In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
The Key Reinstallation Attack method is a hack which affects both sides of your Wi-Fi networks. Your gadgets like computers, phones, game consoles, and other smart devices, as well as your wireless access point (or router, as most home users call it). As such, practically everything in your house that connects to Wi-Fi will need to be patched in different ways.
This attack's effect is extremely wide, as it affects practically every wireless network in use.
[A]ttackers can use this novel attack technique to read information that was previously assumed to be safely encrypted. This can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on. The attack works against all modern protected Wi-Fi networks.
A more thorough analysis of the attack is available in the Null Byte link below and at the researcher's own website.
Update Your Computers
Fortunately, the researchers behind the attack were kind enough to preemptively warn hardware manufacturers before releasing the exploit to the public. As of right now, there have been no recorded incidents of the attack being used, but as soon as tools become public, there is an extreme potential for targeted damage. First, we should update our operating systems.
Windows has already released a patch for this vulnerability, and while it can be downloaded directly from this page, it should be included in system updates. On Windows 10, updates can be checked for through the Settings window under the "Update & Security" menu. On prior Windows versions, this is available through the Control Panel within the System and Security category as "Windows Update."
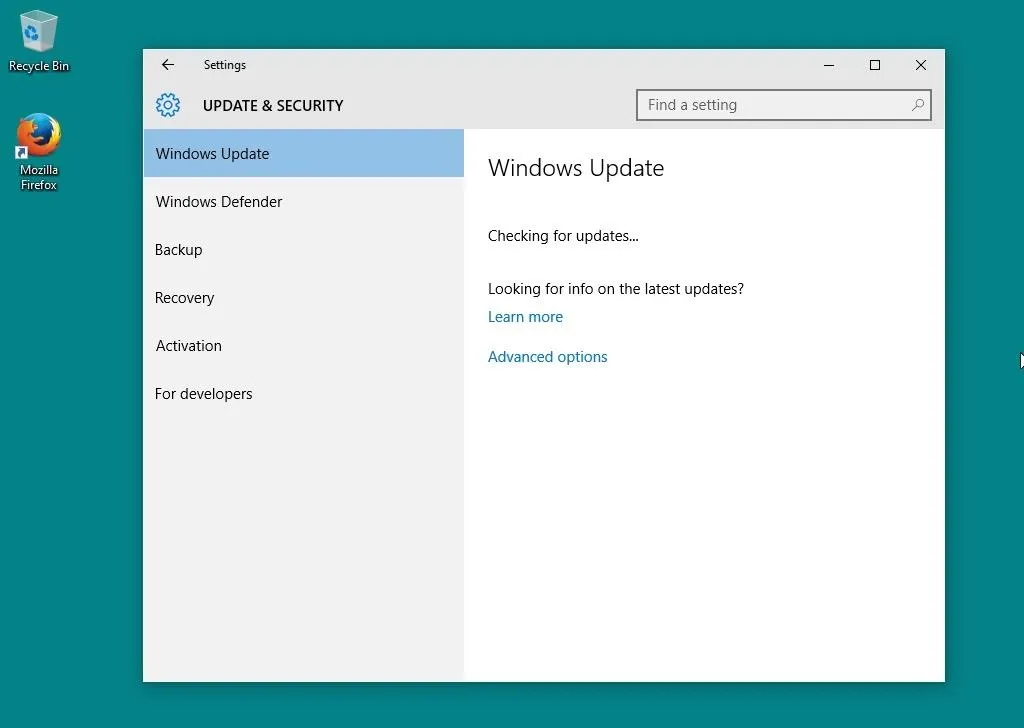
On macOS (previously Mac OS X), within the Apple menu, open "System Preferences" and select "App Store" from the list. Ensure that "Automatically check for updates" is enabled and your system is up to date.
