Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.
Introduction to Wardriving
In 2005, hacker Albert Gonzalez and friends were wardriving along a Miami highway, looking for vulnerable WEP networks. They realized that major retailers like Bob's Stores, HomeGoods, Marshalls, T.J. Maxx, and A.J. Wright were using insecure WEP-encrypted wireless networks in their retail locations. Worse, these stores used the network to service the in-store credit card payment systems.
What happened next was one of the greatest thefts of customer credit and debit card information in history.
Albert and his accomplices cracked the passwords of WEP networks in stores owned by TJX Companies, soon pivoting into the Massachusetts-based corporate network and planting a packet sniffer. This sniffer siphoned 90 million customer credit and debit cards to a server in Ukraine, which then sold them on the darknet for around $11 million. Although it was clear that TJX was aware of the security issues around WEP network encryption, they thought it was unlikely someone would notice.

Wardriving can map networks it discovers to pinpoint vulnerable networks.
Wardriving as a concept has been around since the '90s, fueled by programs like NetStumbler. It turns out, you can do a lot with the data created from wardriving, and since then, everyone from hackers to location providers like Skyhook scan and log Wi-Fi networks worldwide.
- Don't Miss: Null Byte's Guide to Wi-Fi Hacking
In the early 2000s, Google got into the wardriving game and began collecting geotagged Wi-Fi data early in their Google Street View initiative. Led by engineer Marius Milner, the creator of NetStumbler, Google Street View cars began logging the Wi-Fi networks of people around the world, creating a directory of wireless networks tied to addresses and Google Maps imagery. This data also included information from networks which had been left unencrypted, causing Google a lot of legal trouble over privacy concerns and resulting in over $7 million in fees.
More recently, the US military, keen to avoid jamming of GPS (which causes drones to become confused and predictable), have been developing NAVSOP, or Navigation via Signals of Opportunity, as a way of determining your position from random nearby signals even when communication from traditional navigation systems have been cut off.
Wardriving as a Tactical Tool
In this guide, we will be using an Android adaptation of Wigle (Wireless Geographic Logging Engine), which will harvest our data and plug it into the Wigle.net database. Why search only your data when thousands of other people have already contributed?

Wigle Wifi Wardriving, a free Android app, shows the location, channel, encryption, and other important qualities of a Wi-Fi network without ever needing to connect to it.
First started in 2001, the Wigle.net website is a collective searchable database of all discovered networks that have been contributed by wardrivers over the past decade. With over 323,446,100 networks mapped to date, searching Wigle.net is a powerful way to perform a database correlation attack. You can also download your entire personal database at any time through the app, as it's stored on the Wigle.net server if you choose to upload it.
Our focus here will be on creating and linking a Wigle.net account with the Wigle Wifi Wardriving Android app (which we'll just call "Wigle Wifi" from now on) to allow us to build our databases of wireless networks, as well as search a crowdsourced database when needed.
Because Wigle Wifi uses easily available hardware, no specialized computer is needed to conduct a detailed analysis of a target. Even an old Android phone will support the Wigle Wifi app. It's subtle and can be used with no trace, so this method can be used in any high-security location discreetly.
Like cellular triangulation, Wigle Wifi locates networks through combining multiple sightings of an access point. These sightings include precise GPS and signal strength measurements used to calculate the likely position of the router, often down to a few meters. From a signals intelligence perspective, this gives us the ability to run passive, undetectable reconnaissance against a target, and query to a massive database of geolocated APs contributed by other wardrivers to track down probe frames.
Setting Up a Wigle Account
Wigle Wifi is tightly integrated with the Wigle.net database and website. So before we even install the Wigle Wifi app, we'll want to create a Wigle.net account.
If you're on your computer, just navigate to Wigle.net in your browser and click on the "Login" button up top to show the "Register" option. In your phone's browser, after going to the website, tap on the hamburger icon, select "Login," then "Register."



Fill out the fields to create your free account. After that, remember the user name and password so you can input it into the Wigle Wifi app later. This will allow you to upload to the site and retrieve your entire database.
Installing Wigle Wifi
Wigle Wifi is available in the Google Play Store, so just visit that link to download and install it onto your Android device. You need Android 4.0 and higher, so this will literally work on any smartphone you have collecting dust around your place.
Running Wigle Wifi on Android
Once you've got the app installed, open it to the main screen. Wigle Wifi is an aggressive app and will override settings to turn the Wi-Fi card on while it's running, so don't be surprised if your Wi-Fi turns on with Wigle Wifi running in the background.
