value
--------------------+----------------------------------------------------------
Manufacturer |Canon
Model |Canon EOS 60D
X-Resolution |300
Y-Resolution |300
Resolution Unit |Inch
Software |Adobe Photoshop Lightroom 5.6 (Macintosh)
Date and Time |2016:11:25 17:45:11
Compression |JPEG compression
X-Resolution |72
Y-Resolution |72
Resolution Unit |Inch
Exposure Time |1/100 sec.
F-Number |f/4.0
Exposure Program |Manual
ISO Speed Ratings |640
Exif Version |Exif Version 2.3
Date and Time (Origi|2016:11:25 02:56:54
Date and Time (Digit|2016:11:25 02:56:54
Shutter Speed |6.64 EV (1/99 sec.)
Aperture |4.00 EV (f/4.0)
Exposure Bias |0.00 EV
Maximum Aperture Val|3.00 EV (f/2.8)
Metering Mode |Pattern
Flash |Flash did not fire, compulsory flash mode
Focal Length |17.0 mm
Sub-second Time (Ori|00
Sub-second Time (Dig|00
Color Space |sRGB
Focal Plane X-Resolu|5728.177
Focal Plane Y-Resolu|5808.403
Focal Plane Resoluti|Inch
Custom Rendered |Normal process
Exposure Mode |Manual exposure
White Balance |Auto white balance
Scene Capture Type |Standard
FlashPixVersion |FlashPix Version 1.0
--------------------+----------------------------------------------------------
EXIF data contains a thumbnail (16091 bytes).Information can also include geolocation data, as exact coordinates, which is supplied by the device that took the photo. If the photo was taken on a phone, there is a much higher chance that it includes geotags.
