The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous Englishand Swedishlanguagemovies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.
The Girl in the Spider's Web was actually a bit of a box office failure. While critics didn't go easy on the plot or performances, there are many hacks featured in the film worth examining in detail. It's a relief to see a relatively high degree of realism on the topic, as television and movie studios are known for producing over-the-top hacking scenes (we're talking about you, NCIS).
While the hacking scenarios in the film aren't entirely descriptive, most being super brief and vague, it doesn't make them any less riveting to watch. Just because there are no verbal or even visual indications of how an attack or exploit was performed, it doesn't mean they aren't legit. However, it does make it difficult to say with any certainty how any of the hacks can be recreated.

The Girl in the Spider's Web/Sony Pictures Entertainment
If you've bought the Blu-ray or DVD or digital download, replaying the hacks won't be enough to understand what's actually going on in the scene. But we're here to help with that. We watched the film over and over again, analyzing the hacks, gadgets, and technology featured within, and we hope to shed some light on the practicality of the exploits, software, and applications used, as well as deduce how the attacks were likely executed.
Spoiler Alert
Keep in mind, our analysis was done using only the information provided in the film, not the book. There are many spoilers ahead which may apply to both, so it's worth at least watching the movie or reading the book before going any further.
1. Lisbeth Disables a Home Security System
The movie opens with Lisbeth breaking into the home of Peter Ahlgren, a CEO who abuses his wife and was acquitted of assaulting two women. The power in the entire apartment gets shut off while Peter is being abusive. Peter investigates by approaching the home security system console and is presented with a system reset request, which he uses to regain power to his home.

The Girl in the Spider's Web/Sony Pictures Entertainment
First of all, it would make more sense for Peter to inspect the electrical breakers in the event of a power outage, but since the filmmakers likely wanted to put emphasis on the security system being disabled, they smashed the two together.
After zooming into the image and enhancing the sharpness, the text in the console becomes clear: "Fault Code 120-00-01." Fault codes, similar to those found in automotive vehicles, provide an identification code that can be used to programmatically diagnose error conditions and suggest appropriate responses for the end-user and manufacturer. The fault code seen here isn't real, so there are no telling how it was invoked.
The security system could have been disabled simply by cutting the power to the entire apartment or building. Home security systems usually have backup power supplies for redundancy in the event of a blackout, but this doesn't seem to be the case in the movie. Additionally, security control panels will sound an alarm if tampered with, so it's difficult to say how Lisbeth pulled this off. Unfortunately, there's isn't enough information in the scene to further speculate.
Popular wireless consumer alarms have been highly susceptible to hacking for years via "proactive jamming," a kind of denial-of-service attack. The control panel is wirelessly flooded with signals that prevent the receiver on the door from communicating to the control panel that the door has been opened. For a comprehensive look at the subject, check out Eric Escobar's talk on hacking home security systems using software-defined radio.
2. Lisbeth Hacks Peter's Smartphone
As Peter hangs helplessly upside-down from the ceiling, Lisbeth takes his smartphone and inserts a small USB Type-C flash drive with a glowing blue light into it. The USB-C device, which holds the payload, proceeds to automatically bypass the lock screen, giving Lisbeth full access to his bank accounts.

The Girl in the Spider's Web/Sony Pictures Entertainment
At first glance, the hack appears to go overboard with flashy terminal popups appearing on the screen. If we take a closer at what's happening, it shows a few interesting things. First, the top of the pop-up reads "RUN://phAckU.dll," which would indicate some kind of malicious DLL was injected upon inserting the flash drive. In the past, it has been proven possible to dynamically inject shared libraries into running Android processes.
Second, the URL at the bottom of the pop-up belongs to a real website. ScienceDirect is an open-access peer-review website for science and medical research. The URI scheme "/science/article/pii/" is legitimate but I didn't manage to find the article starting with "S10506..." on my first attempt.

The Girl in the Spider's Web/Sony Pictures Entertainment
The "MFCV," "MUAPT," and "EMG" acronyms that appear multiple times in the exploit seem to have no real meaning or relation to smartphones that are immediately obvious. Respectively, these acronyms stand for "muscle fiber conduction velocity," "motor unit action potential," and "electromyogram," which are all legitimate medical terms. I know what you're thinking: Wow, this analysis of the hack got medically technical really quick. My thoughts exactly. Using the acronyms in my search allowed me to locate the full "S10506..." article.
So what do these medical terms have to do with the lock screen hack? It's likely related to wearable USB-powered devices that track muscle fatigue in medical patients. The devices transmit fatigue and surface electromyographic (sEMG) data to an Android application in real time via Bluetooth, and they contain an application-specific integrated circuit (ASIC) that track muscle fatigue by estimating muscle fibre conduction velocity (MFCV). The wearable and Android application together allow for state-of-the-art muscle fatigue monitoring.
Lisbeth might have utilized a vulnerability in Android that allowed her to abuse the MUAPT and ASIC functionalities to bypass the lock screen or exploit the device. Notice the "EMG_MUAPT_inter_spike_interval" function in the pop-up. This could indicate some kind of injection of false moment data that overwhelmed the ASIC system and allowed for some degree of exploitation. Whether or not Peter was using any of these medical technologies with his Android is never made clear.
3. Jan Holtser Uses His Laptop to View Security Feeds
Frans Balder is a computer engineer and cryptographer. In cooperation with the NSA, Frans has created "FireFall," a piece of software designed to access and control the nuclear arsenals belonging to major countries around the world — effectively creating a cyberweapon to remotely control all nuclear weapons.
Frans employs Lisbeth to steal FireFall after losing control of it to the NSA. As they rendezvous at a museum, we learn Frans is being followed by Jan Holtser, a prominent member of The Spiders (more on this sinister collective of bad guys later) and one of the primary antagonists of the film. Jan is shown observing Frans' meeting with Lisbeth using a pocket-sized laptop.