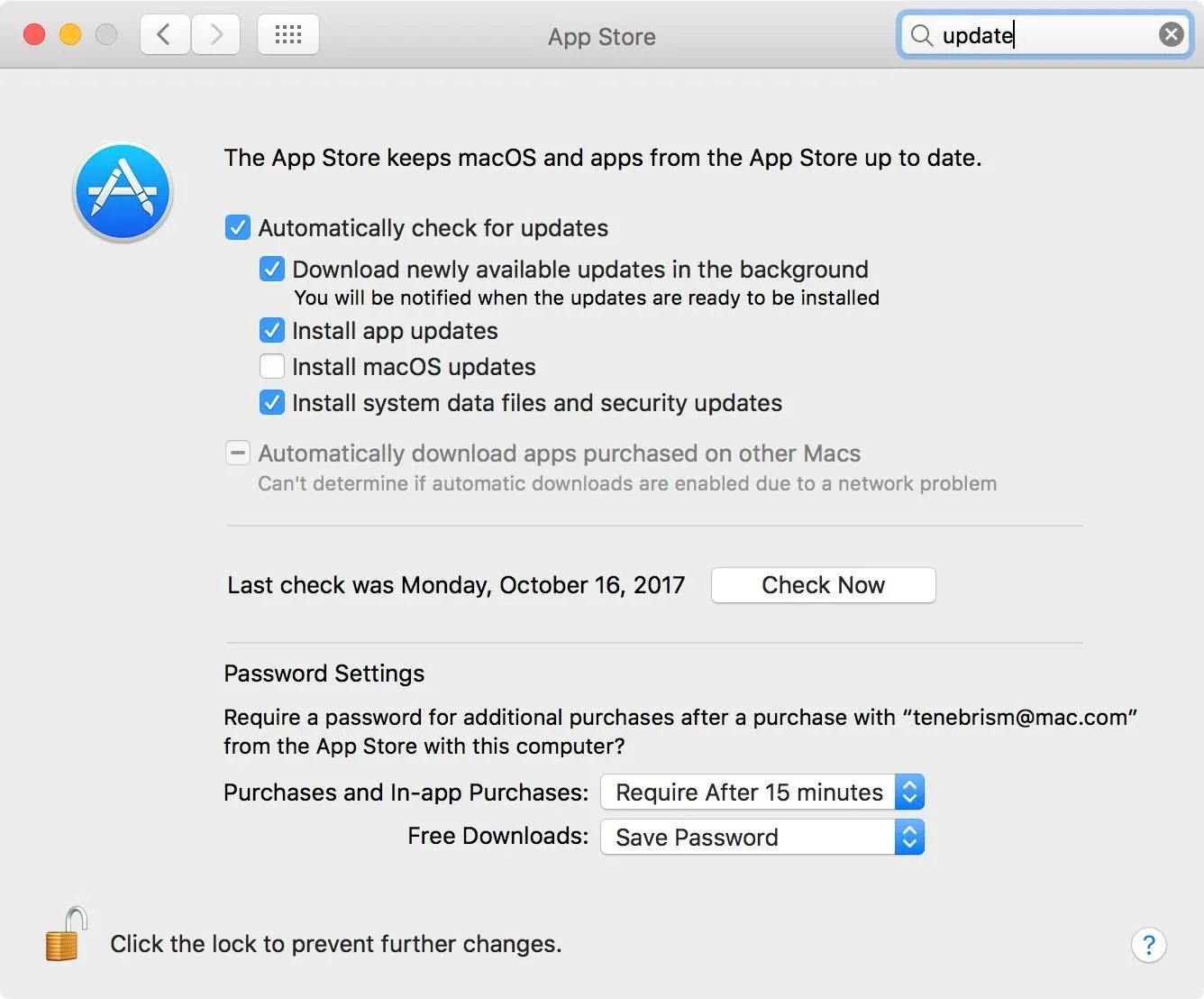
If you are using Linux, a patch is already available and ported to several distributions. On Debian-based systems like Ubuntu, we can update our system using apt.