As it is in the output above, we've learned that the person who created this file is using a Canon EOS 60D camera, has a lens with a focal length of 17.0 mm, worked on the file in Lightroom, and uses a Mac computer. That's a lot from a simple image file!
Use Jeffrey's Image Metadata Viewer Web App
If you're using a browser, there are two great free websites to extract Exif data. First, let's start with Jeffrey Friedl's Image Metadata Viewer over at exif.regex.info. The site does not use HTTPS, unfortunately. If you don't mind that, you can see the simple design is easy to use and supports a vast variety of formats, unlike the command line tool which only works with JPG files. So you can scan RAW images files like CR2 and DNG, PNG, and TIFF, to name a few.
Upload a file or add its public URL, check the CAPTCHA, and hit "View Image Data."
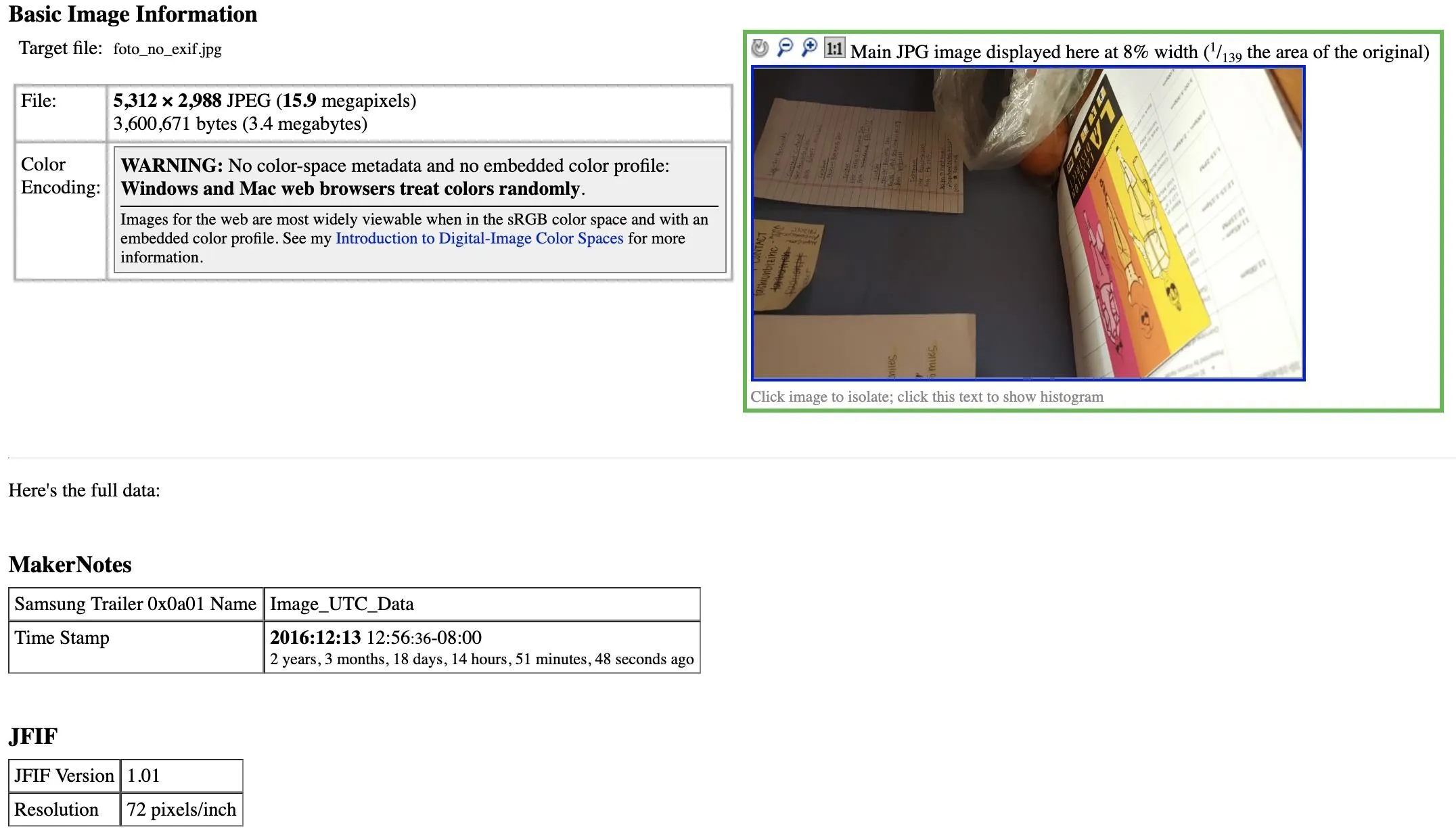
Once you scan a file, you should see a decent amount of information if it came from a smartphone. In my example below, a photo that's over two years old contained a GPS location.
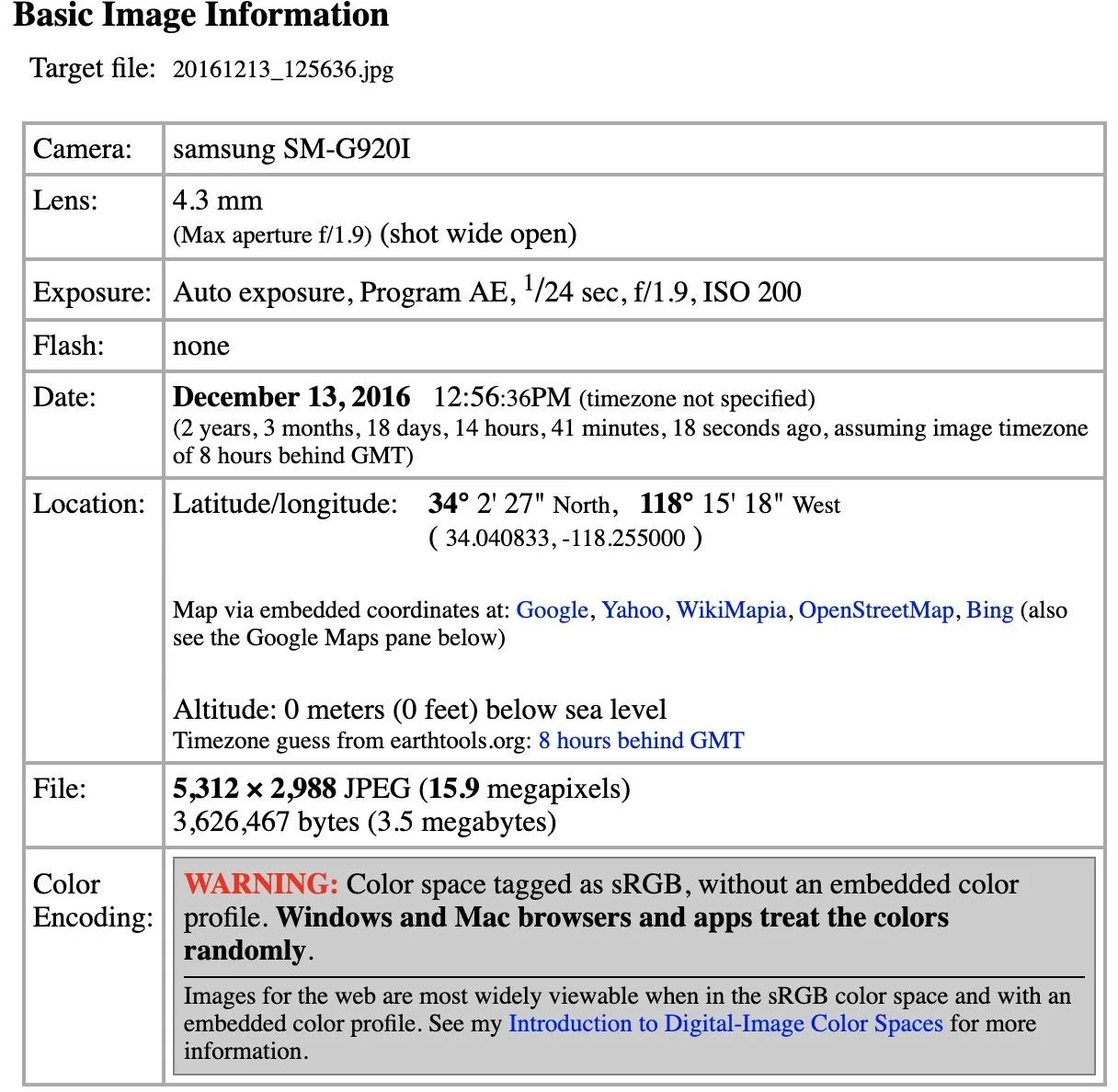
The actual amount of data captured takes up several pages and is quite extensive.
EXIF
Make samsung
Camera Model Name SM-G920I
Software G920IDVS3EPK1
Modify Date 2016:12:13 12:56:36
2 years, 3 months, 18 days, 15 hours, 41 minutes, 18 seconds ago
Y Cb Cr Positioning Centered
Exposure Time 1/24
F Number 1.90
Exposure Program Program AE
ISO 200
Exif Version 0220