The Girl in the Spider's Web/Sony Pictures Entertainment
Jan's laptop is shown multiple times in the film, always very briefly. This laptop is the GPD Pocket, currently considered one of the smallest laptops in the world.
Jan appears to be watching Frans and Lisbeth through a museum surveillance camera, which would suggest he hacked into the camera system. However, this is never directly addressed in the film.
4. Lisbeth Remotely Hacks NSA Agent Edwin Needham
This is the first major hacking scene in the movie. It opens with Edwin Needham, the senior security agent at the NSA responsible for storing and securing FireFall. Needham isn't an antagonist but spends most of the movie trying to track down Lisbeth after she steals it from him (as we're about to see).
Needham receives a notification from an unknown Android app on his phone regarding an unauthorized login taking place on his system.

The Girl in the Spider's Web/Sony Pictures Entertainment
Enhancing the image of his phone doesn't produce helpful information this time. It's unclear what kind of application is being used but seems to be an account management interface. Login notifications and intrusion detection systems are common in high-security environments like the NSA headquarters.
Upon discovering the successful login, Needham rushes to his office and finds a file transfer in progress on one of the computers. At this point, I'd like to point out: a computer storing software like FireFall should be air-gapped, as well as require some form of two-factor authentication to log in. C'mon, Needham, get it together!
There's no mention of the software, protocol, or port being used to transfer the file, but it seems like it should be possible to simply stop the download directly from the workstation. It's also unusual for an advanced IDS to allow such data exfiltration while aware of an active breach. A system capable of identifying an intruder ("unknown user") exporting a large file should be able to prevent the activity altogether, but it's only just a movie, I know.
As for how Lisbeth breached the NSA network and Needham's workstation, it's impossible to say based on the events that transpired. She's just that good?
5. Needham Shuts Down the Facility with a Killswitch
With the exfiltration still in progress, Needham quickly engages the "Emergency Stop" system. This effectively cuts the power to the entire facility and disconnects Lisbeth from the workstation.

The Girl in the Spider's Web/Sony Pictures Entertainment
Emergency Stop (aka E-Stop) or a killswitch is a safety mechanism used to abruptly shut down machinery in an emergency, usually when it can't be stopped in the normal manner. Unlike a typical shutdown switch which allows the system to power off gracefully, killswitches are designed to immediately abort operations as quickly as possible. It's absolutely believable that a sophisticated government agency would have a working killswitch readily available in the middle of their office to mitigate security breaches.
6. Needham Tracks Lisbeth's IP Address
After realizing FireFall had been moved from his workstation, Needham proceeds to track Lisbeth's IP address despite her efforts to mask it behind at least eleven different servers around the world.

The Girl in the Spider's Web/Sony Pictures Entertainment
The internet is entirely made up of interception points. While expensive to collect and store incomprehensible amounts of web traffic on a daily basis, agencies still make efforts to tap the backbone of the internet.
This is kind of correlation is theoretically probable, while not yet proven or disclosed as being possible. If a government agency, in cooperation with other government organizations, becomes capable of observing a large majority of the internet at once, they would be able to literally connect the dots and identify the origin of web traffic the way Needham geographically located Lisbeth.
7. Lisbeth Stops an Elevator in Motion
After being attacked in her home and losing FireFall to Jan, Lisbeth seeks out Mikael Blomkvist to help track him down. Mikael is an investigative journalist who Lisbeth has had dealings with in the past. She trusts Mikael but remains emotionally detached as her feelings for him seem to complicate things.
Mikael is shown entering an outdoor elevator when it suddenly stops in motion. He inspects the elevator buttons and notices Lisbeth in the elevator adjacent to his.

