Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.
Mitaka, created by Manabu Niseki, works in Google Chrome and Mozilla Firefox. Once installed, it lets you select and inspect certain pieces of text and indicators of compromise (IoC), running them through a variety of different search engines, all with just a few clicks. The tool can help investigators identify malware, determine the credibility of an email address, and see if a URL is associated with anything sketchy, to name just a few things.
Installing Mitaka in Your Browser
If you've ever installed a browser extension before, you know what to do. Even if not, it couldn't be easier. Just visit Mitaka in either the Chrome Web Store or Firefox Add-Ons, hit "Add to Chrome" or "Add to Firefox," then select "Add" to verify.
- Mitaka: Chrome Extension | Firefox Add-On
Then, once you've found something of interest on a website or in an email that you're investigating, all you need to do is highlight and right-click it, then look through all of the options Mitaka provides in the contextual menu. On the GitHub page for Mitaka, there are a few examples worth trying out to see how well Mitake works.
Inspecting Email Addresses
Whenever you see an email address that you suspect is malicious, whether it's defanged (obfuscated so it can't be clicked) or clickable, you can highlight it, right-click it, then choose "Mitaka." If it's defanged, which usually means putting in [.] where regular periods go to break up the link, Mitaka will rearm it so that any search you perform will still work.
In the Mitaka menu, you'll see a variety of tools you can use to inspect and investigate the email address. There are searches you can perform on Censys, PublicWWW, DomainBigData, DomainWatch, EmailRep, IntelligenceX, OCCPR, RiskIQ, SecurityTrails, ThreatConnect, ThreatCrowd, and ViewDNS. For example, if you want to learn its email reputation, choose "Search this email on EmailRep."
From the results, we can see that test@example.com is probably not one we should trust. In fact, we can see from this report that it's been blacklisted and flagged for malicious activity.
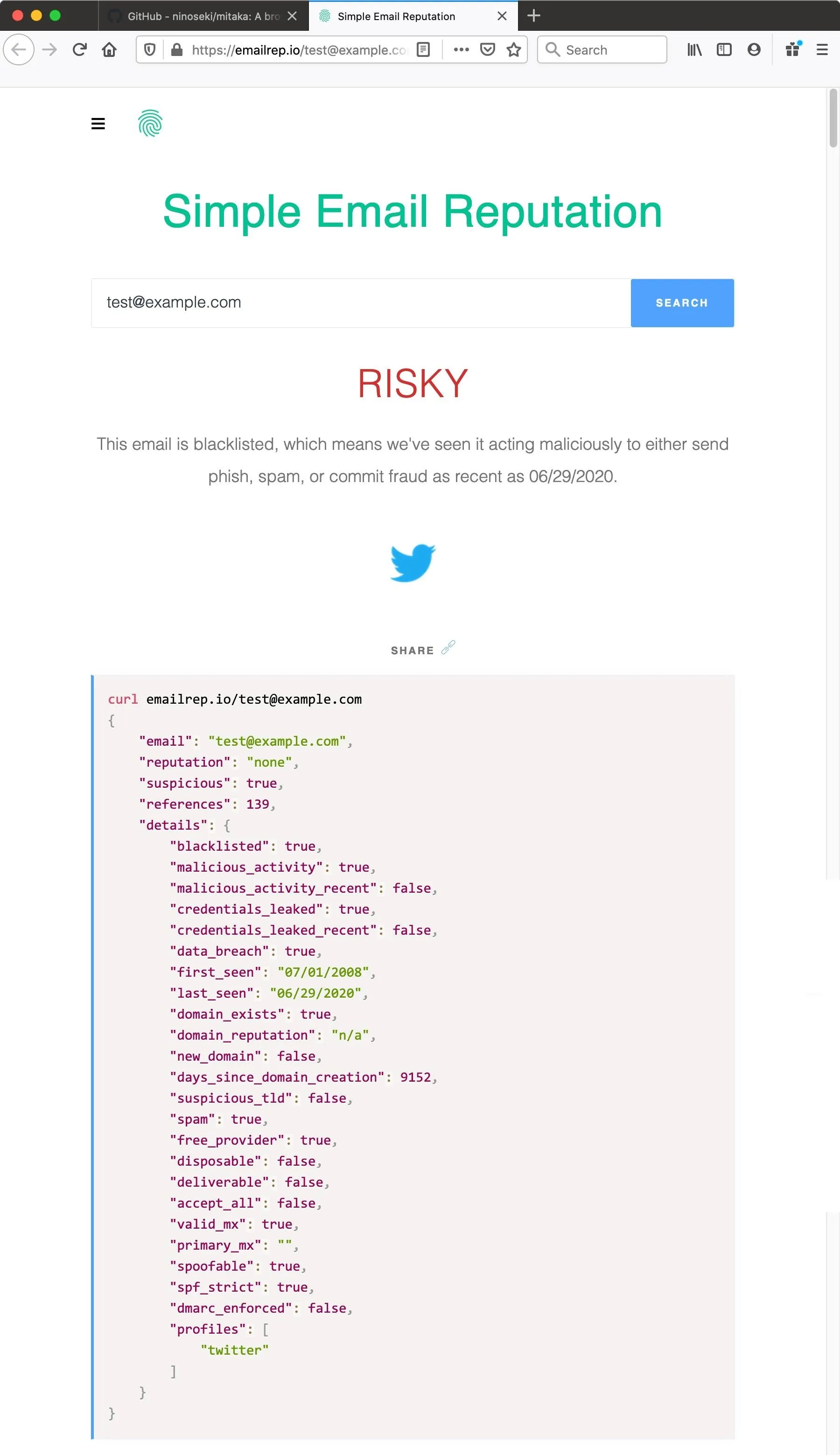
So, if we were to find or receive an email address that had been flagged this way, we would be able to very quickly determine that it was associated with somebody who was blacklisted for malware, or possibly something like phishing, and that would be an excellent way to identify a risky sender or user.
Conversely, let's say we're looking through a breach of different people's passwords, and we want to identify whether or not a real person owns an email address. We can take a properly formed email address, right-click it, select "Mitaka," then use the same EmailRep tool to check.