Date/Time Original 2016:12:13 12:56:36
2 years, 3 months, 18 days, 15 hours, 41 minutes, 18 seconds ago
Create Date 2016:12:13 12:56:36
2 years, 3 months, 18 days, 15 hours, 41 minutes, 18 seconds ago
Shutter Speed Value 1/24
Aperture Value 1.90
Brightness Value 0.27
Exposure Compensation 0
Max Aperture Value 1.9
Metering Mode Spot
Flash No Flash
Focal Length 4.3 mm
Image Size 5,312 × 2,988
Maker Note Unknown (98 bytes binary data)
User Comment
Flashpix Version 0100
Color Space sRGB
Exposure Mode Auto
White Balance Auto
Focal Length In 35mm Format 28 mm
Scene Capture Type Standard
Image Unique ID A16LLIC08SM A16LLIL02GM
GPS Version ID 2.2.0.0
GPS Latitude Ref North
GPS Latitude 34.040833 degrees
GPS Longitude Ref West
GPS Longitude 118.255000 degrees
GPS Altitude Ref Below Sea Level
GPS Altitude 0 m
GPS Time Stamp 20:56:27
GPS Date Stamp 2016:12:13
2 years, 3 months, 19 days, 4 hours, 37 minutes, 54 seconds ago
Image Width 512
Image Height 288
Compression JPEG (old-style)
Orientation Rotate 90 CW
Resolution 72 pixels/inch
Thumbnail Length 11,484
Thumbnail Image (11,484 bytes binary data)
MakerNotes
Unknown 0x0001 0,100
Unknown 0x0002 73,728
Unknown 0x000c 0
Unknown 0x0010 undef
Unknown 0x0040 0
Unknown 0x0050 1
Unknown 0x0100 0
Samsung Trailer 0x0a01 Name Image_UTC_Data
Time Stamp 2016:12:13 12:56:36-08:00
2 years, 3 months, 18 days, 14 hours, 41 minutes, 18 seconds ago
File — basic information derived from the file.
