It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.
The purpose of your password is to authenticate any device requesting access to your online account data, in the hopes of keeping out unauthorized users. This only works if you have a strong password and never share, reuse, or accidentally enter that password into the wrong place. Stealing the password for an online account is the most obvious way of breaking in, and those in the business of breaking into accounts have turned this single point of failure into a science.
Phishing & Whaling Mean Passwords Aren't Enough
Passwords are stolen for many reasons, and those behind phishing attacks have motives that vary significantly in scope.
Criminals will often attack an organization or person for personal financial gain, using the compromised account to steal financial or blackmail data from a business. While this kind of attack is the most obvious, executives and other important people also must worry about an evolution of this attack called "whaling," where their accounts are targeted due to the user's influence in a company.
Hijacking social credit and trust is a major concern in whaling attacks, and the success of this tactic has peaked the interest of state-sponsored attackers. Stealing the password of an account owned by an important person in a company has many advantages for criminals.
The attacker compromising the account of an executive can request changes internally to make the organization as a whole easier to attack, request payments be made, or target another business the executive works with by sending fake invoices or other documents full of malware.
APTs Are Changing Phishing to a Weapon of War
In 2016, the power of Russian cyberwarfare was unleashed against members of the Democratic National Party. Russian intelligence-linked advanced persistent threat (APT) groups began aggressively spearphishing the accounts of important members of the Clinton election committee. APTs are called persistent because they have the state-backed resources to probe high-priority targets endlessly for vulnerabilities, making their eventual success nearly guaranteed. It only took a single mistake for the DNC to be infiltrated by this group.
APT hacking groups overwhelm targeted organizations by bringing more technical and resource firepower. The goal of the DNC attack was not financial gain, but an intelligence operation to gain political leverage from the data stolen from these accounts. This information was scoured for anything embarrassing or damaging to the organization, doctored, and then released for maximum political effect. Attacks like this are a calculated attempt to destroy the organization they target and can be turned against the press and human rights activists by anyone with the resources and motivations to mount such an attack.
Motivated and resourced APT groups have the ability to phish two-factor authentication codes delivered by push or SMS notifications, leading to the dilemma of how to securely and conveniently access important accounts. While government contractors have needed to worry about this threat for quite some time, the general population are now needing to learn more about the tactics the government and private sector has adopted to defend against this threat.
Advanced Protection from Phishing for Google Accounts
With many organizations using Google products like Drive and Gmail for work, Google credentials are a high-priority target for hackers. To combat this, Google designed a program for those at risk of phishing attacks or interested in preventing them altogether. At the Enigma 2018 conference, Google presented Advanced Protection, their solution to state-sponsored or well-resourced APT attacks targeting Google credentials. Advanced Protection has actually been around since Oct. 2017, but many still aren't away this program exists.
Advanced Protection removes the weak link in the kind of two-factor authentication most people are familiar with. SMS messages and push notifications are not a barrier for a skilled attacker attempting to compromise an account, so Google turned to the Universal 2nd Factor authentication standard adopted by physical security keys to creating a system that is more secure.

Kody/Null Byte
Multi-factor authentication uses a combination of challenges to make sure a device is allowed to access the account. A password represents one of three commonly used factors of authentication, a secret you know. The other factors can include something you are, like a fingerprint or facial scan to unlock a phone, or something you have, like a physical key. A USB security key is used to add an extra layer of security to your device, meaning an attacker will need to physically steal your key in order to get in.
This is critical because tricking you into entering this physical key won't even allow an attacker access since it changes each time and is generated in response to a challenge. Simply having your password doesn't get them anywhere, provided it's not a password you reuse with any other accounts. While this sounds great, there are some tradeoffs for the security Google's Advanced Protection gives users unwilling to trust their account data's security to a single password.
The Inconvenience of Security — U2F for Beginners
The most serious tradeoff is the inability to give account access permission to third-party apps, including Apple. You'll need to use Google app, and the Chrome browser, to access your data or any signed-in services. Make sure you can live with that before turning this feature on. Other types of 2FA can't be used, so you'll need to make sure you have a U2F token any time you need to add a new device (or connect from a VPN).
When using U2F physical security tokens, which cost somewhere between $15 and $30, it's good to think of them as keys. If you only have one and you lose it, you'll need to go through the hassle of proving your identity to get back in, and it won't be like just requesting a password reset. You must have at least two in order to enable Advanced Protection, and this is to protect you from you.
For Android devices and any other device with a USB port, you can use a Fetian or Yubikey USB security key. These keys are sturdy, and the Yubikey supports other helpful features like secure one-time password generation just by tapping on the gold disk. Additionally, you can quickly use them with Android over NFC, allowing you to authenticate any desktop, laptop, or Android device with NFC.
iPhone users will need to rely on a Bluetooth-type U2F token, which looks something like a mix between a garage door clicker and a Tamagotchi. After downloading the Google Smart Lock app, iOS users can authenticate their device with the Bluetooth token to access their Google Advanced Protected account data.
Setting Up Advanced Protection
It's important to note that Google Advanced protection is rolling out for Gmail accounts, but if you try to enroll an organization account (one with a custom domain rather than an @gmail.com domain), you'll see the following message.