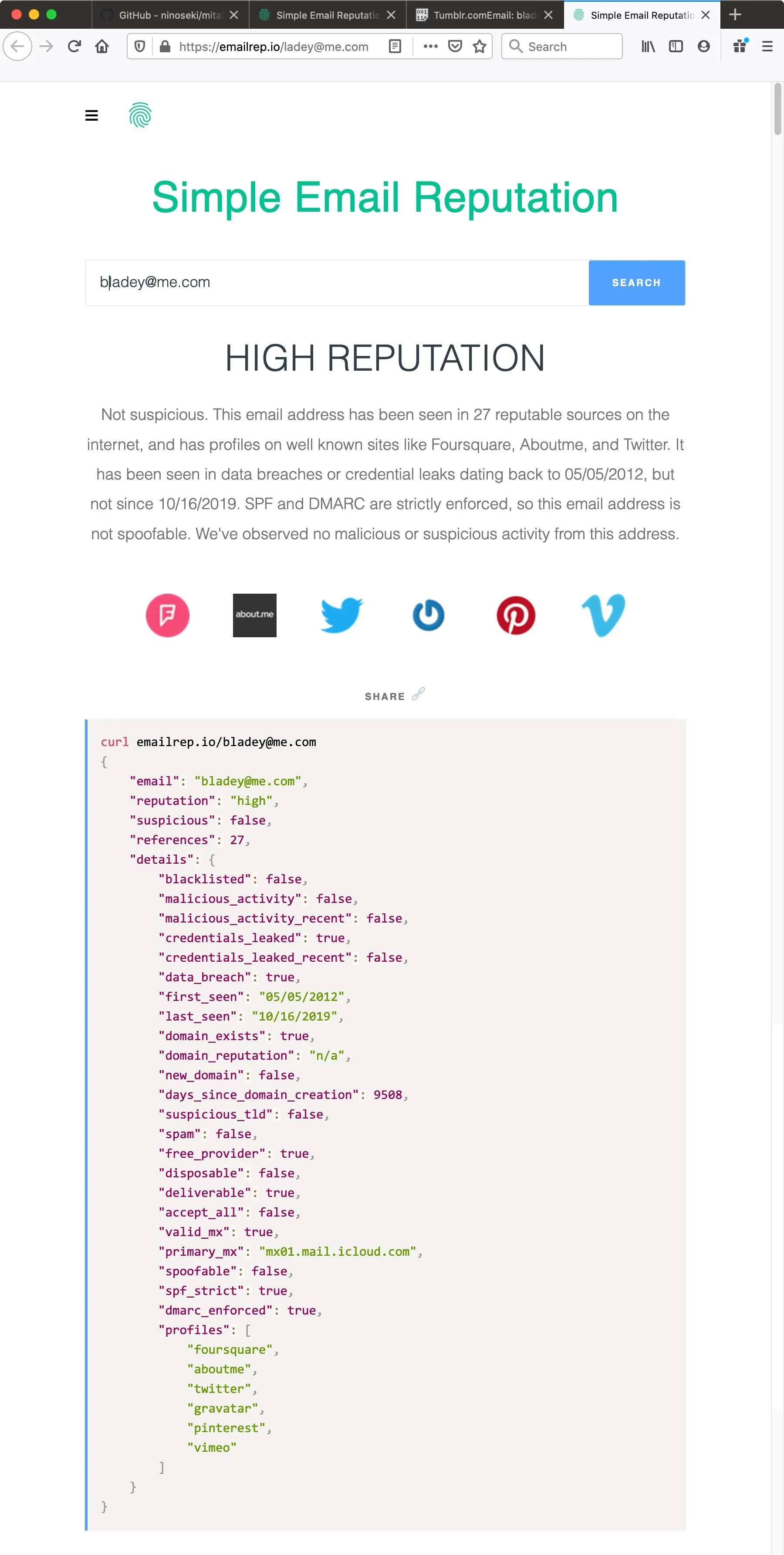
From a report, we can assume that it's probably a real person because the email address has been seen in 27 reputable sources on the internet, including Vimeo, Pinterest, and Aboutme. In the code, we can see all of the information about the different types of high-quality profiles that are linked to the email address, which further legitimizes the account as real.
Performing Malware Analysis on Files
Malware analysis is another exciting tool in Mitaka's arsenal. Let's say that we're on a website, and we have a file that we want to download. We've heard of the tool before, it looks reputable, and the web app seems good. Once we download the file, we can compare the hash to the one listed on the site. If the hash matches, we know we downloaded the file the site's author intended, but how do we know that the file is really OK?
If a virus scanner doesn't catch it on the computer, you can always take the hash of the file that's on the website, right-click it, choose "Mitaka," then use something like VirusTotal. This scanner can identify potentially suspicious files by looking at the hash and trying to find out whether or not it could harm your computer.