The Girl in the Spider's Web/Sony Pictures Entertainment
The particular type and model of the outdoor elevator couldn't be identified, so it's not possible to say if the elevator could actually be remotely stopped. However, it's reasonable to believe modern elevators can be remotely controlled. According to Null Byte writer Hoid, elevators operate on very simple control systems that can be easily abused by hackers to control or stop the elevator in motion.
8. Plague Tracks Frans Balder Using Geotags
Lisbeth's follow-up meeting with Frans Balder was missed because she was attacked in her home by Jan. After the attack, she visits Plague, a fellow computer hacker and associate that appears several times in the movie to assist Lisbeth with her hacks in various ways. Lisbeth inquires about the whereabouts of Frans Balder, and Plague replies:
Checked out of his hotel. Cell phone disconnected. Look at this, look who he went to. His last geotag showed him at Säpo headquarters this morning.

The Girl in the Spider's Web/Sony Pictures Entertainment
Geotag refers to the process of adding geographical coordinate metadata to various media files such as photographs or videos. GPS coordinates have been used to catch black hat hackers in the past. Most notably, in 2012, FBI agents extrapolated a hackers geographic location using the GPS metadata found in a photo he uploaded to the internet.
Plague doesn't say how the geotags are collected, however. Geotags can also be included in SMS and other forms of digital communication, so it's possible he gathered that information by other means.
9. Plague Hacks Swedish Security Service Servers
Unaware that Lisbeth was attacked and lost FireFall, Frans panics, suspecting she decided to keep it. In his distress, he seeks the aid of Gabriella Grane, the deputy direcotr of the Swedish Security Service (Säkerhetspolisen, aka Säpo). In the same scene as above, it appears Plague has surveillance footage of Frans' private meeting with Gabriella. It also appears he acquired surveillance footage of a building with "Säkerhetspolisen" on the front.

The Girl in the Spider's Web/Sony Pictures Entertainment
In a later scene, Plague again tracks Frans' location and states, "I got into the Säpo servers. They're keeping him at 774 Birger Jarlsgatan." There's no indication of how or when exactly this was accomplished.
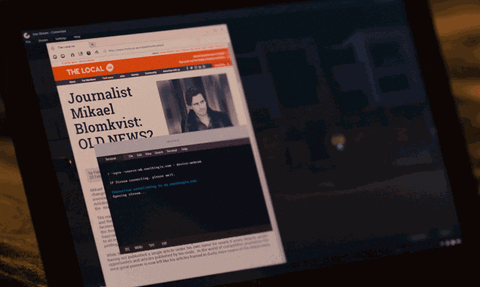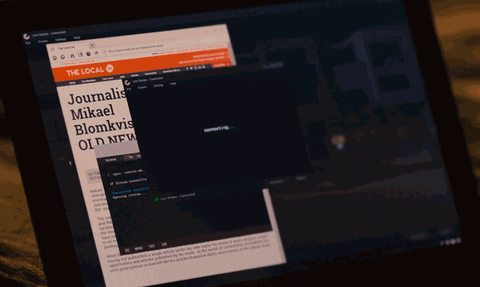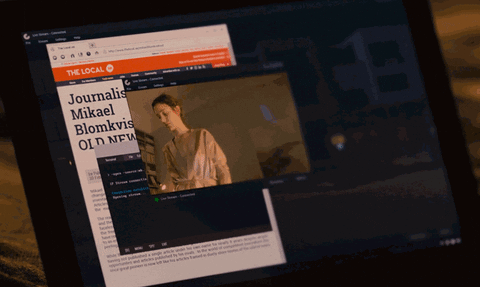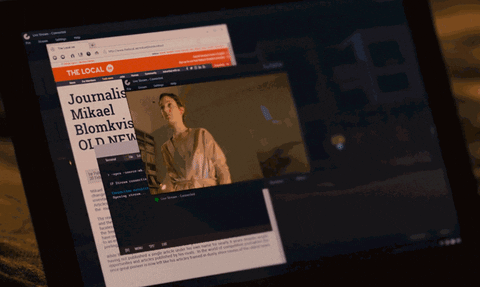
10. Lisbeth Accesses Mikael's Laptop Webcam
Mikael discovers the man who stole FireFall from Lisbeth is part of an organization called "The Spiders." Lisbeth calls Mikael and asks if he's alone, but he avoids the question. Lisbeth senses his hesitation and quickly accesses his laptop webcam.
The Girl in the Spider's Web/Sony Pictures Entertainment
Zooming into the terminal in the background, we can see she runs the below command to establish a live stream using his laptop webcam.
> -open -source:mb.onethingin.com - device:webcam
IP Stream connecting. please wait.
Connection establishing to mb.onethingin.com
Opening stream...The -source argument would suggest the origin of the live stream is coming from mb.onethingin.com, which is an existing domain created in 2010. Based on DNS and Whois lookups, as well as TCP and UDP port scans, there seems to be nothing remarkable about the domain or server that we could find.
With Dynamic DNS (DDNS) and Ngrok-style servers, remote computers can be accessed behind firewalls and routers using domain names. It's common for hackers to embed DDNS and Ngrok URLs into payloads designed to connect back to their system. Presumably, Lisbeth has configured a backdoor into Mikael's laptop that allows her to quickly access his webcam using this domain.
Accessing the webcam of a macOS Mojave device, for example, can be accomplished without Apple's screen-sharing application, root privileges, or being detected by third-party antivirus software. Coupled with an automation script, accessing a webcam remotely using a single command is entirely realistic.
11. Needham Triangulates Lisbeth's Location
The scene starts with agent Needham acquiring a dumbphone from one of Lisbeth's acquaintances. He later uses the phone to text Lisbeth in an attempt to social engineer an SMS reply, which allowed him to triangulate her phone's physical location.