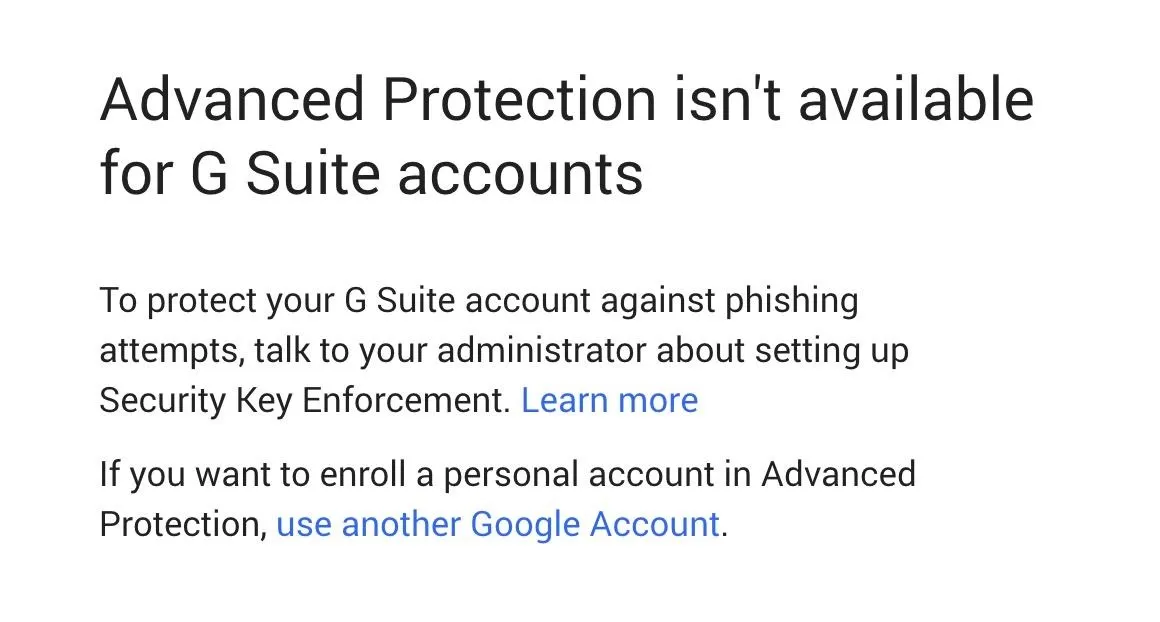
If you're a Google domain administrator, or you want to talk to yours about adding U2F security keys to protect your organization, you can learn more about enforcing similar protections on Google's information page.
If you have an individual account and you want to protect it against phishing with Advanced Protection, then make sure you can live with the tradeoffs, and let's get started!
Purchase 2 Universal Two-Factor Security Keys
Navigating to Google's Advanced Protection setup page, you'll be greeted with the following message prompting you to purchase at least two U2F keys.
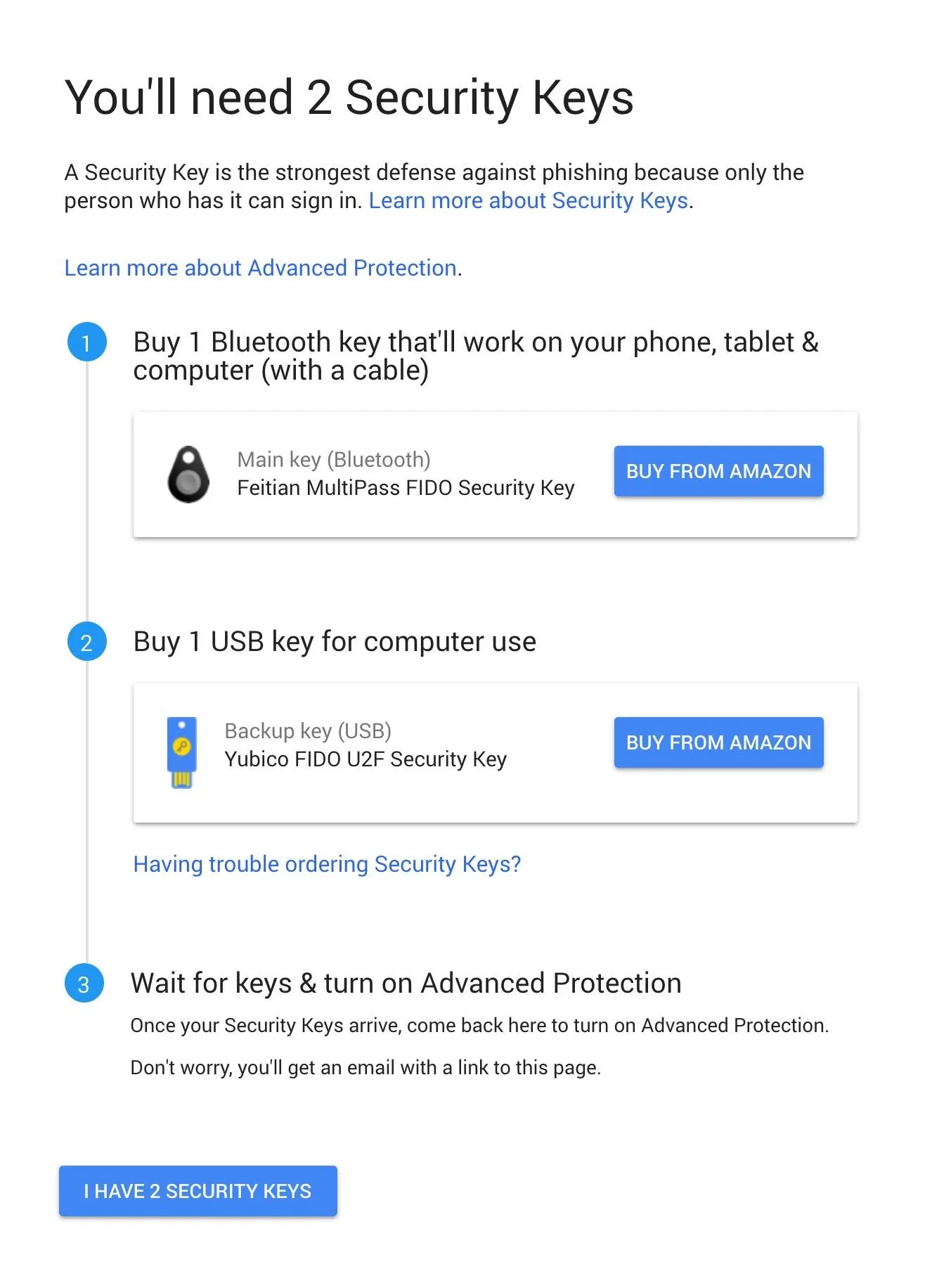
You probably have more than one key to your house, so make sure you have more than one key to access your important data. I recommend the Yubikey NEO from personal experience and from reading reviews about it surviving incidents that destroyed regular keys. It features a USB and NFC interface. Google recommends the Yubico FIDO security key.
If you only use Android, you can purchase a pair of these, or the cheaper $16 Fetian security key. These aren't as compatible with other services as the Yubikey, but purchasing one as a cheap backup is a good idea.