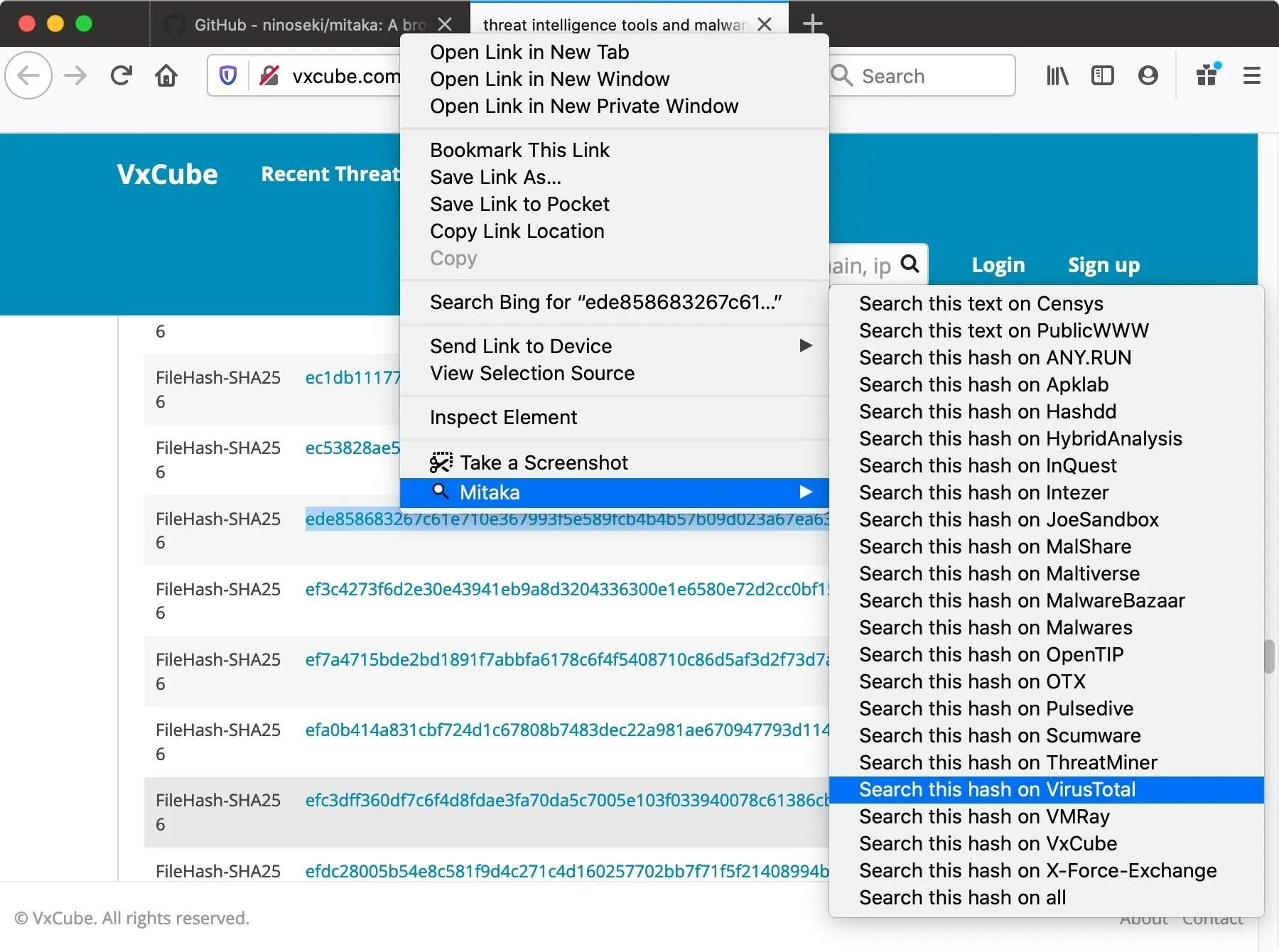
In our case, we can see that there are multiple detections and that this is a macOS crypto miner. So if we had run this on our computer, even though it's undetected by Avast and a bunch of other different, pretty reputable malware scanners, it still would have gotten through.
