Null Byte is looking for forum moderators!
Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).
These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. This week's mission on HackThisSite was to try to get to the password file in the current directory by hacking the previous mission we did last week.
Basic Mission 9
We are greeted upon starting the mission.
"Network Security Sam is going down with the ship - he's determined to keep obscuring the password file, no matter how many times people manage to recover it. This time the file is saved in /var/www/hackthissite.org/html/missions/basic/9/.
In the last level, however, in my attempt to limit people to using server side includes to display the directory listing to level 8 only, I have mistakenly screwed up somewhere.. there is a way to get the obscured level 9 password. See if you can figure out how...
This level seems a lot trickier then it actually is, and it helps to have an understanding of how the script validates the user's input. The script finds the first occurance of '<--', and looks to see what follows directly after it."
In order to hack this, we need to go to the previous mission and inject some nasty HTML that will list the contents of the mission 9 directory.
To exploit this, we need to mask our command in an HTML comment, then traverse using "../" to go up one more level compared to the original hack, followed by the appropriate mission number. In our case, we use 9.
<!--#exec cmd="ls ../../9" -->
This tells the server to execute the command ls in a terminal, replacing the returned names with a subdirectory listing.
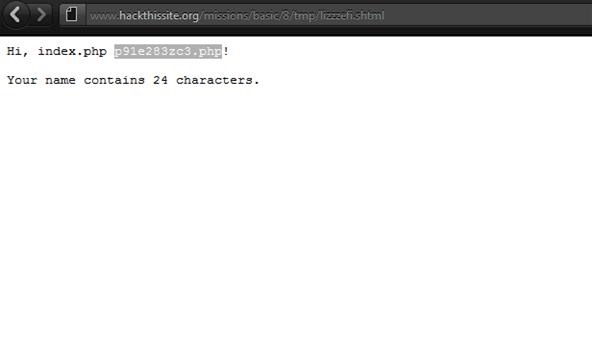
View the obscurely named PHP file in this directory by appending its name to the end of the original mission 8 URL. This will reveal our password! Enter it in the field and the mission should credit your HTS account with the points.
Want more Null Byte?
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























Be the First to Comment
Share Your Thoughts