Kody/Null Byte
If you have an iOS device you'll need to authenticate, or you want to be able to do so via Bluetooth, you'll need a Bluetooth security token like the Feitian MultiPass FIDO security key (which Google also recommends). In addition to syncing these via Bluetooth, they can be plugged directly into any device with a USB port via a small micro-USB port on the bottom to charge or authenticate a device with the click of a button.
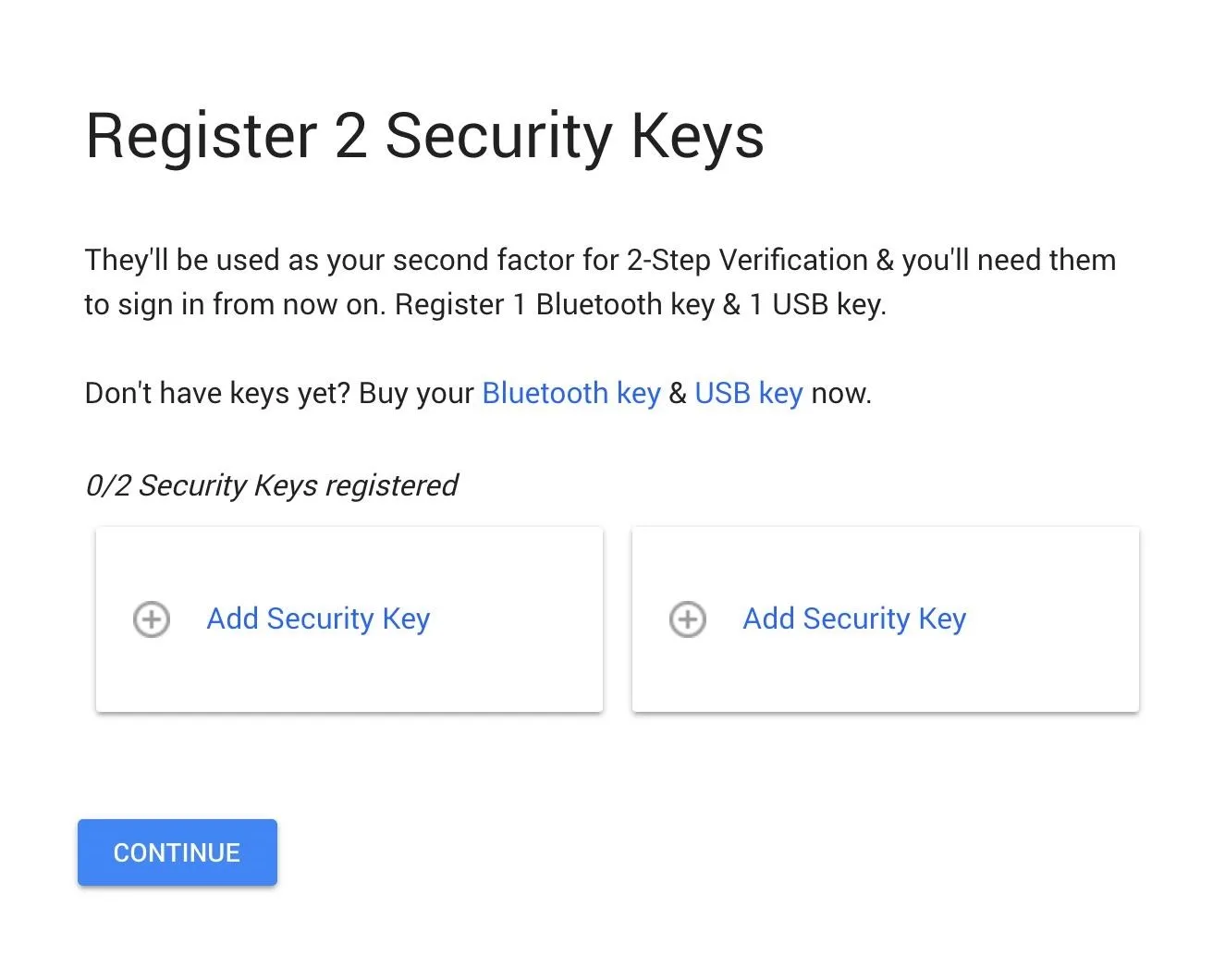
Register Your Security Keys
After selecting "I Have 2 Security Keys" from the Advanced Protection setup page, you'll need to sign in again to verify your identity (or if you're not currently logged into Google), then you'll be greeted with the registration screen.