The Girl in the Spider's Web/Sony Pictures Entertainment
There's a misconception here. Cell phone triangulation, while very realistic, doesn't require an active call or SMS to work. Needham should've been able to triangulate Lisbeth's location without first texting her. Wireless carriers can do this when requested by emergency services or law enforcement. Hell, those carriers even sell the data to location aggregators like LocationSmart, a company that recently popped up in the news again for selling tower information to a location data seller who then sold it to bounty hunters and bail bondsmen.
When attempting to triangulate a device's location, you measure the time delay between how long it takes for the phone to communicate with a nearby cell tower. The delay is then calculated into distance. This is performed using multiple cell towers surrounding the phone, which makes it possible to generate a relatively accurate depiction of the phone's proximity to the cell towers (give or take fifty meters). This is shown in the below graphic.

Distortion/Null Byte
How Needham identified the floor and apartment number where Lisbeth was presumably located isn't made evident in the film. However, GPS modules in cell phones can measure altitude, but the elevation accuracy is very low. Still, wireless carriers have access to this which also sells this data to the aforementioned services which, in turn, sell more accurate location data to those who want it.
12. Lisbeth Spoofs Her Location to Evade Triangulation
We soon learn Needham has been fooled by Lisbeth's masterful abilities to spoof her location as he finds himself in a somewhat abandoned storage area.

The Girl in the Spider's Web/Sony Pictures Entertainment
There are no servers or computers shown in the area so it's not clear how Lisbeth pulled this off. The fact that Lisbeth is using a dumbphone (not an iPhone or Android phone) to text Needham pushes the practicality of this spoofing into the realm of fiction.
With an Android phone, for example, Lisbeth could've hid the phone in the storage area and remotely controlled it through another device or relayed text messages to a server. This doesn't appear to be what she did in the film but there's simply not enough coverage to further speculate.
13. Lisbeth Accesses Her Wireless Camera
It's established in the film that Frans Balder's son, August, is the only person who can unlock Frans' "Freak" encryption. This makes him The Spiders' primary target. Frans and August seek the protection of the Säpo security agency and are moved to a safehouse.
Jan kills the Säpo agents protecting the safehouse as well as Frans. He then kidnaps August and forces him into a black vehicle. Lisbeth hastily begins her pursuit by remotely accessing footage in the video camera she planted in front of the Säpo safehouse located by Plague earlier in the movie.

The Girl in the Spider's Web/Sony Pictures Entertainment
The camera, of course, is an actual Sony camera that can be used for remote surveillance. Similarly, GoPro cameras can perform the same functionalities at a fraction of the price.
14. Lisbeth Tracks a Smart Car
After learning the license plate number, Lisbeth uses a Säpo laptop (found in the dead agent's car) to track the black vehicle in real time. The computer has direct access to EUVID and TVIS vehicle identification databases.

The Girl in the Spider's Web/Sony Pictures Entertainment
This is accurate for most government agent vehicles, such as the FBI. For over a decade, law enforcement agencies have been able to hijack a vehicle's OnStar and SiriusXM radio system using search warrants and court orders to geographically locate the driver. Lisbeth accomplishes this by simply entering the license plate number.
15. Lisbeth Remotely Deploy's the Smart Car Airbags
As Lisbeth approaches the black vehicle, she attempts to connect to it using her phone. Her attempt to remotely interface with the vehicle plays on how most people think of syncing Bluetooth devices. While not entirely accurate to smart cars, she manages to connect when August accepts her authentication request from inside the car. She then immediately deploys the front airbags, incapacitating the driver and passenger.

The Girl in the Spider's Web/Sony Pictures Entertainment
Realistically, there's a lot owners can do while remotely accessing a smart car. Such features include monitoring the vehicle mileage, viewing repair diagnostics, adjusting climate, starting the engine, unlocking the doors, and even triggering the car's anti-theft alarm.
- Don't Miss: Tesla Model S Vehicle Hacked
Where the film goes too far is Lisbeth's ability to deploy the airbags. It would be irresponsible for car manufacturers to build such a feature into a remote control app. As we see in the movie, the driver of the black vehicle is knocked unconscious as the car continues to move with people still inside. A "Deploy Airbag" button would simply be too dangerous.
16. Lisbeth Remotely Unlocks Several Cars at Once
After rescuing August from The Spiders, the characters find themselves in a parking lot seeking a new vehicle. Lisbeth is seen using her phone to quickly unlock several cars in the area. This is represented in the film by the sound of multiple cars being unlocked simultaneously, so the below GIF doesn't do the hack justice.