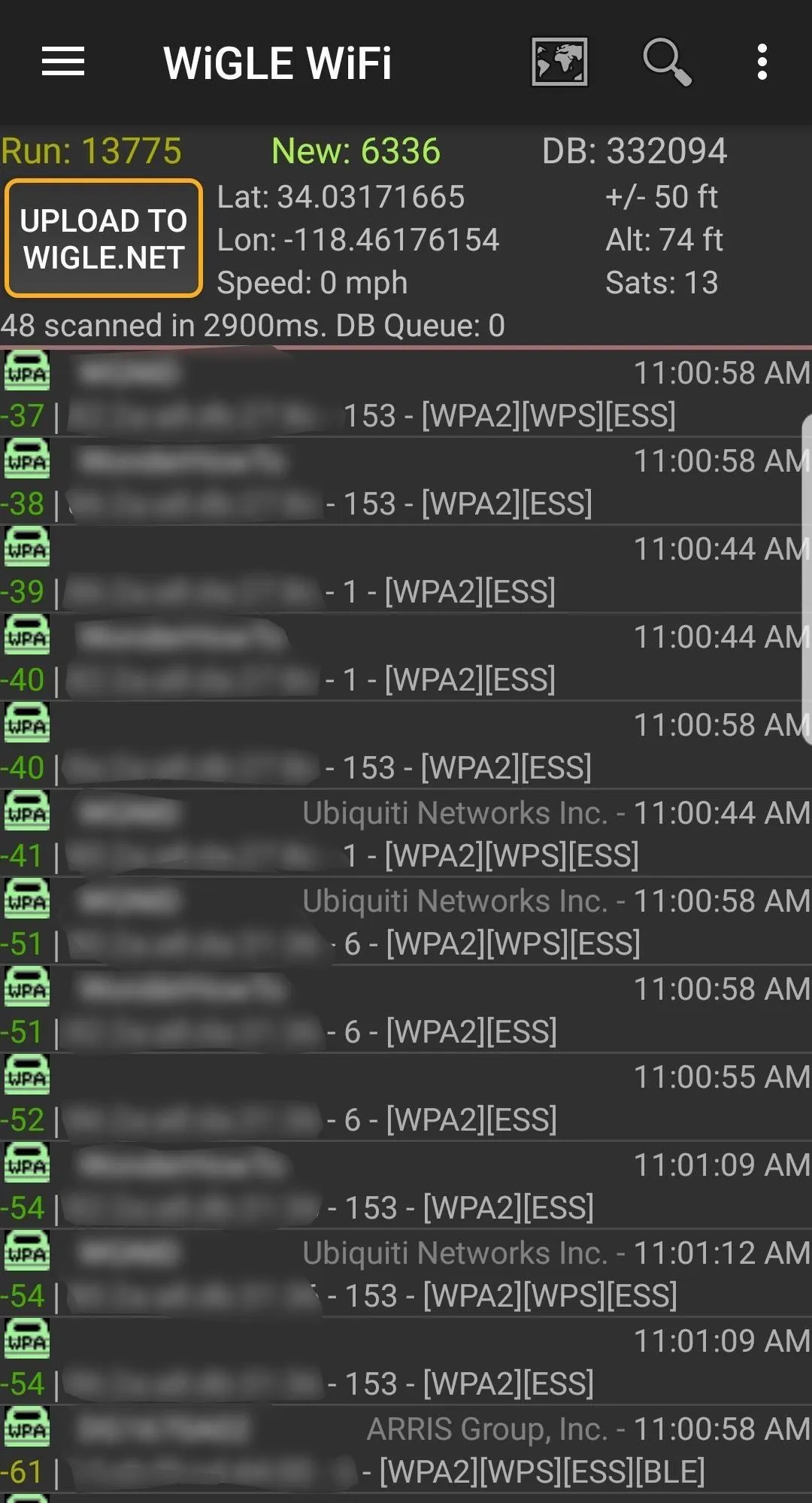
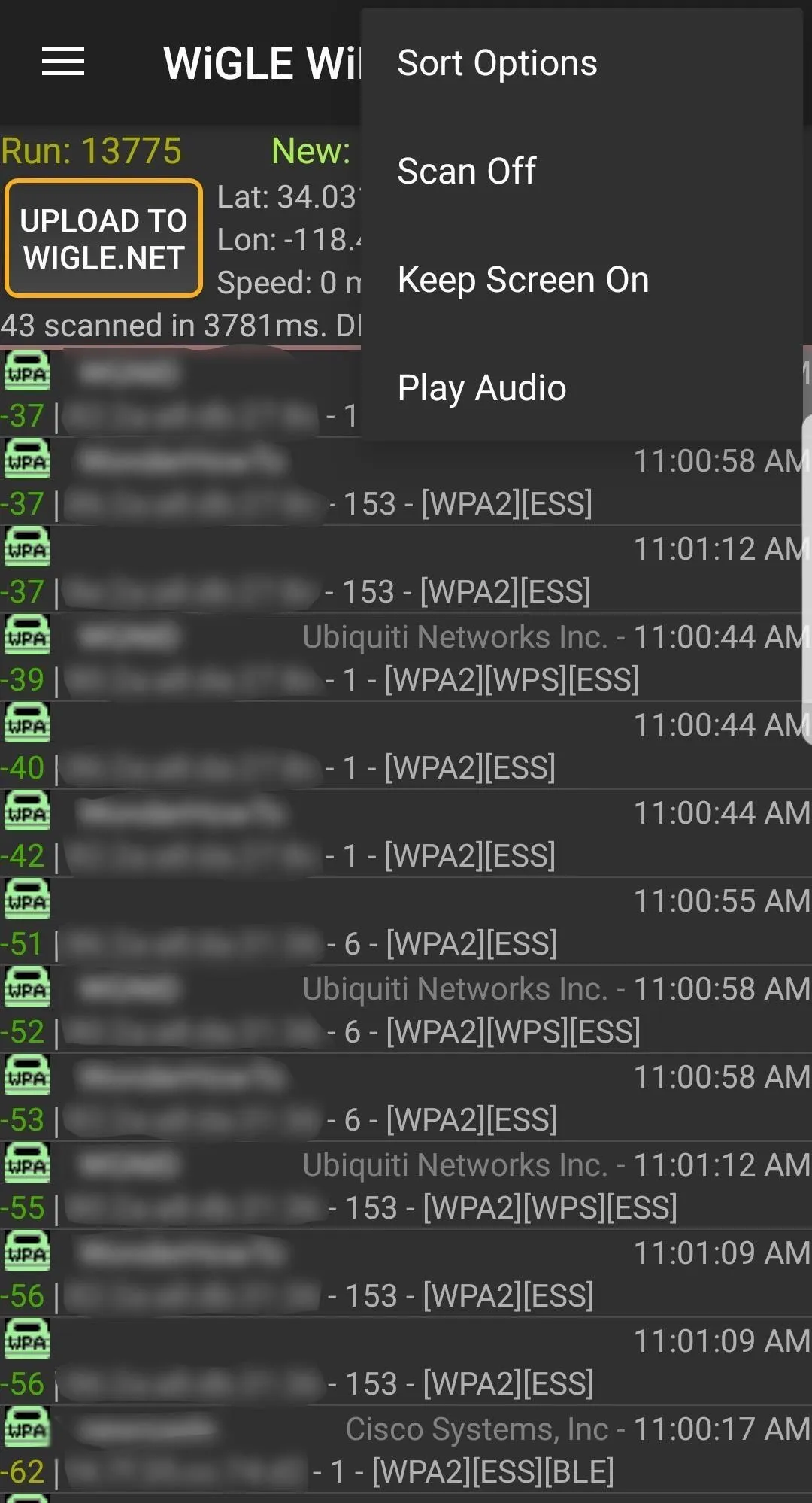
After granting the app all of the required permissions, a run should start right away. If not, make sure you're on the "Network List" page (via the hamburger icon), then tap on the three-dots icon in the top right. Select "Scan On" to begin scanning through channels and collecting wireless information. This will immediately begin displaying wireless networks in the area.