File Type JPEG
MIME Type image/jpeg
Exif Byte Order Little-endian (Intel, II)
Encoding Process Baseline DCT, Huffman coding
Bits Per Sample 8
Color Components 3
File Size 3.5 MB
File Type Extension jpg
Image Size 5,312 × 2,988
Y Cb Cr Sub Sampling YCbCr4:2:2 (2 1)
Composite
This block of data is computed based upon other items. Some of it may be wildly incorrect, especially if the image has been resized.
GPS Latitude 34.040833 degrees N
GPS Longitude 118.255000 degrees W
GPS Altitude 0 m Above Sea Level
Aperture 1.90
GPS Date/Time 2016:12:13 20:56:27Z
2 years, 3 months, 18 days, 14 hours, 41 minutes, 27 seconds ago
GPS Position 34.040833 degrees N, 118.255000 degrees W
Megapixels 15.9
Shutter Speed 1/24
Light Value 5.4
Scale Factor To 35 mm Equivalent 6.5
Circle Of Confusion 0.005 mm
Field Of View 65.5 deg
Focal Length 4.3 mm (35 mm equivalent: 28.0 mm)
Hyperfocal Distance 2.11 mUse Ver Exif's Web App
Our second website, Ver Exif at verexif.com, spits out all of the Exif data after a scan, but it also comes with an option to strip metadata out of images. Removing the metadata is useful if you want to make sure an image you're sending doesn't contain data you didn't intend to send.
