Welcome back, my novice hackers!
There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.
Many novice hackers focus way too much energy on cracking passwords (which should be a last resort unless you have specialized tools or a 10,000 machine botnet) or exploiting a vulnerability in an operating system (increasingly rare). With all the protocols that computer systems use (DNS, SMTP, SMB, SNMP, LDAP, DHCP, etc), there is bound to be a vulnerability in one that we can exploit to get what we're after.
DNS Spoofing: Redirecting Users to Your Website
In this hack, we will be exploiting the Domain Name Service (DNS). As you know, DNS is used for domain name resolution or converting a domain name such as wonderhowto.com to an IP address, 8.26.65.101. If we can mess with this protocol, we could very well send some one looking for a domain name such as bankofamerica.com to our malicious website and harvest their credentials.
Dug Song of the University of Michigan developed a suite of hacking tools that are excellent for this purpose. We have already used one of his tools, arpspoof, for doing a man-in-the-middle attack. In this attack, we will be using his dnsspoof tool, which will enable us to spoof DNS services on a local area network.
Remember, even though this hack requires that you be on the same LAN, you could get access to the LAN through a remote vulnerability or a weak password on just ONE machine on the network. In institutions with thousands of computers on their network, that means you must find a single machine that is exploitable to be able implement this attack for the entire network.
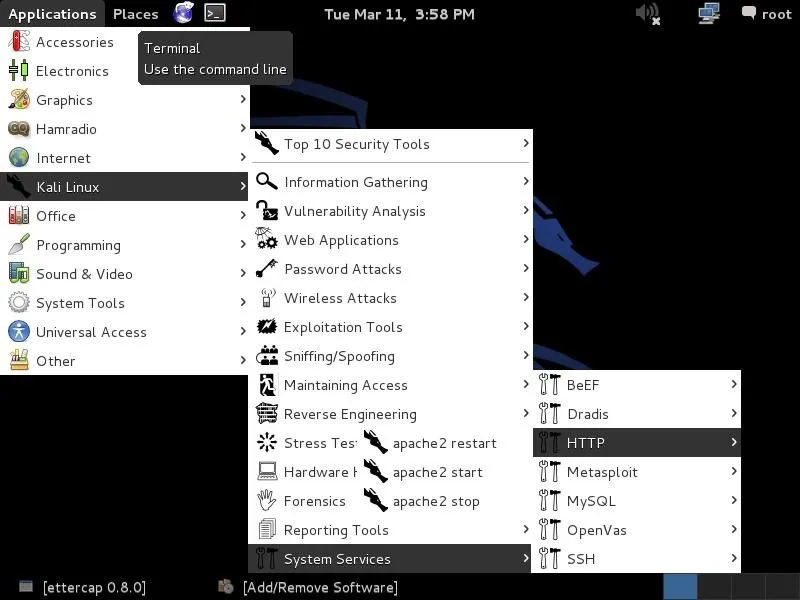
Fire Up Kali
Let's get started by firing up Kali and going to Applications -> Kali Linux -> Sniffing -> Network Sniffers, and finally, dnsspoof, as seen in the screenshot below.