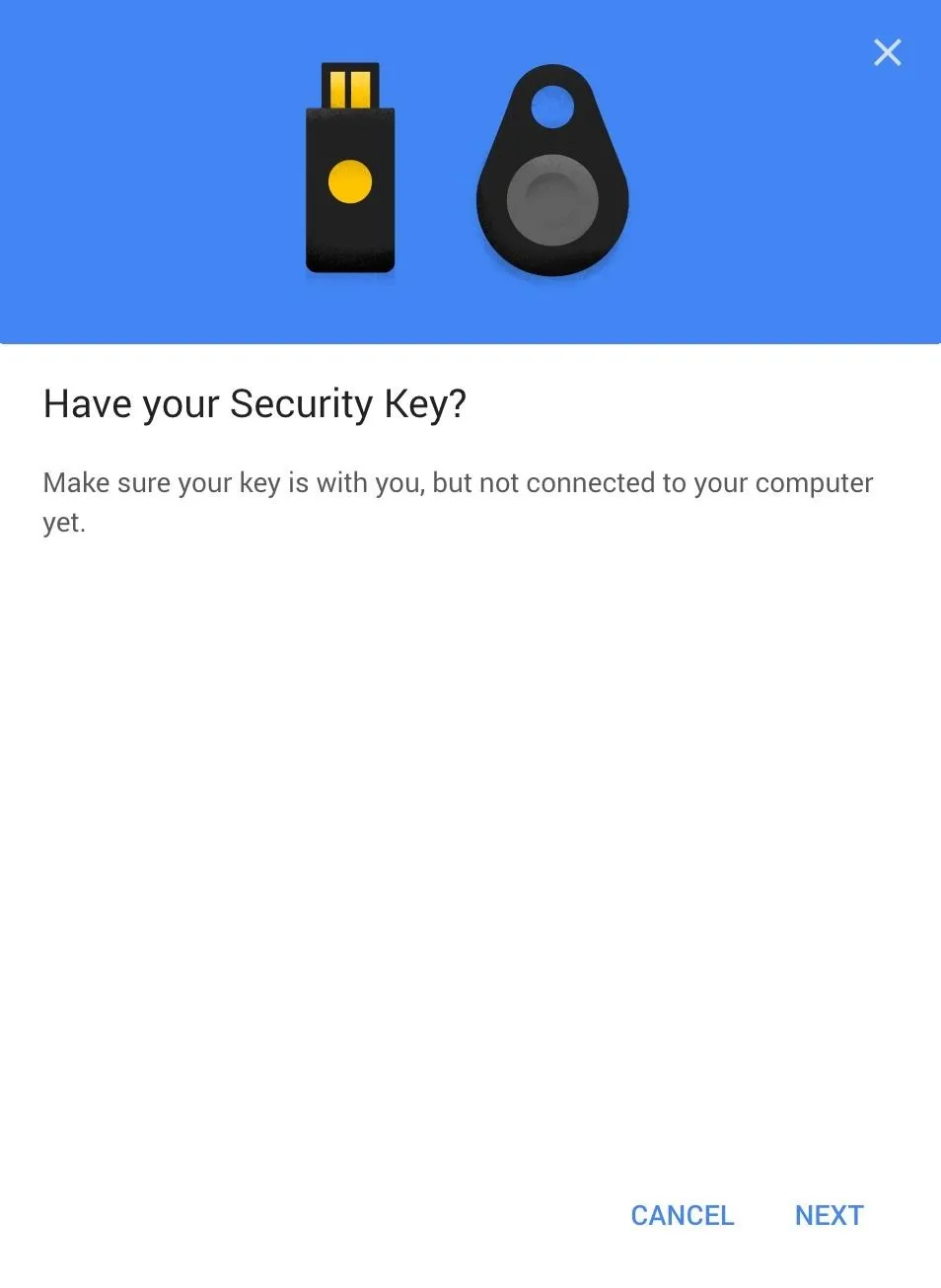
To register one of your keys, click the "Add Security Key" button. Click through the first prompt about making sure you have your key but that it's not connected to your computer yet, then when you see the next prompt, connect your security key by plugging it into the USB drive of your computer.
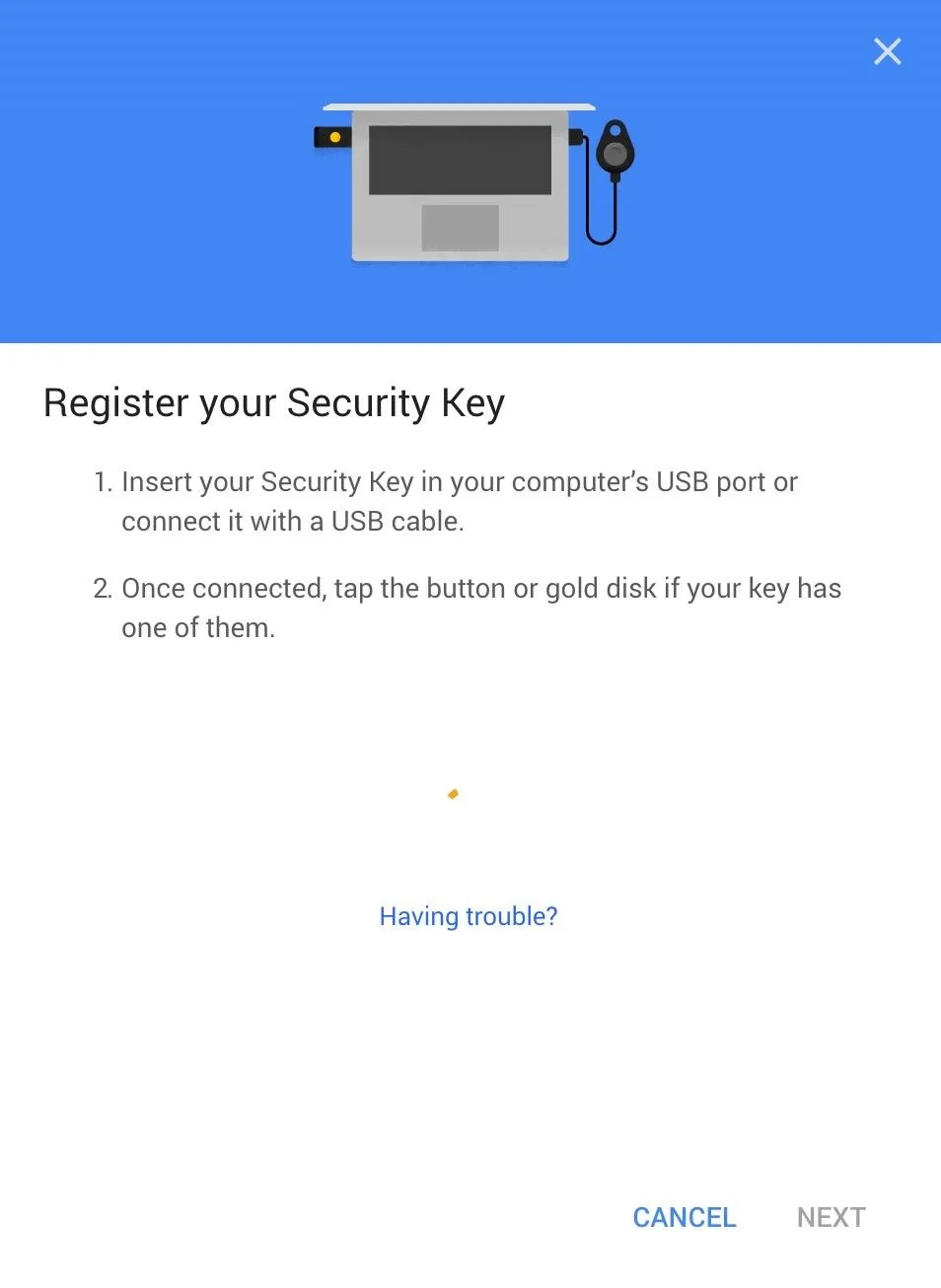


Tap the gold disk on your USB key or, if you're connecting a Bluetooth U2F device via USB cable, tap the button on the dongle to register the key. You should see the result in the picture below, inviting you to name your key so you can remember it. Do so and click on "Done."