- Don't Miss: How to Hide Data in Audio Files Like Mr. Robot
To view Exif information, upload a file or add its public URL, then hit "View Exif." In my example, passing the same photo into this website, the output is much less, but it generates a handy map of where the photo was taken. The information is accurate, but not as big of a data dump as the Image Metadata Viewer web app.
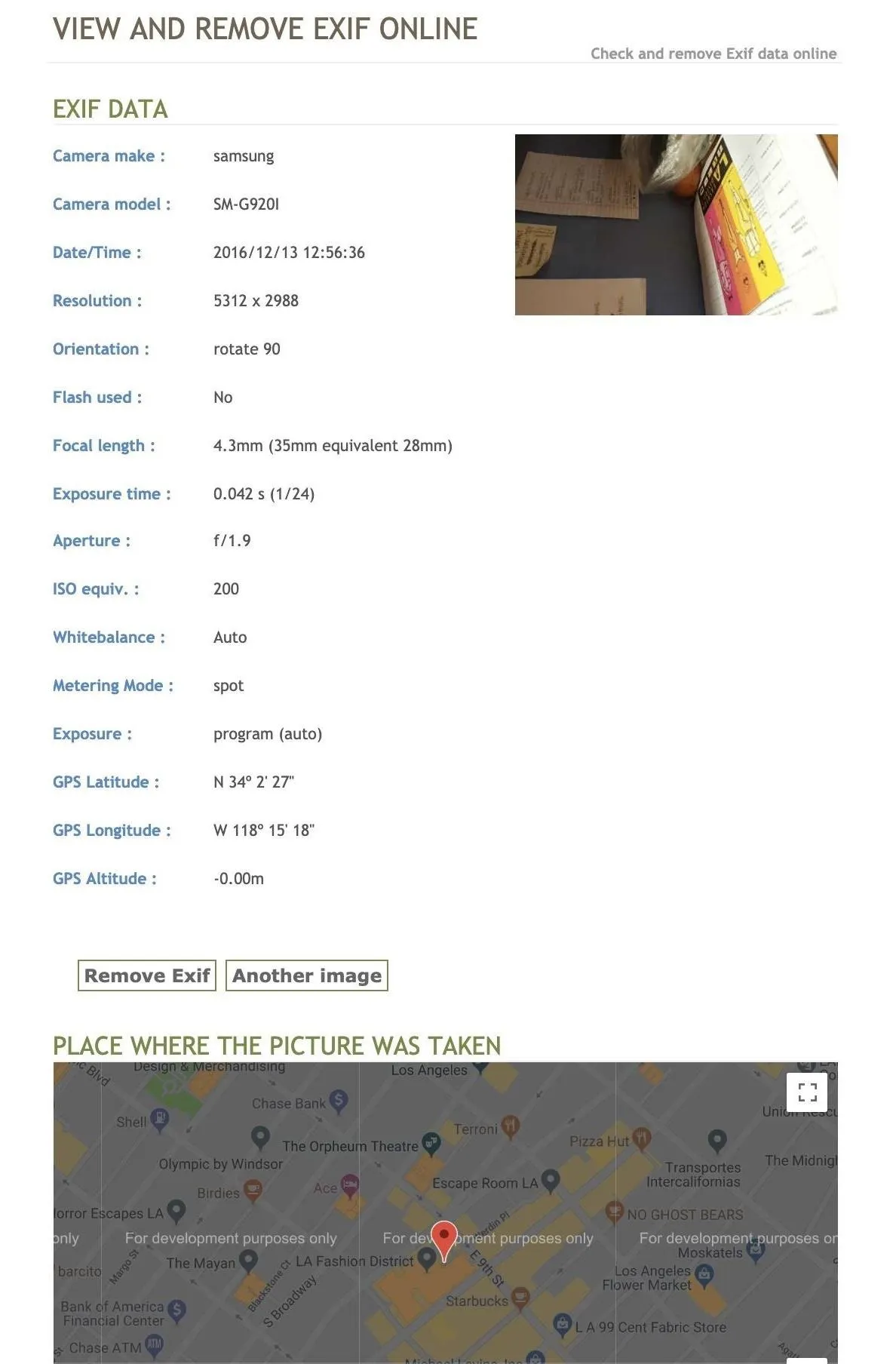
Interestingly, after I passed the test photo through the "Remove Exif" data option, I uploaded it to the first website to see if the metadata was truly removed. It turns out I can still tell it was taken on a Samsung device, so I don't recommend using this tool to strip metadata from your photos.
Use the EXIF Viewer Chrome Extension
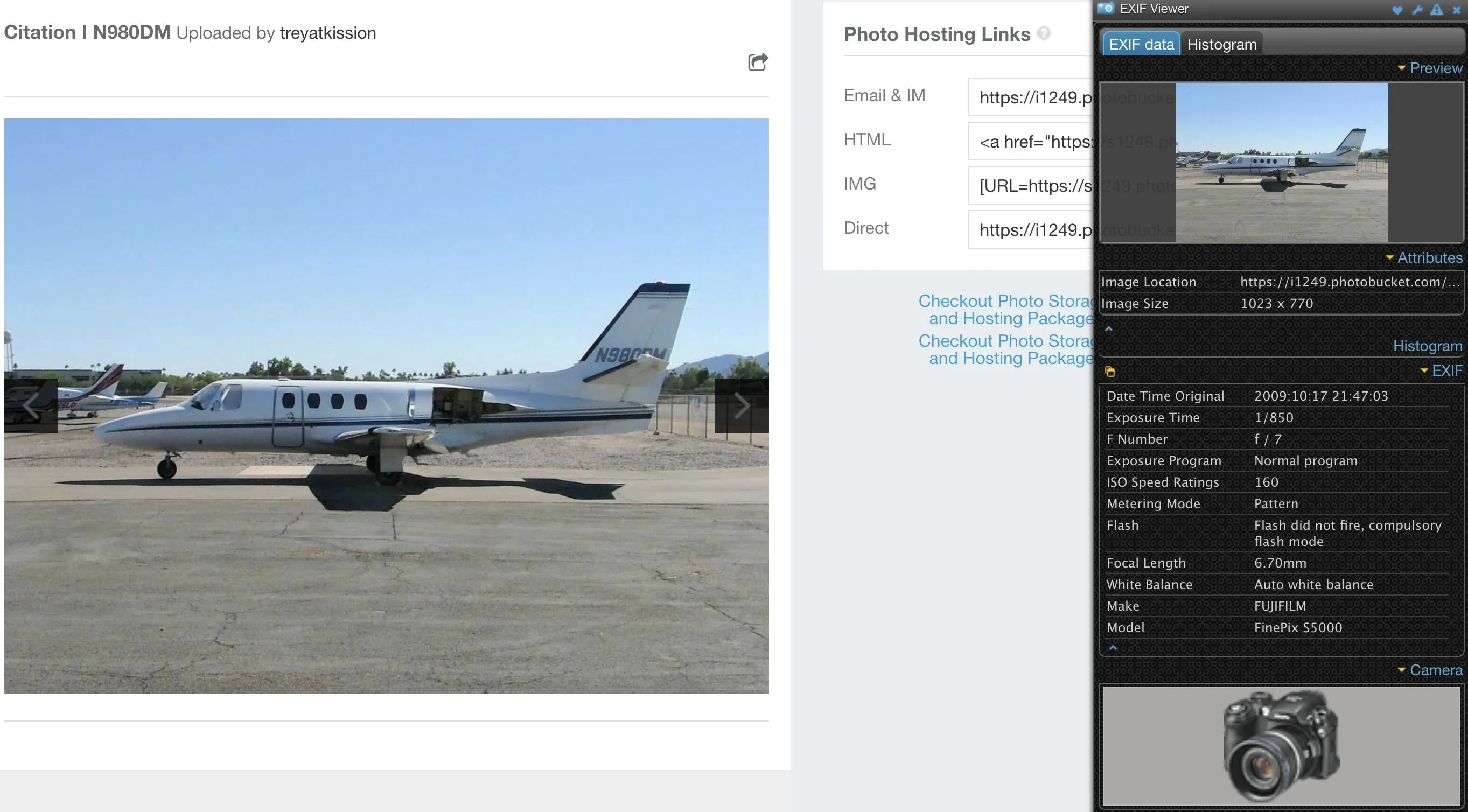
In Google Chrome, you can install the EXIF Viewer extension, which will let you pull up the Exif data from any photo you load into the browser.