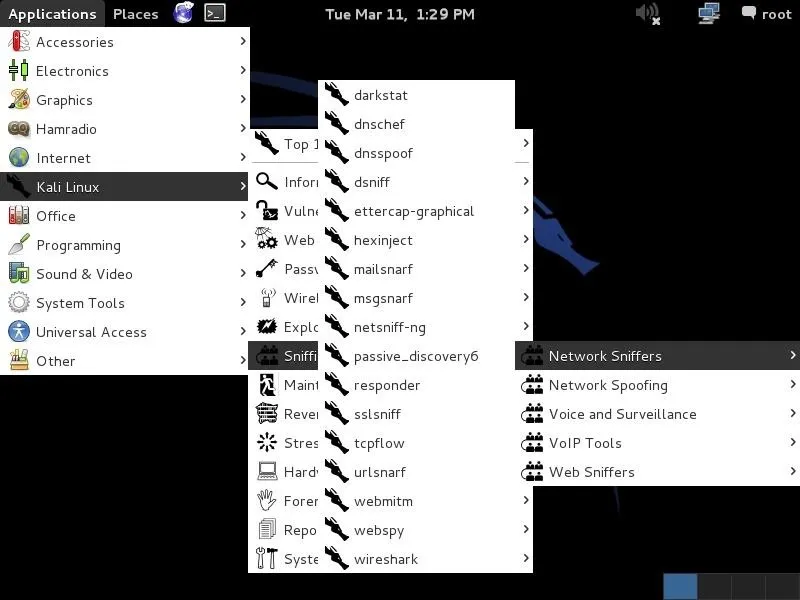
Open Dnsspoof
When you click on dnsspoof, the following terminal opens. Notice how simple the syntax is.
- dnsspoof -i
-f
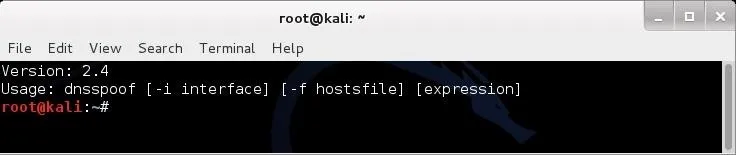
Set Up for Sniffing
We will trying to get a Windows 7 system on our network to redirect its bankofamerica.com navigation to our own website. Let's use Google Chrome, or any browser, to navigate there.
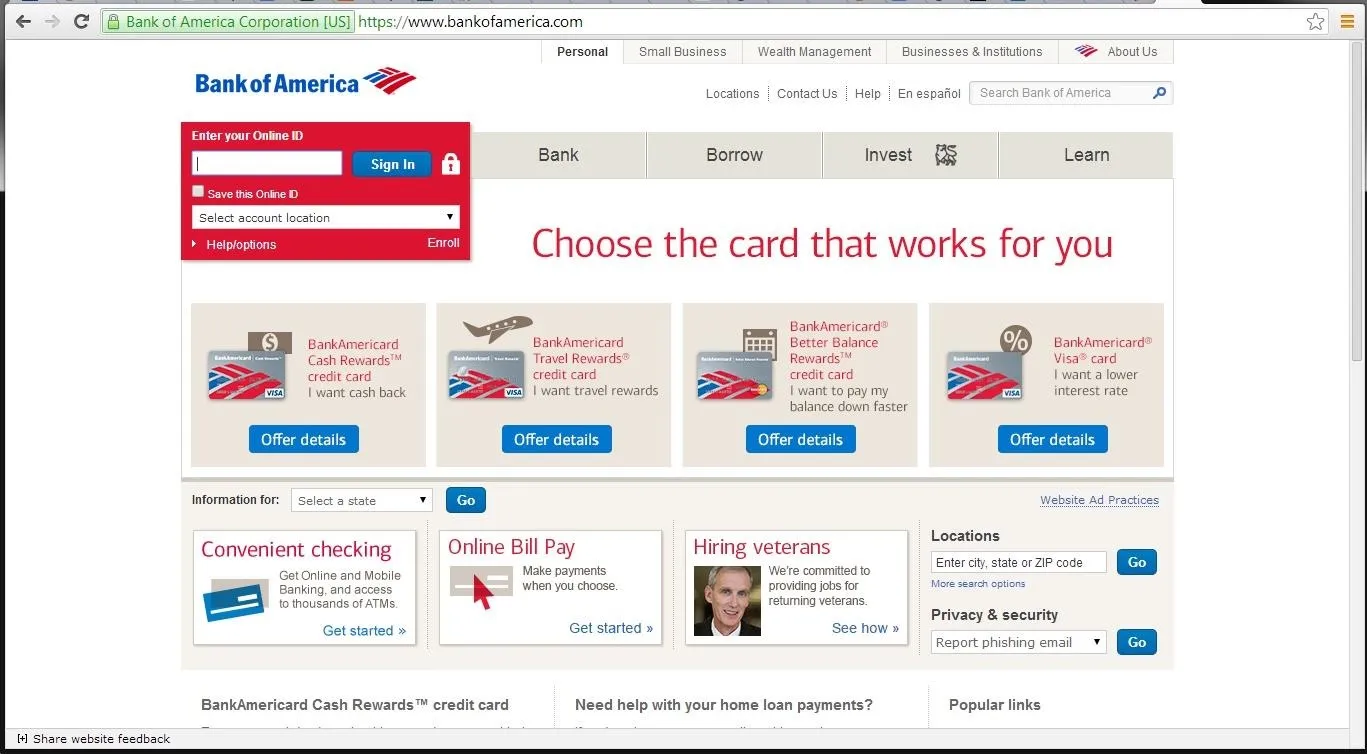
Flush the DNS Cache
First, we need to flush the DNS cache of the Windows 7 system. In this way, the Windows client won't use the cached DNS on the system and will instead use our "updated" DNS service. In reality, this step is not necessary, but for our demonstration it speeds things up.
First, close the browser and type:
- ipconfig /flushdns
Now we need to set our network card on our Kali server to promiscuous mode (she, your network card, will accept anyone's packets).
- ifconfig eth0 promisc
Now we need to kill the connection between the Windows 7 system and [www.bankofamerica.com]. This forces the Windows 7 machine user to re-authenticate.
- tcpkill -9 host [www.bankamerica.com]
After killing www.bankofamerica.com, stop the tcpkill with a ctrl c.
Create Hosts File