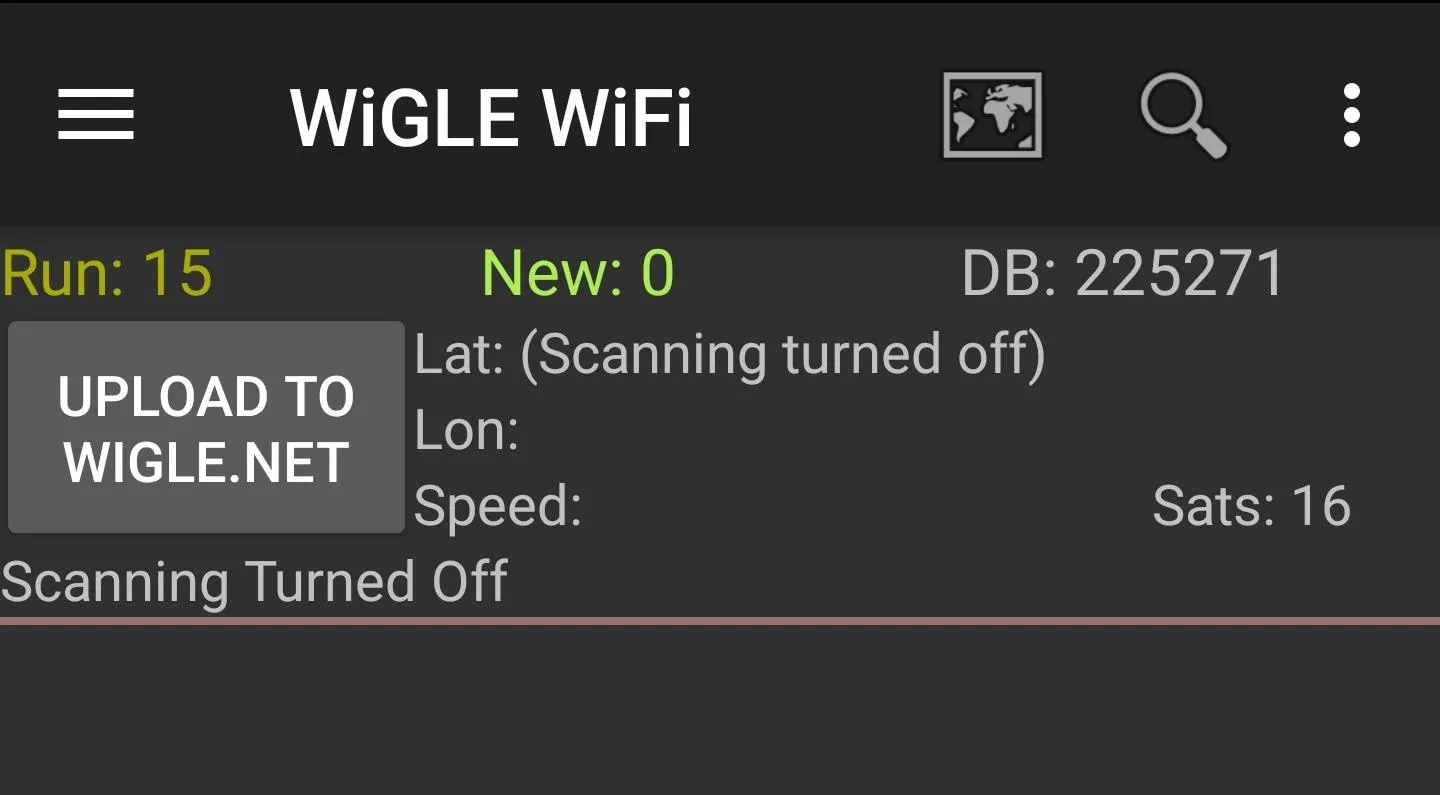
The "Network List" screen with scanning off.
Keep in mind, Wigle Wifi will consume extra power while scanning and logging networks. The more often you run it in the background, though, the better location accuracy you'll get. You can go back to the same three-dot menu and select "Scan Off" when you don't need it.


Adjusting Wigle Wifi's Settings
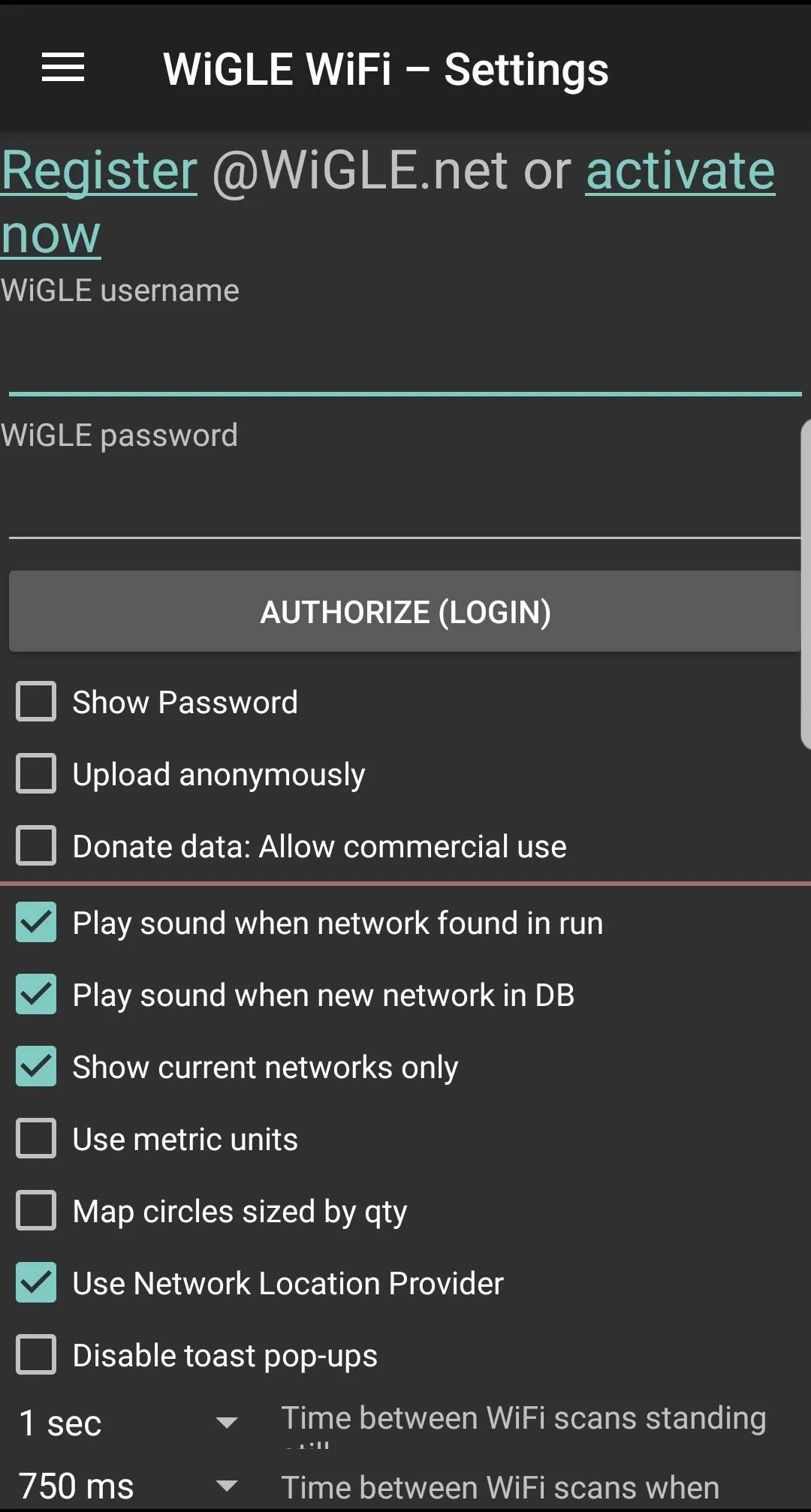
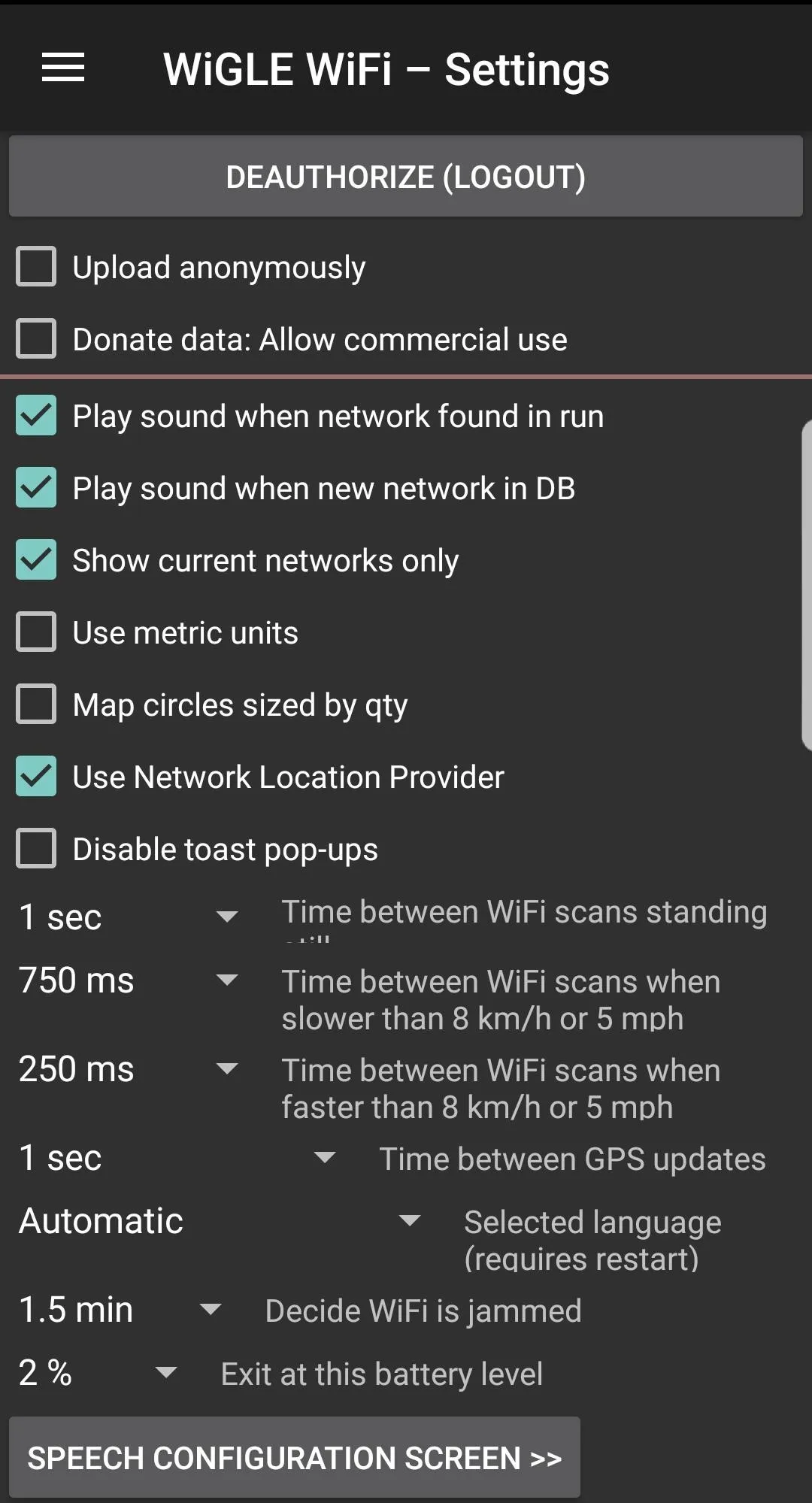
To adjust the settings, you can access the menu by tapping the hamburger icon on the top left and selecting the "Settings" option. At the top of this menu, you can enter your Wigle.net login and password.
Here, you can also adjust the display and run options, as well as specific options like how to increase or decrease scan times in response to changes in speed. Increasing the number of scans will drain the battery faster but capture more networks if you're moving quickly.


Backing Up Your Runs from Wigle Wifi
Make sure you've entered your Wigle.net login at the top of the "Settings" menu item, then back up your data in the app by tapping the "Upload to Wigle.net" button on the Network List page. When you upload your runs, you'll always be able to view and download them later on Wigle.net.
