Null Byte News


Buyer's Guide: Top 20 Hacker Holiday Gifts for Christmas 2017
Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

News: Hak5 Just Released the Packet Squirrel
Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

Release the KRACKen: WPA2 Wi-Fi Encryption Hackable Until All Clients & APs Are Patched
Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

News: WannaCry Ransomware Only Works if You Haven't Updated Your Computer in Months
As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

News: Intel Confirmed Critical Escalation of Privilege Vulnerability — Now What?
With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

News: Malware Targets Mac Users Through Well-Played Phishing Attack
Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).
News: The DEA Spent $575,000 of Your Tax Dollars on Zero-Day Exploits
The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

News: 'Impossible to Identify' Website Phishing Attack Leaves Chrome & Firefox Users Vulnerable (But You Can Prevent It)
Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

News: Shadow Brokers Leak Reveals NSA Compromised SWIFT
The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

News: Hack the Switch? Nintendo's Ready to Reward You Up to $20,000
It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

News: How Governments Around the World Are Undermining Citizens' Privacy & Security to Stockpile Cyberweapons
In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

News: Use ProtonMail More Securely Through the Tor Network
ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
News: A Siri 'Feature' Makes Personal Information Accessible from a Locked iPhone
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

News: It's Time to Ditch Your Yahoo Account
If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

News: Mirai Botnet Source Release Threatens Increased DDoS Attacks from Smart Home Devices
Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

News: Hello to the Null Byte Community!
Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.
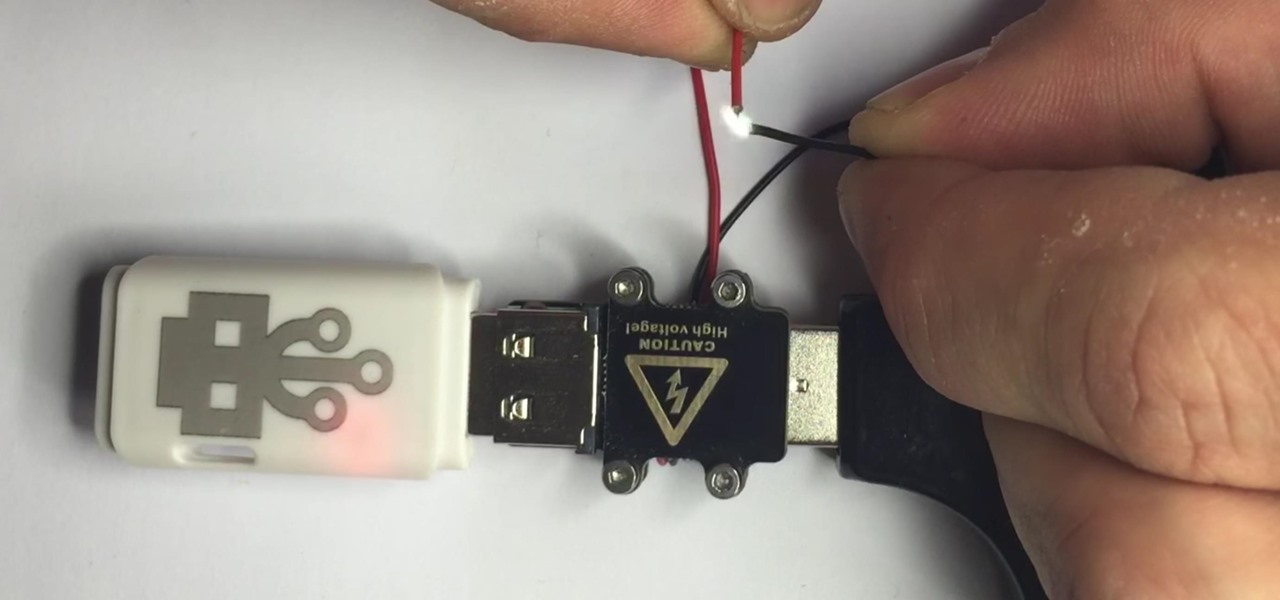
News: The Cheap USB Kill Stick That Destroys Any Computer You Want
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

News: Samy's MagSpoof Hacking Device Was Just Featured on Mr. Robot
Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

News: 'Beast' Cracks Billions of Passwords in Seconds
Dr. Michael Pound, a computer science researcher and professor at the University of Nottingham, uses hashcat and 4 GPUs in parallel to go through 1o billion hashes a second in this Computerphile video. He calls his deep-learning server the "Beast." If you're new to cracking passwords, he does a great job breaking down the process of what's going on as hashcat does its magic.

News: If you use Tor Browser, the FBI just labelled you a criminal.
Well this law was passed... Our privacy is slowly being pulled away from us. But I'm certainly not going to let it stop me. We'll just have to take more secure measures. If You Use Tor Browser, The FBI Just Labeled You a Criminal.