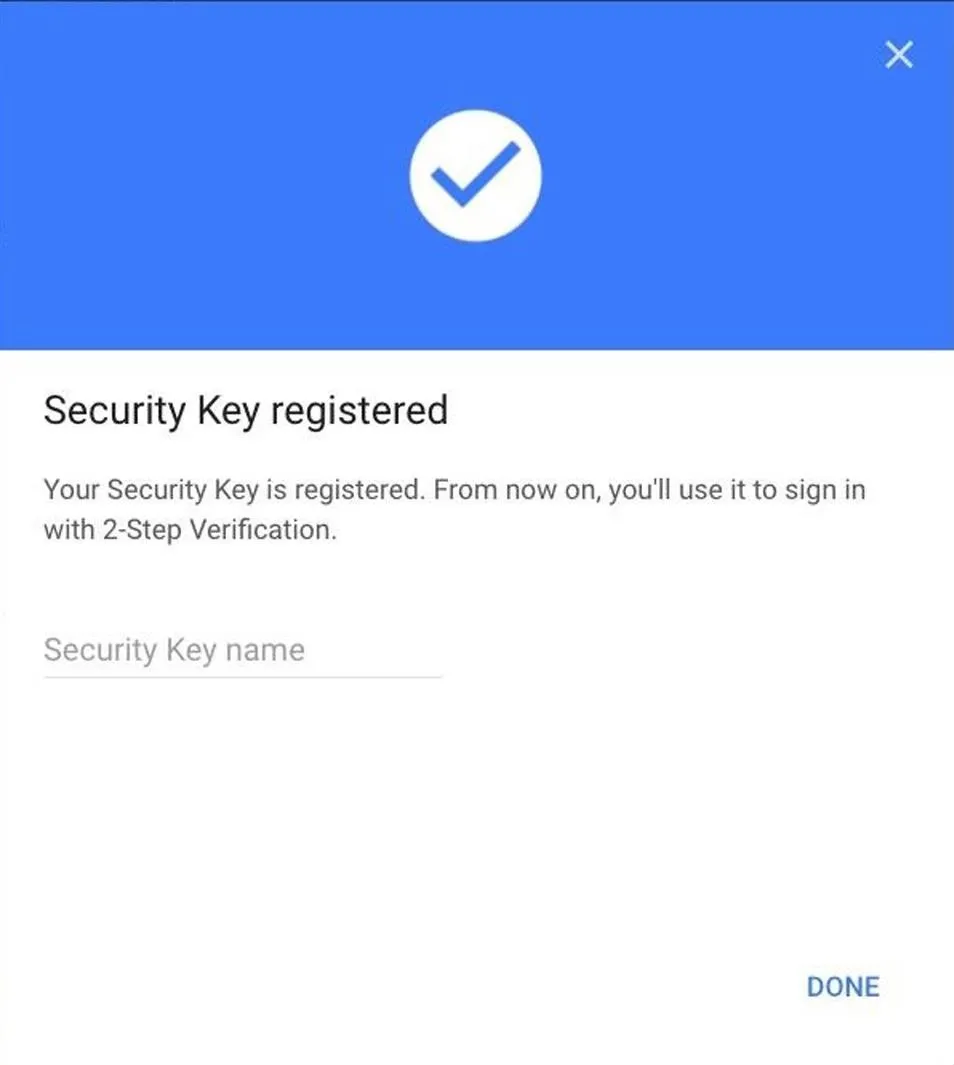
The setup menu should now show your registered key. Repeat this process by clicking the second "Add Security Key" link to complete the key registration process with your second key.
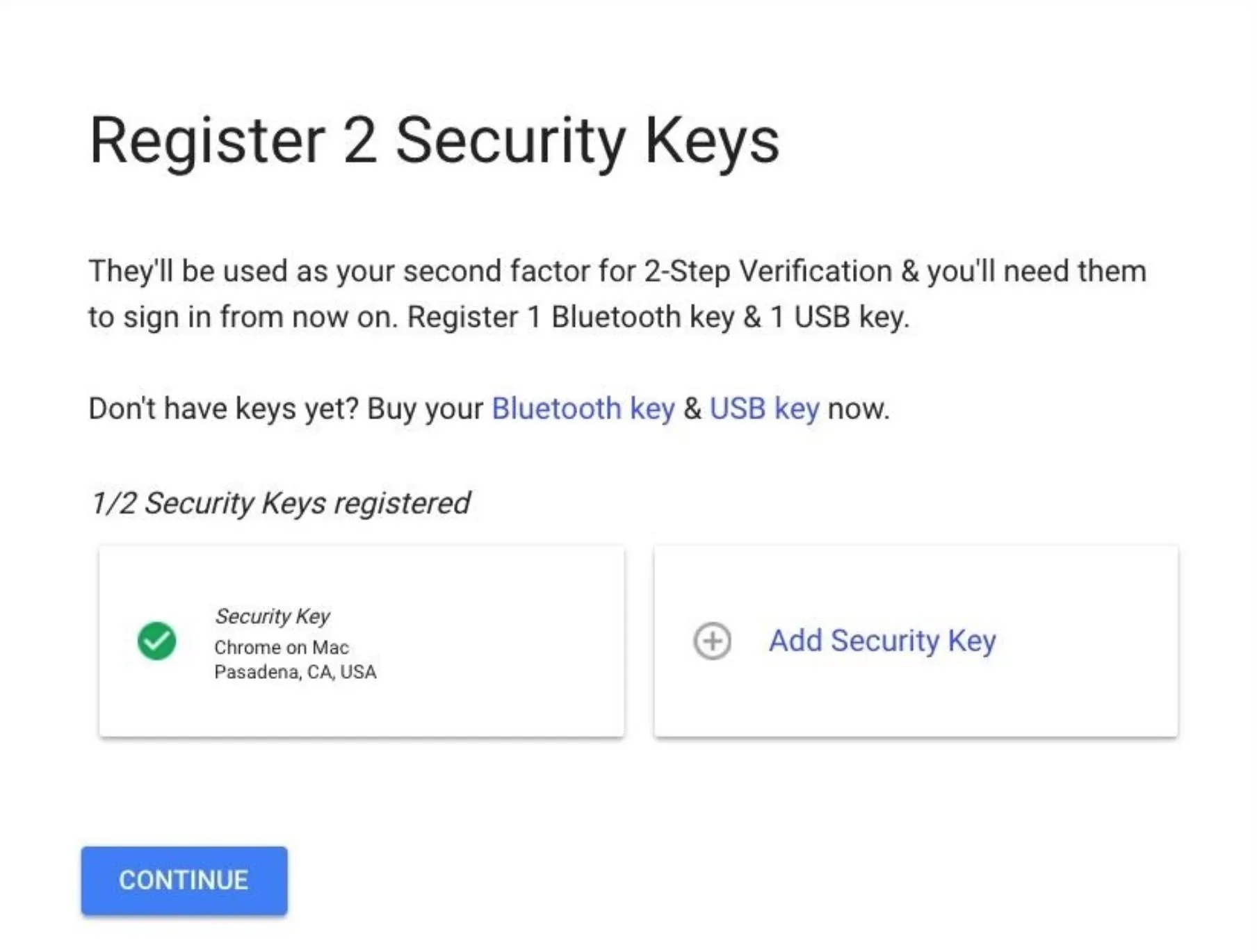
Once both of the checkboxes are green, you're ready to confirm and activate Advanced Protection in the final step, so hit "Continue" and keep going.