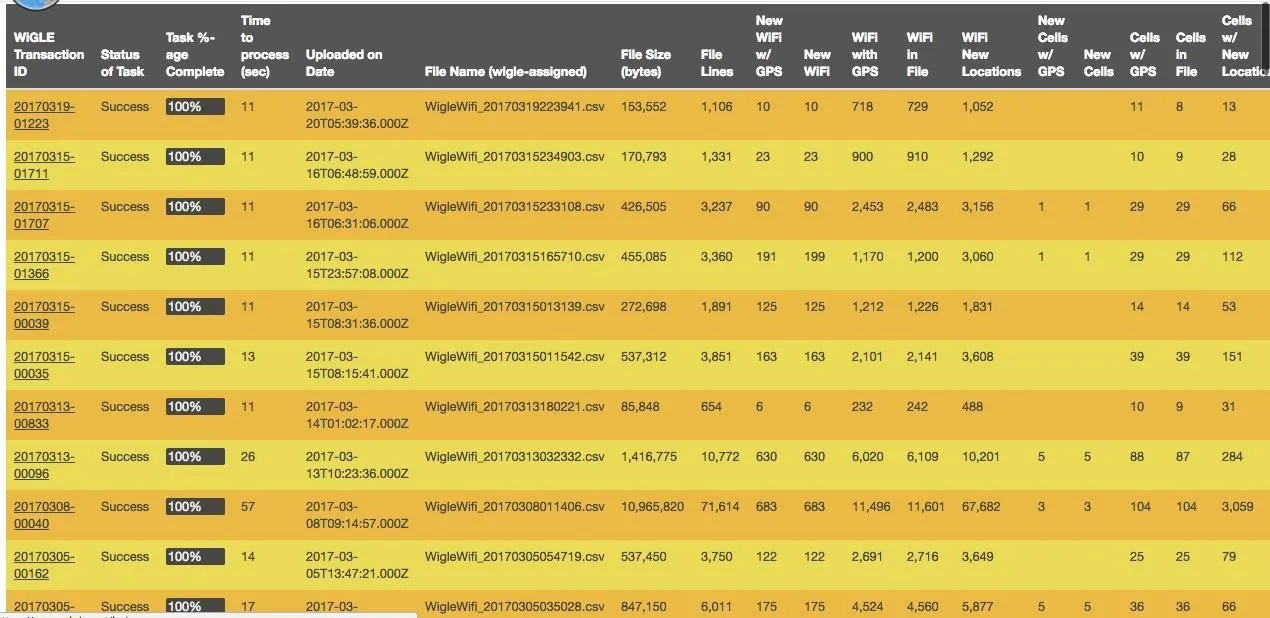
Here, we see many runs with number of networks and other information displayed.
Using the Wigle.net Website
To easily search your entire database, as well as other contributed data, we'll open Wigle.net in a browser. You can do this on your phone's browser or your computer's browser.
There are many ways to search for information on Wigle.net. In the Wigle Wifi app, you can search for nearby networks, but on the website, you can search the entire database of contributions. The most obvious settings are under the "Search" function that appears after you log into your account.
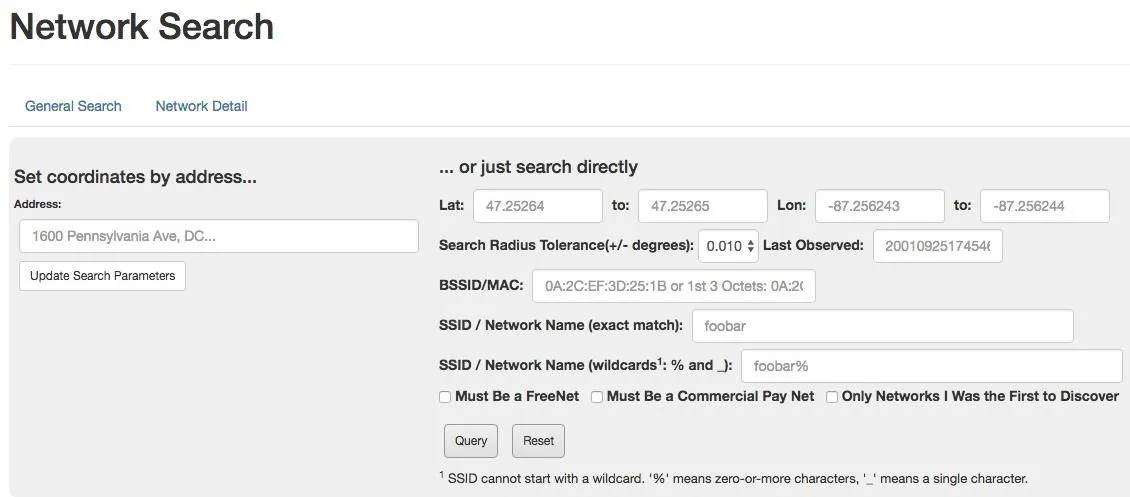
Searching the Wigle.net database for a network.
For a more visual overview of the target, check out the "Maps" section. You can type in an address and adjust overlay filters to create a graphical map of the target with wireless data overlayed.
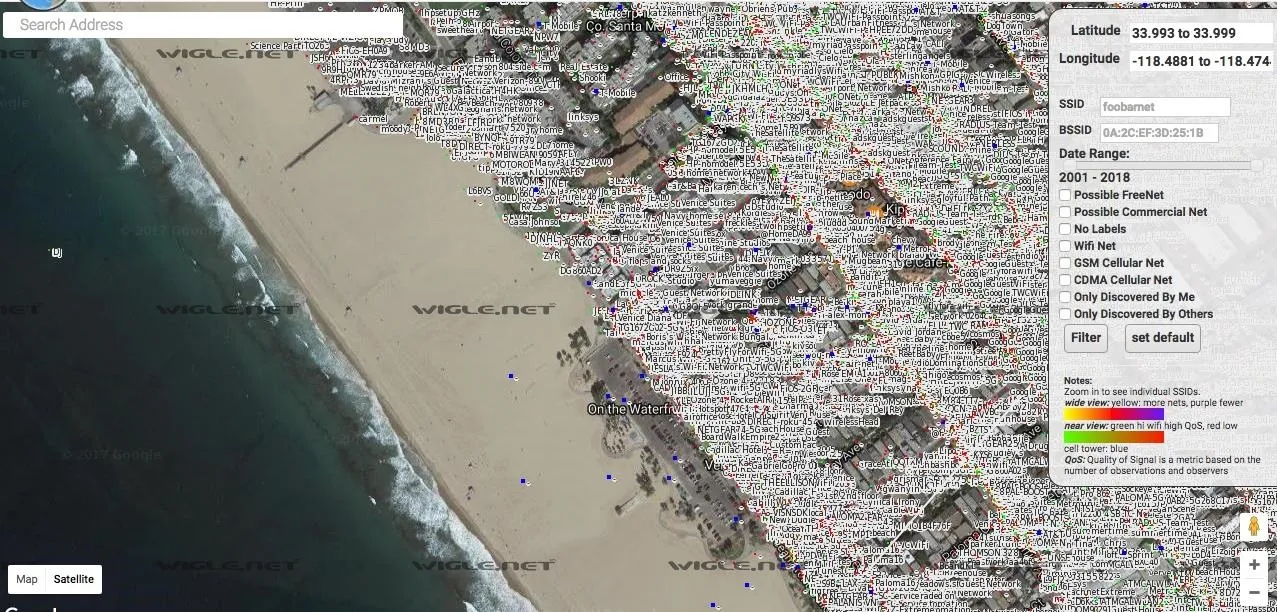
Lots of people wardrive, and there is a lot of information already out there.