The Girl in the Spider's Web/Sony Pictures Entertainment
This hack resembles Rolljam, created by Samy Kamkar, which was designed to defeat "rolling codes" found in modern vehicles using keyless entry systems. For Rolljam to be effective, the attacker must first be near the vehicle as it's unlocked by the owner. This allows the attacker to intercept the unlock code sent to the vehicle. Rolljam can then replay the intercepted code and unlock the vehicle.
Lisbeth seems to bypass multiple keyless entry systems using her cellphone with a Rolljam-like hack. While this flirts with fictional undertones, many car exploits have been disclosed in recent years. Modern vehicles can have over one hundred built-in microcomputers. And like any computer, these systems can be hacked — sometimes remotely.
17. Lisbeth Delivers a Message Using a Printer
Mikael learns of Frans Balder's murder and the kidnapping allegations against Lisbeth on the news. Suddenly, his printer begins to generate a map of Lisbeth's safehouse coordinates.

The Girl in the Spider's Web/Sony Pictures Entertainment
As we learned earlier in the movie, Lisbeth has established a persistent backdoor into Mikael's laptop. It would be trivial for her to remotely issue print jobs using his computer.
At the time of this writing, there are over 130,000 registered servers containing a "printer" header on Shodan. Many of these printer owners are not aware their device is accessible to the entire internet. There are many noteworthy printer hacking projects such as the PRinter Exploitation Toolkit (PRET), used to control printers both remotely and locally.
In recent news, over 50,000 printers were remotely compromised for YouTube celebrity PewDiePie in an effort to bring awareness to his channel. Another 100,000 printers were hacked only a few weeks later, again, trying to increase PewDiePie's fanbase.
18. Lisbeth Social Engineers an Airport Police Officer
Lisbeth believes agent Needham can help protect August from being captured by The Spiders. Unfortunately, Needham is currently detained at an airport jail for interfering with Säpo's FireFall investigation and awaits deportation to the United States. Lisbeth, being the hacker she is, decides to break him in out.
The scene begins with Lisbeth lugging a large, very noticeable pink suitcase through the airport's main floor. She intentionally walks through a large crowd of people, dumps the suitcase midway through, and emerges without it.

The Girl in the Spider's Web/Sony Pictures Entertainment
Lisbeth's making an attempt to disguise the origin of the suitcase. The suitcase is pickup by an airport police officer and taken to the lost-and-found located behind a keycard-locked door. Its contents are examined by the police officer and a cell phone is discovered in the suitcase (among other things).

The Girl in the Spider's Web/Sony Pictures Entertainment
This is a classic social engineering technique. The suitcase is made to appear out of nowhere and moved deeper into the private employee-only quarters. It effectively acts as an infiltration vector to embed Lisbeth's hacking device (the cell phone) further into the security offices. The suitcase full of sex toys is meant to be an obscene distraction to divert attention away from the otherwise ordinary object, the cell phone.
This resembles USB dead drop attacks where a hacker places a USB flash drive somewhere for a target to find. Believing the device to be lost, the target curiously inserts the flash drive into their computer, which, of course, contains a payload designed to compromise the target's computer and grant the hacker full access to their machine.
Realistically, the airport's security system would be able to playback the surveillance footage and see Lisbeth enter the crowd with the suitcase. In low-security environments where every inch of the building isn't observable by one (or more) security cameras, this tactic is plausible.
19. Lisbeth Hacks the Airport Control System
Shortly after, there's a shot of the cell phone shown just a few feet away from the router in the security room. Lisbeth proceeds to remotely compromise the router using the cell phone found in the suitcase and accesses the "Airport Control System" using her own cell phone.

The Girl in the Spider's Web/Sony Pictures Entertainment
Readers familiar with Aircrack-ng will recognize the barely readable Airodump-ng sessions running in the background. This isn't the most accurate representation of wireless router hacking.
Airodump would suggest a WPA2 handshake capture, as WEP has been an outdated encryption protocol for over ten years and isn't used by the TP-Linkrouter featured in the film. This would mean Lisbeth is engaging in some kind of password-cracking attack and not invoking a router-specific exploit as we hoped. This was probably a missed opportunity to feature a WPS attack. A brute-force attack using a smartphone CPU is very impractical but realistically possible. Still, the movie scores points for paying homage to Aircrack.
Hundreds of router exploits are disclosed every single year. Pivoting from the router to a control system on the network is possible with frameworks like RouterSploit and Metasploit. RouterSploit is a popular router exploitation framework that can be run on an Android device to quickly compromise a TP-Link router as well as many others. With full access to the routers internal settings, an attacker can engage in DNS poisoning and software update hijacking attacks.
20. Lisbeth Breaks Needham Out of Jail
After gaining access to the airport's control system, Lisbeth allows herself to be detected by surveillance cameras. As the airport police rush out to arrest her, she presses a button on her phone to unlock Needham's jail cell.
The Girl in the Spider's Web/Sony Pictures Entertainment
With access to the airport's internal control system, Lisbeth could've remotely unlocked Needham's jail cell. There are no close-ups of her phone or any indication of how this was achieved in the film, unfortunately. However, major airlines and police stations have been affected by data breaches and ransomware in recent history.
21. Lisbeth Delivers a Message Using the Announcement System
After evading the police officers, Lisbeth issues an airport-wide announcement alert and delivers a message to agent Needham directing him to another part of the airport.