In my Linux tutorial on client DNS, I showed you how the hosts file in Linux acts like a static DNS. Here we will be using the hosts file to redirect that Windows 7 system's search for Bank of America to our website. Let's go to the /usr/local directory.
- cd /usr/local
From there, let's open the hosts file in any text editor. Kali doesn't have kwrite that we had been using in BackTrack, but it does have a graphical VIM, or gvim, so let's use that.
- gvim hosts
Now that we have the hosts file open, we need to add the following line to it. Remember, the hosts file is simply mapping an IP address to a domain name, so we put our IP address in and map it to [www.bankofamerica.com].
- 192.168.1.101 www.bankofamerica.com
It's important here to use the TAB key between the IP address and the domain. Spaces will be interpreted by the system to be part of the domain name.
Create a New BOA Webpage
Before we go any further, we now need to turn off promiscuous mode on our network card (she decided to commit to you and only you).
- ifconfig eth0 -promisc
Now we need to create a website that the user will be directed to when they type bankofamerica.com in the URL of their browser. Let's create a simple webpage. If you want more info on how to create a simple webpage and host it in Linux, check out my Linux guide on Apache web servers.
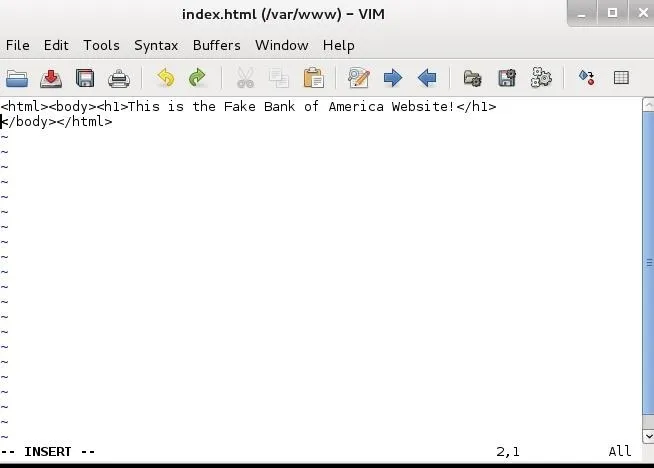
Now open the index.html.
