While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.
A former NSA hacker named Patrick Wardle creates these free tools for MacOS designed to detect and stop malicious programs — even if this kind of malware has never been seen before. The two we'll cover today, OverSight and RansomWhere, both look for the behavior of harmful programs instead of scanning for known malicious code. So, these programs will alert you as soon as someone starts accessing your camera, microphone, or begins encrypting files.
Threats to MacOS
For the average MacOS user, some security threats are more severe than others. Ransomware is a particularly nasty type of malware, which tries to get the victim to pay the attacker by encrypting all the files on an infected computer. To get their data back, the victim has to pay the attacker for a key. Not only can the ransom be costly, but there is no guarantee the attacker will give you the key after you pay it.
Another dangerous type of malware gives an attacker access to the victim's webcam and microphone, allowing them to eavesdrop on the victim from afar. While MacOS computers have an LED that turns on by default when the camera is on, there is no such indicator for the microphone. Because of this, it's common for MacOS malware to attempt to listen in on the microphone to avoid detection.
RansomWhere for MacOS
RansomWhere is a free tool that looks for behavior that could be destructive to your computer, such as rapid encryption of multiple files. Upon detection, the RansomWhere program halts the process that's encrypting and displays an alert to let you decide whether or not to let it proceed. In a scenario where a malicious program was trying to encrypt your hard drive, you'd be warned early in the process and asked if you'd like to kill the program.
While sometimes legitimate updates of apps like Adobe products may trigger this, smart math in the background is able to keep false negatives low by being able to discern between file encryption and compression. Once RansomWhere detects a program encrypting more than three files rapidly, your decision as to whether or not to let it continue is saved to a whitelist, further reducing false positives.
Keep Track of Eavesdropping with OverSight
For MacOS users wanting to monitor whether any programs are accessing their webcam or microphone, OverSight allows you to supervise these devices and alert you to any violations of your privacy. By giving visibility to the microphone as much as the camera, it's easy to spot a program accessing the microphone that shouldn't be and block it. The rule of thumb goes that if you discover random programs suddenly asking to access your microphone and camera, you've probably got a problem on your computer worth checking out further.
More than live monitoring, OverSight also creates logs of which programs accessed these devices and when along with whether you decided to allow or block them from using it. The log lets you go back to look for suspicious activity if you're worried about someone with physical access to your computer installing a program to access your microphone.
Let's get these programs installed and working on our new Mac.
What You'll Need
To install these free Objective-see tools, you'll just need a MacOS computer, a browser, and an internet connection. You can find all of them on the product section of the 0bjective-see website.
Download RansomWhere
First, head to the main webpage for RansomWhere on Objective-See.com. From there, we can read a lot more about the way it works. If you'd like to learn more about the development process and everything RansomWhere was designed to do, you can read the blog post that Patrick wrote about creating it.
Click "Download" just under the key logo to start downloading the program. Once downloaded, you can double-click the download to unzip the installer and then click to open it.
Install & Configure RansomWhere
Installation of RansomWhere is very simple. When the installer program opens, you'll need to type in your password to give the installer permission to install the program. Next, click "Install" to run the installer process.
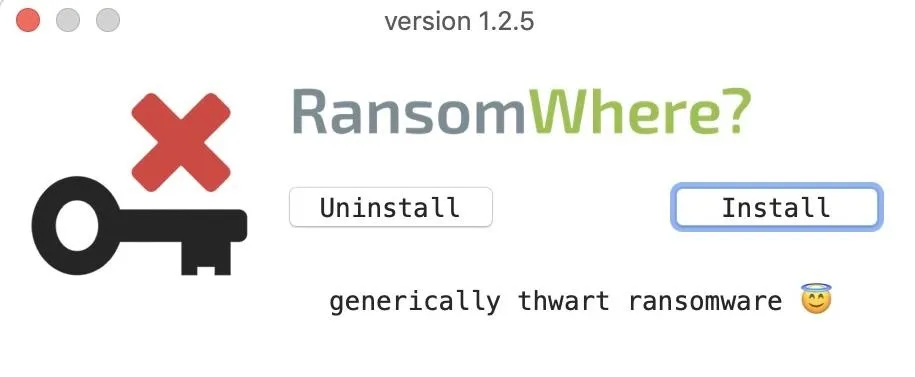
Once we see the dialog that RansomWhere has successfully installed, we're done! Unless we want to test the program, we can move on to installing OverSight.
(OPTIONAL) Test with Python3 Ransomware Simulator
If you want to test out RansomWhere, you can run a program that acts like ransomware to see it's working. In my example, I create a Python program to encrypt any PNG file left in the same folder.
