Welcome back, my rookie hackers!
In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.
Before I discuss the inetd process, I want to explain that in Linux and Unix, processes that run in the background are called daemons. In some places, you we will even see them referred to as "demons," but that is incorrect. A daemon is a spirit that influences one's character or personality. They are not representatives of good or evil, but rather encourage independent thought and will. This is in contrast to a "demon," which we know is something quite different.

Unknown
Now, back to inetd. In the beginning—well, at least in the beginning of Unix—all daemons started at boot time and ran continuously. As you might imagine, this meant that processes that were not being used were using resources and depleting performance. This obviously was an inefficient way of doing business.
As systems gained more and more services, it became readily apparent that something different needed to be done. As a result, a programmer at Berkeley decided that it might be best to create a daemon that would control all other daemons, a sort of super daemon. Thus, began inetd, or the Internet daemon.
Inetd always runs in the background and it then decides when to start and stop other daemons. So, if a call comes in on port 21 for FTP services, inetd starts the FTP daemon. When a call comes in on port 80 for HTTP services, inetd starts HTTP services, and so on. In this way, inetd conserves resources and improves overall system performance.
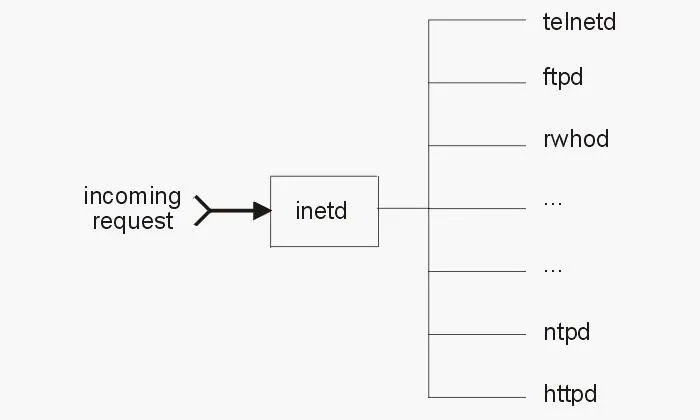
Eventually, this super daemon was exploited by hackers (imagine that) in a number of ways. If you think about it, if I can exploit the super daemon that controls all of the other daemons, I can control the entire system. At the very least, if I can control the super daemon, I can probably DoS the system. This is exactly what did happen and, as a result, we got a new and improved super daemon called xinetd.
Xinetd was developed to address some of the security vulnerabilities in inetd and was rather rapidly adopted by the commercial Linux distributions, Red Hat and SUSE. Debian and Ubuntu, which are the underlying Linux distributions of Kali and BackTrack, respectively, stayed with the older inetd, initially. But now Debian has transitioned to a newer version of inetd, labelled rlinetd.
Find Rlinetd
We can find rlinetd in our Kali system by typing the following.
kali > locate rlinetd
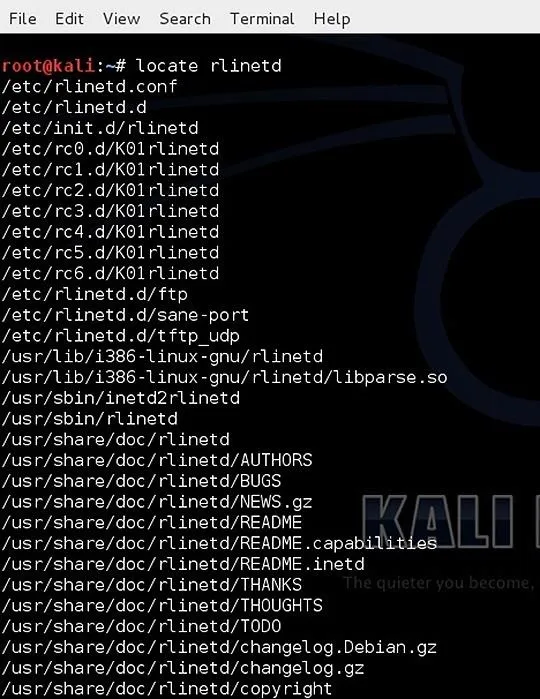
We can see at the top of the list, the configuration file for rlinetd and the daemon file itself.