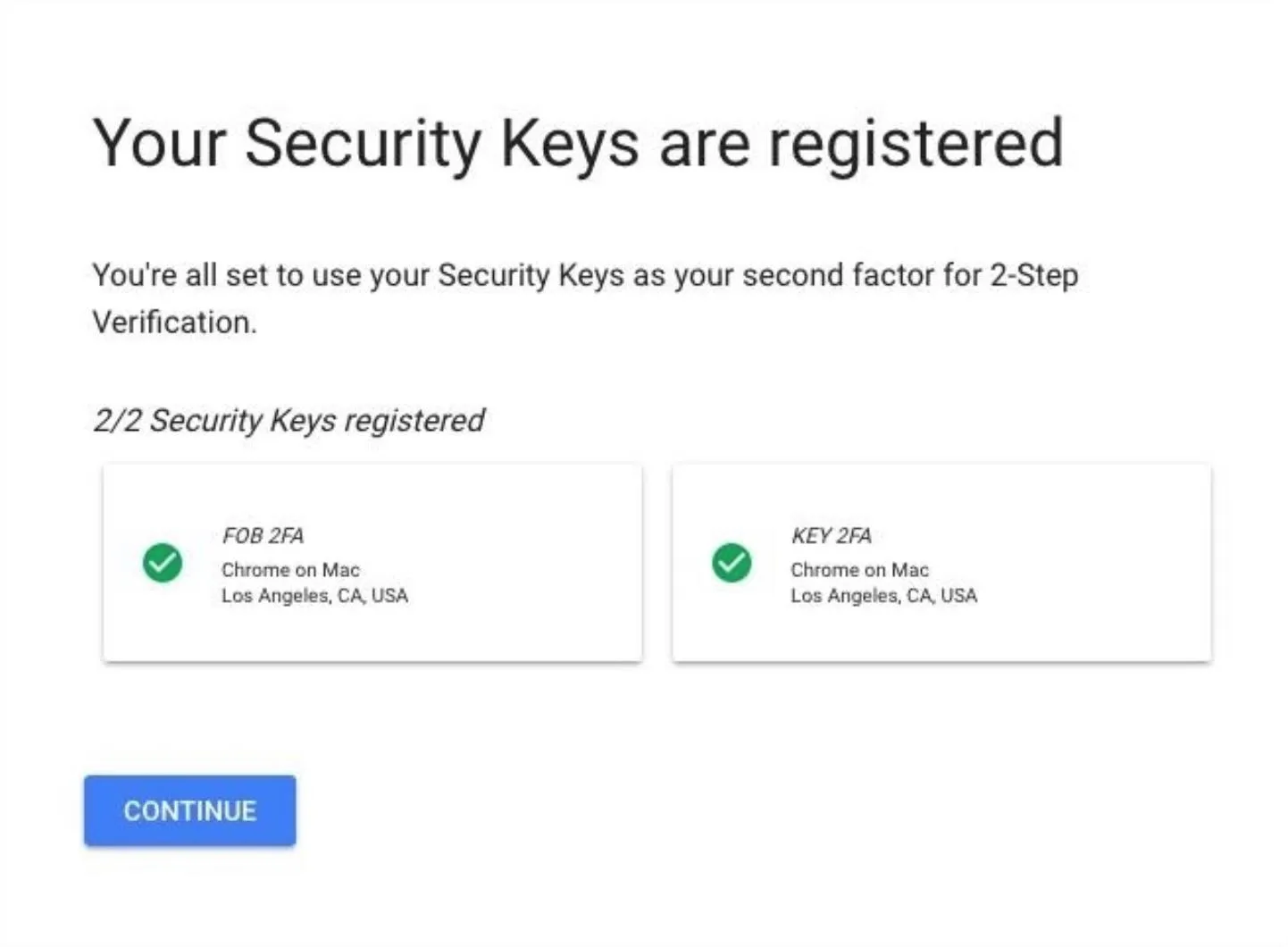
Activate Advanced Protection
Clicking on "Continue" leads us to the final warning screen before enabling Advanced Protection. Thoroughly read the warning before accepting, because you'll have to live with these changes.