sudo apt-get update && sudo apt-get upgrade
Update Your Mobile Devices
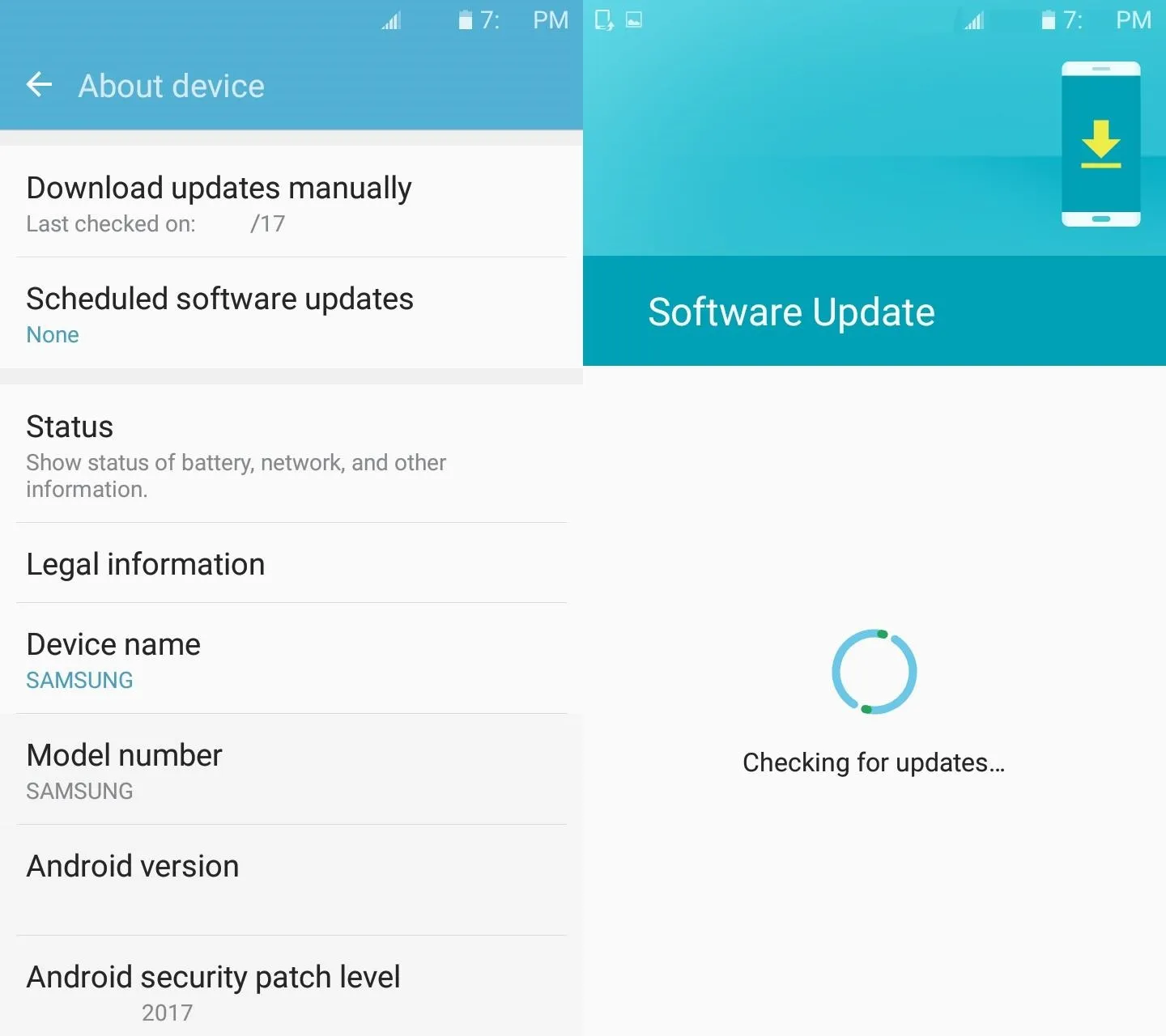
Mobile devices are vulnerable as well, so be sure to keep them updated. On Android, updates can be checked for and installed within the "About device" or "About phone" section of the Settings menu. Specifically look at "Download updates manually" and "Android security patch level" to make sure that your phone is up to date.
Unfortunately, Google will not be releasing a patch for this exploit until November 6 (and even then, that will only go out to their latest stock Android devices). As such, if you use an Android phone, your only option is to disable Wi-Fi and use your cellular data if you're doing something online that you're worried others may be eavesdropping on. Just remember, in order to execute the attack, someone will have to have a device physically in between you and the router.
On iOS devices, such as iPhones and iPads, you would go to "General" in the Settings app, then select "Software Update." If there is an update, you should update immediately.


Update Your Routers
According to the researchers which uncovered the vulnerability, the primary concern for security rests in the clients which connect to wireless networks.
Our main attack is against the 4-way handshake, and does not exploit access points, but instead targets clients. So it might be that your router does not require security updates. We strongly advise you to contact your vendor for more details. In general though, you can try to mitigate attacks against routers and access points by disabling client functionality (which is for example used in repeater modes) and disabling 802.11r (fast roaming). For ordinary home users, your priority should be updating clients such as laptops and smartphones.
Nonetheless, routers are indeed a part of the attack, and one of the trickier things to upgrade.