The Girl in the Spider's Web/Sony Pictures Entertainment
Public announcement systems such as amber alert and emergency alert systems, navigation displays, traffic signs, and digital billboards are often hacked, usually to display obscene or ridiculous warning messages.
Again, Lisbeth already had access to the control system so there could've been a built-in function to conveniently relay a message to the announcement system operator.
22. Needham Hacks Big Pharma
While regrouping at Plague's home, Needham finds himself recalling a hack he performed many years before. He states:
Took down big pharma with this bad boy... I did it from a triple-seven-zero.

The Girl in the Spider's Web/Sony Pictures Entertainment
The computer he's referring to is the "Compaq Armada 7770," which features an Intel Pentium MMX processor, up to 144 MB of RAM, and only 3 GB of hard drive space.
It would be possible to compromise a remote computer or server with this laptop. Looking at the 7770's specs, it's fascinating how far technology has come. Today, a standard Raspberry Pi includes a superior CPU and RAM to Needham's laptop at a fraction of its cost in 2002.
Needham's reference to "big pharma" is likely a play on the notorious hacker group, Anonymous, and its declared war on big pharma. No other information is given in the scene for further speculation.
23. Lisbeth Embeds a Tracking Device in a Chess Piece
Earlier in the film, while seeking refuge at Lisbeth's safehouse, she gives August a bishop chess piece. We soon learn there's a GPS locator device embedded inside the chess piece.

The Girl in the Spider's Web/Sony Pictures Entertainment
Tiny GPS locators, small enough to fit inside of a chess piece, do exist. For instance, there's the TK-STAR GPS Tracker that's slightly larger than a quarter. It features a 600 mAh battery that allows the device to transmit its location in real time for up to seven days. Popular trackers such as Tile Mate would not work here, not only because they're too big, but because it does not have GPS built in, instead using a Bluetooth connection to a smartphone.
24. Jan Spoofs a Phone Call & Tracks August's Location
While Lisbeth is effortlessly breaking Needham out of the airport prison, Mikael and August are left alone at Lisbeth's safehouse. Unexpectedly, August receives a call from his father, Frans Balder, who was killed by Jan several scenes before. Confused by the incoming call, August answers his phone.
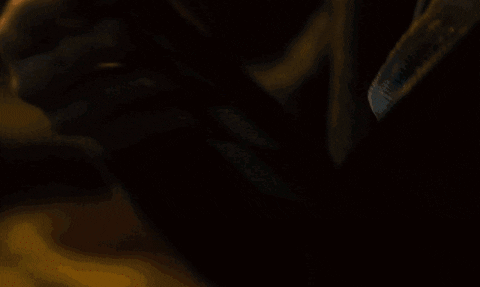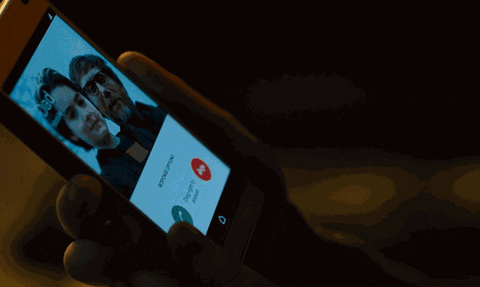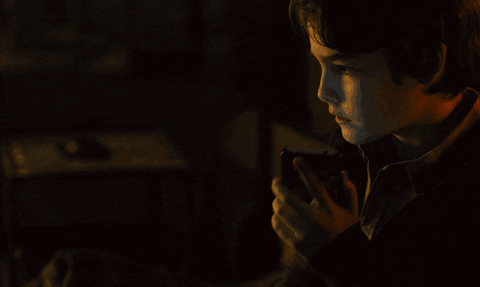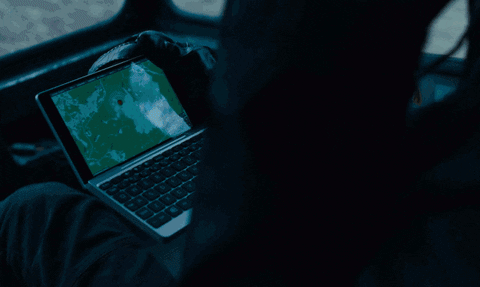
The Girl in the Spider's Web/Sony Pictures Entertainment
It's difficult to deduce how Jan was able to invoke an incoming call as Frans Balder. The movie never suggests he acquired Frans' cell phone, so we're sort of left assuming it's a spoofed call. Exactly how Jan was able to pinpoint August's exact location from a single phone call is entirely unclear and unrealistic.
Interestingly, Jan's social-engineering tactic resembles email phishing attacks. Using a compromised email account, attackers will send phishing links to everyone in the victim's address book; making the origin of the message appear legitimate.
A realistic alternative to this scene could have consisted of Jan texting August (as Frans Balder), with the SMS containing a link that can be tapped. August would've opened the link, revealing his IP address to Jan's website. IP addresses aren't geographically precise, but if Lisbeth's safehouse was located in the middle of nowhere, there would only be a limited number of structures in the area capable of acting as a hideout.
25. Lisbeth Uses the Chess Piece to Track August's Location
When August is kidnapped by Jan (yes, again), Lisbeth uses the GPS locator to track his location with Plague's computer.