To try this out, open a terminal window and type the following commands to create a folder called "GenEncrypt" in your home folder.
cd
mkdir GenEncrypt
cd GenEncrypt/
nano RealBadFile.pyNow, copy and paste the Python code below into the window, and hit ctrl + x and then "Y" when you're done to finish writing to the file.
import pyAesCrypt
import os
counter = 0
def encryptDat(victimFile, counter):
# encryption/decryption buffer size - 64K
bufferSize = 64 * 1024
password = "tunnelsnakesrule"
# encrypt
pyAesCrypt.encryptFile(victimFile, victimFile + (str(counter+1)) + ".aes", password, bufferSize)
counter += 1
counter = 0
current = os.getcwd()
for file in os.listdir(current):
if file.endswith(".png"):
victimFile = os.path.join(current, file)
encryptDat(victimFile, counter)
print("Done!")When you type ls, you should see the Python file "RealBadFile.py."
This Python3 code will encrypt every PNG file in the same folder with AES encryption! To test this, throw in at least 3 .PNG files (try taking a screenshot to create some). Now, in a terminal window, type the following to run the program.
pip install pyAesCrypt
python3 RealBadFile.pyProvided the script encrypted at least 3 files, you should see a warning like below. On MacOS Catalina, you may need to enable notifications for RansomWhere to get these popups.
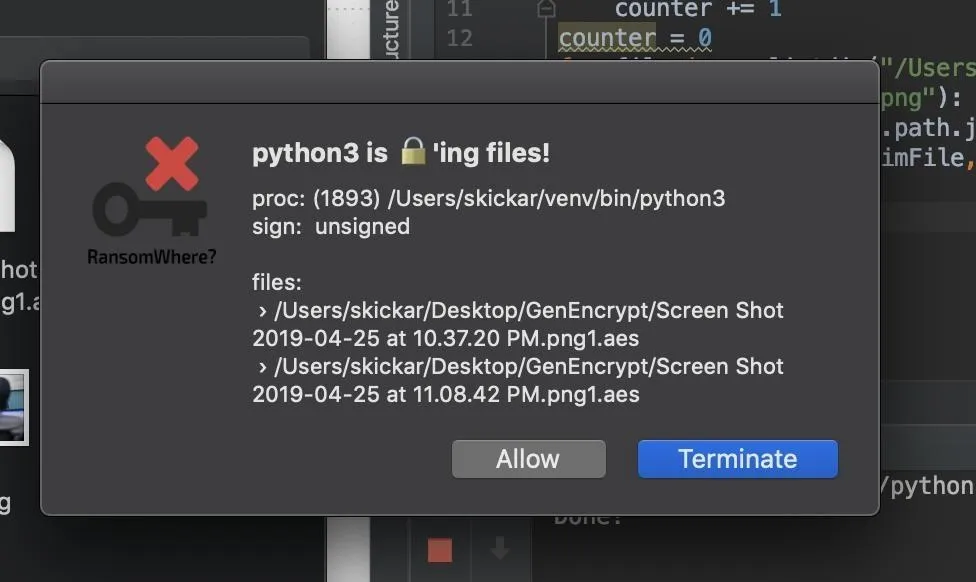
You can click "Terminate" to stop the process from encrypting more files. Pretty cool!
Download OverSight
To download OverSight, head to the OverSight page on Objective-See.com to read more about it and locate the download link.
Click on "Download" under the icon on the top left to download the installer, and then double click the file when it's finished downloading to unzip and then double click to launch the installer. Enter your password for the program to have permission to install, and then click "Install" to set up OverSight.

Once OverSight is installed, open up a program that needs access to the camera, like Photo Booth. You should see an alert, which allows you to decide whether to allow access to the camera or not. On MacOS Catalina, you'll need to enable notifications for OverSightHelper to get these alerts.
Set Preferences & Block Unwanted Requests
To configure OverSight, click on the umbrella icon in the task bar, and then click on preferences. You'll also notice this will list the current status of the microphone and camera.
In the preferences menu, you can set whether to run OverSight at login, whether to log activity and several other options.