If you want to do this the easy way, check out our guide on using Fing, which you can run on any smartphone. You can see our guide to network mapping on Fing at the link below.
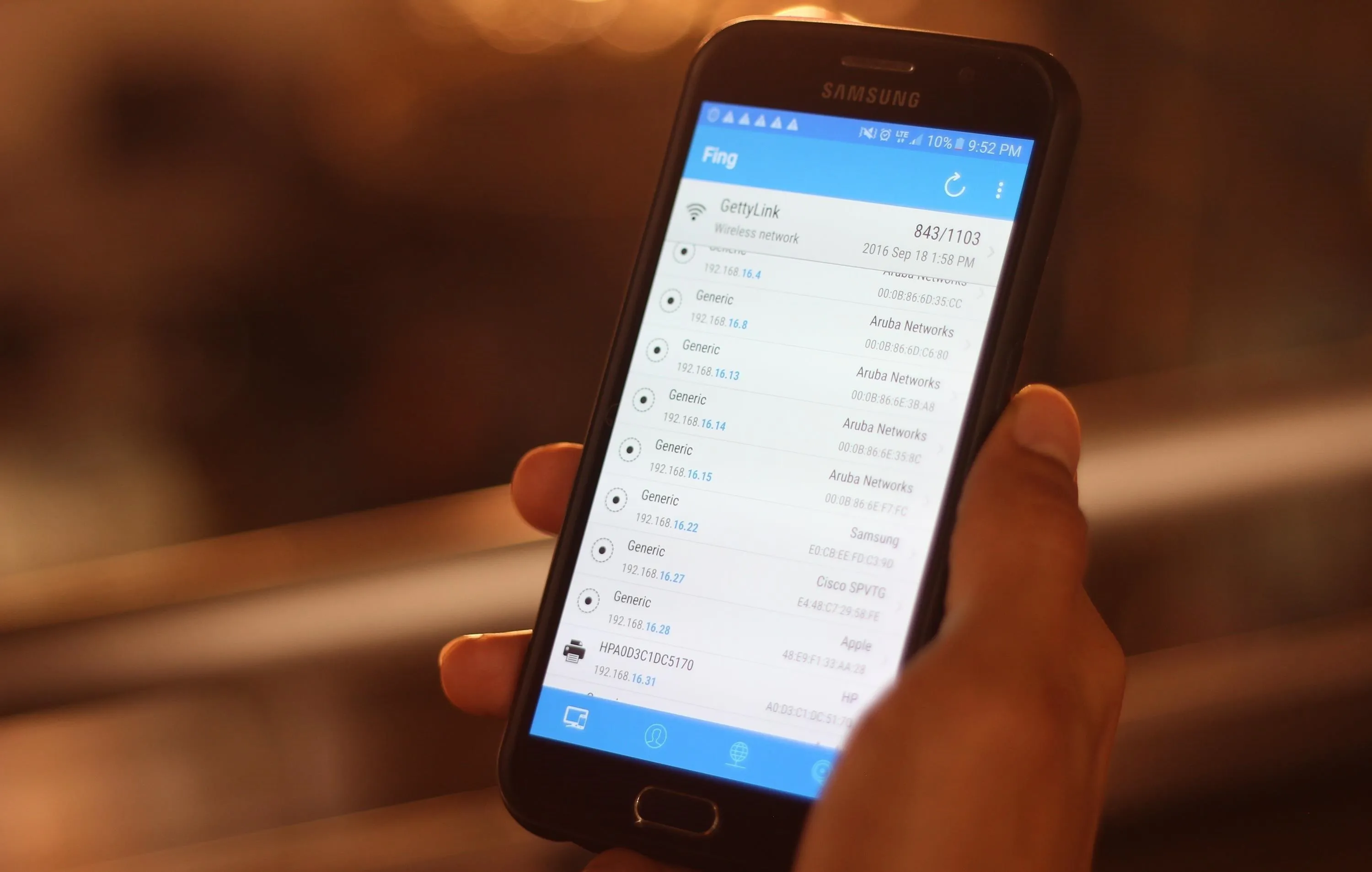
Discovering devices on the network with Fing.