Selecting on a network will give you more information about it. You can filter networks with the list of options on the right of the screen. Look up your address and see if your router has been logged!
Searching Local Queries in Wigle Wifi's Map
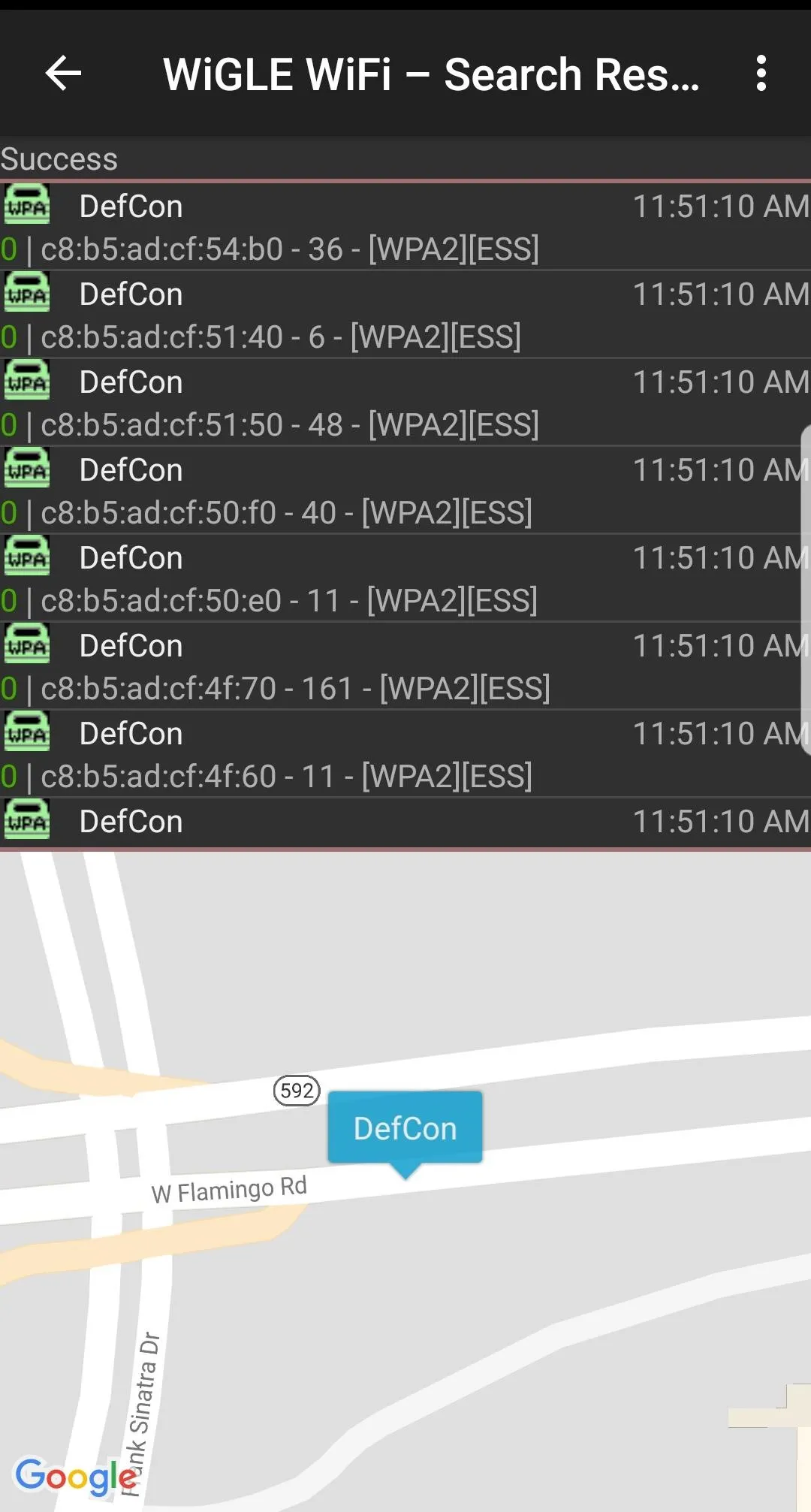
If you want to search a wardriving run on your phone rather than Wigle.net, you can do so (or watch results appear on the map live) by tapping the "Map" menu option. This will open a map of the area pinned to your current location and display nearby networks. Tapping on a network will bring up information about the manufacturer, the security used, and the channel and BSSID. Below, we see some mapped results from a local run.