The Panama Papers Hack: Further Proof That Hacking Is Changing the World
Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.
News: Even Microsoft Acknowledges the Superiority of the Bash Shell Now
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

News: Capture the Flag, Round 1
As many of you know, Standard User proposed that we start a Capture the Flag (CTF) competition. I think this is a great idea! Standard User proposed to set up the server and the flags for this first competition. Since Standard User was new to our community, I asked him to postpone the start of this competition until I had a chance to make certain that this was safe and legitimate for our community. I have good news! With the help of Phoenix750, we have done the necessary due diligence and we ...
News: What Are the Motivation Things You Do or Read to Become a Hacker?
I usually read hackers manifesto. :)

News: U.S. Justice Department Indicts Iranian Hackers
Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...
News: FASCINATING WORLD of NETWORKING...
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

News: Ukraine Power Attacks; How, Who and Why?
Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

News: Keep Practicing.
One of my favorite quotes. What's yours ??

News: Uber Is Offering Up to $10,000 to Anyone Who Finds Bugs in Their App or Website
If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.
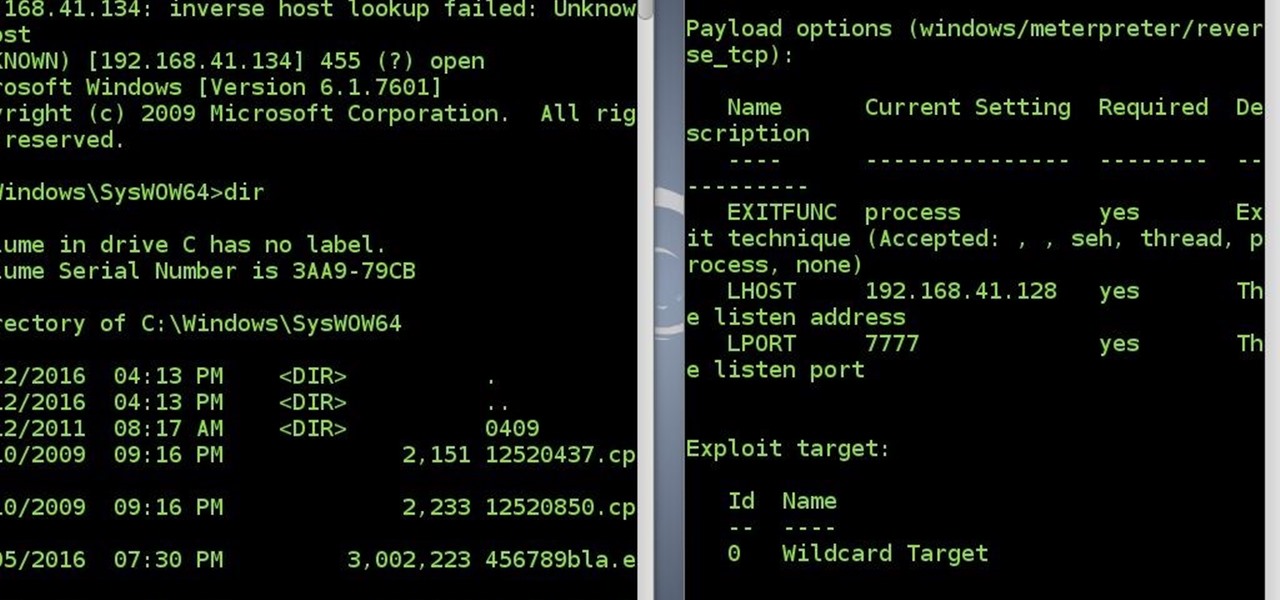
News: Reconnect to Victim's System Success
After a long time I succeed to reconnect to victim's system without a touch(the victim did not click the app again)

News: A Brief History of Hacking
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

White Hat Hacking: Hack the Pentagon?
The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

News: And the Winner of the White Hat Award for Technical Excellence Is...
It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

Security Alert: Your Wireless Mouse or Keyboard Can Be Hacked
If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).
News: Latest VPN Review
We all know that VPNs may or may not keep logs, and may or may not tell the whole truth when asked about what records they do keep. With this in mind, here's the latest review of VPN services from those lovely folks at Torrentfreak. https://torrentfreak.com/vpn-anonymous-review-160220/

News: Why YOU Should Study Digital Forensics
As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"
News: The Hacker's Jargon
removed!

News: Null Byte's First White Hat Award for Technical Excellence Contest Has Closed
The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Hacking in the Media: Our Craft's Portrayal as Black Magic
People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234.

News: Null Byte's First Technical Excellence Tutorial Contest Ends Feb. 15, 2016!
As you all know, the first Null Byte Technical Excellence Tutorial Contest ends this coming Monday, Feb. 15, 2016. If you are working on another great article or your first article, try to complete it and submit it before midnight Pacific Standard Time (PST) to be considered in this contest. The winner of this contest will not only receive a certificate verifying the technical excellence of their tutorial, but they will also receive a free copy of the Professional version of the Exploit Pack ...