Rlinetd Manual
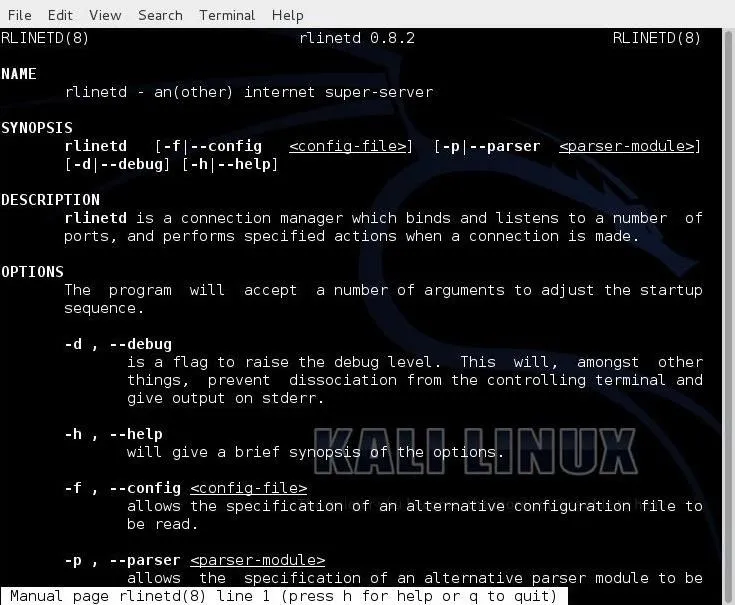
As I mentioned in earlier articles, whenever we want to know something about a particular command in Linux, we can, of course, Google it. Alternatively, we can also use the man, or manual, file. We simply type "man" before the command and the system will pull up the manual file for that command. Let's check out the manual for rlinetd.
kali > man rlinetd
Take a Look at rlinetd.conf
Finally, let's take a look at the configuration file for rlinetd. Let's open it with Leafpad or any text editor.
kali > leadpad rlinetd
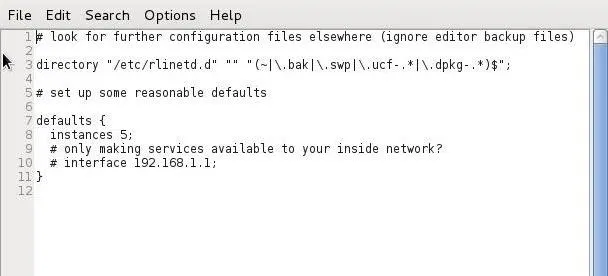
We can make our Linux system more secure by setting some default values in the rlinetd.conf file. For instance, if the system were only used for FTP services, it not only would be inefficient to run any other service, but also less secure. For example, if an attacker were trying to exploit HTTP and HTTP was disabled in the rlinetd.conf, they would not have much luck.
We could also change the rlinetd.conf to only start FTP services as needed and nothing else. If you only want this system accessible to a list of IP addresses or just your internal network, you could configure that access in the rlinetd.conf.
As a beginner with Linux, I recommend not making any changes to the rlinetd as you are more likely to sabotage and disable your system than making it more secure or efficient, but now you understand what inetd is. With more system admin experience, you can manage this super daemon to make your system safer and more efficient.
Don't Confuse Inetd with Init.d
Linux novices often confuse init.d and inetd. Init.d is an initialization daemon that runs when the system starts up. It determines the runlevel and the daemons that activate at start up. When a computer is turned on, the kernel starts the systems init.d, which always has a Process ID (PID) of 1.
The init process starts a series of scripts that get the system ready for use. These are things such as checking the filesystem and then mounting it and starting any system daemons that are required. These scripts are often referred as rc files because they all begin with the rc.(run command). I'll explain more on init.d in a subsequent tutorial, but I wanted to make certain that this distinction was clear.
Keep coming back, my rookie hackers, as we explore further the inner workings of Linux and prepare you to be professional hackers!

























Comments
Be the first, drop a comment!