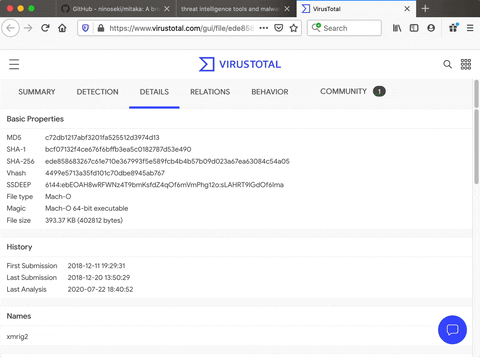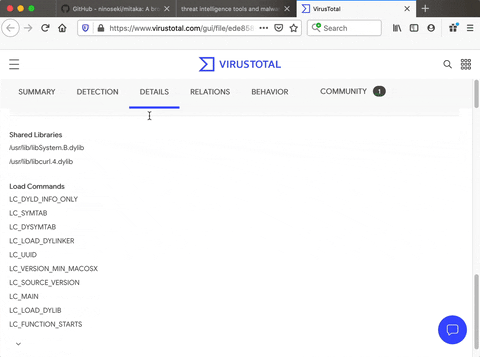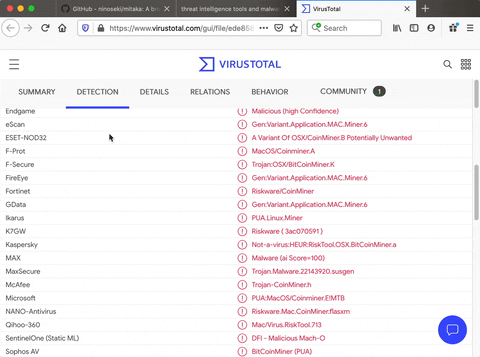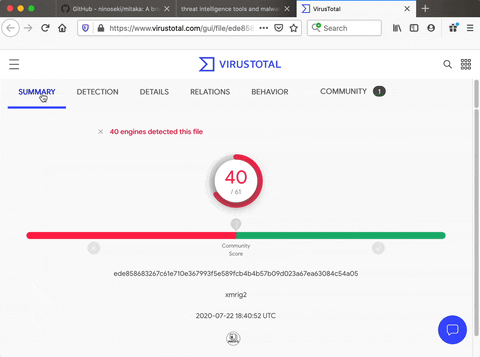
So, as you can see, Mitaka is a pretty effective way of checking to see if a file you encounter on the web has been flagged for doing something bad using tools like VirusTotal or another data source. Available from the menu for this kind of search is Censys, PublicWWW, ANY.RUN, Apklab, Hashdd, HybridAnalysis, InQuest, Intezer, JoeSandbox, MalShare, Maltiverse, MalwareBazaar, Malwares, OpenTIP, OTX, Pulsedive, Scumware, ThreatMiner, VirusTotal, VMRay, VxCube, and X-Force-Exchange.
Checking to See if a Site Is Sketchy
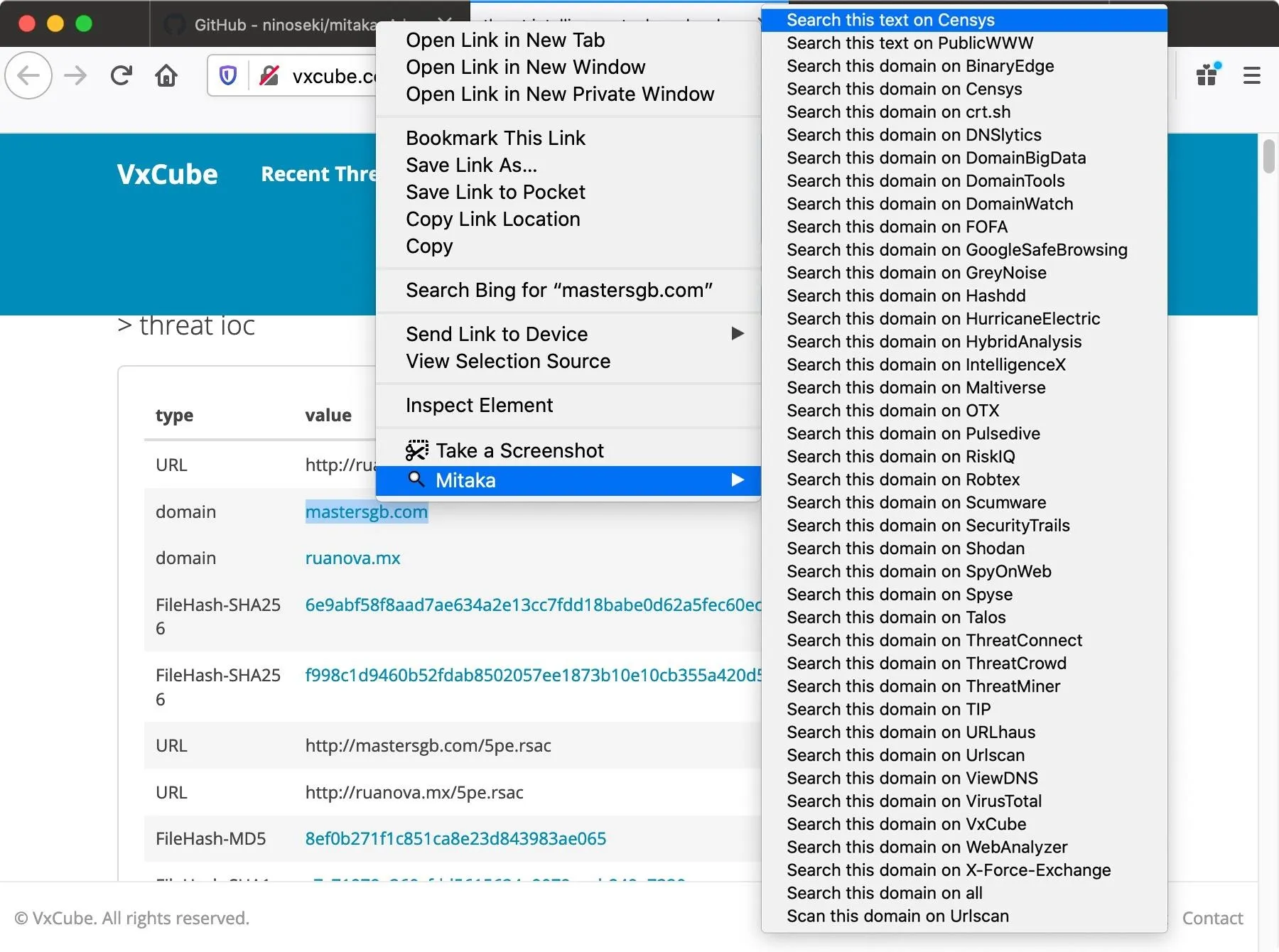
Now, we can also do URL searches with Mitaka. If we're looking at a big data dump, or if we just want to see if a particular URL on a webpage or email has been identified with something sketchy, we can right-click the link, choose "Mitaka," then select from one of the tools.
Available tools for this kind of search include Censys, PublicWWW, BinaryEdge, crt.sh, DNSlytics, DomainBigData, DomainTools, DomainWatch, FOFA, GoogleSafeBrowsing, GreyNoise, Hashdd, HurricaneElectric, HybridAnalysis, IntelligenceX, Maltiverse, OTX, Pulsedive, RiskIQ, Robtex, Scumware, SecurityTrails, Shodan, SpyOnWeb, Spyse, Talos, ThreatConnect, ThreatCrowd, ThreatMiner, TIP, URLhaus, Urlscan, ViewDNS, VirusTotal, VxCube, WebAnalyzer, and X-Force-Exchange.
For our test, let's just check on Censys.
In our case, the domain we searched is associated with some pretty sketchy stuff. Because we can see that it's being used for poor lookups and all sorts of other worrisome activities, we can assume that it's probably not a domain that's owned by a corporation or company that is more straightforward with its dealings.
This is just someone looking to make as much money as they can off of the web space that they have. We can also see that it uses an Amazon system, which means that it's probably just a rented system and not actually someone's physical setup. All of this data points to the fact that this would be a very sketchy website to do business with and may not be as legitimate as you'd like.
There's a Lot More to Explore!
Those were all pretty basic use-cases, but as you can see, there are a ton of different ways we can investigate a clue on the internet using a simple right-click menu. One thing that is really cool about Mitaka is that it's able to detect different types of data so that the contextual search options can cater to the right information.
This was just a quick overview. If you want to get started with Mitaka, you should go through all the different data types, highlight something on a website or email, then right-click and choose your Mitaka search. There is a lot of available sources, and it can be overwhelming at first, but that just means Mitaka is a valuable tool with tons of helpful searches available at the tip of your finger.
Cover photo, screenshots, and GIF by Retia/Null Byte

























Comments
Be the first, drop a comment!