Routers are usually administrated through a web-browser focused access panel. This panel is usually accessed by entering the local address of the router within the network, usually 192.168.0.1 or 192.168.1.1 in some cases. If you're on your personal network, you can check the existence of either page by clicking one of these links. If not, we can check the location of the router on Windows by running ipconfig. First, open a Command Prompt window, and then run the following command.
ipconfig/all
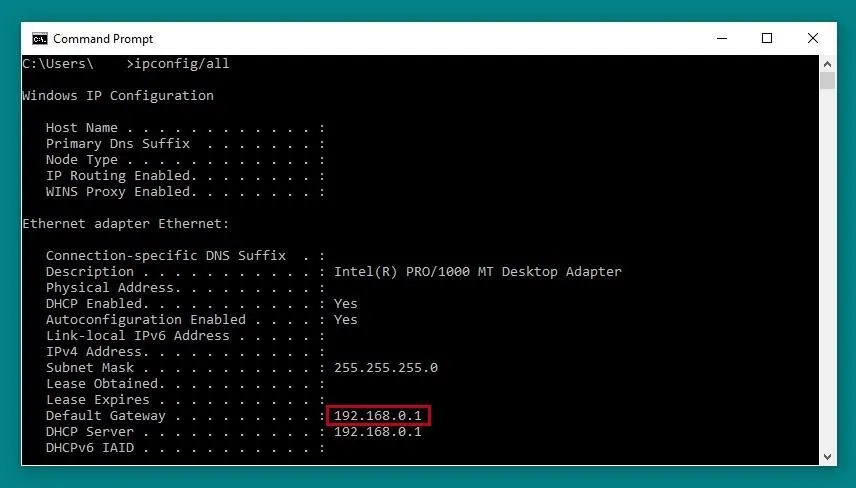
The router IP is shown next to "Default Gateway."
On macOS and Linux, we can do the same using netstat. Open a terminal window and run the following command.
netstat -rn
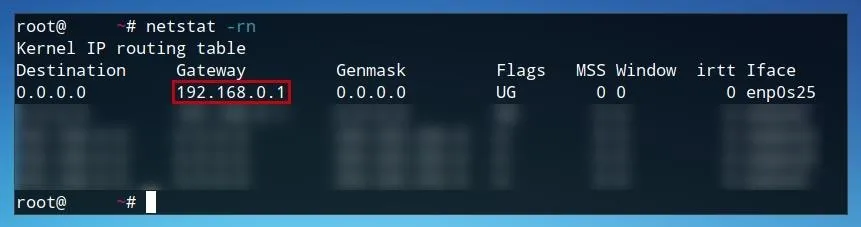
Once we've identified where are router is, we can open it in the web browser of our choice as if it was any other URL.
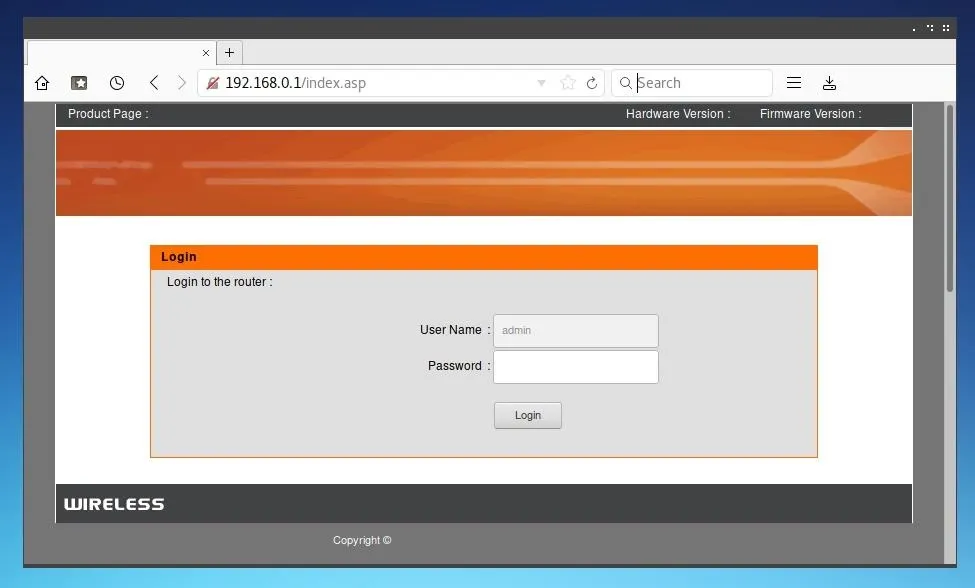
Here, we can see our router manufacturer, hardware version, and current firmware version. We can check this against the list of manufacturers which were affected, and confirm if a patch is available for our hardware version.