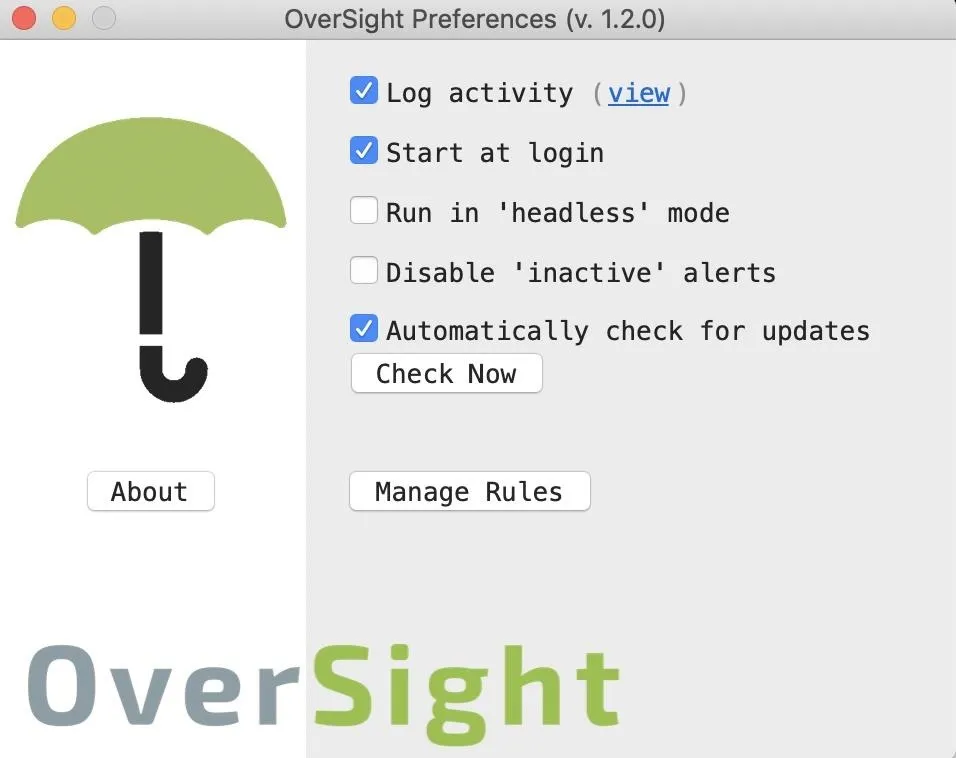
If you click "Manage Rules," you'll be taken to the application whitelist. This list shows every application allowed to use these devices without permission, and you can revoke permission from any of them by clicking on the "x" to the right of the application.
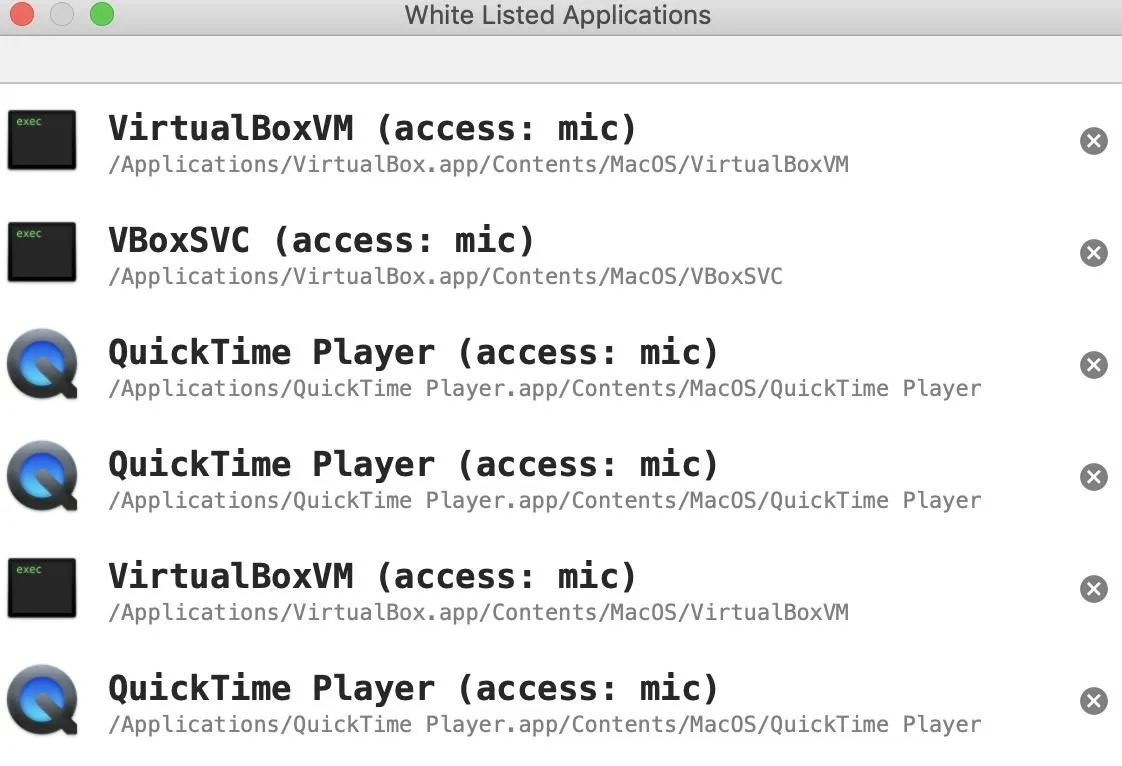
Now, we should be set up to detect when our devices are accessed by any program in real time.