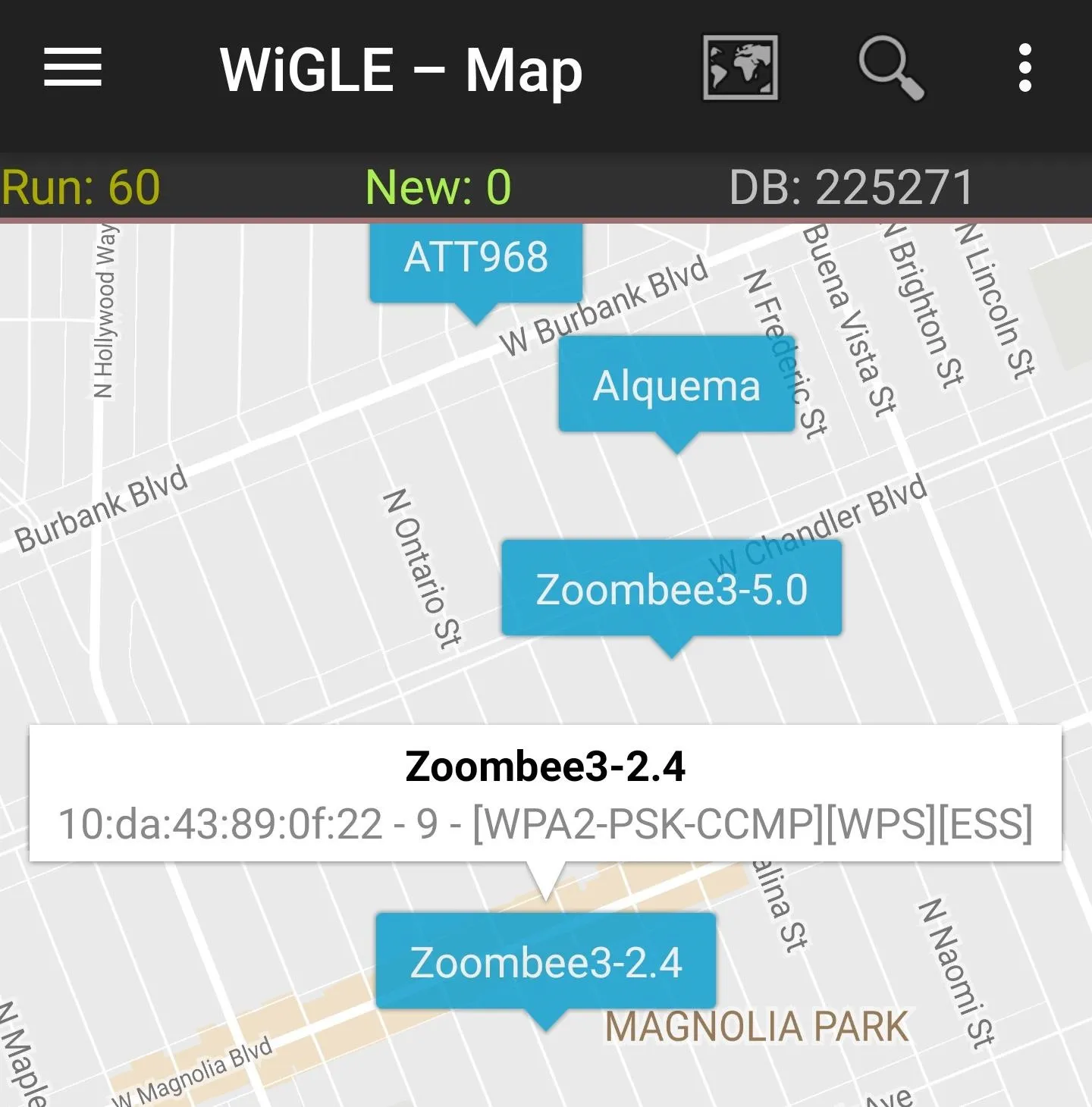
Querying the local database on the Wigle Wifi app.
You can see how many networks you've collected in a run by selecting the "Dashboard" option in the menu.

Wigle Wifi lets you build your own database of networks around you.
Exporting Data from Recon Runs in Wigle Wifi
Maybe you want to work with your data directly. Navigating to the "Database" tab on the Wigle app shows the various options for exporting data from Wigle Wifi.
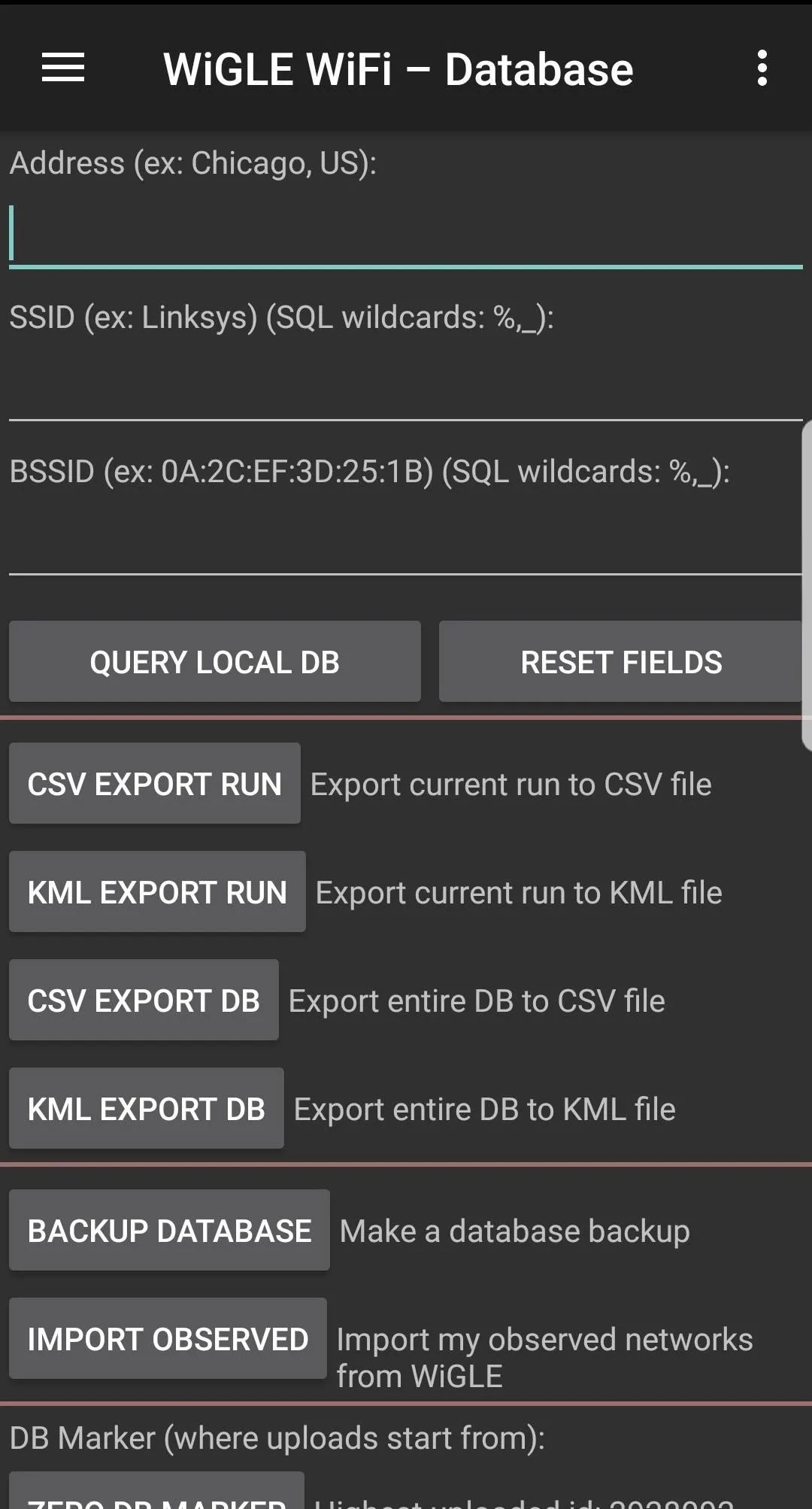


If you want to pull everything you've ever uploaded into one file, you can select "Import Observed." Doing this pulls from Wigle.net, so be prepared to wait a little for the download if you have a ton of networks. You can also use this tab to search network runs, although sometimes this functionality can be a little buggy.