Not all devices will be patched immediately, but if and when a patch is available for a specific router, it will generally be installed in a similar manner.
With the router management page open, log in to the router. This password may have been set by you, your ISP, or may remain its default credentials. These credentials can generally be found online in the router's documentation or manual and sometimes even on the side of the router. Once logged in, within "Advanced Settings" or a similar menu you may find a maintenance or update page.
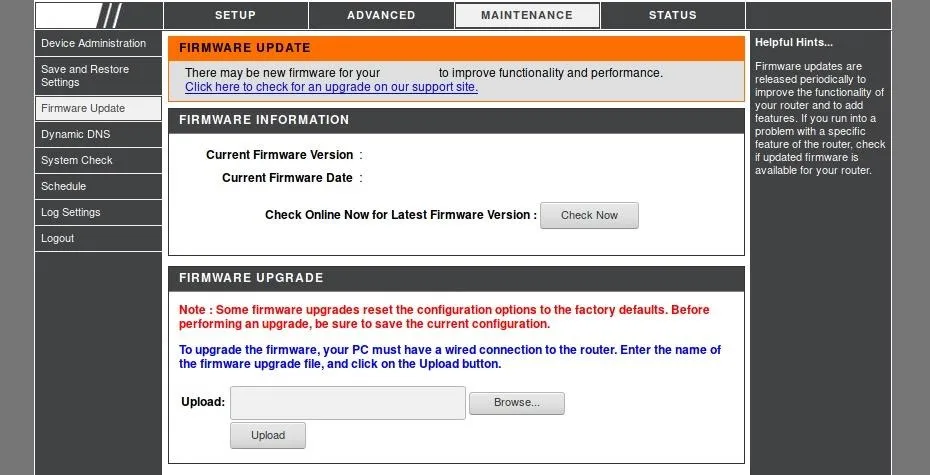
Within this page, one should be able to check for firmware updates, or potentially manually upload a firmware version to update to. The process will differ depending on the router, for some patches it may be necessary to manually install updates, while for others it may just be the click of a button.
While not all routers will immediately be able to be patched, this should be all that is needed to update router firmware as soon as patches become available.
Update Your Security Cameras, Light Bulbs, Doorbells & Streaming Boxes
Thanks to the explosion of the Internet of Things (IoT), you need to briefly consider what items, no matter how absurd, may contain a Wi-Fi card that needs to be updated. Unfortunately, you will need to identify the devices that need to be updated on your network and refer to the manufacturer for the specific fixes. What kinds of things may need to be updated, you may ask?
- Smart cameras, Wi-Fi connected baby monitors, and other remote viewing devices.
- Amazon Echo and Echo Dot, Google Home, Wink Connected Home Hubs, and other types of home automation hubs.
- Smart light bulbs, Wi-Fi connected power strips, and devices like the Nest Thermostat that connect home objects by sticking a Wi-Fi card inside.
- Apple TV and Roku streaming box type devices.
- Wireless Printers, scanners, and other office devices which connect over the network.
There are a lot more, all the way down to securing any internet-connected "adult toys" that use an app to communicate or control over Wi-Fi which you may find lying around.
All of these devices will need to be updated for the Wi-Fi connection to them to be secure. If you don't have time to, don't know how, or are paranoid, you should stop using them over Wi-Fi and switch to Ethernet (if possible) until a fix is available for that particular device.
For this, we can again use the Fing network scanner to see every device on our network. For our full guide, you can check it out here. Once you've connected to the network you want to scan and opened the Fing app, you can press the refresh button on the top right (sometimes called a "whirly-whoo") to scan or re-scan the network for devices.