- gvim /var/www/index.html
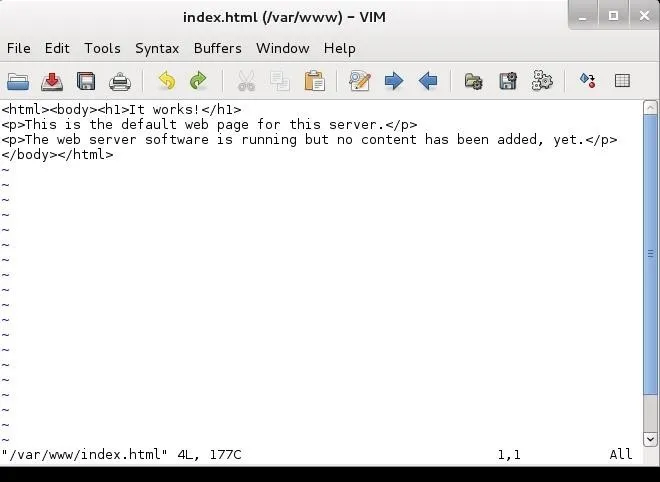
This is what it looks like by default. We want to change it and put in the following html and save it.
This is the Fake Bank of America Web Site!
Of course, if you really wanted to pull off this hack, you would want to take the time to build a website that looks and acts just like the site you're spoofing, but that is another tutorial entirely.
Start a the Apache Web Server
Now, start the web server built into Kali. This is Apache and the service is HTTP, so we go to Kali Linux -> System Services -> HTTP, and finally, apache2 start. This will start our web server on our Kali system hosting the fake Bank of America website.
Start Dnsspoof
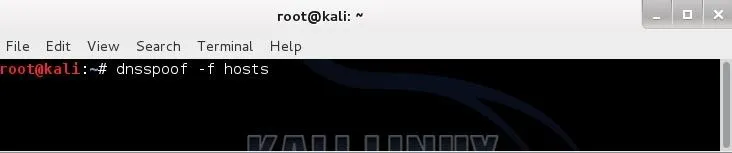
In our last step, we need to start dnsspoof and direct users to the entries in our "hosts" file first. Dnsspoof will intercept DNS queries and send them first to our hosts file before then sending them along to the DNS server. In this way, if we have any entry in our hosts file that the client is looking for, it will directed as specified by our hosts file.
Remember, we mapped bankofamerica.com to our IP address so that they will go to OUR web server and see OUR website.
- dnsspoof -f hosts
Navigate to BOA from Windows 7
Now, from the Windows 7 system, type in the URL bankofamerica.com and it will pull up our fake website vs. the real Bank of America site.
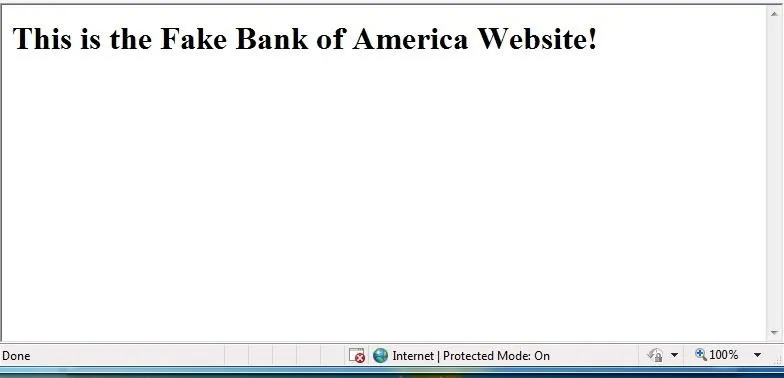
Now, when anyone on the local area network attempts to navigate to the Bank of America website, they will instead come to our website!
As you can imagine, with dnsspoof in place, we can wreak all kinds of havoc on a LAN!
URL box image via Shutterstock

























Comments
Be the first, drop a comment!