The Girl in the Spider's Web/Sony Pictures Entertainment
A closer look at the graphical interface Lisbeth used to locate August reveals several things. First, OpenStreetMap is a community-driven Google Maps alternative, with an API and Web Map framework that can be used to create personalized tracking applications.

The Girl in the Spider's Web/Sony Pictures Entertainment
Second, there's what appears to be the GPS locator's MAC address. MAC addresses are unique identifiers for network interfaces found in all electric devices. An organizationally unique identifier (OUI), represented by the first six characters in the MAC address, indicates the device's vendor or manufacturer. In the case of the MAC address in the screenshot, there's no manufacturer linked to address. Additionally, MAC addresses are made up of twelve characters, and this one is missing two (45:22:45:CF:29:??), making it an inaccurate representation of MAC addresses.
26. Lisbeth Bypasses a Locked Door
Lisbeth tracks August's location to the old mansion where The Spiders operate. With the help of Plague and agent Needham, they devise a plan to rescue August. Lisbeth is seen infiltrating the mansion through a towering passageway (a backdoor, so to speak) and lifting the latch securing the door from the other side with a nail puller.
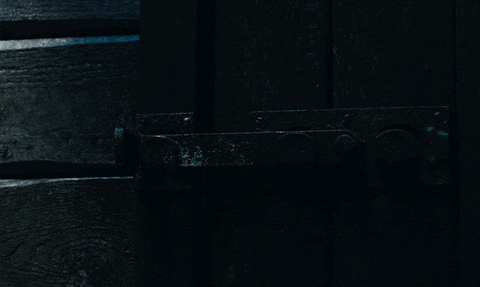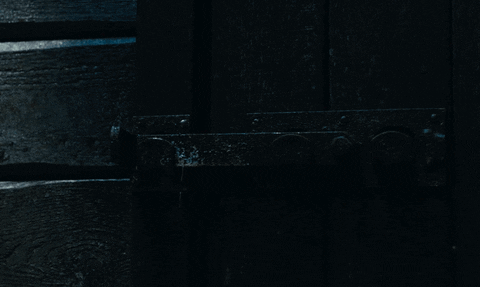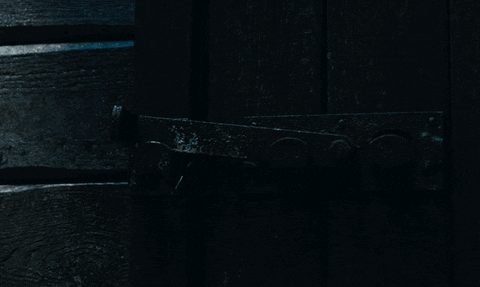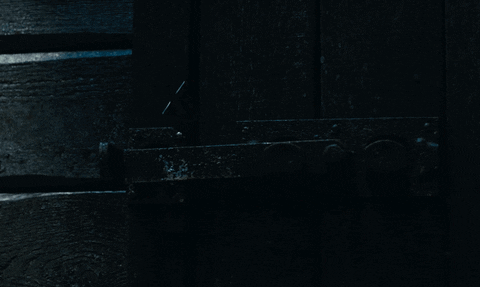
The Girl in the Spider's Web/Sony Pictures Entertainment
Physical penetration testers will use anything they get their hands on to bypass locked doors, and it's common for hackers to break into places using ordinary objects. This is best demonstrated in Walter Belgers' talk on physical pentesting where he shows how to use rubber bands, pieces of plastic, metal wires, and tape measures to get into all kinds of private areas.
27. Lisbeth & Plague Vampire-Tap a Camera System
After infiltrating the mansion, Lisbeth accesses the control panel responsible for managing the surveillance camera system. She's shown tapping into the camera system, which gives Plague remote access to all of the cameras in the mansion.