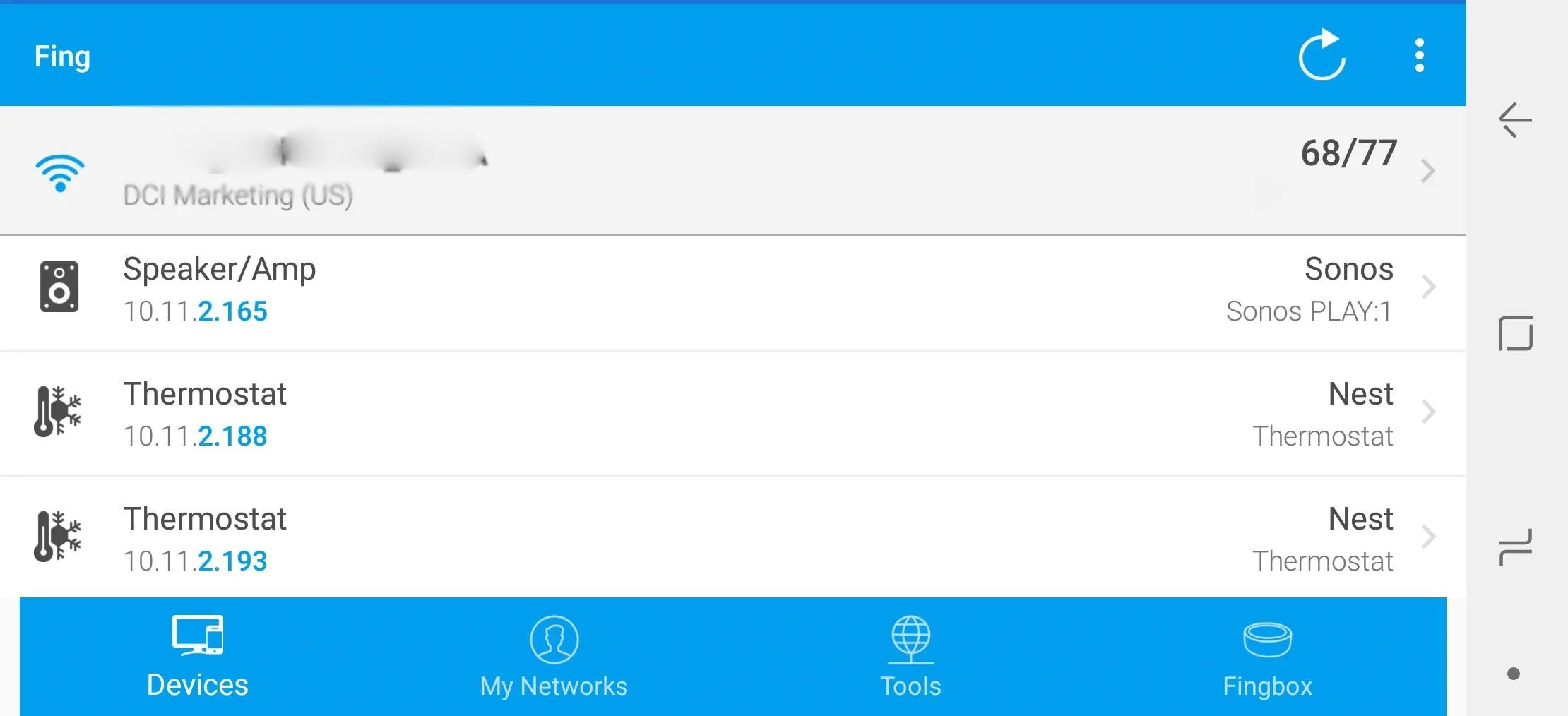
Using the Fing network scanner app to locate smart devices on the network.
You should see a list of connected devices. By tapping on them, you can show more details about the device manufacturer to help you figure out what it is, and you can even "Scan services" to find a port 80 connection you can attempt to access from your browser to update the device. This will usually be where the administrative control panel will be.
What to Remember
The KRACK vulnerability needs to be addressed on both sides of a Wi-Fi connection since it exploits a flaw in the way Wi-Fi is implemented. While many companies have released patches, the challenge is for you, the user, to make sure those patches are applied. Otherwise, the security and privacy of your devices will remain broken and vulnerable for as long as they're broadcasting on Wi-Fi.
We've gone over several ways of updating laptop and desktop computers, routers, and many IoT devices. The only way to successfully update these devices is to first make an accounting of how many you have in your home or work, and make sure to look up from the manufacturer how to secure each of them. If you're unsure what devices may be connected, use the information above to scan your network to find and identify any devices that are attached to your Wi-Fi network.
Thank you for reading! You can leave any questions in the comments below or on Twitter @tahkion.
- Follow Null Byte on Twitter and Google+
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Google+
Cover image and screenshots by TAKHION/Null Byte

























Comments
Be the first, drop a comment!