The Wigle team also shared a few more tips with us for accessing your data: First, you can access the runs from your SD card or internal memory; Each run is archived upon upload, and the SQLite database can be backed up and accessed. Second, the transid on your uploads page gives you a link to a KML representation of your run with bad and incomplete data points filtered out for the most part.
Contributing to the Big Picture
Wigle.net works because of people contributing. If you feel like adding to the giant pool of knowledge that is Wigle.net (or you've got a competitive streak), consider adding to the community database to build a better OSINT tool for fellow wireless researchers.
There is a thriving community of wardrivers who compete to discover the most networks, and anyone can join! You can even create a team to rank up against other wardriving teams. With some users having discovered millions of new networks, competition is fierce for a place in wardriving history. Check out the "Rankings" menu item in the app.
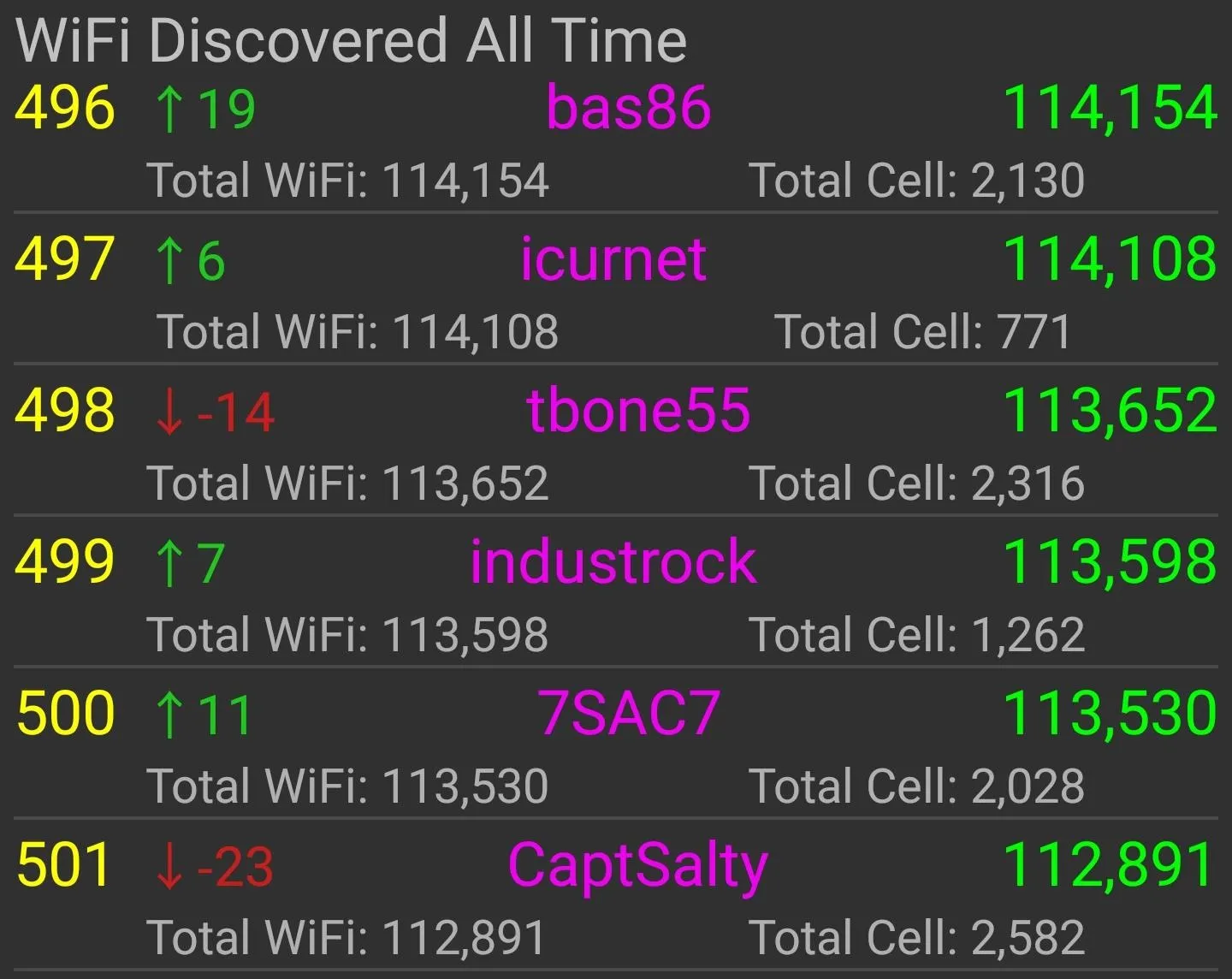
It currently takes finding over 100,000 new (previously unknown to Wigle.net) Wi-Fi networks just to crack the top 500 users on Wigle's leaderboard, so be prepared to do some serious hunting to earn street cred in the wardriving community!
Conclusion
Whether you're wardriving for tactical network reconnaissance, to build a database of your city's Wi-Fi networks, or just to contribute to an exciting project, Wigle Wifi is a great tool to quickly learn about the wireless world around you.

Tactical wardriving, or warwalking, can give you a picture of a target's wireless infrastructure.
As we learned with Routersploit, even an unrooted Android phone can get you started hacking! If you have any questions, ask them here or @sadmin2001 on Twitter or Instagram.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by SADMIN/Null Byte

























Comments
Be the first, drop a comment!