Review Logs to See When Devices Have Been Activated
Aside from live monitoring notifications, you can also go back to see if any programs have been accessing your microphone or camera. By clicking on the "(view)" link after "Log Activity" in the preference menu, you can see a complete history of access to both devices.
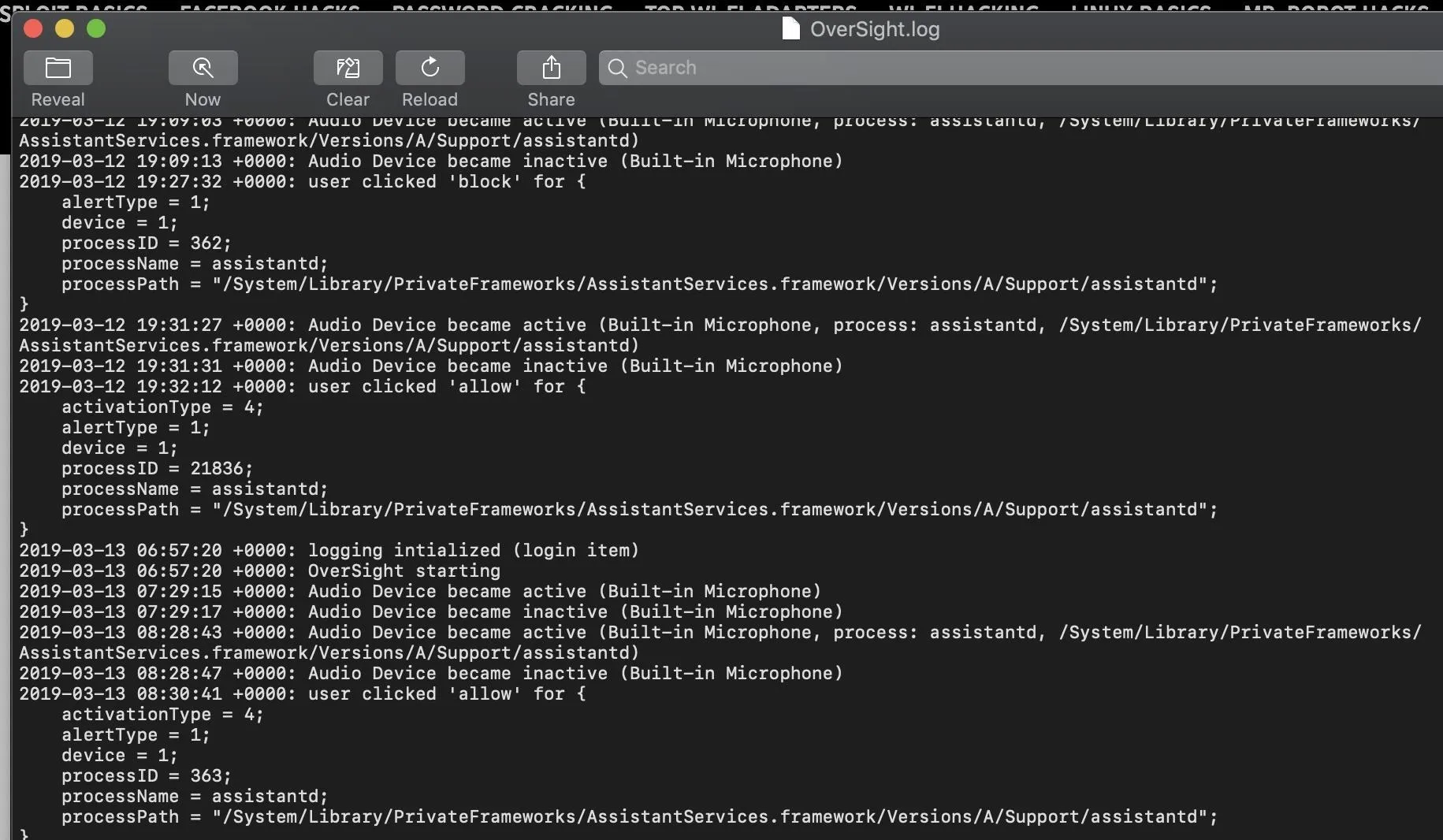
With this information, we've now got complete access to the details of what programs are connecting to our camera and microphone, and when they did so.
Locking Down Your MacOS Isn't Hard
While fighting malware might seem overwhelming for the average MacOS user, it's easy to be smart about spotting and stopping malware in its tracks if we hunt for bad behavior on our system. Thanks to OverSight and RansomWhere, we can detect bad behavior and stop it before it becomes more serious, and even reveal malware that's never been seen before by detecting what it does.
I hope you enjoyed this guide to locking down your MacOS computer with RansomWhere and OverSight by Objective-See! If you have any questions about this tutorial on securing MacOS or you have a comment, ask below or feel free to reach me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo by Benjawan Sittidech/123RF; Screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!