Using browser add-ons to extract Exif data is even simpler than using a web-based tool. After installing and enabling the plug-in, we can right-click any image in the browser and select "Show EXIF data" to reveal any information the image contains.
To test this out, I found a random image on a photo-sharing website and looked through the metadata provided by EXIF Viewer to find the type of camera that was used to take it.
Use the Exif Viewer Firefox Add-On
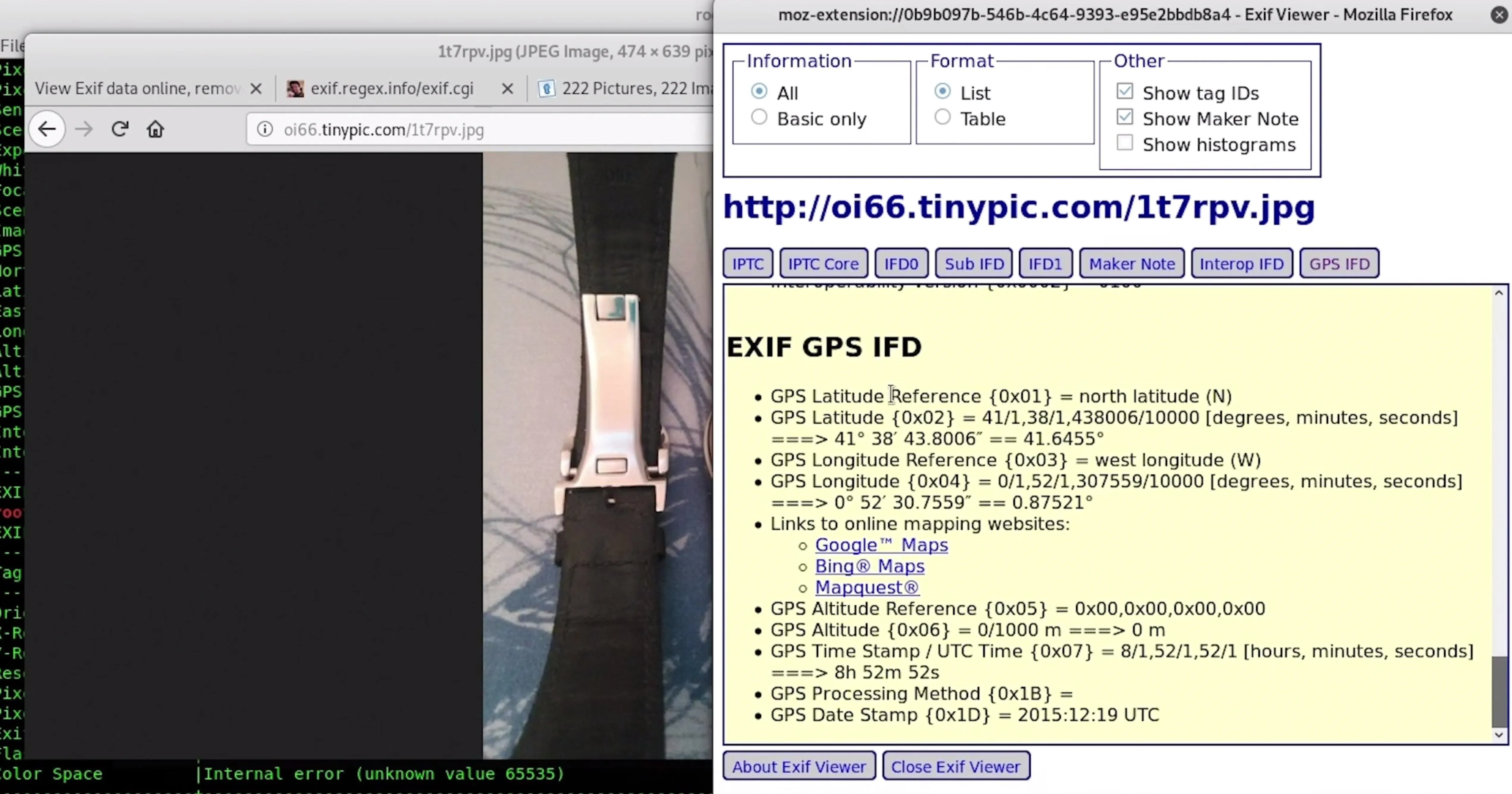
You could also install the Exif Viewer add-on for Firefox, developed by Alan Raskin, which allows similar functionality as the Chrome extension above. After installing and enabling the add-on, right-click on an image in your browser, then click on "Exif Viewer."
A pop-up window appears, where there's a slew of metadata to sort through. You can see the link to the image; in the GPS section you get links to open up the location on Google Maps, Bing Maps, and Mapquest; and all of the other helpful information in the Exif data.
In general, browser extensions are a great way to tackle extracting Exif data, because you can also open photos in a browser window and use an extension to read the data inside.
Metadata Reveals the Story Behind a Photo
While a photo may yield valuable information, the real value may be in what's encoded in the metadata. Accessing this data is easier than ever, so it's essential to be aware of what information you may be giving away when you send a photo.
While many social media platforms and photo-hosting services do you the favor of stripping out this data, not all do. It's important to make sure you're not leaking this data if you don't intend to, and these tools can quickly help you identify any ways you might be leaking your location or other private data in photos you want to share online. Most importantly, make sure to disable geo-encoding on your phone if you don't want GPS coordinates burned into every image you take.
I hope you enjoyed this guide to extracting hidden metadata from image files! If you have any questions about this tutorial on image OSINT or you have a comment, ask below or feel free to reach me on Twitter @KodyKinzie.
Cover photo by Justin Meyers/Null Byte; Screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!