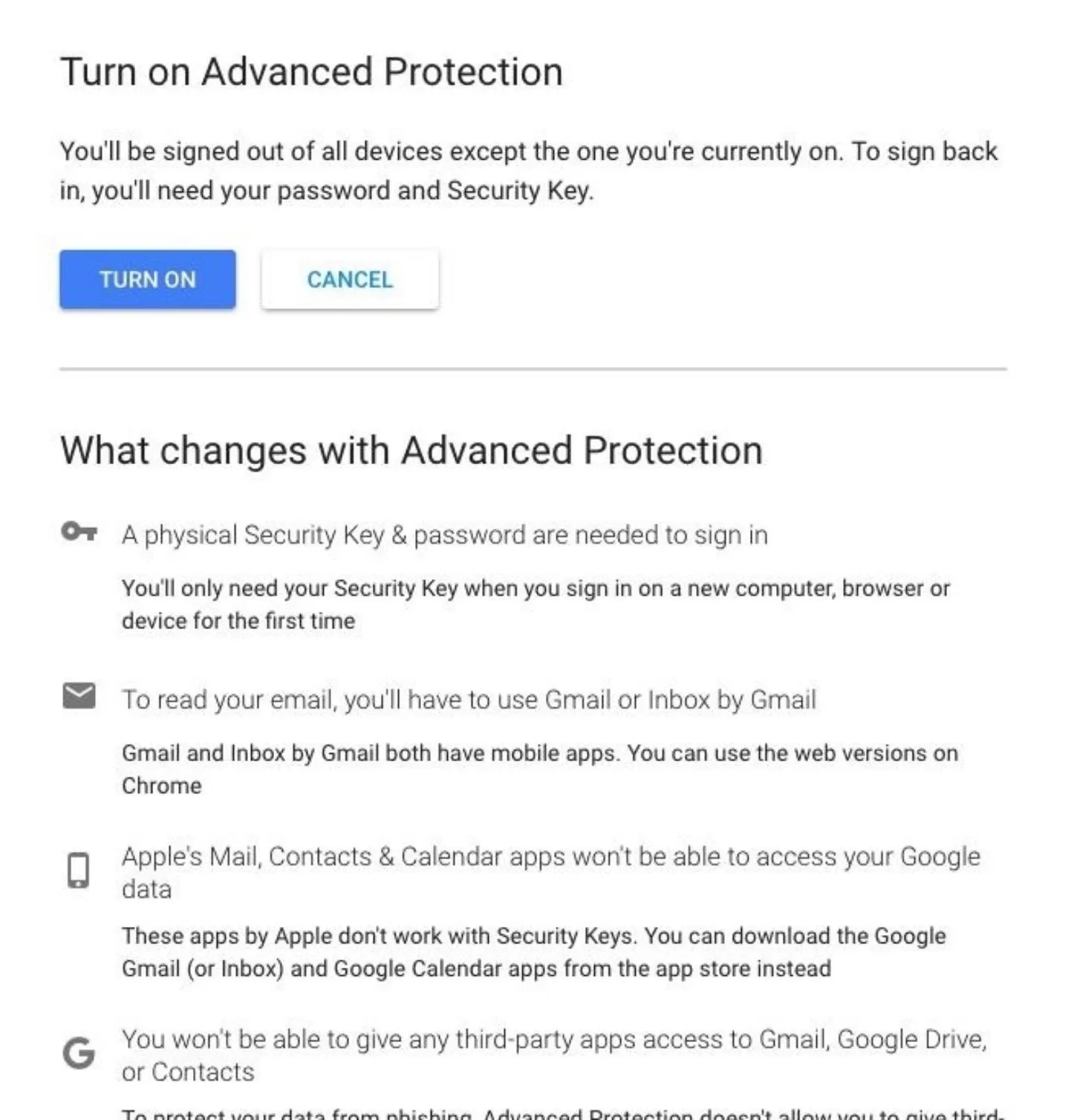
Once ready, click "Turn On" to proceed. A popup explaining that you will be signed out of all devices will appear. This means that you'll need to re-authenticate for every device that you aren't currently on.
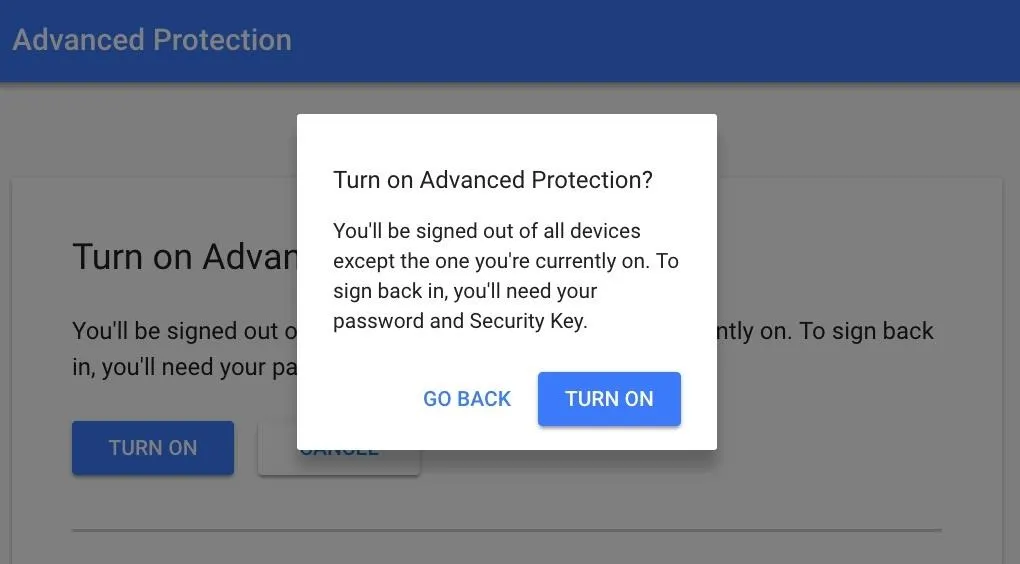
After selecting "Turn On" on this last popup, you should see a confirmation screen like the one below.