The Girl in the Spider's Web/Sony Pictures Entertainment
Small Computer Systems Interface (SCSI) is the kind of ribbon Lisbeth is shown vampire tapping into. SCSI was designed to connect to many different devices such as hard drives, scanners, and printers using a single bus. This was before USB became as popular as it is today. The way Lisbeth connects to the SCSI ribbon (with a plastic connector/clamp) is referred to as "chaining" and is somewhat accurate to how SCSIs can function.
We can see the SCSI ribbon is precisely 34 strands. 34-pin SCSIs were actually meant for old floppy disk drives. It could also be a 2-layer 68-pin SCSI, but it's just not possible to say exactly what kind of hardware is being used. There are too many types of SCSI cables, and the scene doesn't offer enough information.
Furthermore, it would've been more realistic for Lisbeth to interact with the CAT6 cables shown on the left of the SCSI ribbon. CAT6 cables can perform high volumes of data transfer, and they're more likely responsible for carrying the video signals produced by the surveillance cameras.
28. Plague Builds a 3D Map of the Mansion
Using the surveillance cameras, Plague generates a 3D mapping system that allows him to position people moving throughout the mansion. He then transmits the data to agent Needham who is outside the mansion with a sniper rifle. The data sent to Needham allows him to shoot people through the walls.
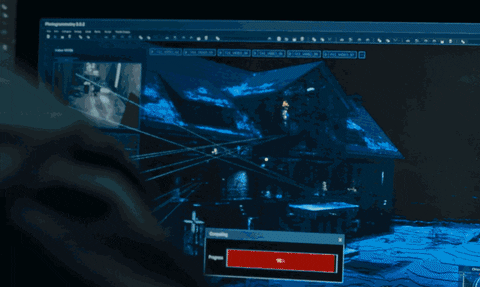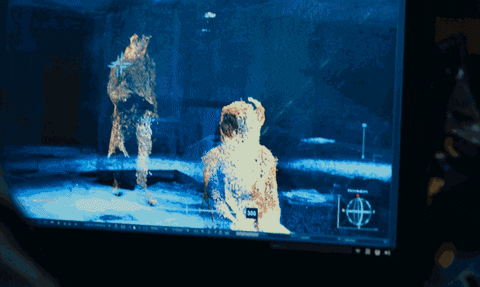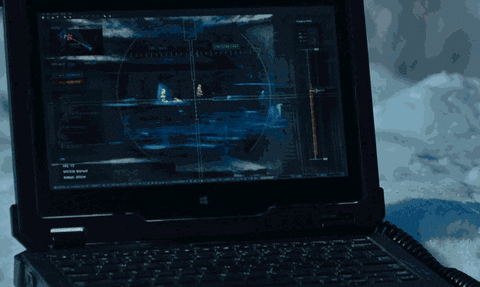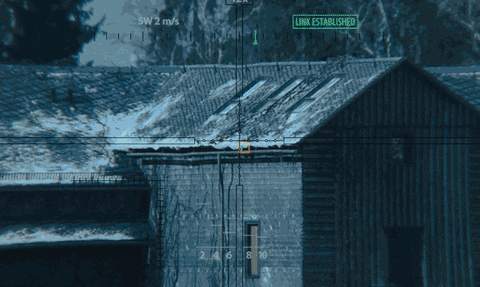
The Girl in the Spider's Web/Sony Pictures Entertainment
Modern robots have built-in sensors capable of mapping their environment. State estimation, for example, refers to the position of a landmark or object and its proximity to the sensor (or surveillance camera) which can be identified using mapping technologies. Simultaneous localization and mapping (SLAM) is a popular robotics mapping and navigation technology that simultaneously estimates the position of the sensor (localization) while mapping the environment in real time.
While there is no standalone software similar to the one Plague is seen operating, this concept of mapping people through walls using multiple localization points is realistic. It would require more than one camera to a room and a specialized image recognition software, but it can probably be done with today's technology.
Is It Worth Watching?
While the plot of The Girl in the Spider's Web had some weak points, it's still one of the best movies to feature hacking to such an extent in recent years.
There's a lot of technology and hacking featured in the film, with some scenes more realistic than others, the worst offender probably being how Lisbeth hacked the airport's router and control system without pressing a single button. With the amount of Wi-Fi hacking tutorials available on the internet, it was unfortunate to see the filmmakers depict this particular hack so inaccurately.
Our favorite hack, however, takes place in the same scene just moments before. Lisbeth leaves a suitcase in a public space and it is almost immediately moved into an employee-only area within proximity of her target, the router. This was an excellent and very realistic social engineering tactic.
We hope you enjoyed this review of the film and its hacks. Be sure to leave a comment below and let us know what you thought.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image via The Girl in the Spider's Web/Sony Pictures Entertainment

























Comments
Be the first, drop a comment!