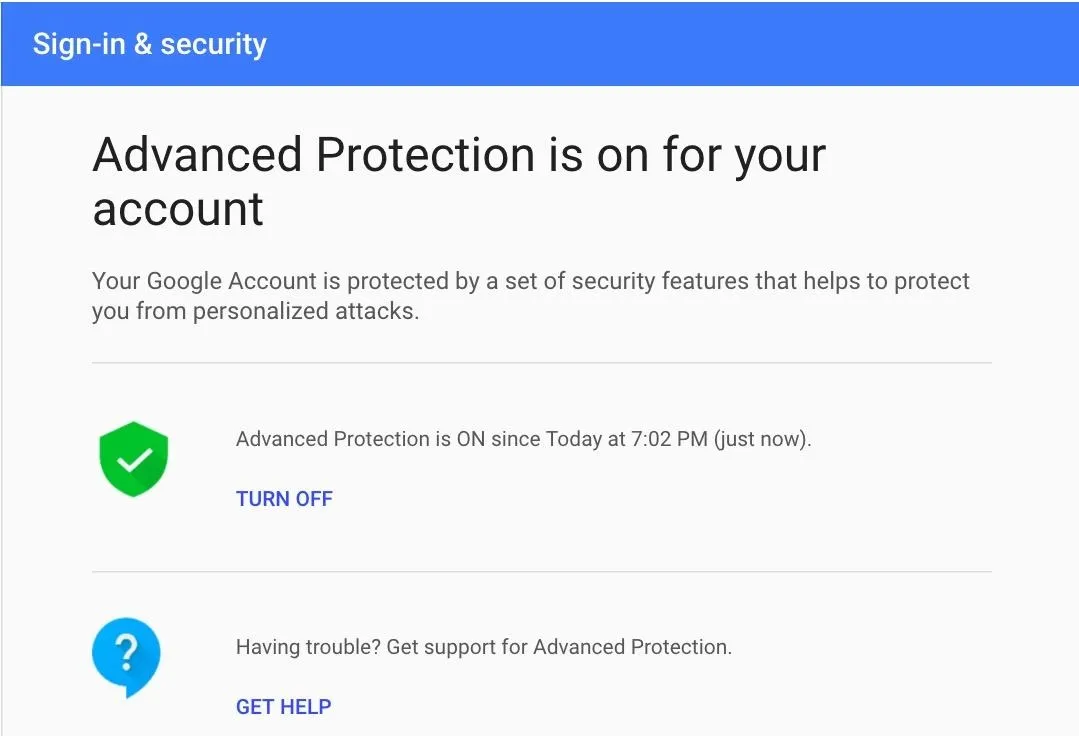
Some Limitations on Locking Things Down
Even though Google Advanced protection is designed to give you the most power to protect your account, it still had some quirks. One issue I found was that I was unable to revoke a Samsung Galaxy S6 device I was no longer using from being listed as having access to my account. Normally, when you select an option from your recently used device list, there will be an option to "Remove" said device. In this case, however, there was simply no option to do so.
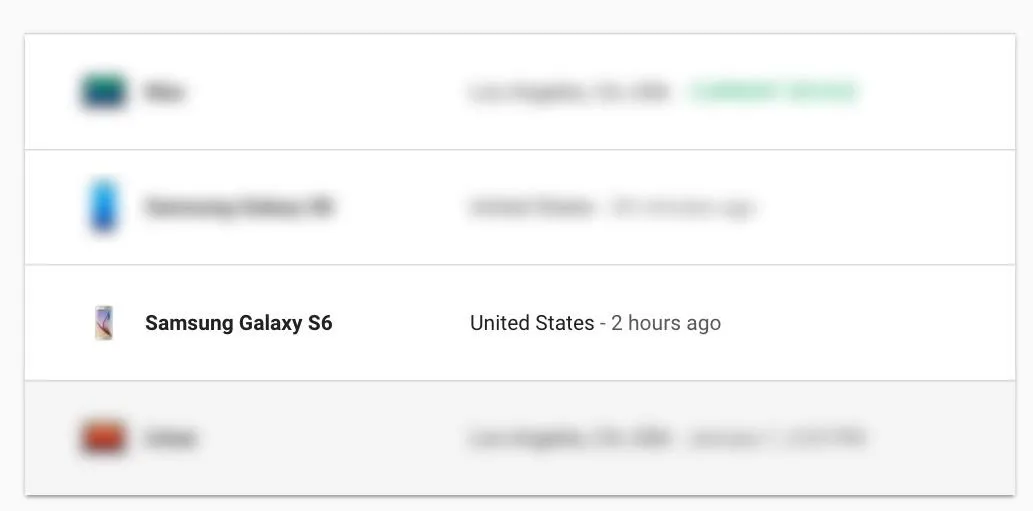
This raised the issue of being unable to revoke access to a suspicious device if someone were able to briefly use your key to add their own. I reached out to the project manager for Google Advanced protection to ask about revoking access to devices, and he mentioned that any device that has accessed your account will stay on this list for 28 days, to prevent an account hijacker from covering their tracks.
To revoke access from any device that doesn't allow you to do so remotely, you can change the password to your Advanced Protected account. The device appearing on your account from that point on is somewhat misleading, but the act of changing your password should lock out all devices and force them to re-authenticate with a U2F token.
Use 2FA Wherever You Can for a Brighter Future
If you're using a password without a second factor of authentication to secure your accounts, you need to be aware that you are one targeted phishing email away from giving a stranger access to all of your online data. This may not have been the case back when you made your account, but it certainly is now, and it's time to get out ahead of that reality rather than letting it run you over. Companies big and small are regularly breached by phishing tactics, and good security hygiene is an essential part of bridging the tech divide to avoid being an easy target.
Everyone, from the important CEOs to the average privacy concerned citizen should be aware of how two-factor authentication works and opt to implement it anywhere you are serious about account security.

Kody/Null Byte
The average user still doesn't know why U2F is important or how to use it, even though many websites now support using U2F security keys. Those in positions of power can't afford to miss this shift in trend — U2F is the new standard for personal account security, and Advanced Protection is a good way to get started being more secure.
I hope you enjoyed this guide to securing your Google account from phishing attacks using Advanced Protection and U2F security keys! If you have any questions about this tutorial or U2F usage, feel free to leave a comment or reach me on Twitter @KodyKinzie. We'll be doing some more guides on this program specifically for macOS and Windows, Arch Linux, Debian, and iOS and Android, so stay tuned.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte

























Comments
Be the first, drop a comment!